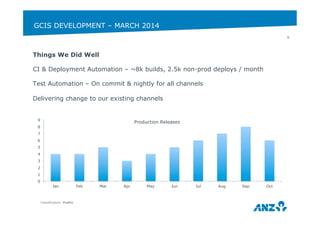
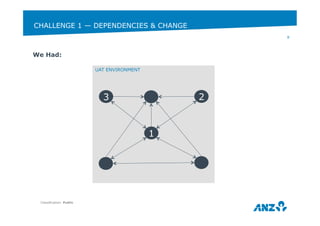
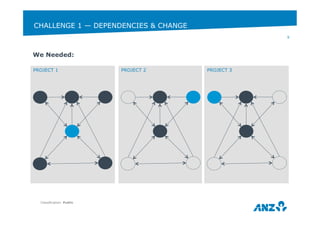
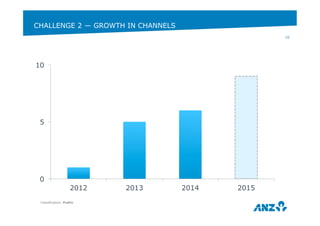
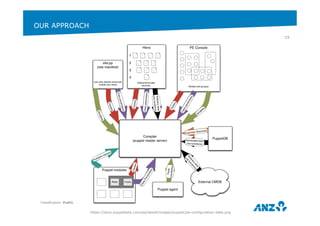
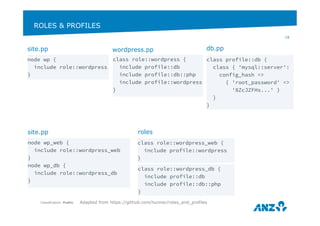
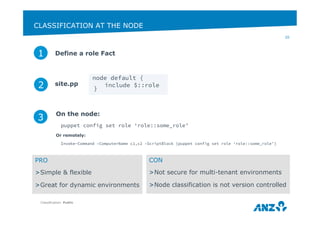
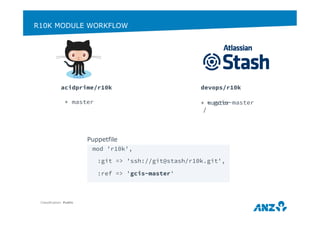
This document discusses ANZ GCIS's journey towards adopting DevOps practices like Puppet configuration management. It describes their initial challenges around managing dependencies and infrastructure growth. Their approach involved adopting roles and profiles in Puppet, using r10k and Hiera for configuration, and packaging tools like Chocolatey. Key lessons included using Puppet to manage Puppet and storing sensitive data securely in Hiera. They have now integrated several monitoring and automation tools through Puppet and improved their testing workflows.










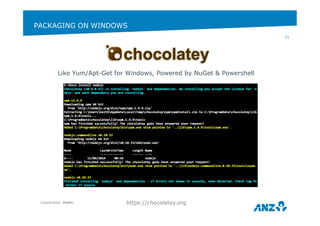
![PACKAGING ON WINDOWS
$chocolatey_package_list = [
]
package { $chocolatey_package_list:
}
Classification: Public
22
Chocolatey Package Provider for Puppet:
'powershell4',
'DotNet4.5',
'git.install',
ensure => installed,
provider => 'chocolatey',
https://forge.puppetlabs.com/rismoney/chocolatey](https://image.slidesharecdn.com/puppetcamptalk-final1-141119133142-conversion-gate02/85/Puppet-Camp-Melbourne-2014-Puppet-and-a-DevOps-Journey-Beginner-22-320.jpg)

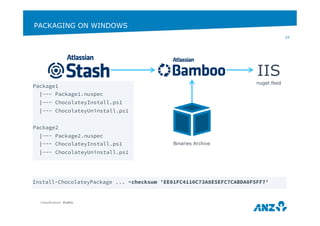



![USE PUPPET TO MANAGE PUPPET
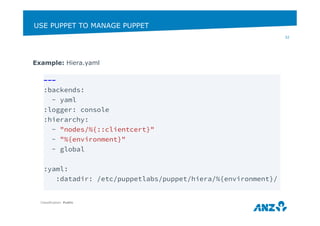
Example: Hiera.yaml via Puppet – https://forge.puppetlabs.com/hunner/hiera
Classification: Public
33
class { '::hiera':
backends => ['yaml’],
datadir => '/etc/puppetlabs/puppet/hiera/%{environment}/',
hierarchy => [
'servers/%{::clientcert}’,
'%{environment}’,
'global',
],
}](https://image.slidesharecdn.com/puppetcamptalk-final1-141119133142-conversion-gate02/85/Puppet-Camp-Melbourne-2014-Puppet-and-a-DevOps-Journey-Beginner-33-320.jpg)
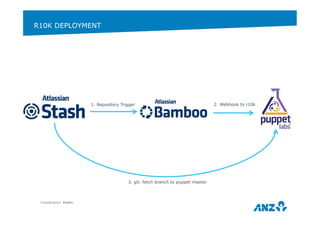
![USE PUPPET TO MANAGE PUPPET
Classification: Public
34
Example: Install & configure r10k - https://forge.puppetlabs.com/zack/r10k
class profile::puppet::master {
class { 'r10k':
version => '1.3.1',
sources => {
'puppet' => {
'remote' => 'ssh://git@stash/puppet.git',
'basedir' => "${::settings::confdir}/environments",
'prefix' => false,
},
'hiera' => {
'remote' => 'ssh://git@stash/hiera.git',
'basedir' => "${::settings::confdir}/hiera",
'prefix' => false,
},
},
purgedirs => ["${::settings::confdir}/environments", "${::settings::confdir}/hiera" ],
manage_modulepath => true,
modulepath => "${::settings::confdir}/environments/$environment/modules:${::settings::…
mcollective => true,
}
}](https://image.slidesharecdn.com/puppetcamptalk-final1-141119133142-conversion-gate02/85/Puppet-Camp-Melbourne-2014-Puppet-and-a-DevOps-Journey-Beginner-34-320.jpg)
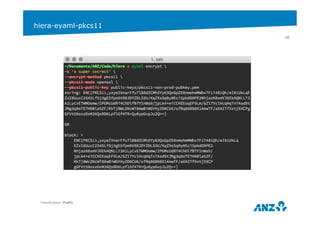
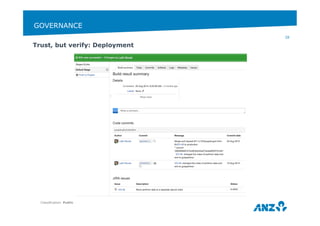
![STORING SENSITIVE INFORMATION IN HIERA
Hiera-eyaml: https://github.com/TomPoulton/hiera-eyaml
/etc/puppetlabs/puppet/hiera.yaml
Classification: Public
35
---
:backends:
- eyaml
:eyaml:
:datadir: /etc/puppet...
:extension: "yaml"
:pkcs7_private_key: "/etc/..."
:pkcs7_public_key: "/etc/..."
/etc/puppetlabs/puppet/hiera/prod.yaml
---
profile::my_app::app_secret: >
ENC[PKCS7,MIIBiQYJKoZIhvcNAQcDoII
BejCCAXYCAQAxggEhMIIBHQIBADAFMAAC
AQEwDQYJKoZIhvcNAQEBBQAEggEAWLZRf
TW8YxvCOf4akyxYdBV5m2AdF+HF85Cz
lqw8qQNKW9oMqktgyaoNzOMGufr0rp2BO
zrdQ+/z3bmQ9HPK2qqJ1k/n/jX9
D5lf5ReEKj5VnhnLblbLyI5HCfLbR...]](https://image.slidesharecdn.com/puppetcamptalk-final1-141119133142-conversion-gate02/85/Puppet-Camp-Melbourne-2014-Puppet-and-a-DevOps-Journey-Beginner-35-320.jpg)
![STORING SENSITIVE INFORMATION IN HIERA
/etc/puppetlabs/puppet/hiera.yaml
Classification: Public
36
0000 +
---
:backends:
- eyaml
:eyaml:
:datadir: /etc/puppet...
:extension: "yaml"
:pkcs7_private_key: "/etc/..."
:pkcs7_public_key: "/etc/..."
/etc/puppetlabs/puppet/hiera/prod.yaml
---
profile::my_app::app_secret: >
ENC[PKCS7,MIIBiQYJKoZIhvcNAQcDoII
BejCCAXYCAQAxggEhMIIBHQIBADAFMAAC
AQEwDQYJKoZIhvcNAQEBBQAEggEAWLZRf
TW8YxvCOf4akyxYdBV5m2AdF+HF85Cz
lqw8qQNKW9oMqktgyaoNzOMGufr0rp2BO
zrdQ+/z3bmQ9HPK2qqJ1k/n/jX9
D5lf5ReEKj5VnhnLblbLyI5HCfLbR...]](https://image.slidesharecdn.com/puppetcamptalk-final1-141119133142-conversion-gate02/85/Puppet-Camp-Melbourne-2014-Puppet-and-a-DevOps-Journey-Beginner-36-320.jpg)