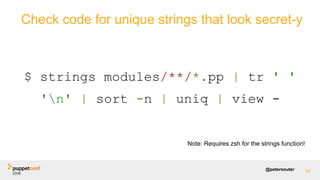
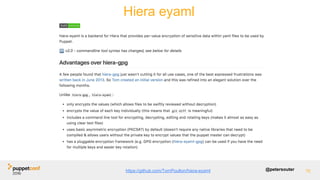
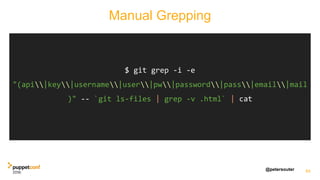
The document discusses operational security (opsec) and best practices for managing secrets within the Puppet toolchain to ensure secure code deployment. It illustrates how to avoid exposing sensitive information, the importance of encrypting secrets, and methods for effectively managing sensitive data using various techniques and tools. Additionally, it emphasizes the separation of configuration from code to prevent security vulnerabilities during deployment.











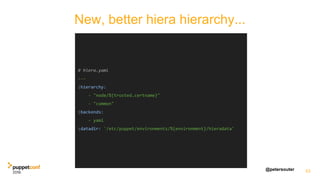
![@petersouter 18
root@homebox:~# puppet agent --show_diff
Notice: Compiled catalog for homebox.home in environment production in 0.10 seconds
Notice: /Stage[main]/Main/File[/etc/sensitive]/content:
--- /etc/sensitive 2016-08-14 23:01:37.036863915 +0100
+++ /tmp/puppet-file20160814-24654-ak1ywd 2016-08-14 23:01:56.852882307 +0100
@@ -1 +1 @@
-Not Secret
No newline at end of file
+SECRET-CONTENT
No newline at end of file
Notice: /Stage[main]/Main/File[/etc/sensitive]/content: content changed
'{md5}2ab96390c7dbe3439de74d0c9b0b1767' to '{md5}44c7be48226ebad5dca8216674cad62b'
Notice: Applied catalog in 0.20 seconds
How it looks...](https://image.slidesharecdn.com/track07thurssouter-161102173914/85/PuppetConf-2016-Nice-and-Secure-Good-OpSec-Hygiene-With-Puppet-Peter-Souter-Puppet-18-320.jpg)

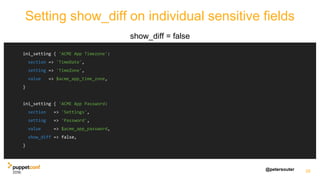
![@petersouter 21
An example from a Supported Module: mysql
file { "${::root_home}/.my.cnf":
content => template('mysql/my.cnf.pass.erb'),
owner => 'root',
mode => '0600',
}
# show_diff was added with puppet 3.0
if versioncmp($::puppetversion, '3.0') >= 0 {
File["${::root_home}/.my.cnf"] { show_diff => false }
}
https://github.com/puppetlabs/puppetlabs-mysql/blob/d58a100fa67bc99b4388d4ea3921b11647d483d7/manifests/server/root_password.pp#L39](https://image.slidesharecdn.com/track07thurssouter-161102173914/85/PuppetConf-2016-Nice-and-Secure-Good-OpSec-Hygiene-With-Puppet-Peter-Souter-Puppet-21-320.jpg)
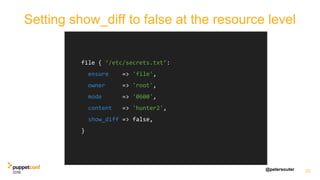
![@petersouter
Setting show_diff to false at resource scope
show_diff = false
22
root@homebox:~# puppet apply secret.pp
Notice: Compiled catalog for homebox.home in environment production in 0.10 seconds
Notice: /Stage[main]/Main/File[/etc/sensitive]/content: content changed '{md5}d3b07384d113edec49eaa6238ad5ff00' to
'{md5}44c7be48226ebad5dca8216674cad62b'
Notice: Applied catalog in 0.19 seconds](https://image.slidesharecdn.com/track07thurssouter-161102173914/85/PuppetConf-2016-Nice-and-Secure-Good-OpSec-Hygiene-With-Puppet-Peter-Souter-Puppet-22-320.jpg)



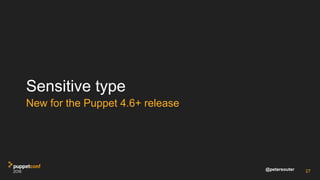
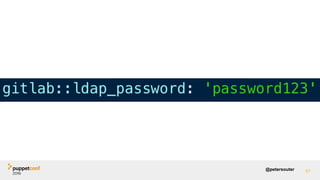
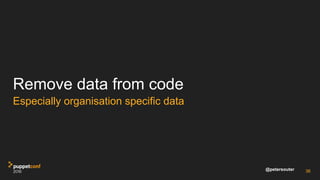
![@petersouter 28
file { '/etc/sensitive':
ensure => 'present',
owner => 'root',
group => 'root',
content => Sensitive('hunter2'),
}
root@homebox:~# puppet apply secret.pp
Notice: /Stage[main]/Main/File[/etc/sensitive]/ensure: changed [redacted] to [redacted]
Notice: Applied catalog in 0.18 seconds
Ability to redact strings with the new Sensitive Type](https://image.slidesharecdn.com/track07thurssouter-161102173914/85/PuppetConf-2016-Nice-and-Secure-Good-OpSec-Hygiene-With-Puppet-Peter-Souter-Puppet-28-320.jpg)
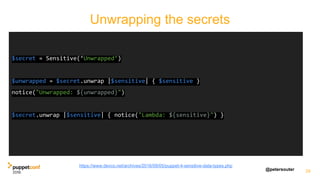
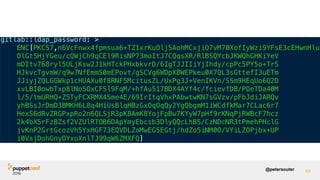
![@petersouter 31https://github.com/openstack/puppet-barbican/blob/2e2b10ae58fdc9ad27d88d3195260ef02af853ad/lib/puppet/type/barbican_config.rb
newproperty(:value, :array_matching => :all) do
desc 'The value of the setting to be defined.'
munge do |value|
value = value.to_s.strip
value.capitalize! if value =~ /^(true|false)$/i
value
end
newvalues(/^[S ]*$/)
def is_to_s( currentvalue )
if resource.secret?
return '[old secret redacted]'
else
return currentvalue
end
end
def should_to_s( newvalue )
if resource.secret?
return '[new secret redacted]'
else
return newvalue
end
end](https://image.slidesharecdn.com/track07thurssouter-161102173914/85/PuppetConf-2016-Nice-and-Secure-Good-OpSec-Hygiene-With-Puppet-Peter-Souter-Puppet-31-320.jpg)
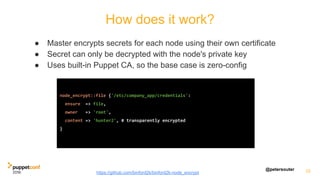
![@petersouter
node_encrypt
34
$ puppet agent -t
Info: Using configured environment 'production'
Info: Retrieving pluginfacts
Info: Retrieving plugin
Info: Loading facts
Info: Caching catalog for master.puppetlabs.vm
Info: Applying configuration version '1450109738'
Notice: /Stage[main]/Main/Node[default]/Node_encrypt::File[/tmp/foo]/Node_encrypted_file[/tmp/foo]/ensure: created
Notice: Applied catalog in 9.33 seconds
$ echo blah > /tmp/foo
$ puppet agent -t
Info: Using configured environment 'production'
Info: Retrieving pluginfacts
Info: Retrieving plugin
Info: Loading facts
Info: Caching catalog for master.puppetlabs.vm
Info: Applying configuration version '1450109821'
Notice: /Stage[main]/Main/Node[default]/Node_encrypt::File[/tmp/foo]/Node_encrypted_file[/tmp/foo]/content: content changed '<<encrypted>>' to
'<<encrypted>>'
Notice: Applied catalog in 7.61 seconds](https://image.slidesharecdn.com/track07thurssouter-161102173914/85/PuppetConf-2016-Nice-and-Secure-Good-OpSec-Hygiene-With-Puppet-Peter-Souter-Puppet-34-320.jpg)






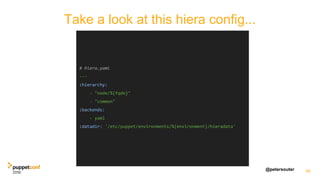
![@petersouter
Facts are spoofable!
49
[root@testbox]# facter fqdn
pe-201620-master.puppetdebug.vlan
[root@testbox]# FACTER_fqdn=evil.example.com facter fqdn
evil.example.com
Facts are spoofable](https://image.slidesharecdn.com/track07thurssouter-161102173914/85/PuppetConf-2016-Nice-and-Secure-Good-OpSec-Hygiene-With-Puppet-Peter-Souter-Puppet-49-320.jpg)