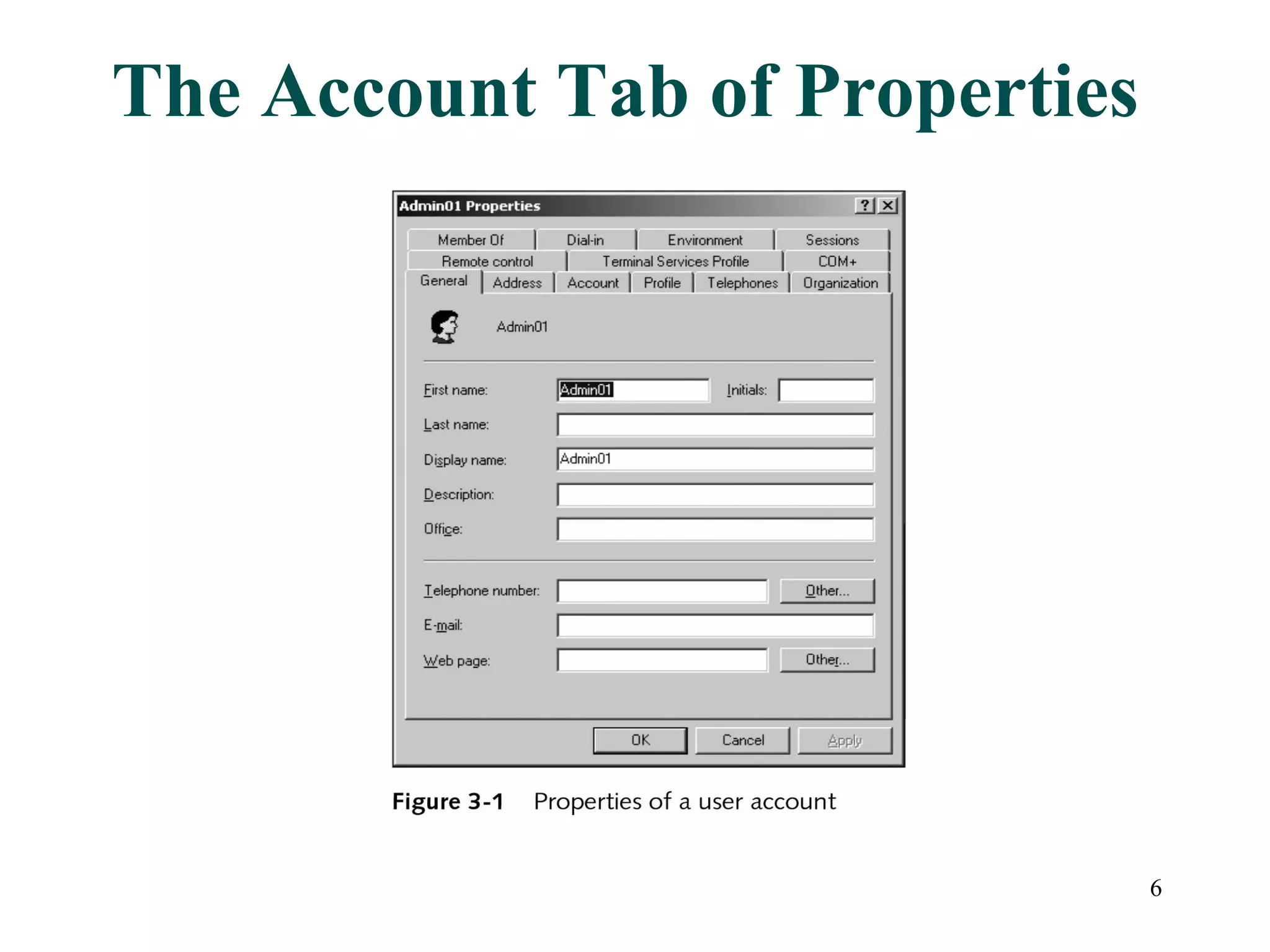
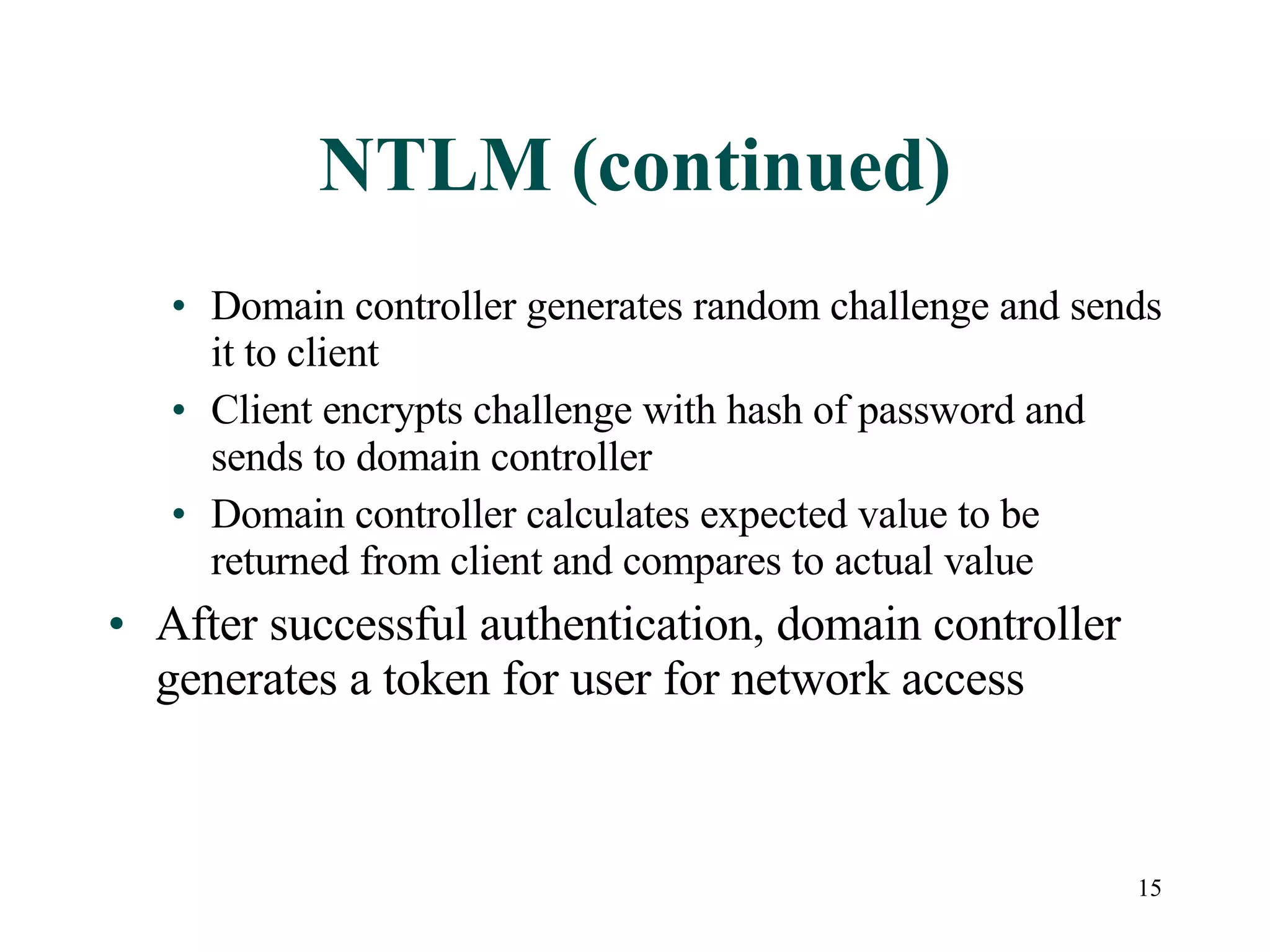
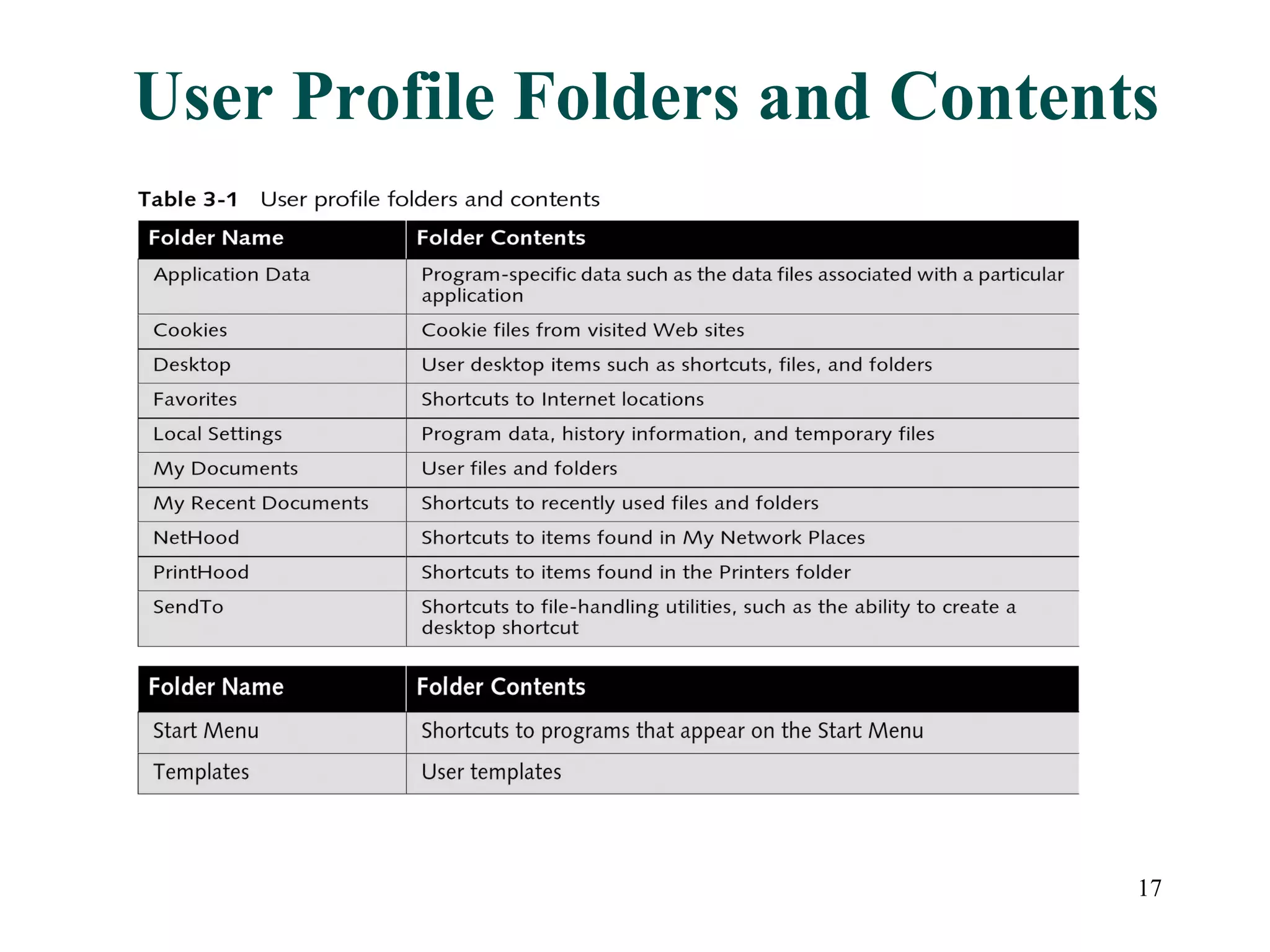
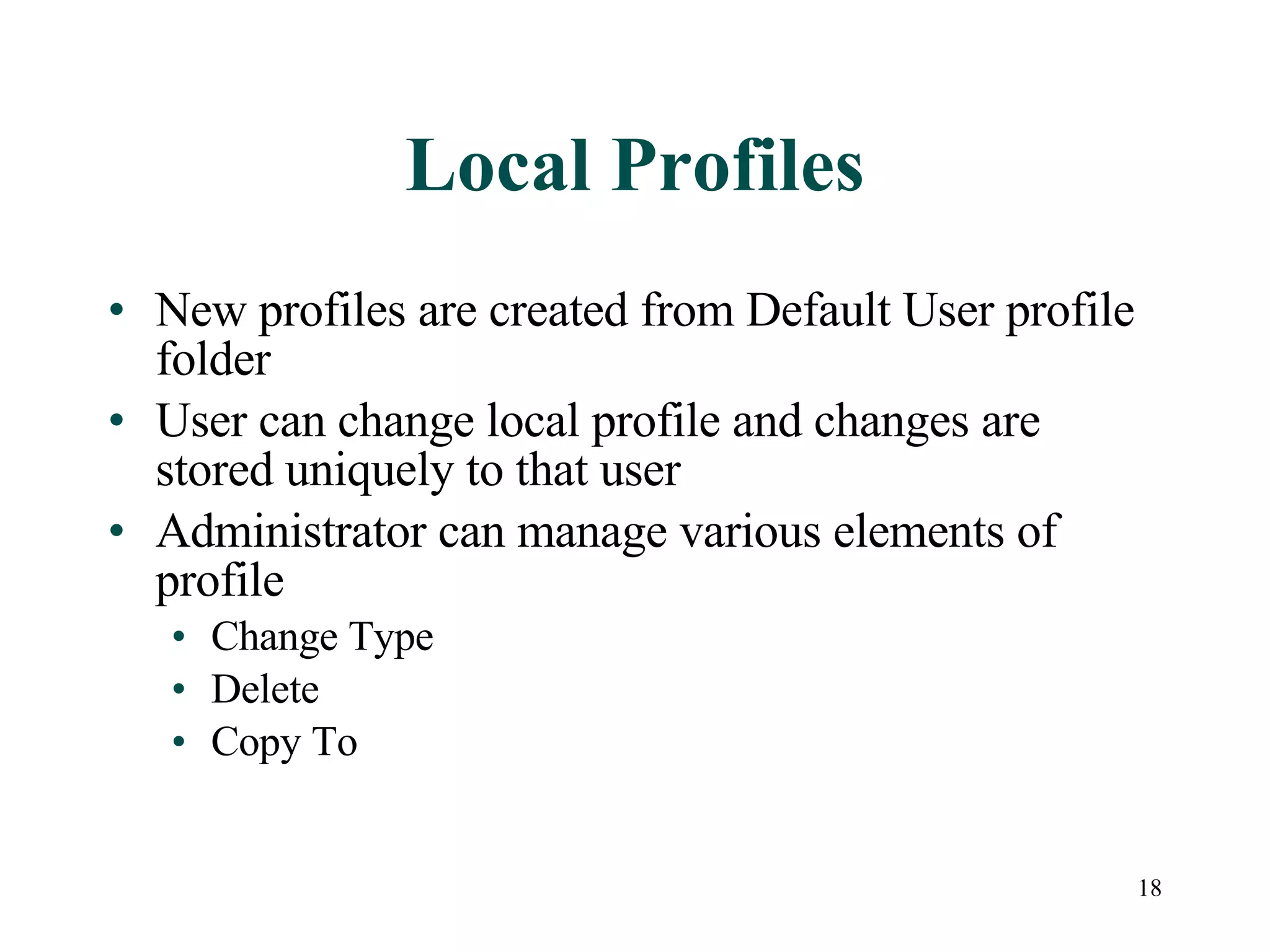
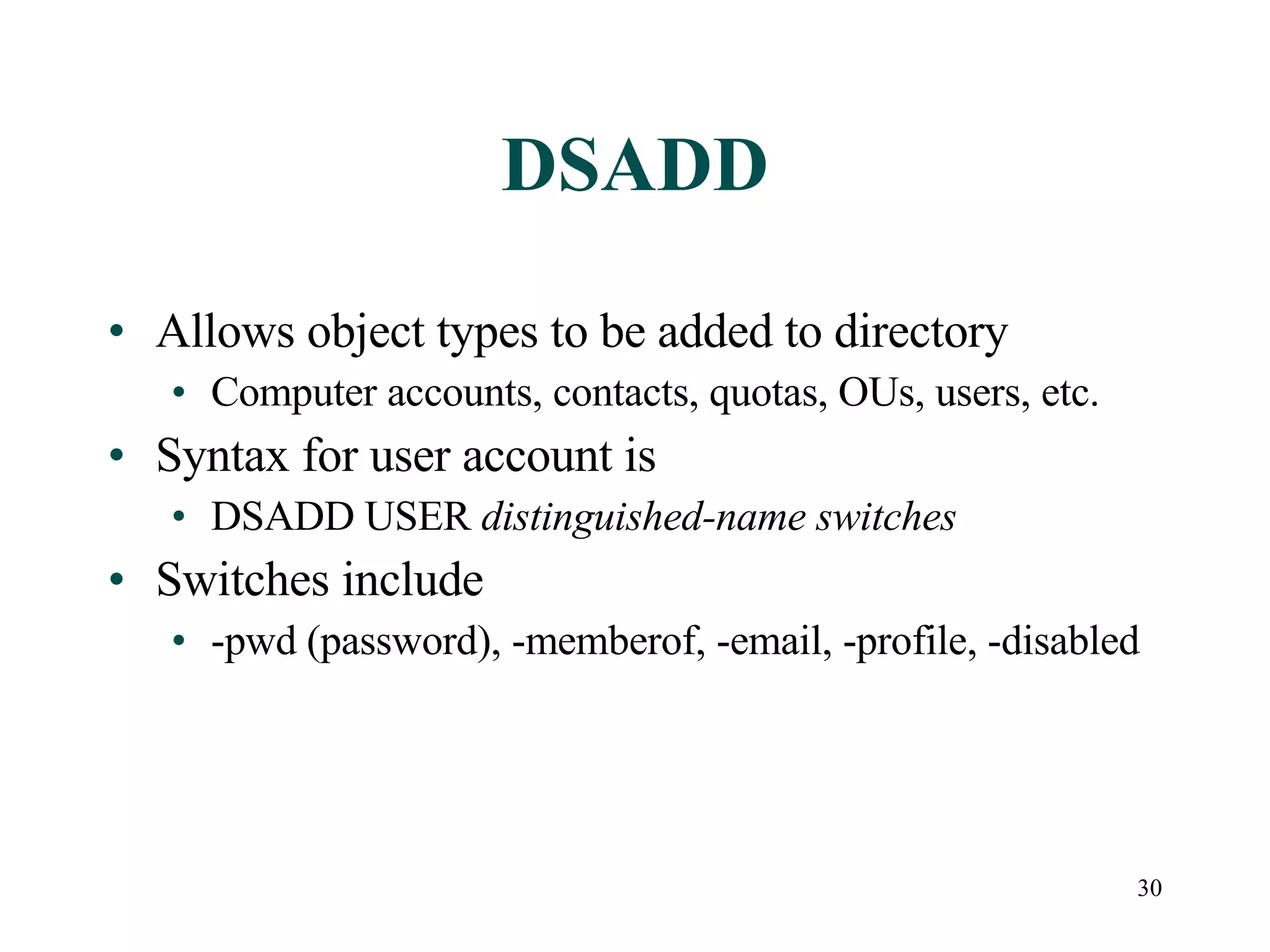
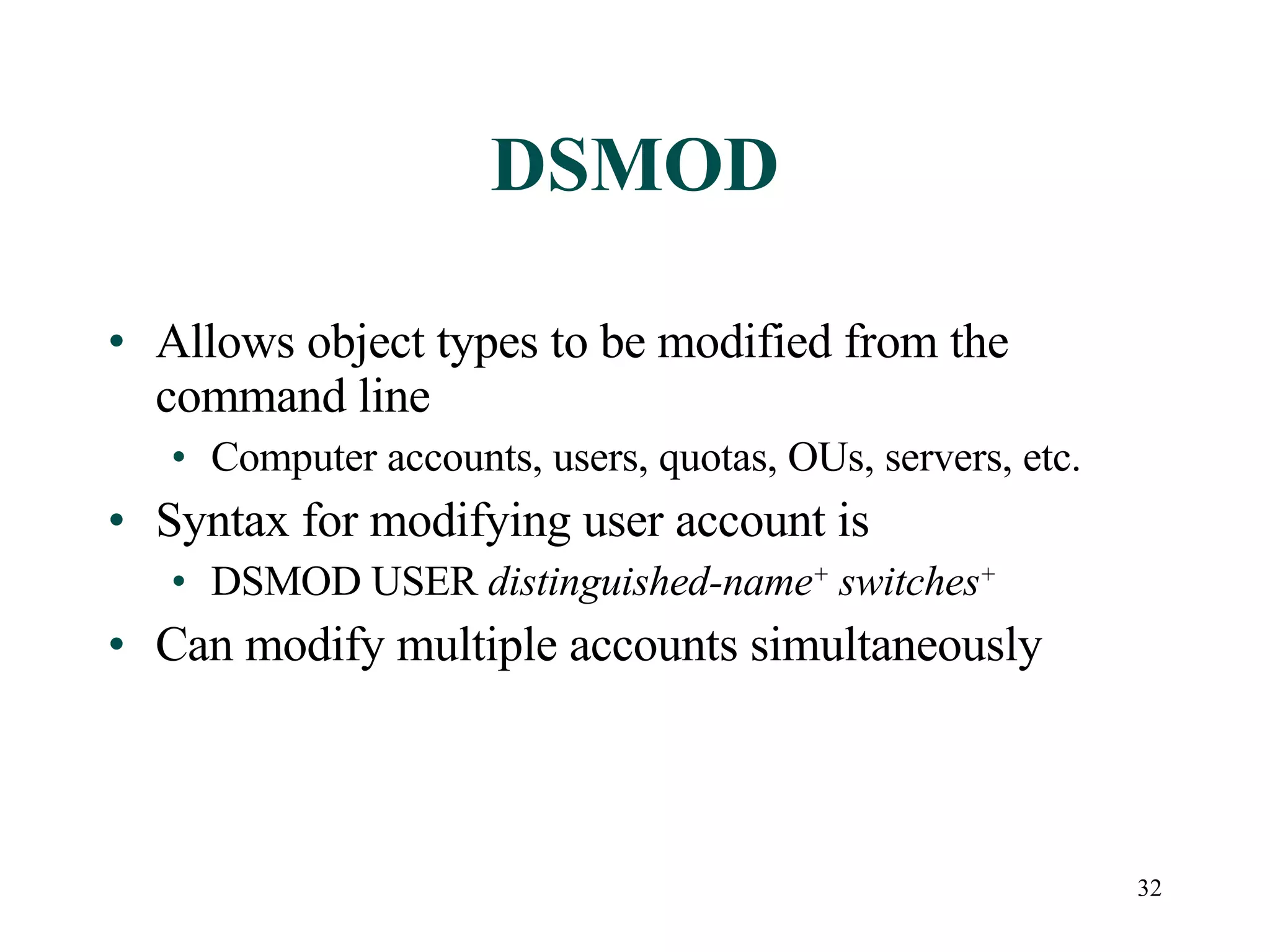
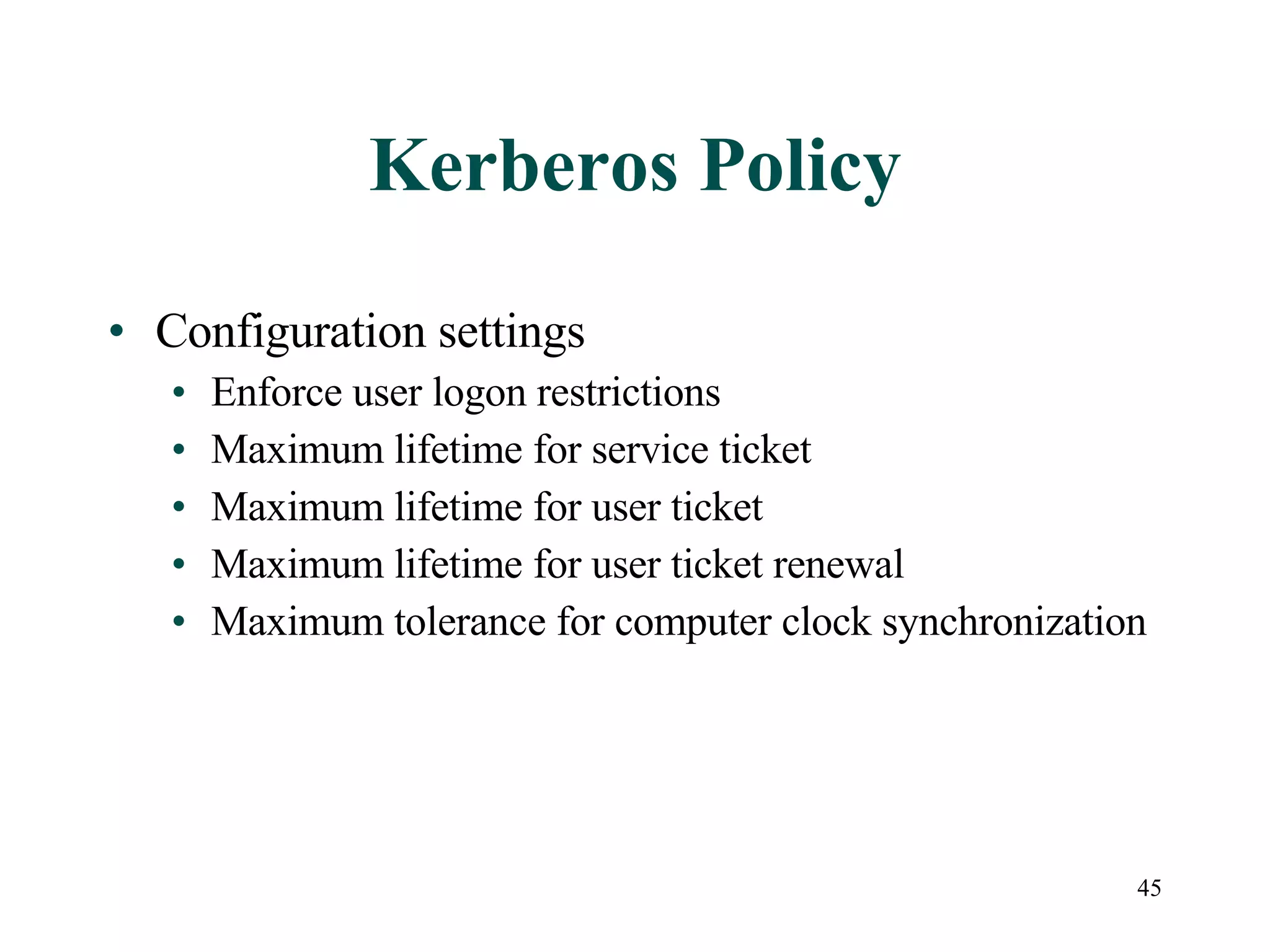
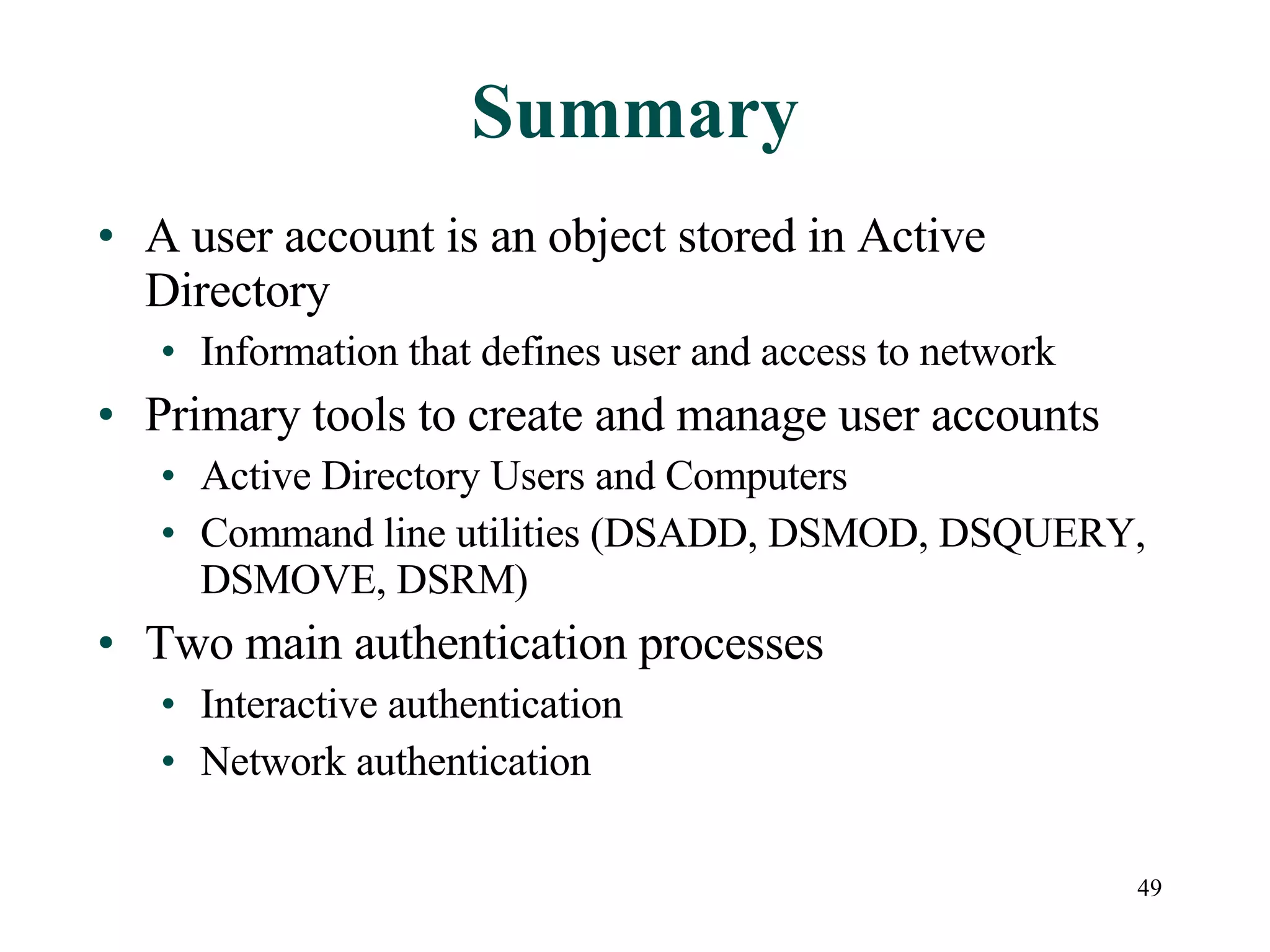
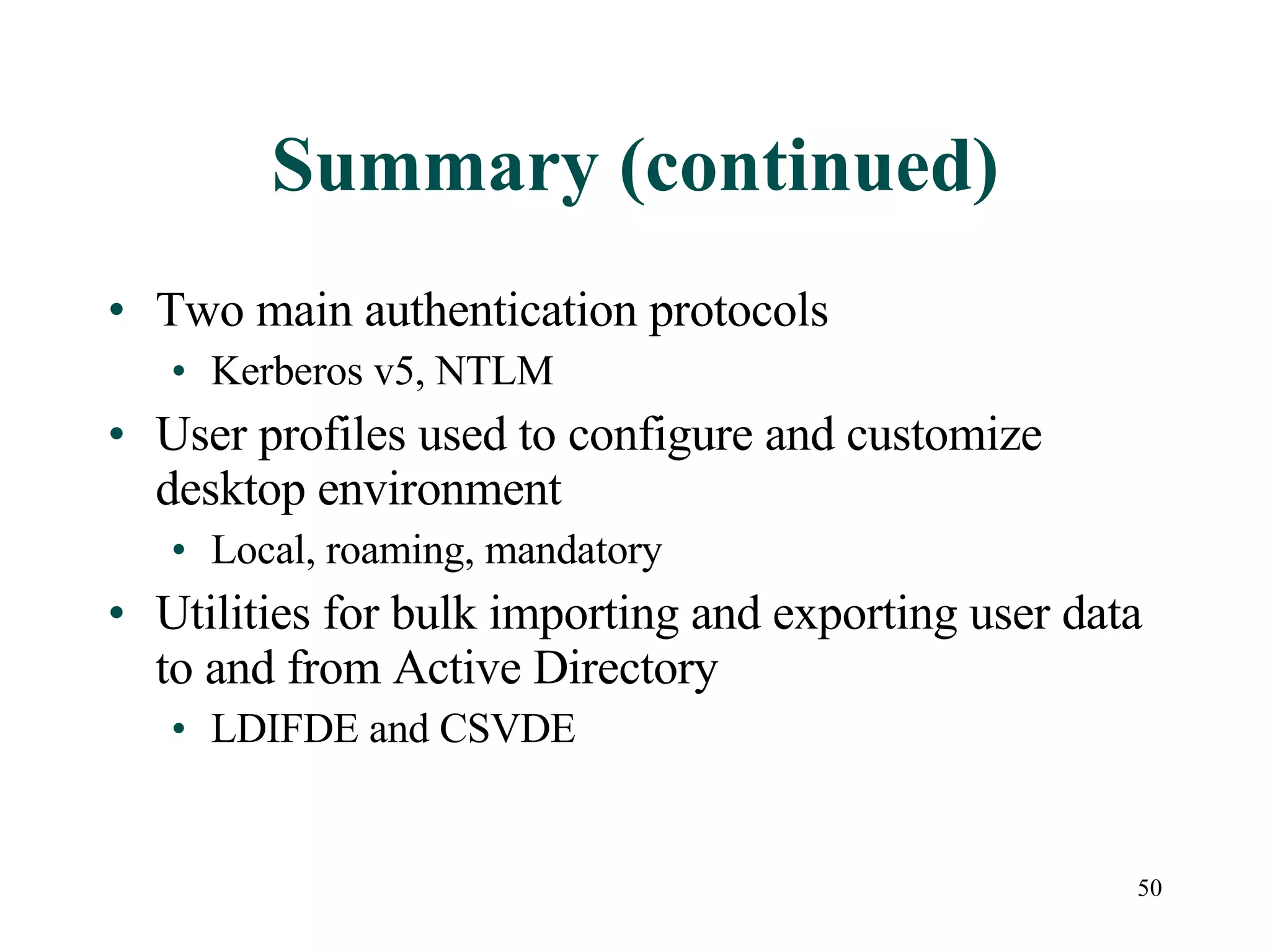
User accounts in Active Directory represent users and their access to network resources. The main tools for managing user accounts are Active Directory Users and Computers and command line utilities like DSADD and DSMOD. User authentication involves validating a user's identity through interactive or network authentication using protocols like Kerberos v5 and NTLM. User profiles store desktop configuration settings and can be local, roaming, or mandatory. Bulk import/export utilities like LDIFDE and CSVDE allow importing and exporting user data to and from Active Directory.