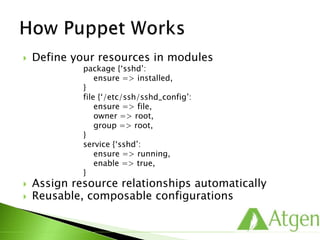
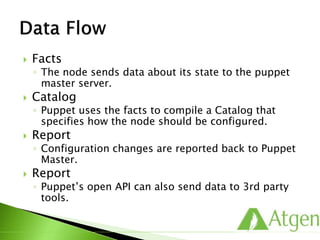
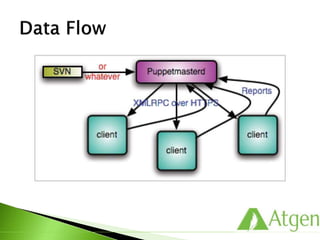
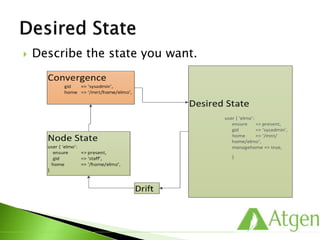
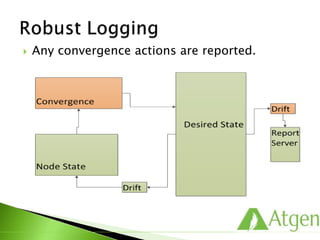
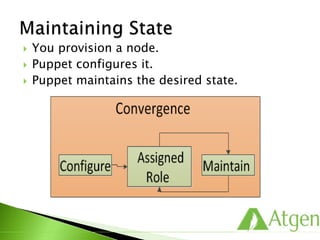
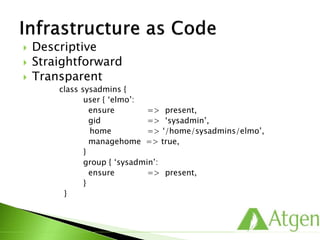
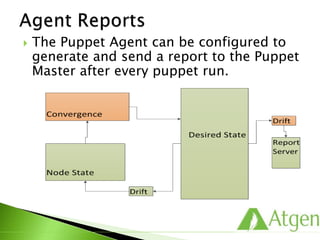
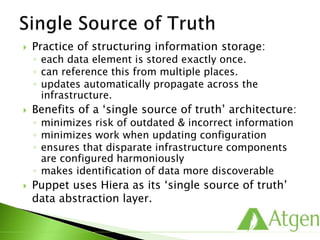
This document provides an overview of Puppet concepts including modules, classes, resources, nodes, catalogs, and roles. It explains that Puppet is configuration management software that uses declarative language and resources to define and enforce the desired state of systems. Puppet Masters compile catalogs that Puppet Agents use to configure and maintain nodes according to assigned classes and dependencies between resources. Modules help organize and reuse configuration code.













![ You could do something like this:
#!/bin/sh
USER=$1 ; GROUP=$2 ; HOME=$3
if [ 0 –ne $(getent passwd $USER > /dev/null)$? ]
then useradd $USER –home $HOME –gid $GROUP –n ; fi
OLDGID=`getent passwd $USER | awk –F: ‘{print $4}’`
OLDGROUP=`getent group $OLDGID | awk –F: ‘{print $1}’`
OLDHOME=`getent passwd $USER | awk –F: ‘{print $6}’`
if [ “$GROUP” != “$OLDGID” ] && [“$GROUP” != “$OLDGROUP” ]
then usermod –gid $GROUP $USER; fi
if [ “$HOME” != “$OLDHOME” ]
then usermod –home $HOME $USER; fi](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-20-320.jpg)




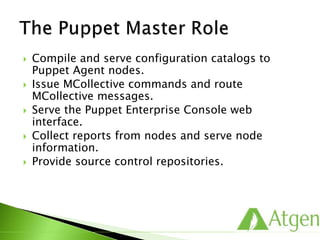













![ /etc/puppetlabs/puppet/puppet.conf
[main]
vardir = /var/opt/lib/pe-puppet
logdir = /var/log/pe-puppet
rundir = /var/run/pe-puppet
[agent]
certname = webdb1
server = puppet](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-48-320.jpg)
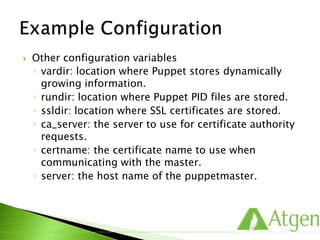









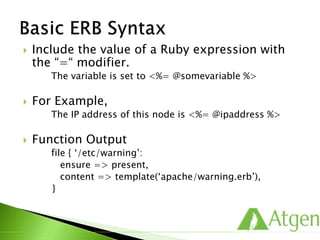
![ Classes define a collection of resources that are
managed together as a single unit.
# /etc/puppetlabs/puppet/modules/ssh/manifests/init.pp
class ssh {
package { ‘openssh-clients’:
ensure => present,
}
file { ‘/etc/ssh/ssh_config’:
owner => ‘root’,
group => ‘root’,
mode => ‘0644’,
require => Package[‘openssh-clients’],
source => ‘puppet:///modules/ssh/ssh_config’,
}
service { ‘sshd’:
ensure => stopped,
enable => false,
}
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-59-320.jpg)
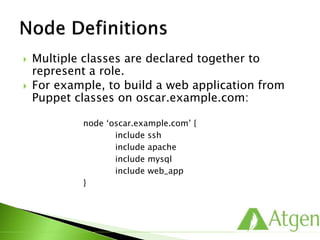



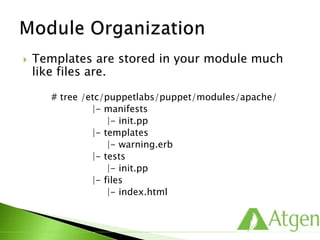
![ Modules enable class auto-discovery.
First, Puppet needs to know where to find your modules.
Then, your classes are placed in this predictable structure.
# tree /etc/puppetlabs/puppet/modules/ssh
…
|- manifests
|- init.pp
|- server.pp
Puppets expects to find classes in the manifests directory of
your module.
# puppet.conf on puppet master
[main]
basemodulepath=/etc/puppetlabs/puppet/modules:/opt/puppe
t/share/project/modules](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-64-320.jpg)


![ When you build a class like the following, you
are defining it.
class ssh {
package { ‘openssh-clients’:
ensure => present,
}
file { ‘/etc/ssh/ssh_config’:
owner => ‘root’,
group => ‘root’,
mode => ‘0644’,
require => Package[‘openssh-clients’],
source => ‘puppet:///modules/ssh/ssh_config’,
}
service { ‘sshd’:
ensure => stopped,
enable => false,
}
}
To use it, you need to declare the class.
include ssh](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-67-320.jpg)


![ One-off manifest enforcement.
Validate your code.
Temporary changes that may be overridden
on the next Agent run.
‘puppet apply’ compiles a manifest file and
enforces it immediately.
# puppet apply tests/init.pp
notice: /Stage[main]/Ssh/Service[sshd]/ensure: ensure
change ‘stopped’ to run….
notice: Finished catalog run in 0.14 seconds](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-70-320.jpg)
![ ‘--noop’ mode simulates without enforcing.
Resource Abstraction Layer [RAL] can
simulate events rather than taking action.
Inform you of system drift and expected
convergence actions.](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-71-320.jpg)



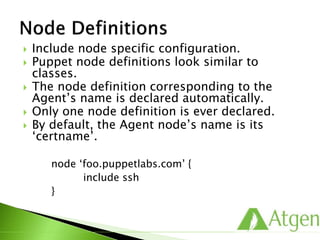






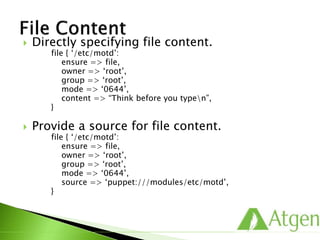




![ The following ensures that the ‘sshd’ service
is started after the ‘openssh’ package is
installed.
package { ‘openssh’:
ensure => present,
}
service { ‘sshd’:
ensure => running,
enable => true,
require => Package[‘openssh’],
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-90-320.jpg)
![ The also ensures that the ‘sshd’ service is
started after the ‘openssh’ package is
installed.
package { ‘openssh’:
ensure => present,
before => Service[‘sshd’],
}
service { ‘sshd’:
ensure => running,
enable => true,
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-91-320.jpg)
![ This ensures that the ‘ssh’ service is
restarted if Puppet changes the
‘/etc/ssh/sshd_config’ file resource.
file { ‘/etc/ssh/sshd_config’:
ensure => present,
source => ‘puppet:///modules/ssh/ssh_cofig’,
}
service { ‘sshd’:
ensure => running,
enable => true,
subscribe => File[‘/etc/ssh/sshd_config’],
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-92-320.jpg)
![ This also ensures that the ‘ssh’ service is
restarted if Puppet changes the
‘/etc/ssh/sshd_config’ file resource.
file { ‘/etc/ssh/sshd_config’:
ensure => present,
source => ‘puppet:///modules/ssh/ssh_cofig’,
notify => Service[‘sshd’],
}
service { ‘sshd’:
ensure => running,
enable => true,
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-93-320.jpg)


![ Availability of variables is dictated by the
variable’s scope.
Local scope locally overrides variables of the
same name from the parent.
class apache::params {
$logroot = ‘/var/log/httpd’
[…]
}
class apache::logs {
include apache::params
file { “${logroot}/httpd.log”:
owner => ‘apache’,
group => ‘apache’,
}
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-97-320.jpg)

![ The Puppet language supports simple arrays:
$somearray = [ ‘one’, ‘two’, ‘three’ ]
Arrays can be used as an argument to some resource
parameters:
user { ‘elvis’:
ensure => present,
home => ‘/home/elvis’,
uid => ‘5000’,
gid => ‘hounddog’,
shell => ‘/bin/bash’,
groups => [‘jailhouse’, ‘surfer’, ‘legend’],
}
Arrays can also be used as title for resources:
file { [‘/tmp/one’, ‘/tmp/two’, ‘/tmp/three’]:
[…]
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-99-320.jpg)










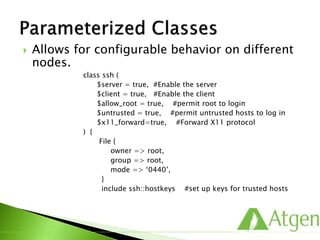
![ Share common behavior among multiple classes.
Start with a base class:
class ssh {
package { ‘openssh-clients’:
ensure => present,
}
file { ‘/etc/ssh/ssh_config’:
owner => ‘root’,
group => ‘root’,
mode => ‘0644’,
require => Package[‘openssh-clients’],
source => ‘puppet://modules/ssh/ssh_config’,
}
service { ‘sshd’:
ensure => stopped,
enable => false,
}
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-115-320.jpg)
![ Inherit a base class and customize behavior:
class ssh::server inherits ssh {
package { ‘openssh-server’:
ensure => present,
}
file { ‘/etc/ssh/ssh_config’:
owner => ‘root’,
group => ‘root’,
mode => ‘0644’,
require => Package[‘openssh-server’],
source => ‘puppet://modules/ssh/ssh_config’,
}
Service[‘sshd’] {
ensure => running,
enable => true,
subscribe => File[‘/etc/ssh/ssh_config’],
}
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-116-320.jpg)
![ Resources from both classes are managed:
◦ From Class [‘ssh’]:
Package [‘openssh-clients’]
File [‘/etc/ssh/ssh_config’]
Service [‘sshd’]
◦ From Class [‘ssh::server’]:
Package [‘openssh-server’]
File [‘/etc/ssh/ssh_config’]
Service [‘sshd’] parameters are overridden in
Class [‘ssh::server’].](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-117-320.jpg)
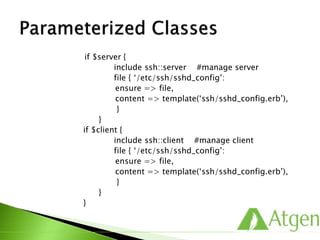

![ Basic Example
info: Applying configuration version ‘1328975856’
notice: Hello World!
notice: /Notify[example]/message: defined ‘message’
as ‘Hello World!’
notice: Finished catalog run in 0.03 seconds
Transaction Data
notice: /Notify[example]/message: defined ‘message’
as ‘Hello World!’
Metric Data
notice: Finished catalog run in 0.03 seconds](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-122-320.jpg)

![ Contains every log message in a
transaction.
Can be used to centralize client logs into
syslog.
Example:
# /var/log/messages
Compiled catalog for training.puppetlabs.vm in 0.86
seconds
Caching catalog for training.puppetlabs.vm
Applying configuration version ‘1328975856’ Hello World!
/Notify[example]/message: defined ‘message’ as ‘Hello
World!’
Finished catalog run in 0.69 seconds](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-124-320.jpg)

![ Delivers log reports via email based on
tags.
Example Configuration:
#
# /etc/puppetlabs/puppet/tagmail.conf
#
all: support@atgensoft.com
webserver: partners@atgensoft.com
Sample Emal:
From: report@atgensoft.com
Subject: Puppet Report for training.puppetlabs.vm
To: support@atgensoft.com
/Notify[example]/message: defined ‘message’ as ‘Hello World!’](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-127-320.jpg)
![ Puppet Agent
#
# /etc/puppetlabs/puppet/puppet.conf
#
[agent]
report = true # true is default for Puppet
Enterprise
Puppet Master
#
# /etc/puppetlabs/puppet/puppet.conf
#
[master]
reports = https,tagmail, store, log
# https,puppetdb is default for Puppet Enterprise](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-128-320.jpg)





![#cd /etc/puppetlabs/puppet/modules/sshdconfig/
#cat manifests/init.pp
class sshdconfig ( $serviceName = hiera(“sshservicename”) ) {
file { “/etc/ssh/sshd_config”:
owner => ‘root’,
group => ‘root’,
mode => ‘0644’,
source => “puppet:///modules/sshdconfig/sshd_config”,
notify => Service[$serviceName],
}
service { $serviceName:
ensure => running,
enable => true,
}
}](https://image.slidesharecdn.com/puppetfundamentals-150618135838-lva1-app6891/85/Puppet-for-Developers-140-320.jpg)