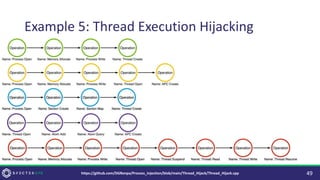
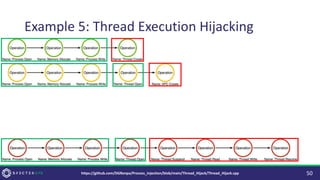
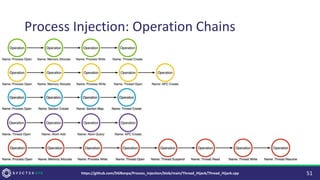
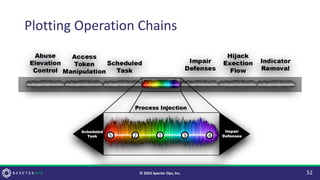
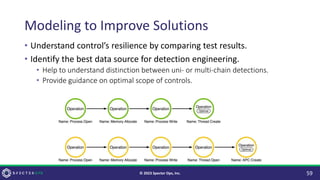
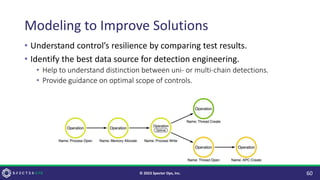
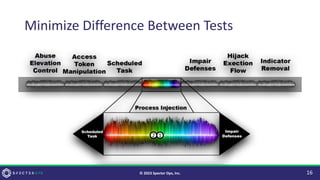
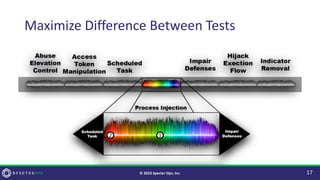
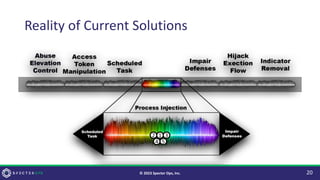
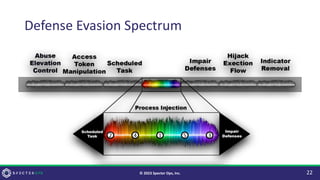
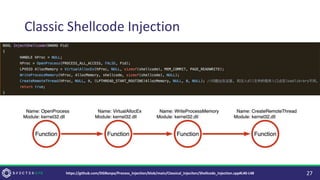
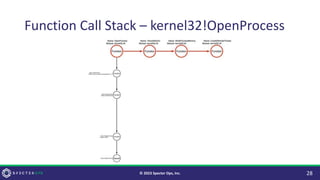
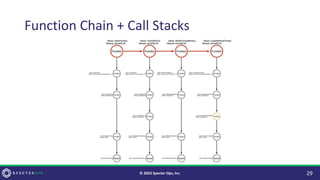
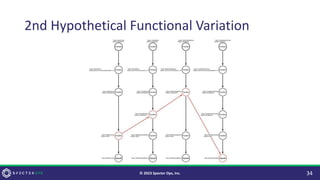
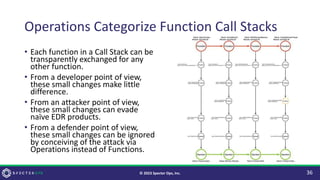
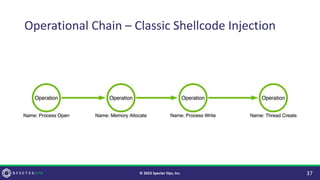
The document discusses purple teaming, which is a collaborative cybersecurity approach integrating red (offensive) and blue (defensive) teams to enhance organizational security. It highlights the importance of understanding adversarial tactics, testing detection capabilities, and improving security measures through deliberate test case selection and feedback mechanisms. Existing solutions and methodologies are examined, emphasizing the need for quality and diverse testing to better anticipate potential threats and improve overall defense strategies.


![What is Purple Teaming?
• A function designed to enhance the information sharing between – and the
ultimate effectiveness of – an organization’s Red and Blue Teams. The ultimate
purpose of improving the organization’s defenses.
• Daniel Miessler
• A blue team becomes “purple” when it emulates the adversary as a means of
self-evaluation.
• Jonathan Reiber
• [Purple Teaming] refers to multiple cybersecurity teams working together to
improve an organization’s security posture…
• Xena Olsen
• Actively pinpoint weaknesses in protection and detection capabilities.
• TIBER-EU
• Enables defenders to gain better understanding of adversary TTP.
• Cristian Pescariu (Pluralsight)
3
https://github.com/ch33r10/EnterprisePurpleTeaming](https://image.slidesharecdn.com/purpleteamwebinar-230323223904-cfaeb0b6/85/Red-Blue-How-Purple-Are-You-3-320.jpg)






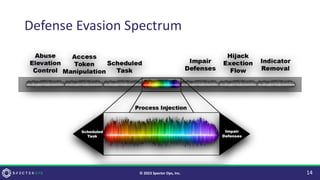
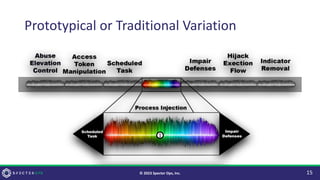






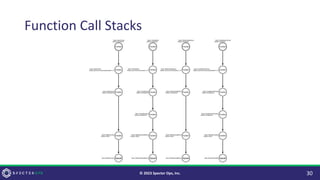
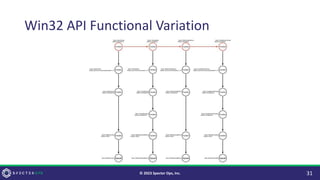
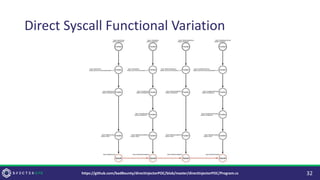
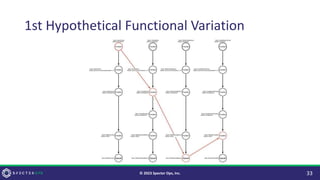
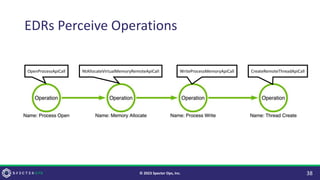

![Why Change it?
• Security Controls!
• This is analogous to natural selection, insofar as, if a control prevents or
endangers the operation it WILL act as a selective pressure.
• The more robust the control, the greater the change.
• [Small] Signatures looking for the string “mimikatz” result in ‘s/katz/dogz/g’.
• [Medium] Controls focused on specific API functions (CreateRemoteThread)
result in non-standard API functions being used (syscall!NtCreateThreadEx).
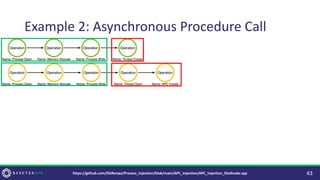
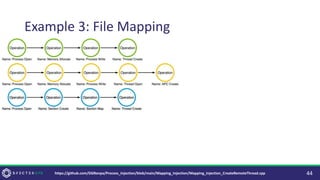
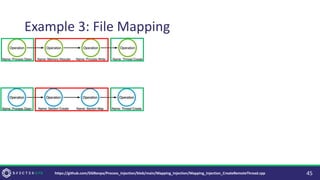
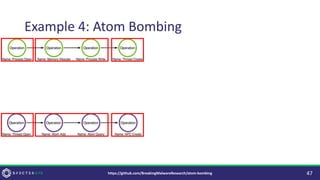
• [Large] Controls focused on the Execution method (Thread Creation) result in
novel Execution methods (Asynchronous Procedure Calls).
• Attackers often implement the “Minimal Stimulus Necessary”
principle.
40
© 2023 Specter Ops, Inc.](https://image.slidesharecdn.com/purpleteamwebinar-230323223904-cfaeb0b6/85/Red-Blue-How-Purple-Are-You-40-320.jpg)