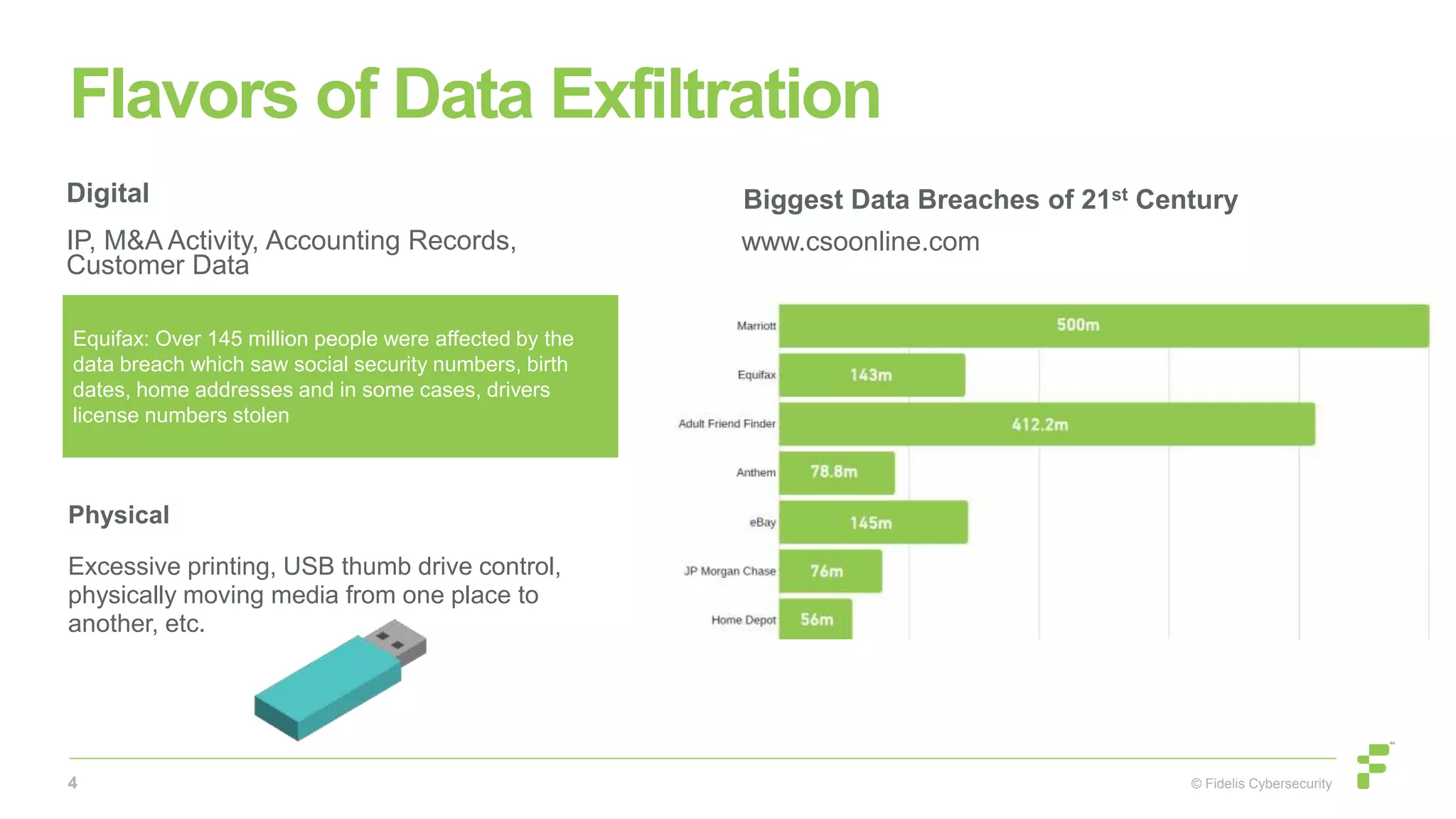
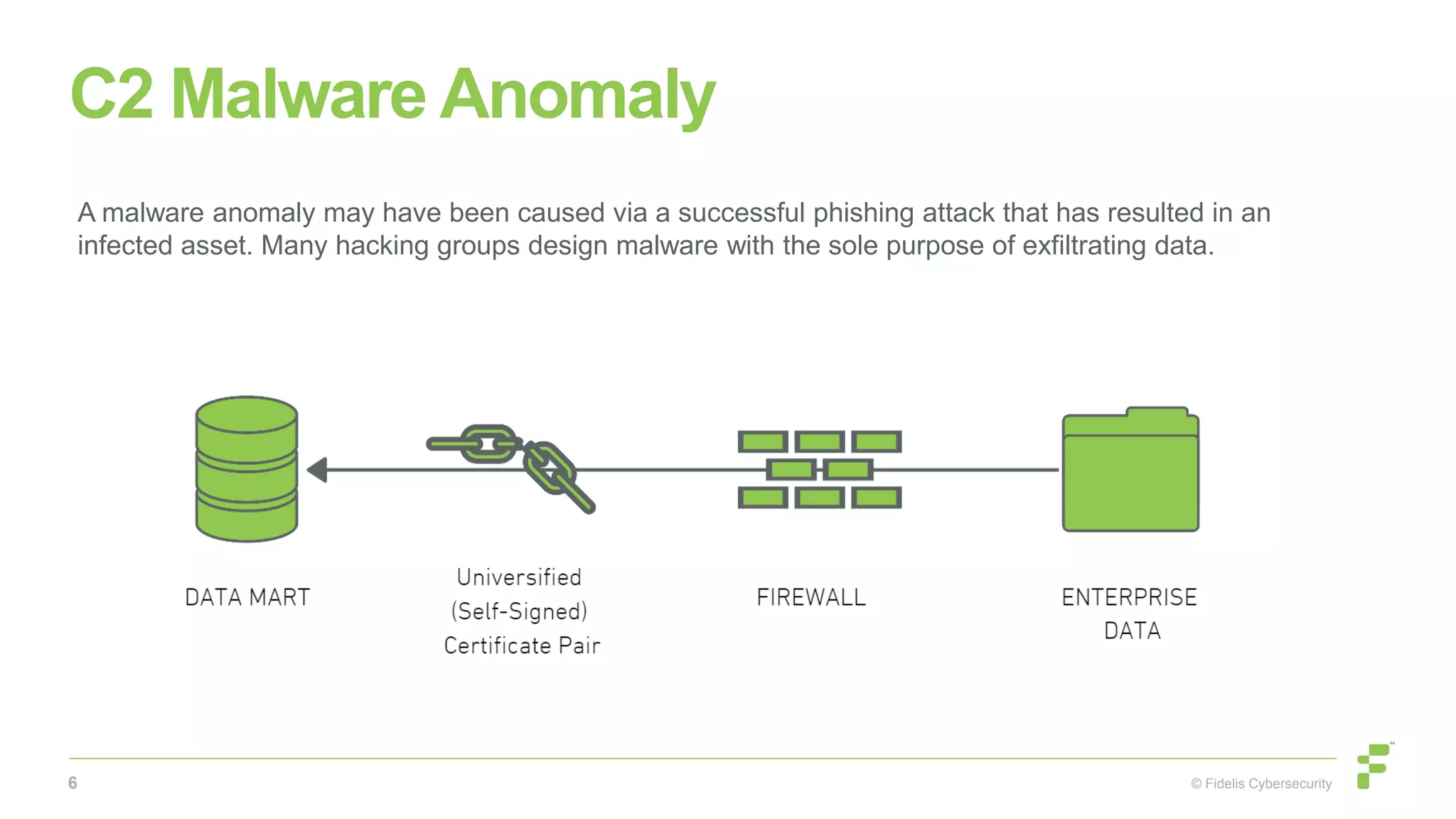
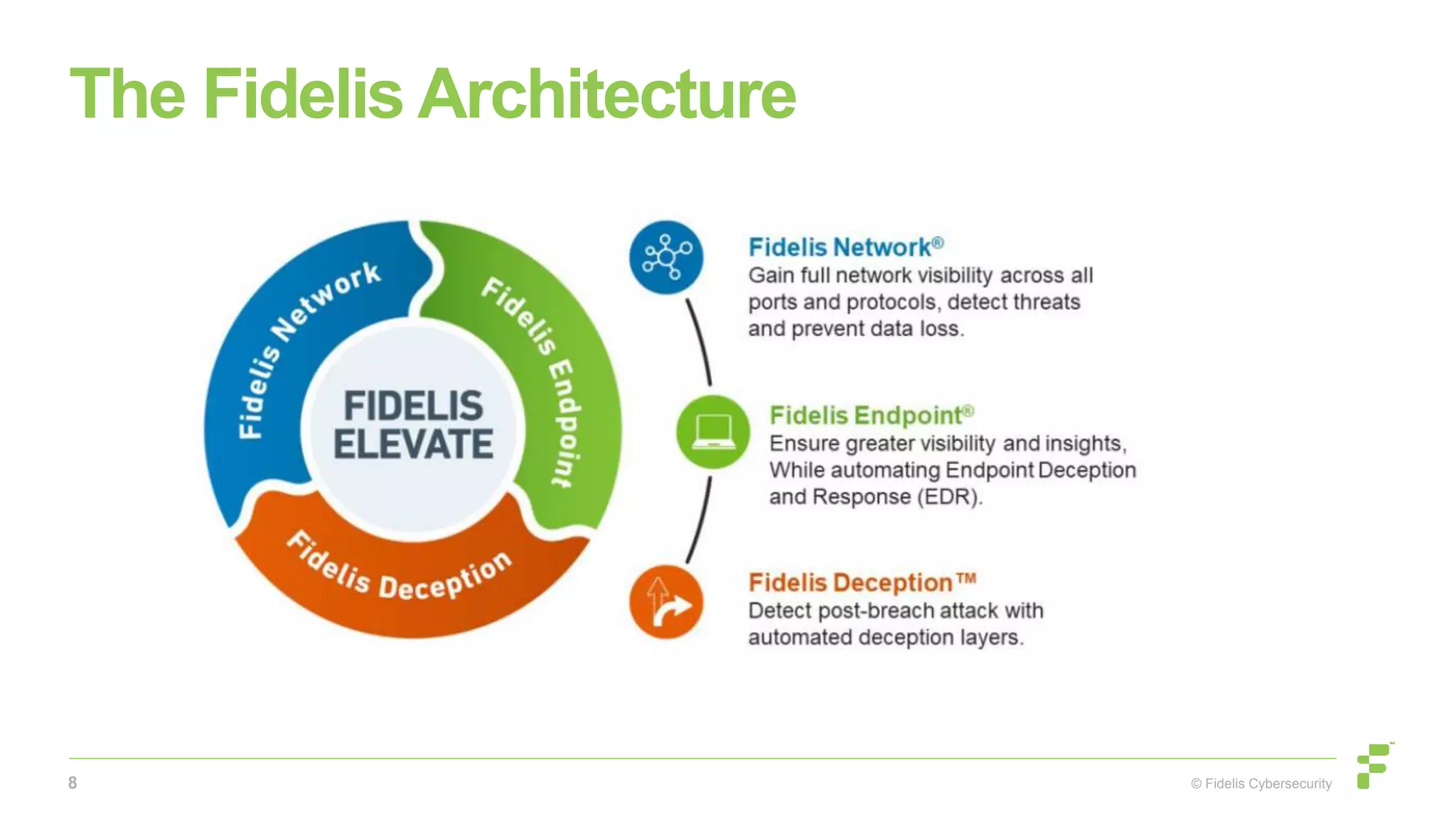
The document focuses on preventing data exfiltration through insider threats, defining categories and indicators of risk, and introducing methodologies for assessing and mitigating such threats. It highlights the importance of establishing behavioral baselines and discusses the role of metadata in enhancing security measures. Additionally, it showcases the Fidelis architecture and emphasizes a proactive approach in monitoring and managing insider threats.