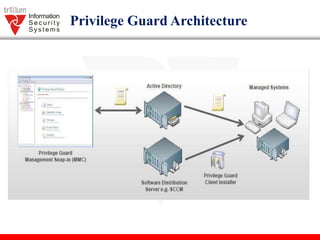
This document summarizes a presentation about a privilege management solution called Privilege Guard. It discusses how least privilege access reduces risks and costs by standardizing the desktop environment. It outlines challenges like users having admin rights and high support costs. Privilege Guard allows assigning privileges based on user roles to control unauthorized software and central management. Benefits include on-demand access, auditing, and broad application support. The architecture provides policy lifecycles and event centralization. Examples are given of deploying Privilege Guard locally and blocking or allowing applications.