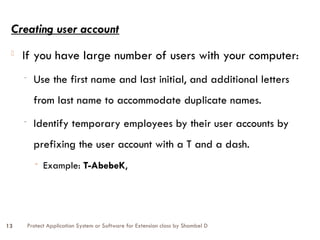
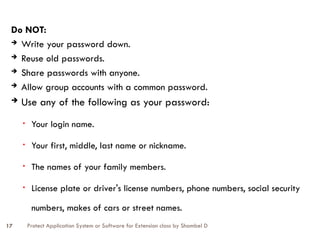
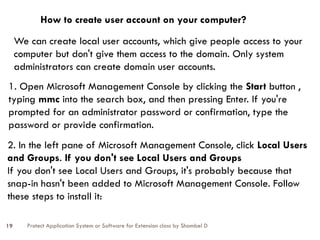
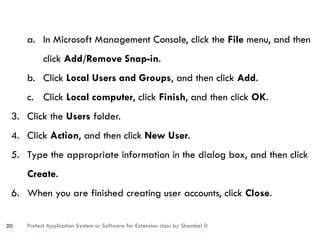
The document discusses the protection of application systems and software, focusing on user accounts, password guidelines, and various types of destructive software such as viruses and malware. It outlines the importance of user account management and the creation of strong passwords to safeguard computers against unauthorized access and other threats. Additionally, it explains different types of destructive software and offers strategies for virus protection and system security.








![Protect Application System or Software for Extension class by Shambel D
12
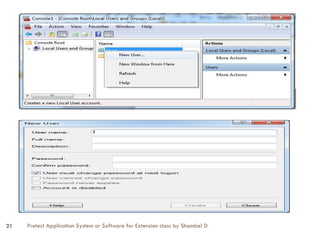
Rules for Creating User Account
- User account Name must be unique when you create
user account.
- Local user account name must be unique when you
create local user account on the computer.
- User logon name can contain up to 20 uppercase and
lowercase characters except special characters like
“/ []:,;!=+*?<>”](https://image.slidesharecdn.com/protectapplication-extensionclass044932-250101202104-1cc58362/85/protect-Application-Extension-Class_044932-pptx-12-320.jpg)