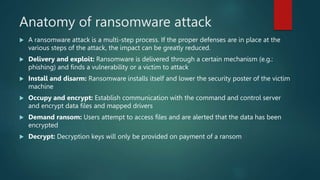
The document provides a comprehensive overview of ransomware, detailing its history, types, and how it operates, highlighting its emergence as a significant cyber threat since the late 1980s. It discusses two main types of ransomware, encryptors and lockers, along with various attack methods and notable examples. Additionally, the document emphasizes the importance of disaster recovery plans and preventive measures to combat ransomware attacks.