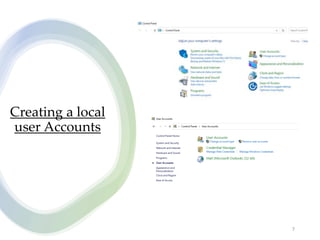
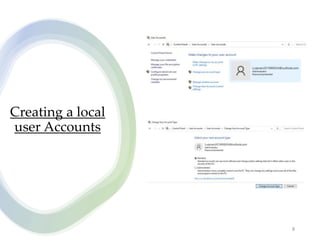
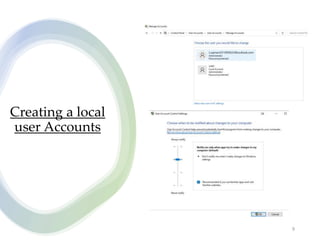
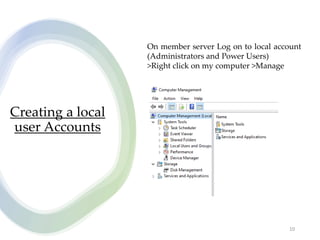
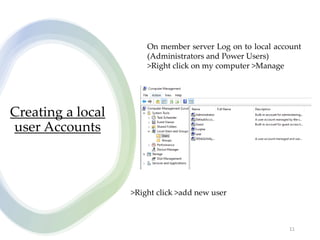
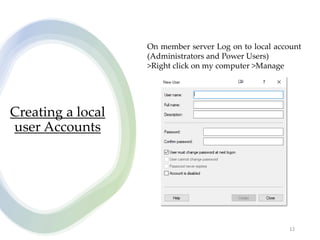
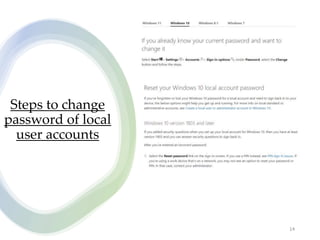
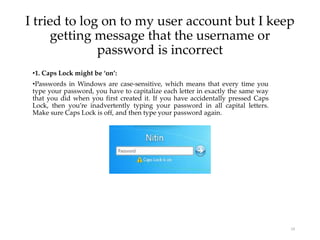
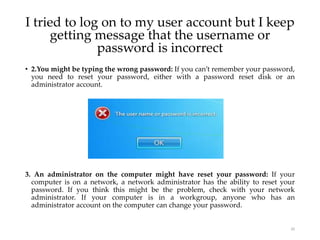
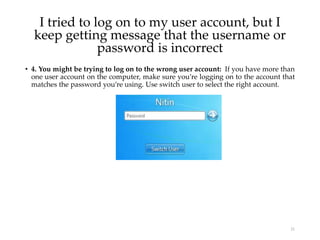
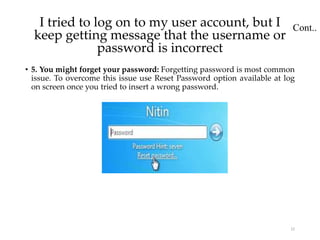
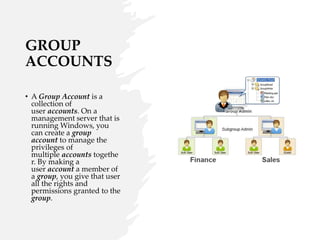
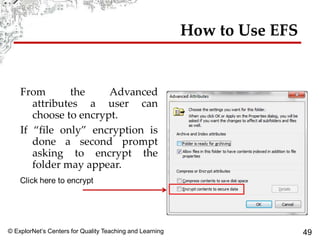
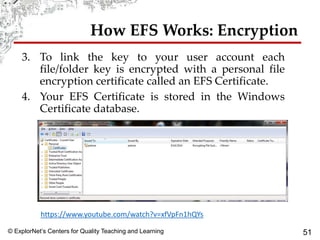
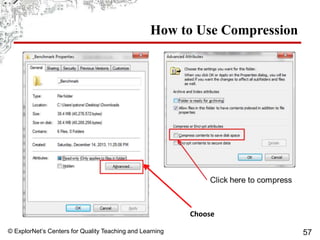
User account management and configuring group accounts are discussed. A user account stores a user's files, settings and access permissions. There are two types of accounts: domain user accounts managed through Active Directory and local user accounts for smaller networks. Groups allow assigning common permissions to multiple users. The document provides steps for creating and deleting local user and group accounts, and troubleshooting issues with user profiles, application access and forgotten passwords. Encrypting File System (EFS) encryption and file compression techniques are also covered.