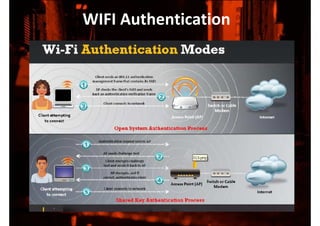
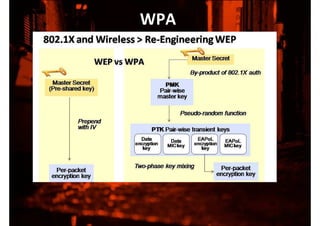
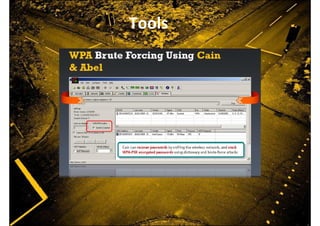
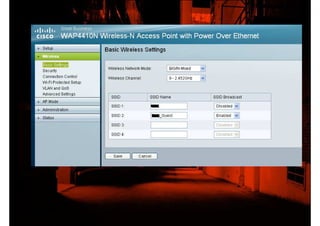
This document discusses protecting wireless networks from hacking. It describes how wireless networks are less secure than wired networks because wireless signals can be easily intercepted. It explains different types of wireless networks and authentication methods like WEP, WPA, and WPA2. It provides details on how to attack a wireless network by scanning for access points, collecting initialization vectors, and using cracking tools. Finally, it recommends using the strongest encryption like WPA2 and changing keys frequently to better secure wireless networks.