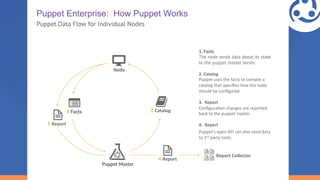
The document discusses how Puppet can be used for security and auditing systems through its state-based configuration, centralized management, and strict master-agent relationship. It describes Puppet's data flow and how it uses facts collected from nodes to compile catalogs specifying how nodes should be configured. It also discusses Puppet's secure workflows using techniques like pull requests, automated testing, Puppet Lint, and Rspec Puppet. Simulation mode and modeling application security is also covered, along with resources for security best practices and implementation guides.