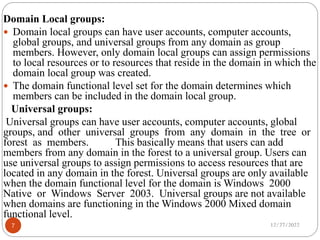
User accounts, authentication, strong passwords, and network security are important controls to ensure authorized access and prevent unauthorized access. Group policy objects and security groups can be used to centrally manage permissions and settings for users and computers. Creating user and computer accounts, defining different group types and scopes, and configuring group policies allows administrators to effectively manage security and resources on the network.


![Authentication: -
The process of verifying the identity of people who are attempting to
access the network or system. This is usually the first step in gaining
access to a computer system. A process of determining what activities or
access will be permitted for user. This may include access to network
resources, data and applications.
Strong passwords
Computer security includes the use of strong passwords for your network
logon and the administrator account on your computer. For a password to
be strong, it should: Be at least seven characters long. Because of the
way passwords are encrypted, the most secure passwords are seven or 14
characters long.
Contain characters from each of the following three groups:
Group Examples
Letters (uppercase and lowercase)A, B, C...Z (And a, b, c...z)
Numerals 0, 1, 2, 3, 4, 5, 6, 7, 8, 9
Symbols (all characters not defined as letters or numerals) ` ~ ! @ # $
% ^ & * ( ) _ + - = { } | [ ] : " ; ‘ < > ? , . /
12/27/2022
3](https://image.slidesharecdn.com/presentation1000-240303054021-db6f915c/85/Presentation-gggffggggg-pdf-3-320.jpg)