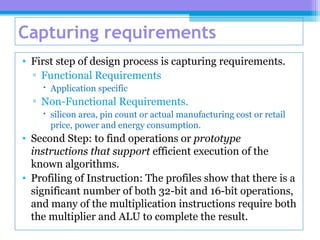
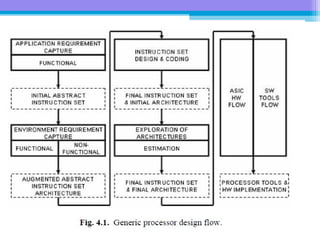
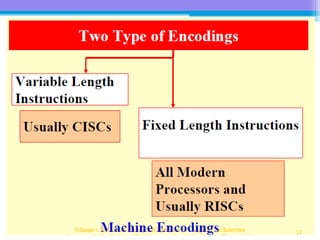
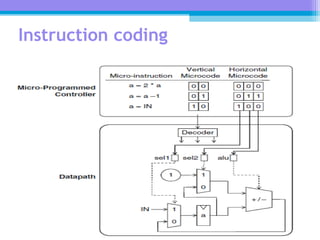
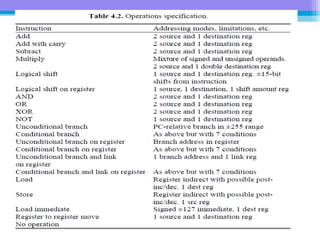
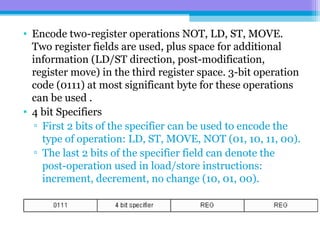
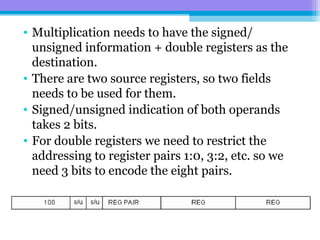
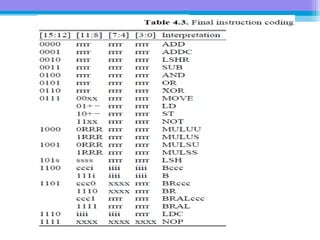
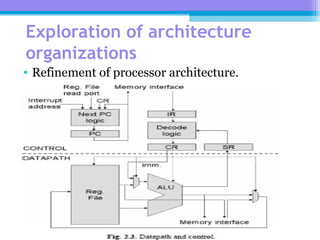
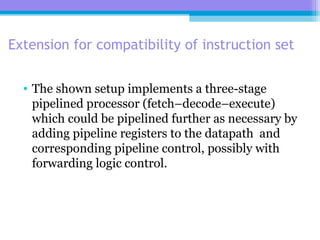
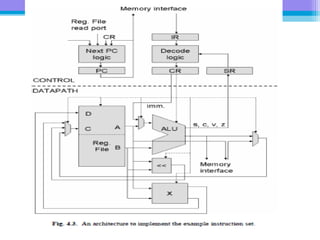
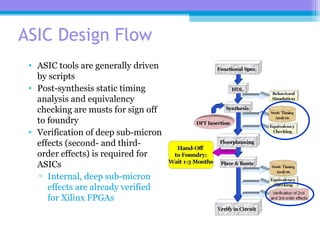
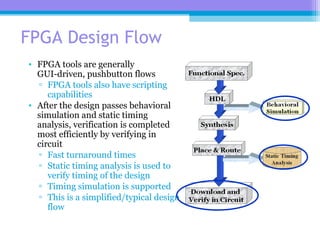
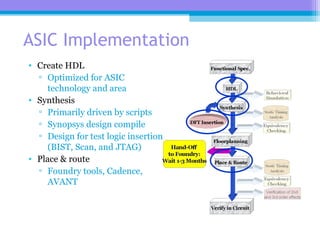
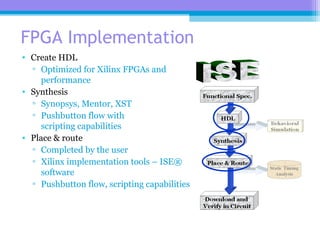
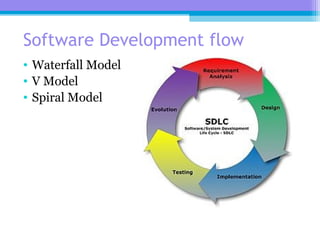
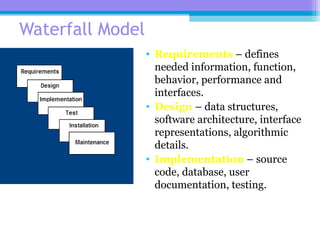
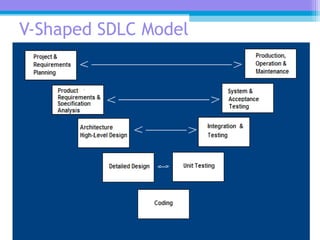
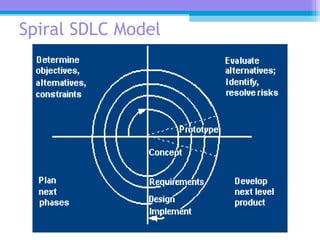
The document discusses the processor design flow, highlighting steps such as capturing requirements, instruction coding, and architecture exploration. It outlines the types of instructions and their encoding methods (horizontal and vertical), along with hardware and software development processes, including ASIC and FPGA design flows. Additionally, various software development models and necessary tools for the development process are briefly described.