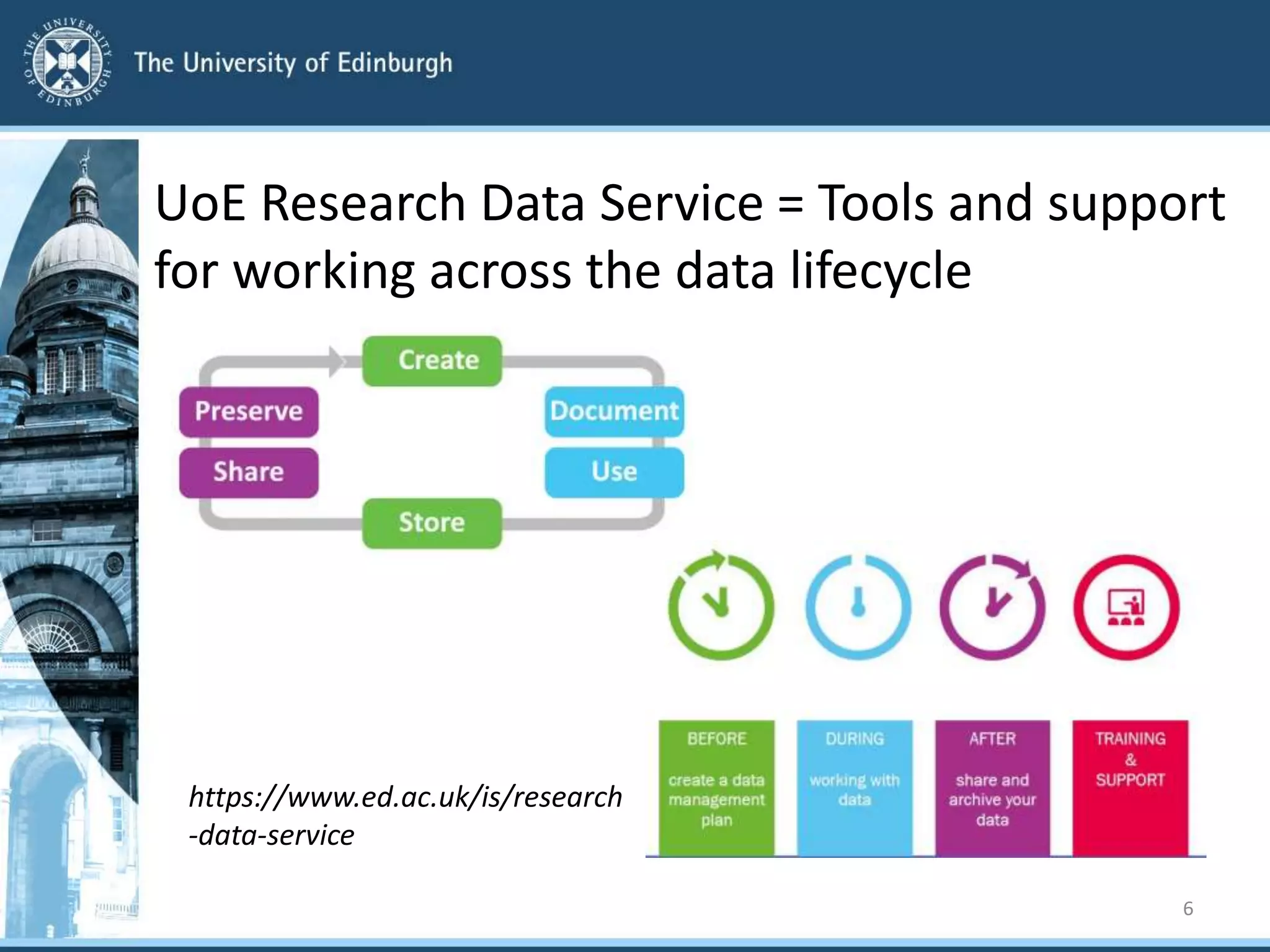
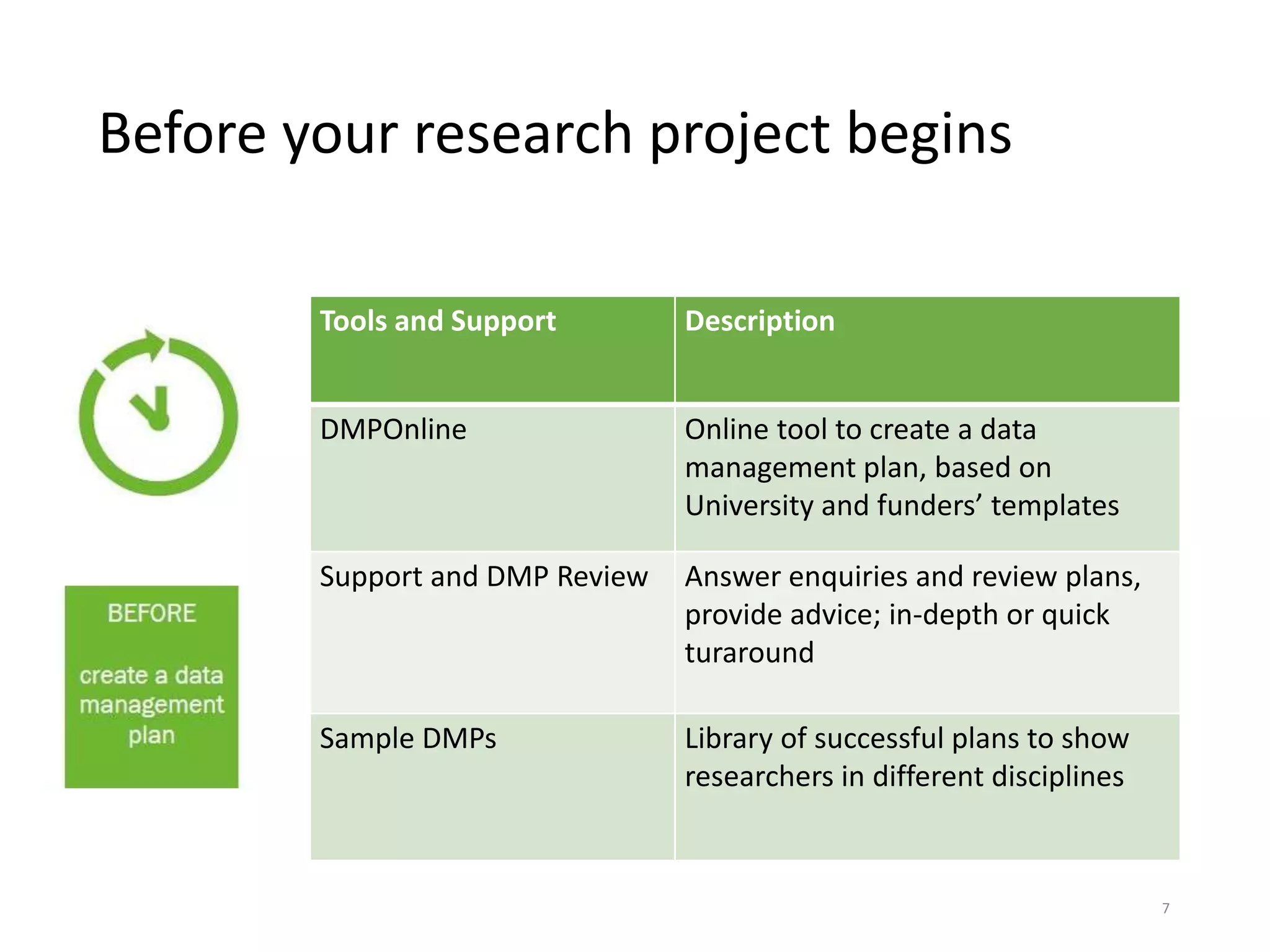
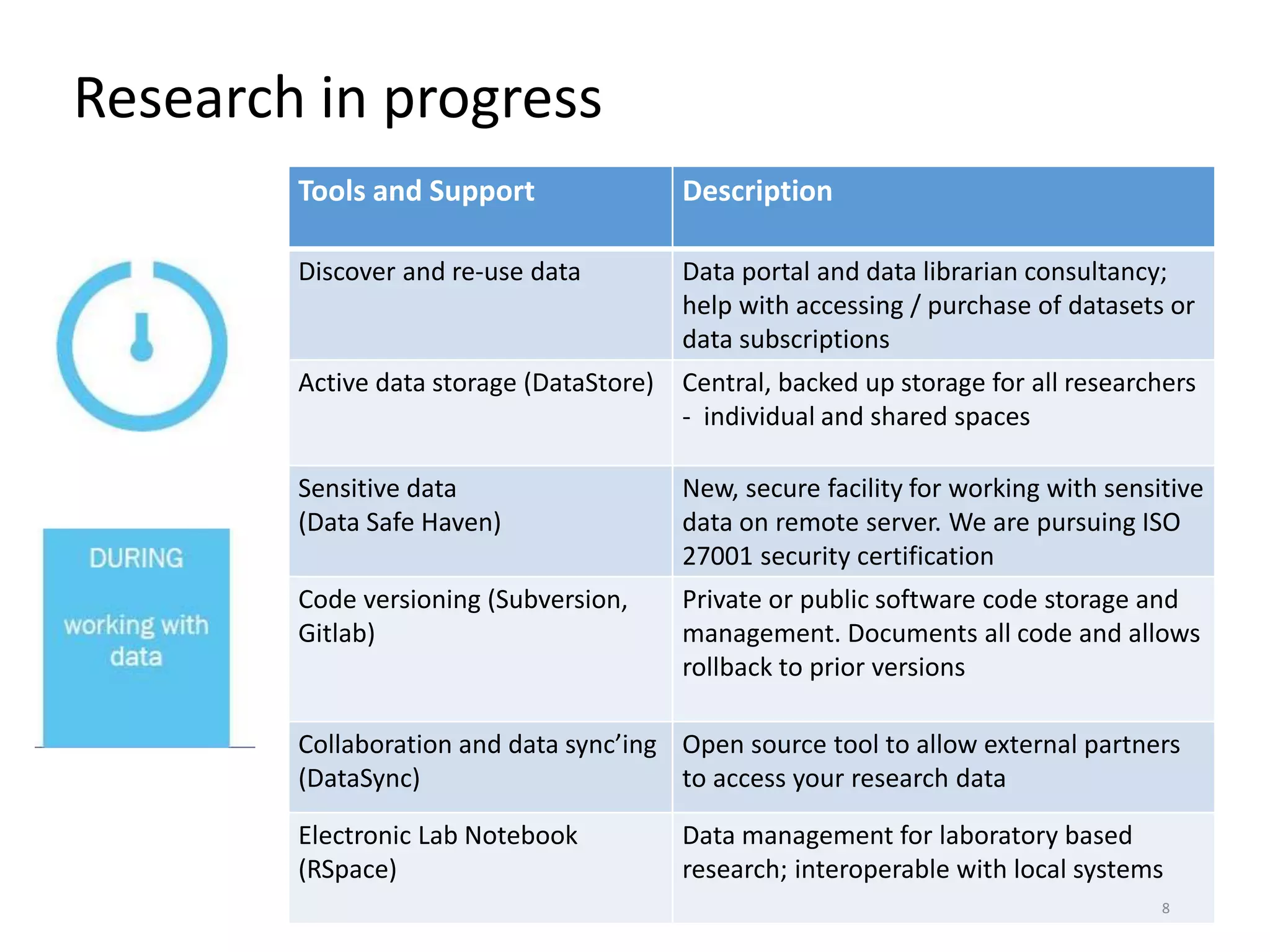
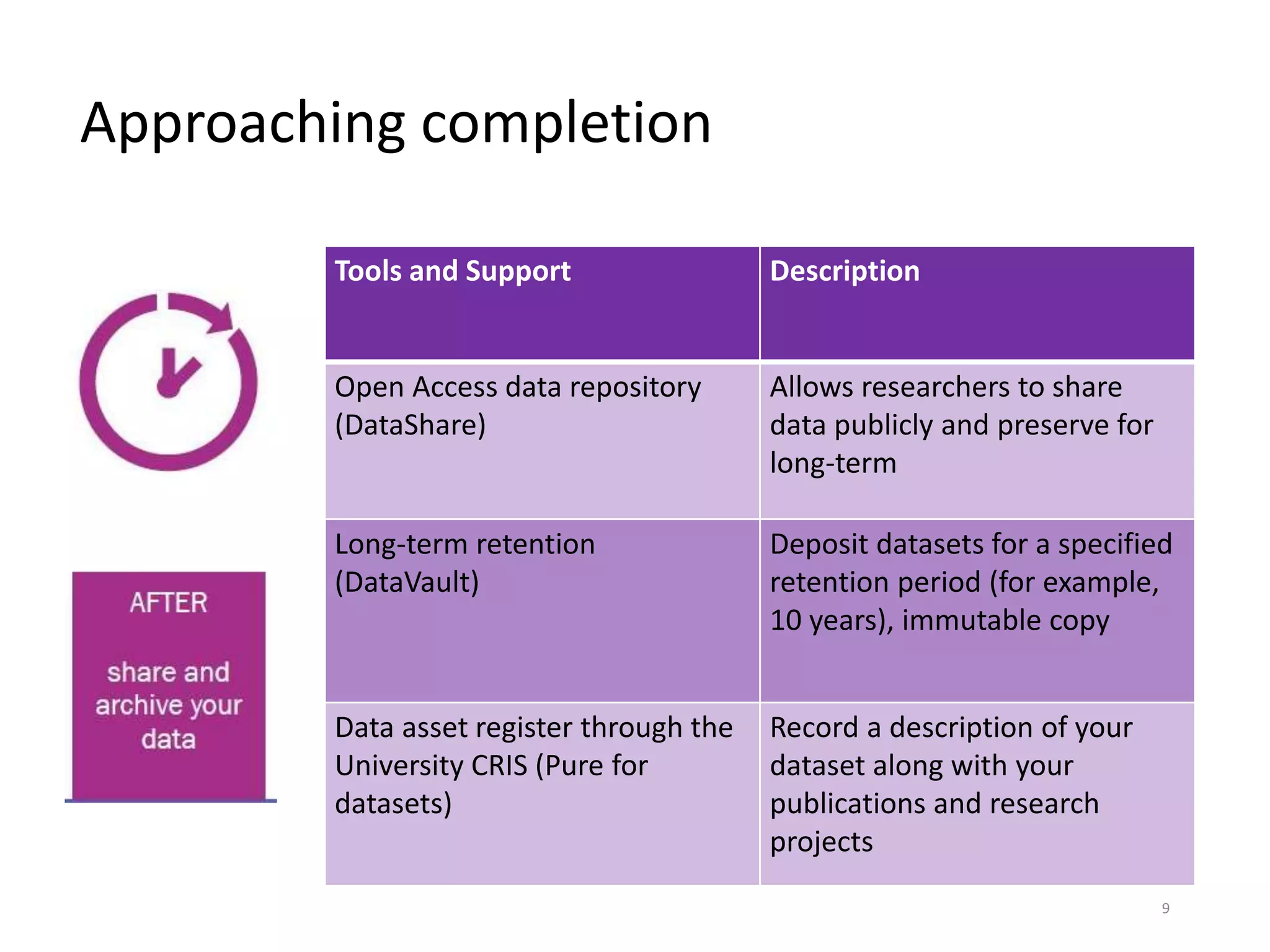
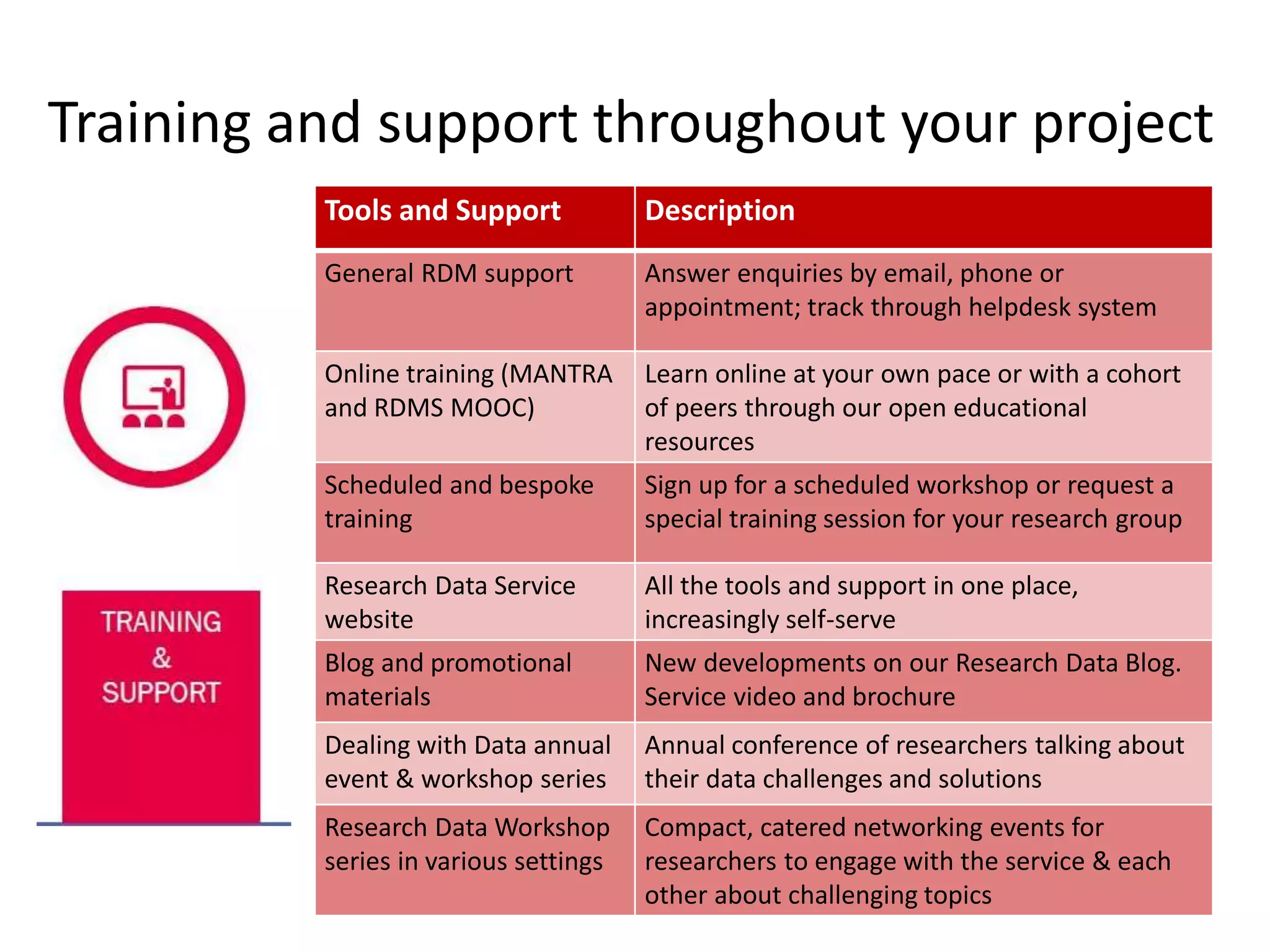
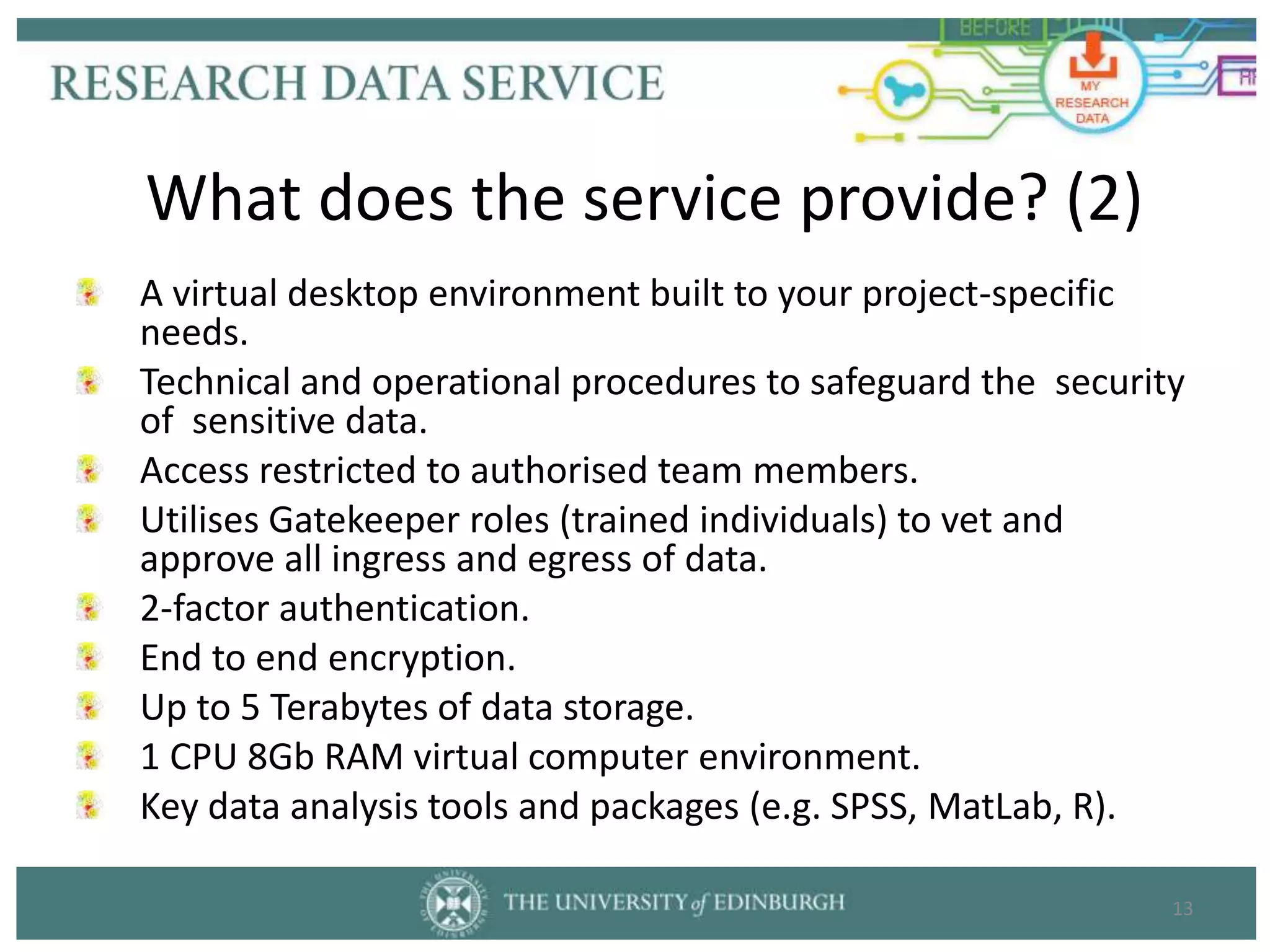
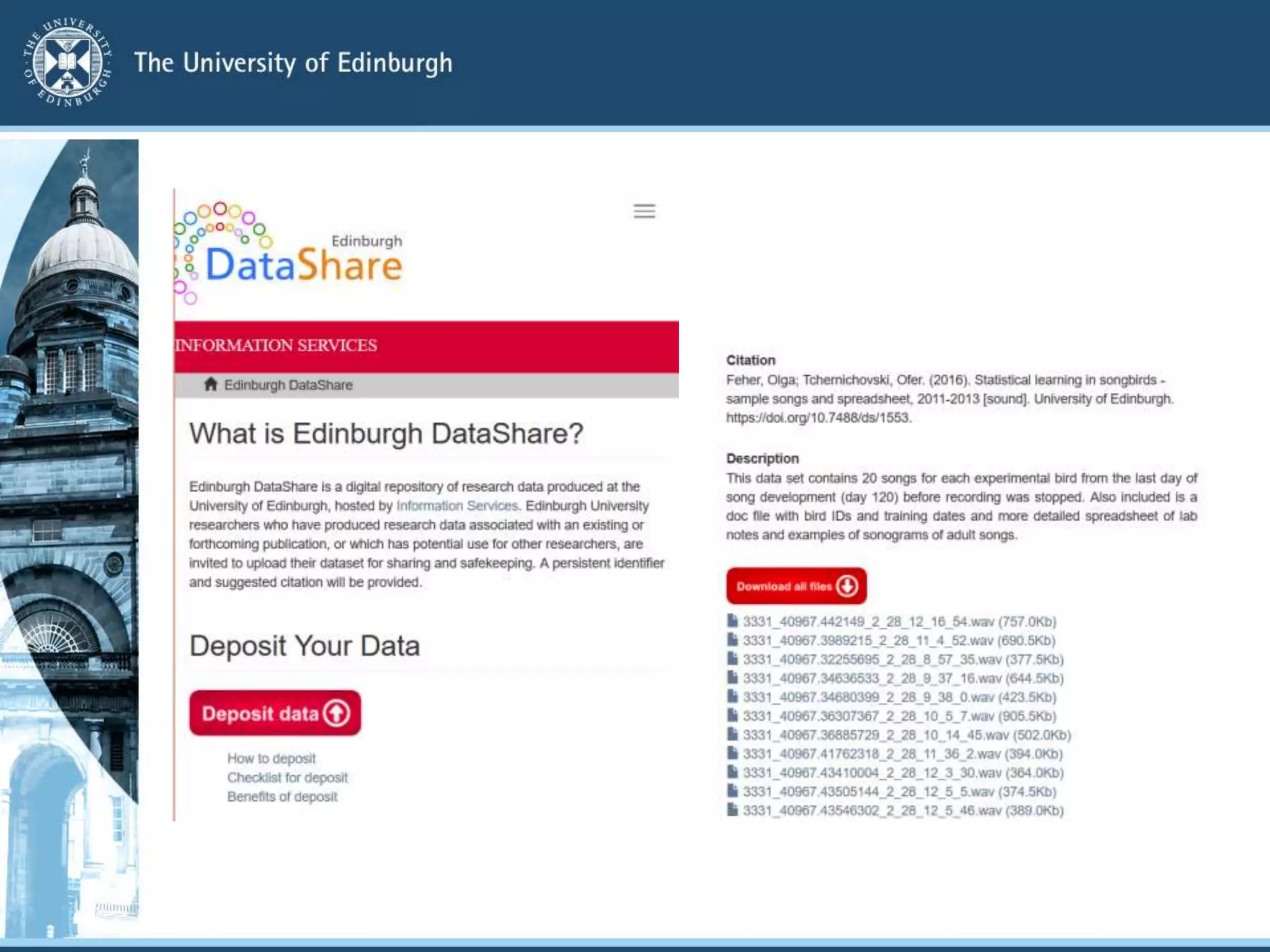
The University of Edinburgh provides support and services to help researchers with good data governance. This includes a research data policy, research data service with various tools across the data lifecycle, and a data safe haven for sensitive data. The research data service offers centralized storage, version control, collaboration tools, and repositories for sharing data openly or long-term retention. Training and outreach aim to educate researchers on topics like data management plans, sensitive data, and GDPR compliance.