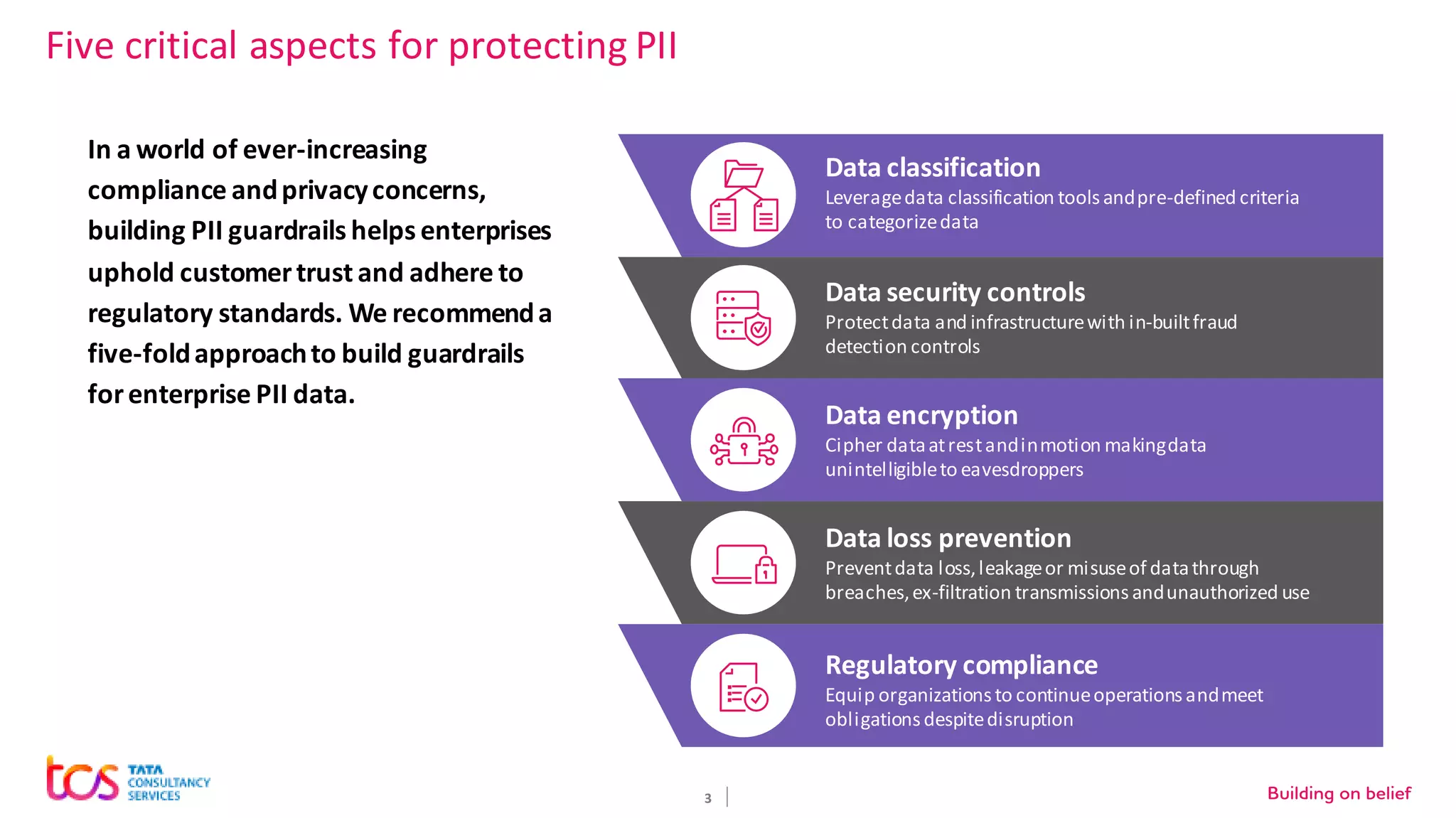
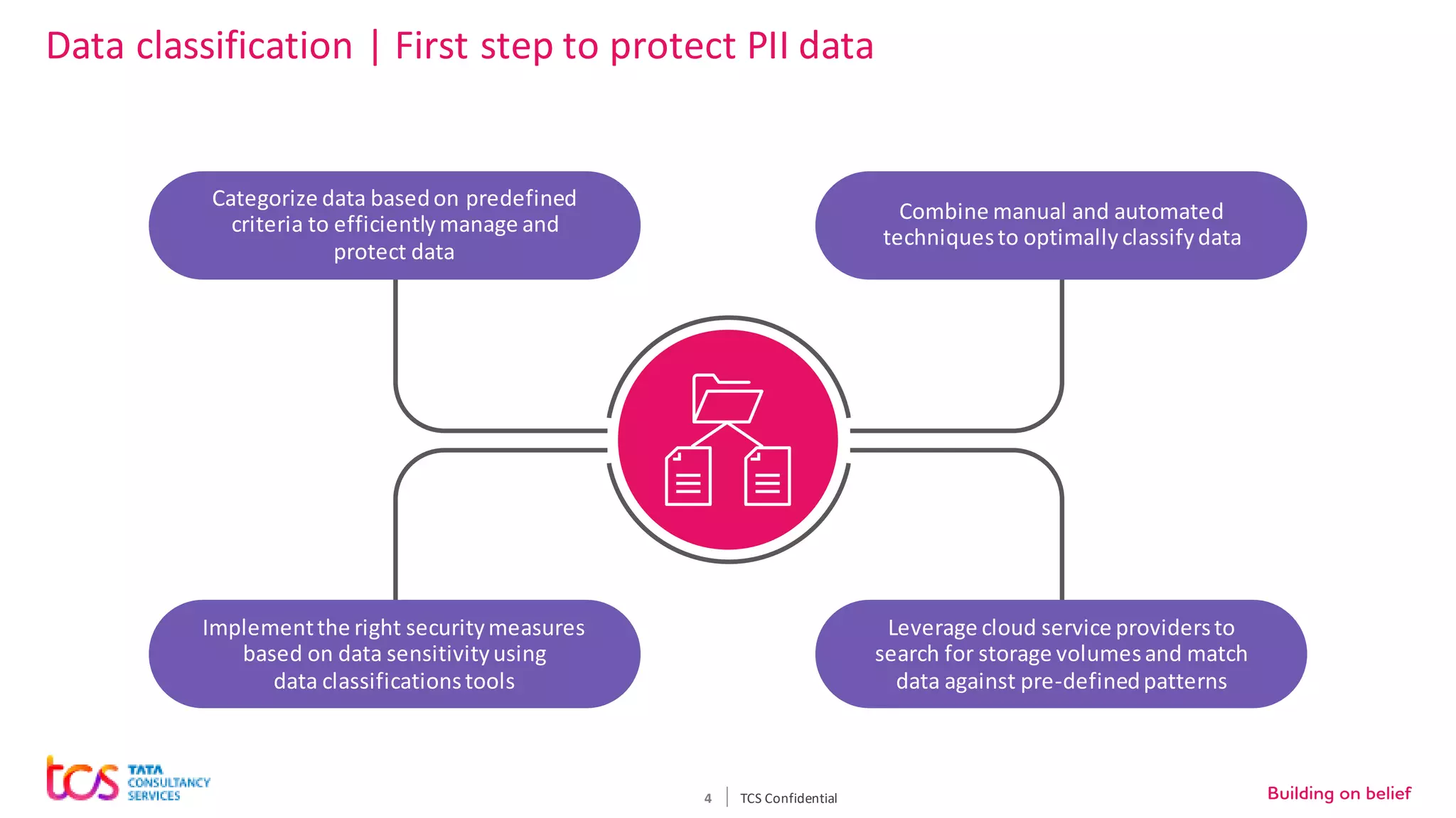
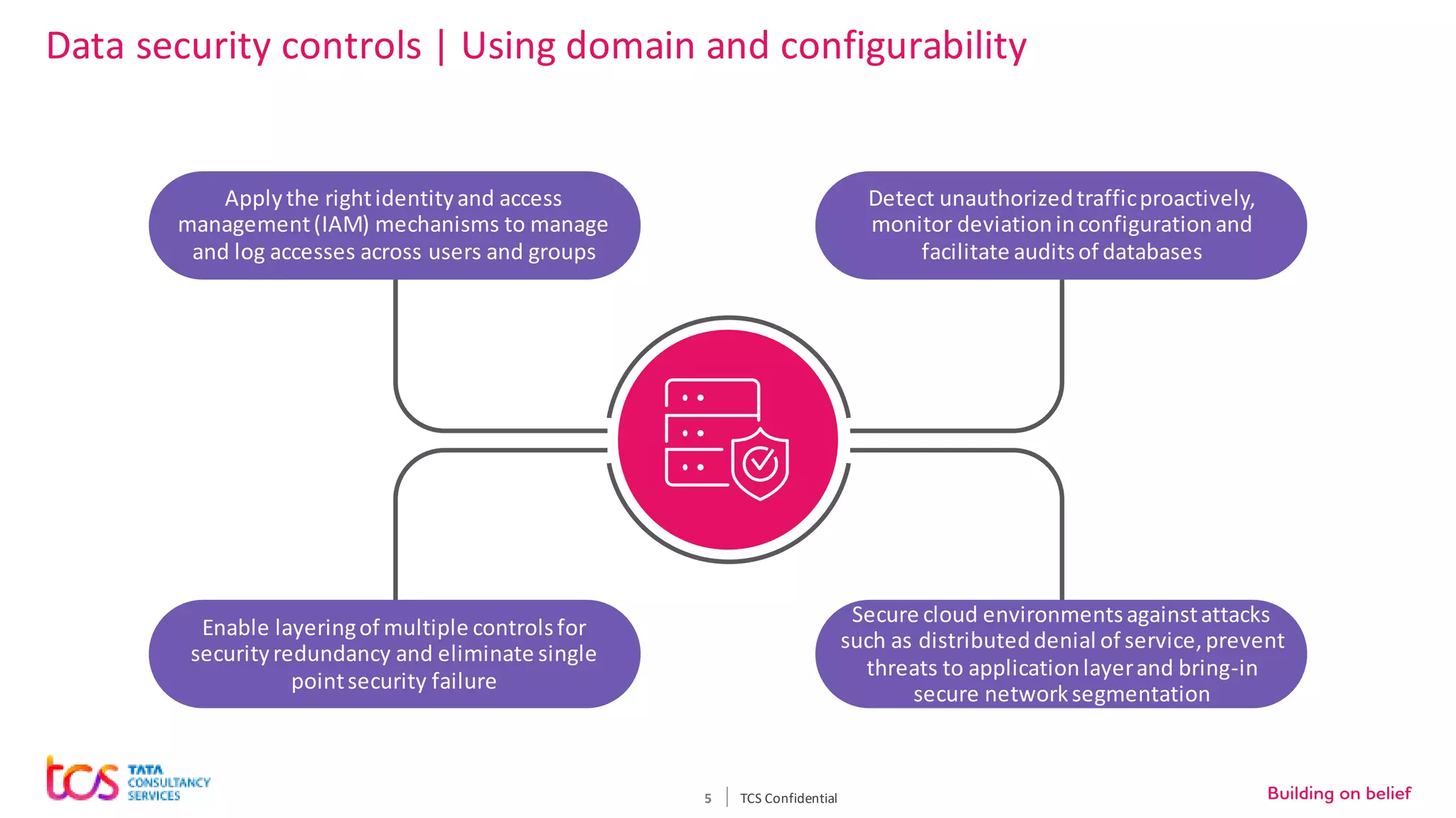
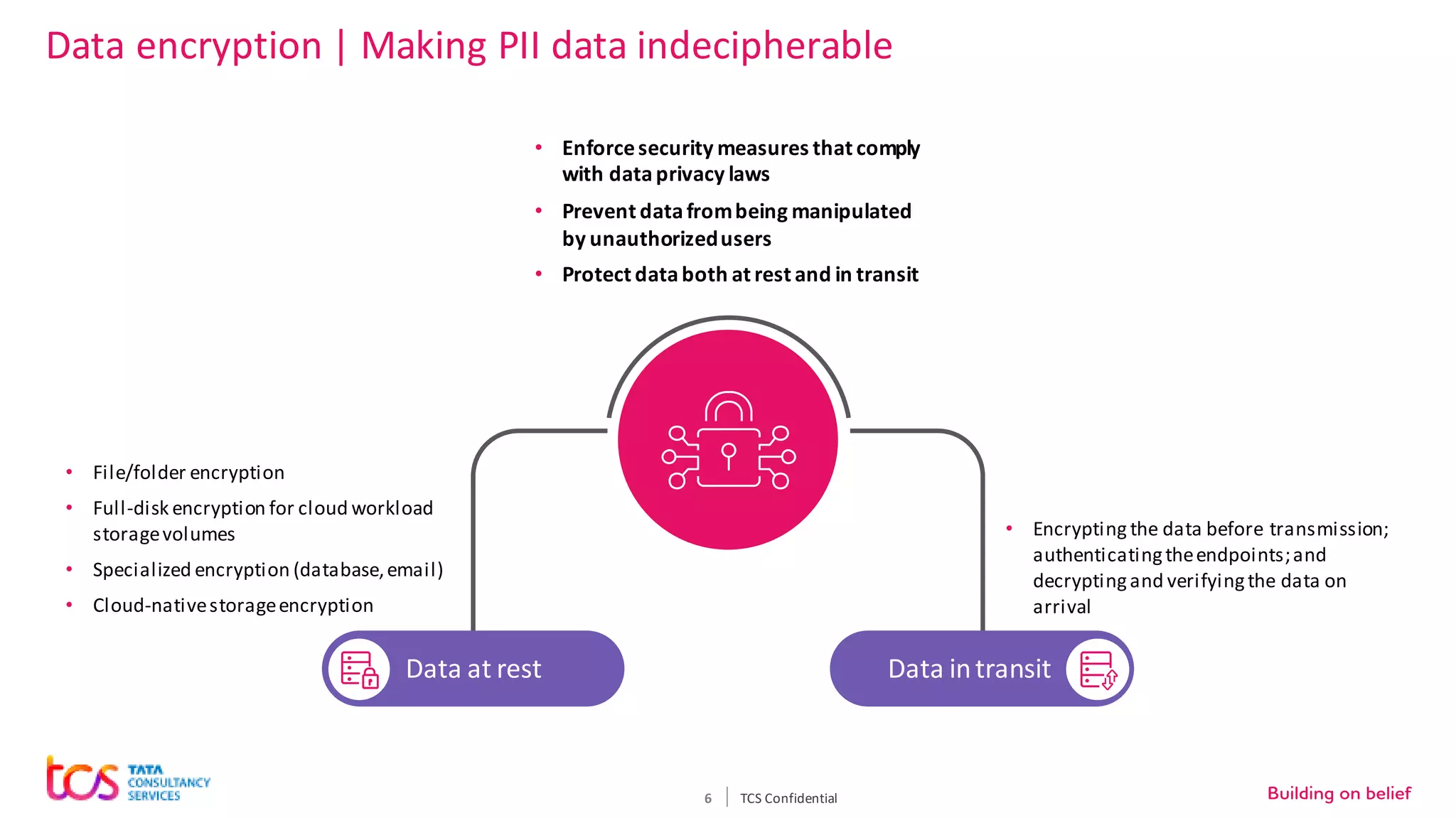
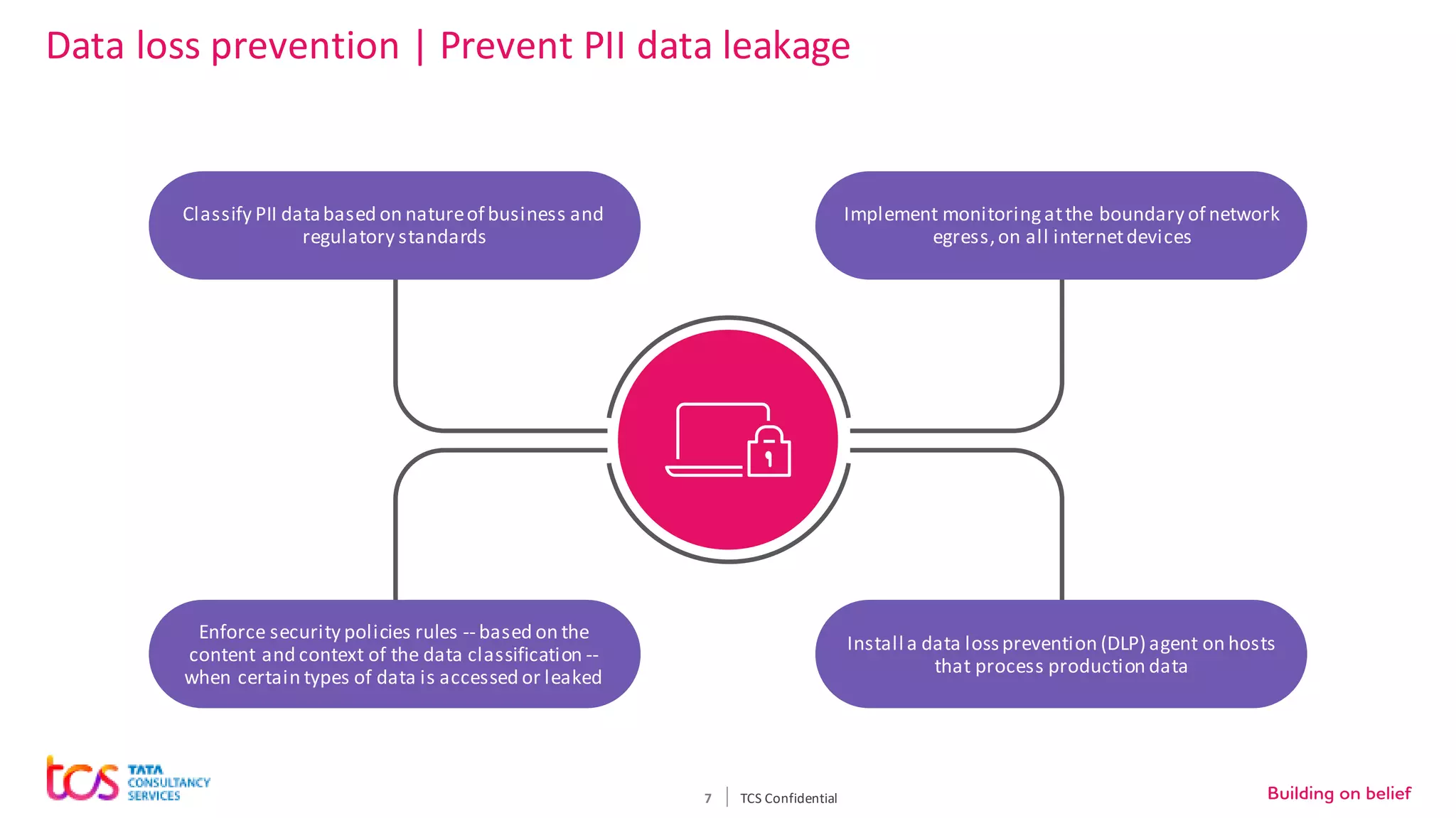
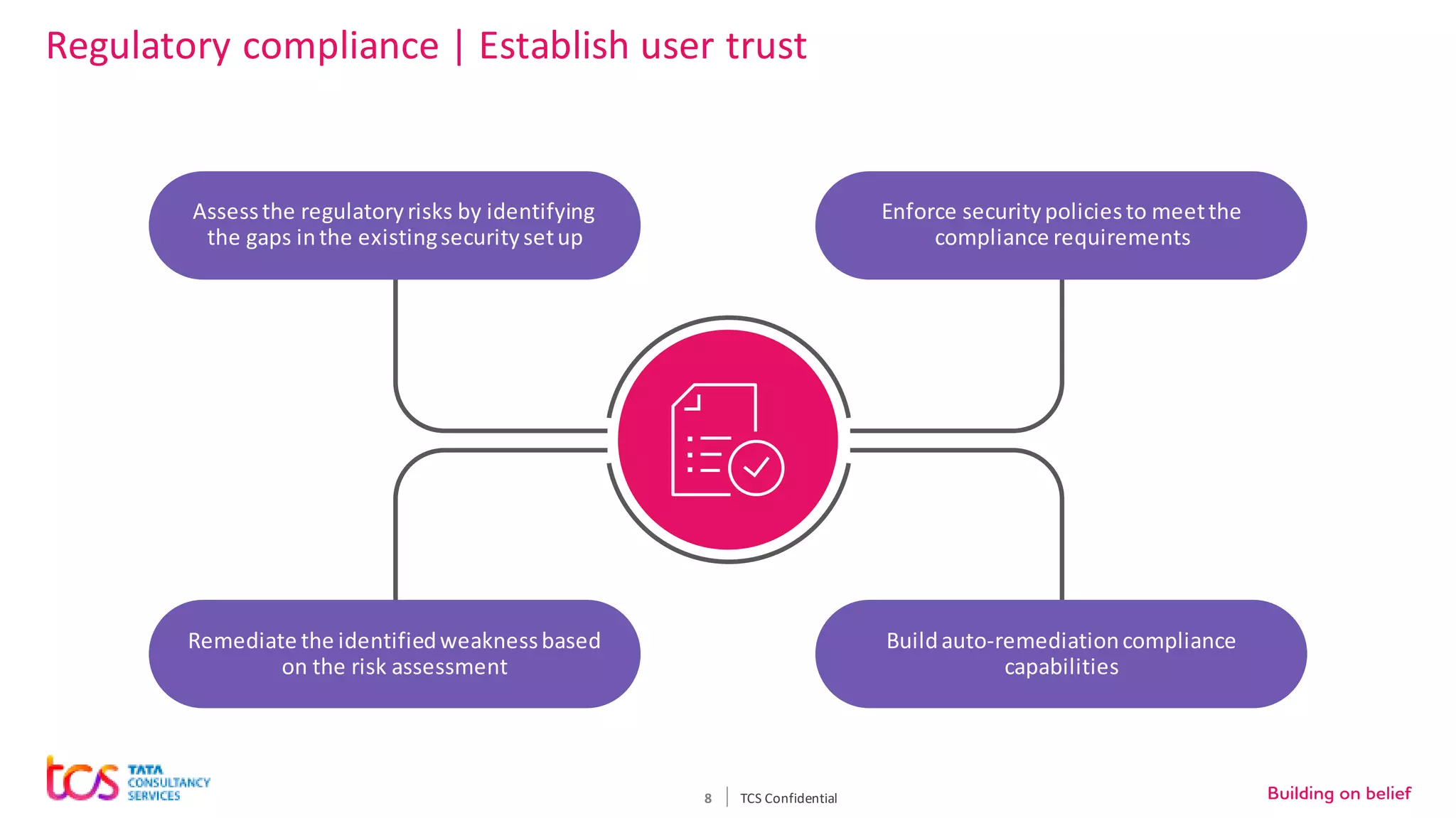
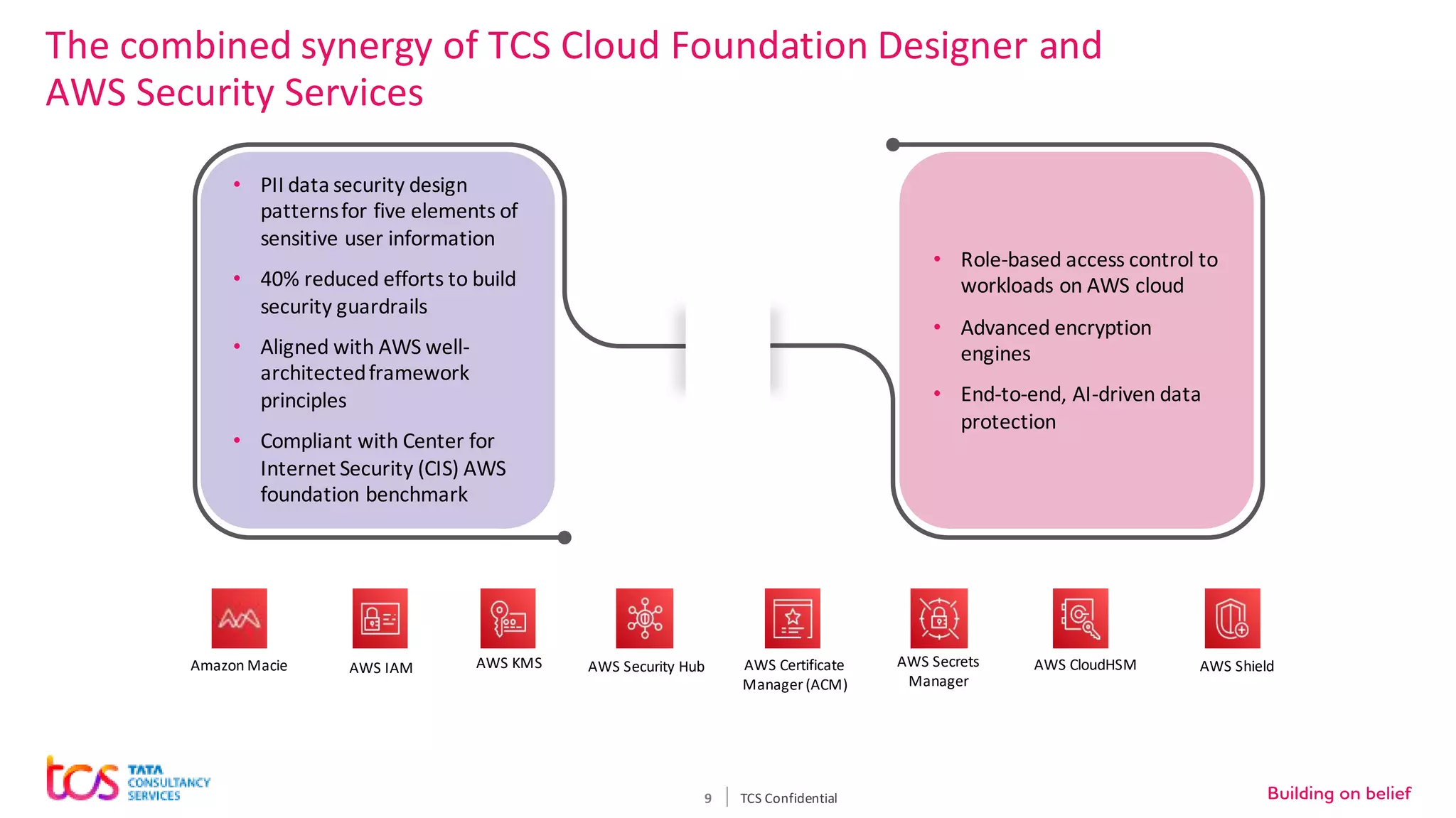
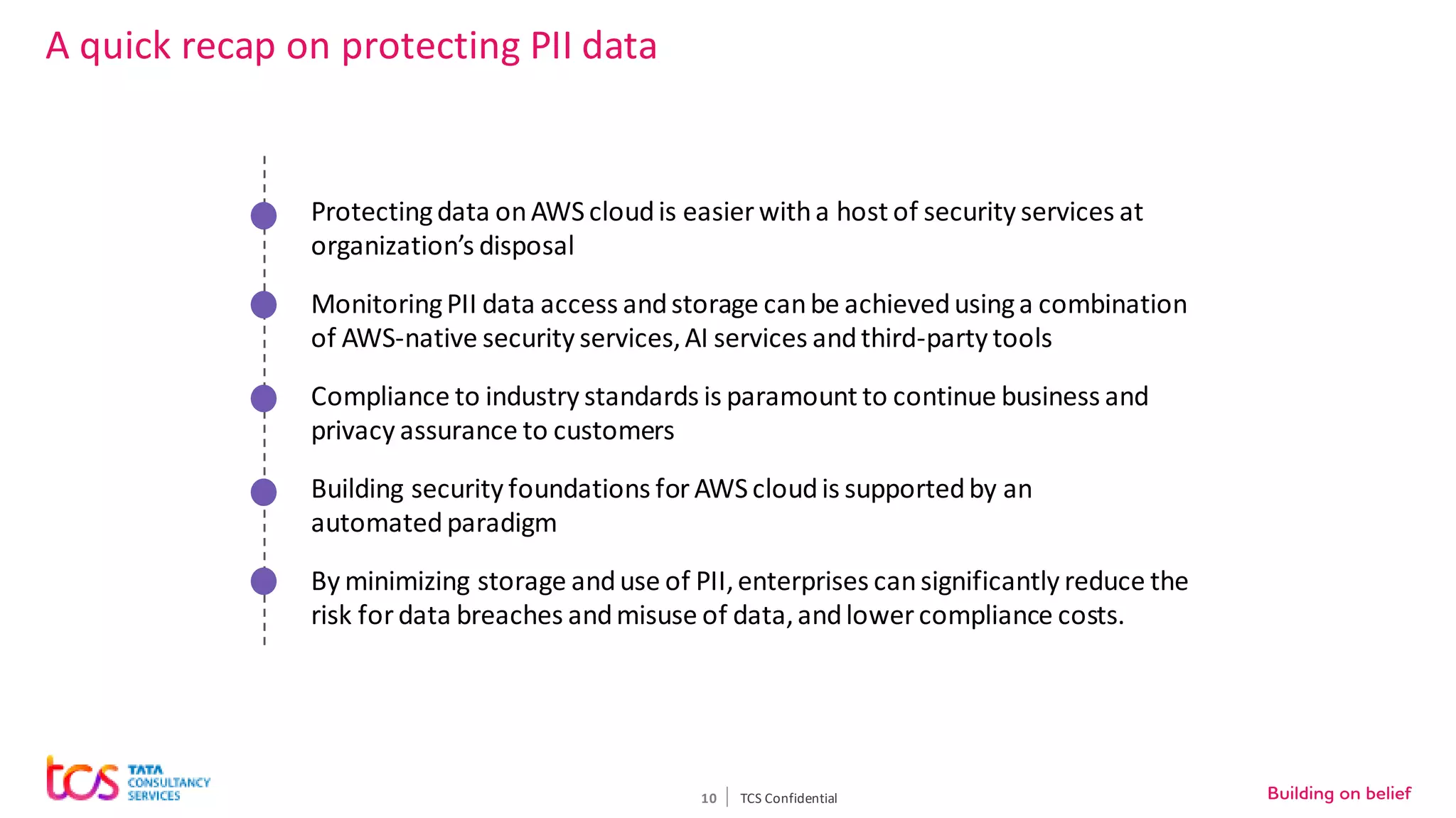
Personal identifiable information (PII) data breaches have risen significantly, posing challenges for enterprises storing PII on cloud. There are five critical aspects to protecting PII data: data classification, security controls, encryption, loss prevention, and regulatory compliance. TCS recommends classifying data using tools and predefined criteria. Then applying security controls like access management and monitoring. Data should be encrypted at rest and in transit. Loss prevention controls like monitoring network traffic can prevent data leakage. Assessing regulatory risks and enforcing policies helps ensure compliance. Combining TCS and AWS security services provides a comprehensive approach to protecting sensitive user data on cloud.