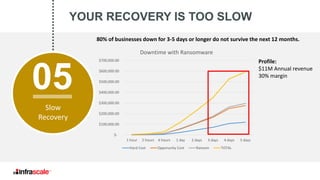
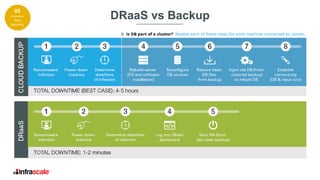
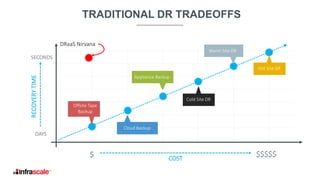
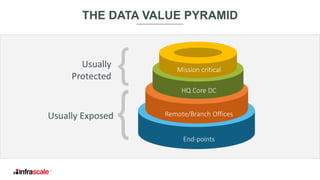
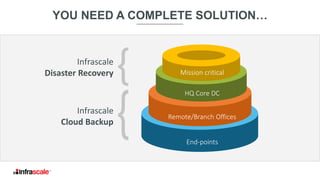
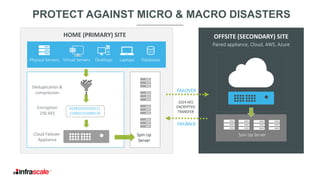
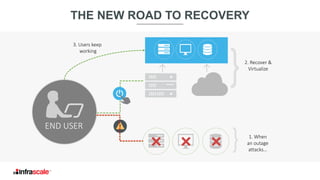
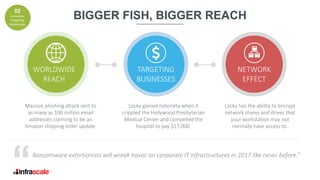
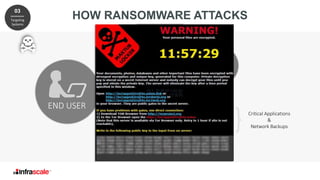
The document discusses the growing threat of ransomware, highlighting its impact on businesses and the importance of having an effective backup strategy. It emphasizes that downtime, rather than the ransom itself, is the most damaging consequence of such attacks. Infrascale offers disaster recovery as a service (DRaaS) that ensures rapid recovery from ransomware incidents, aiming to improve data protection and minimize losses for companies.











![04
ELIMINATING YOUR BACKUPS
Targeting
Systems
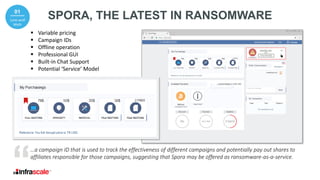
At the end of the encryption process, Spora runs [a] CLI command, which among other things deletes
shadow volume copies, disables Windows Startup Repair, and changes BootStatusPolicy.
Physical Servers Virtual Servers Desktops Laptops Databases
Storage
Encryption
256 AES
Deduplication &
compression
DOMAIN ACCESS GRANTS RIGHTS TO….
Offsite
Replication
010010101010111
110001101000110
BUT, NOT INFRASCALE.](https://image.slidesharecdn.com/triangulum-ransomwareevolved-whyyourbackupsarentgoodenough-170418215807/85/Triangulum-Ransomware-Evolved-Why-your-backups-arent-good-enough-20-320.jpg)