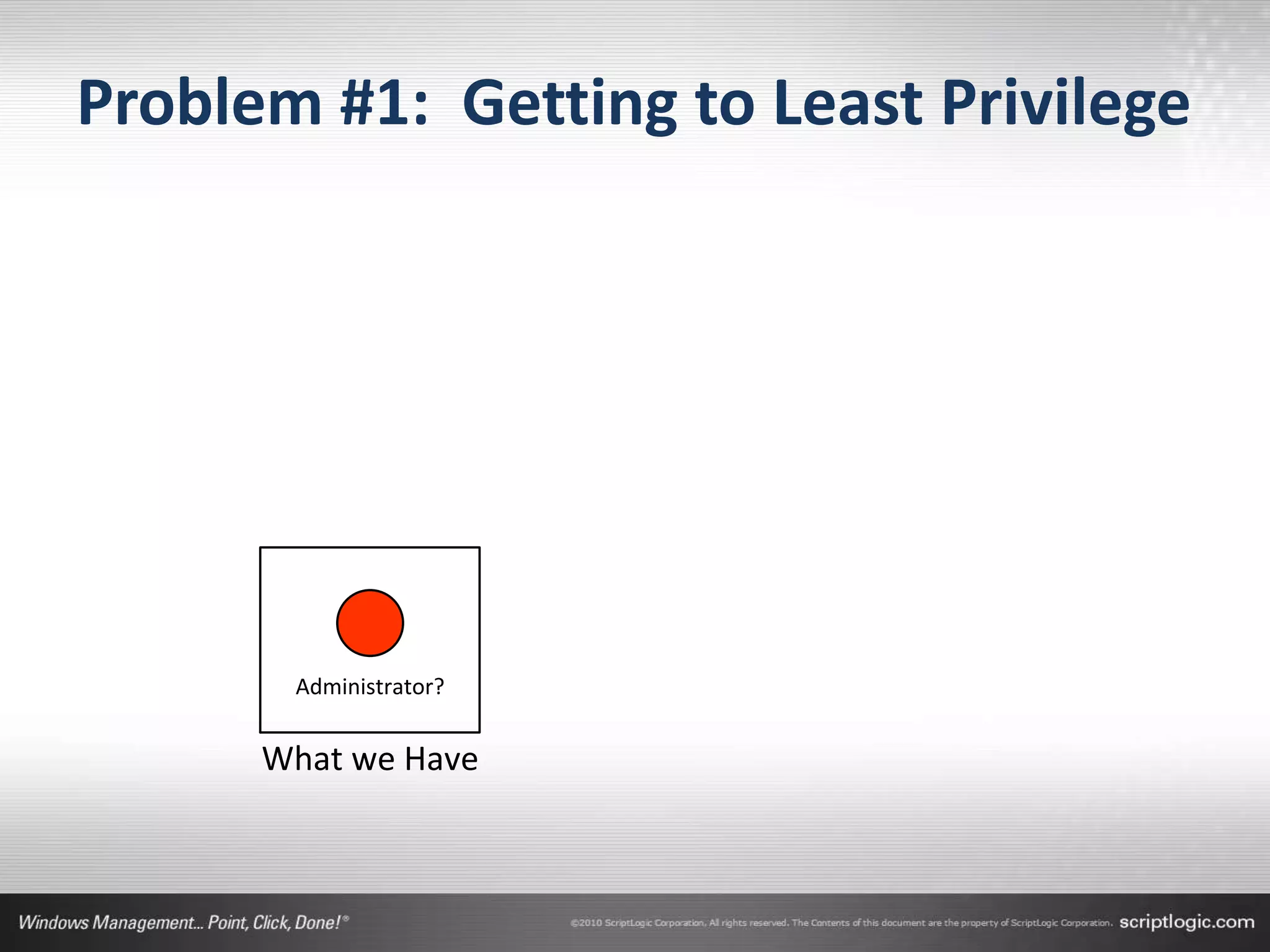
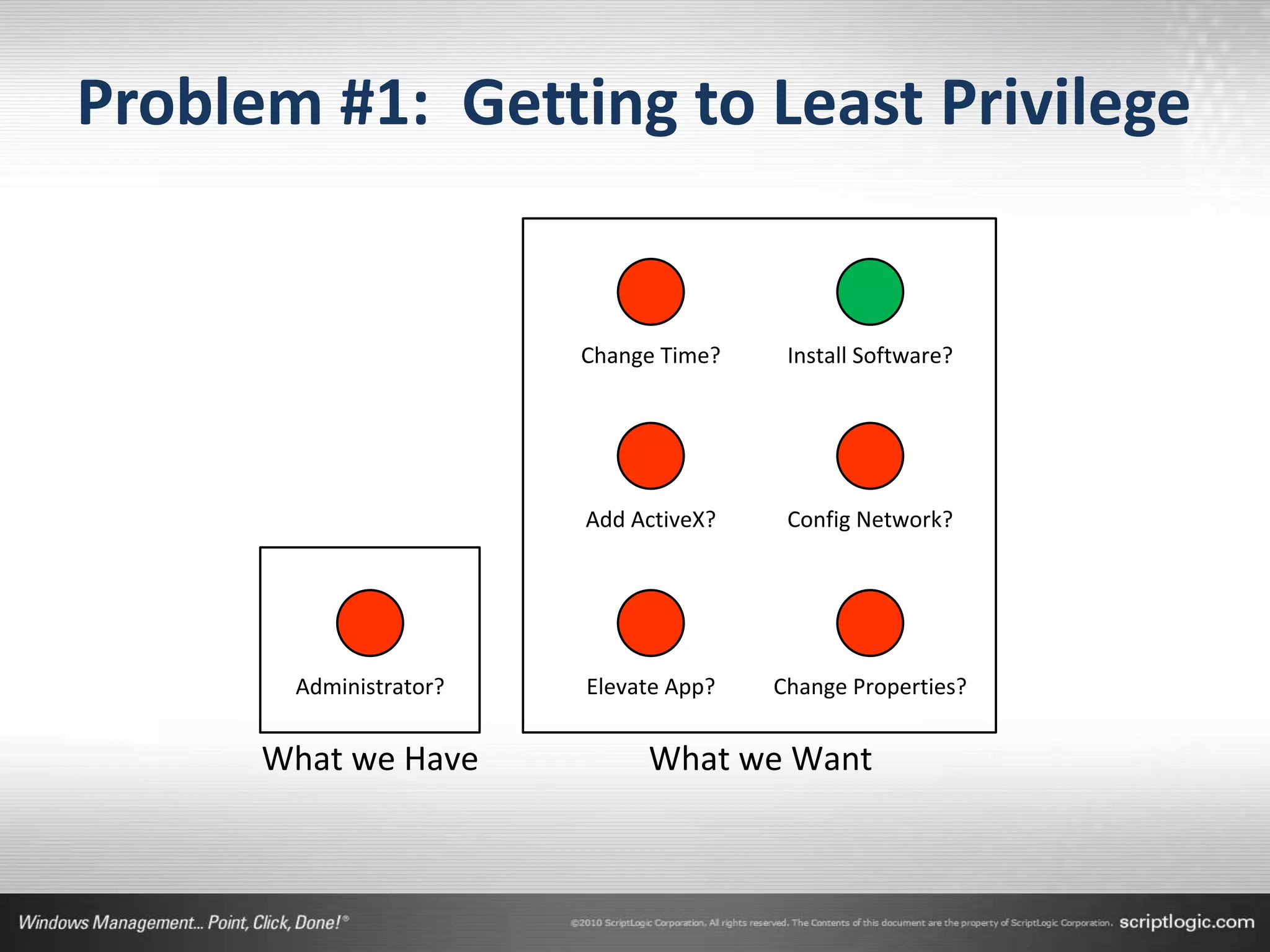
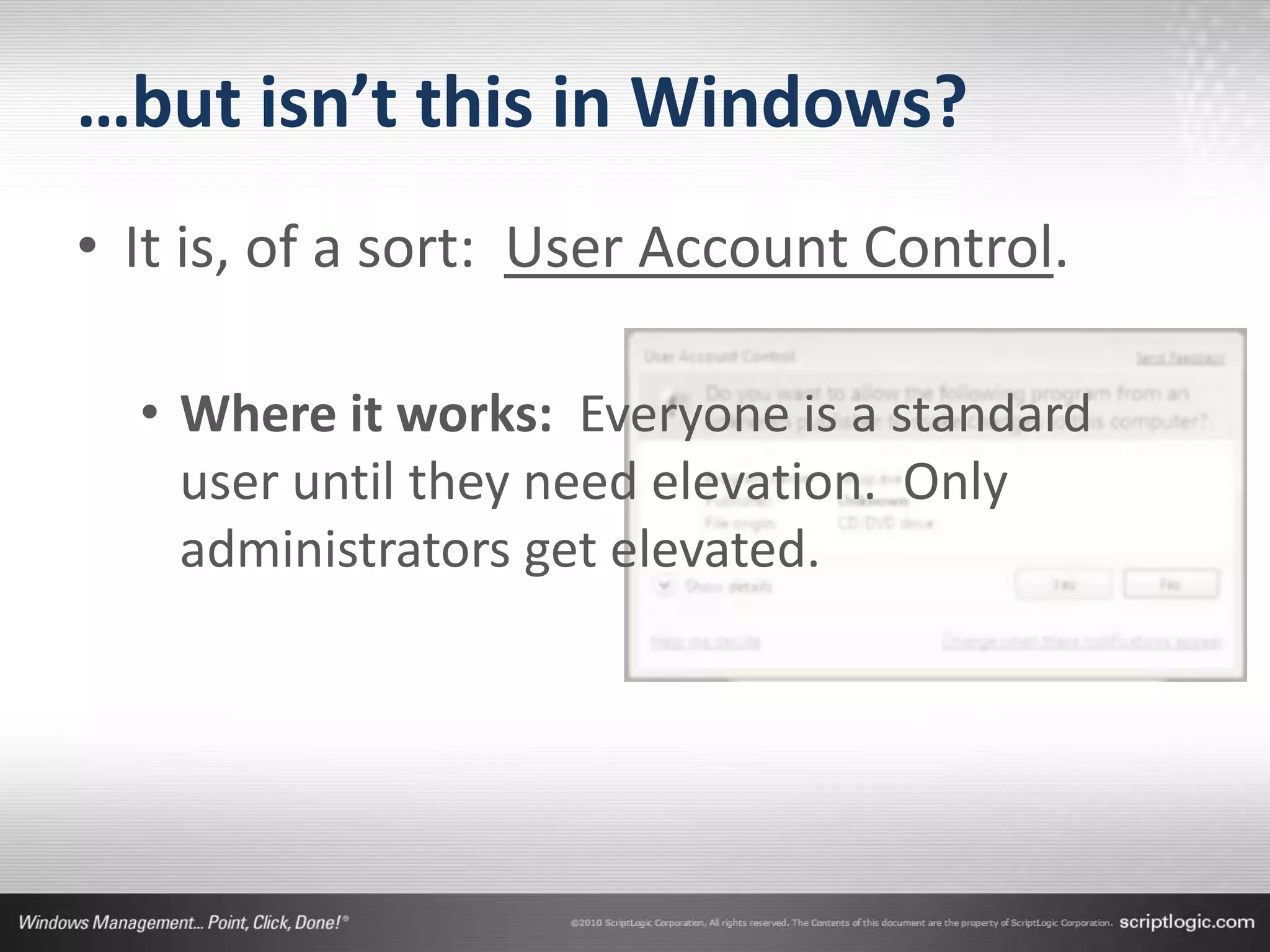
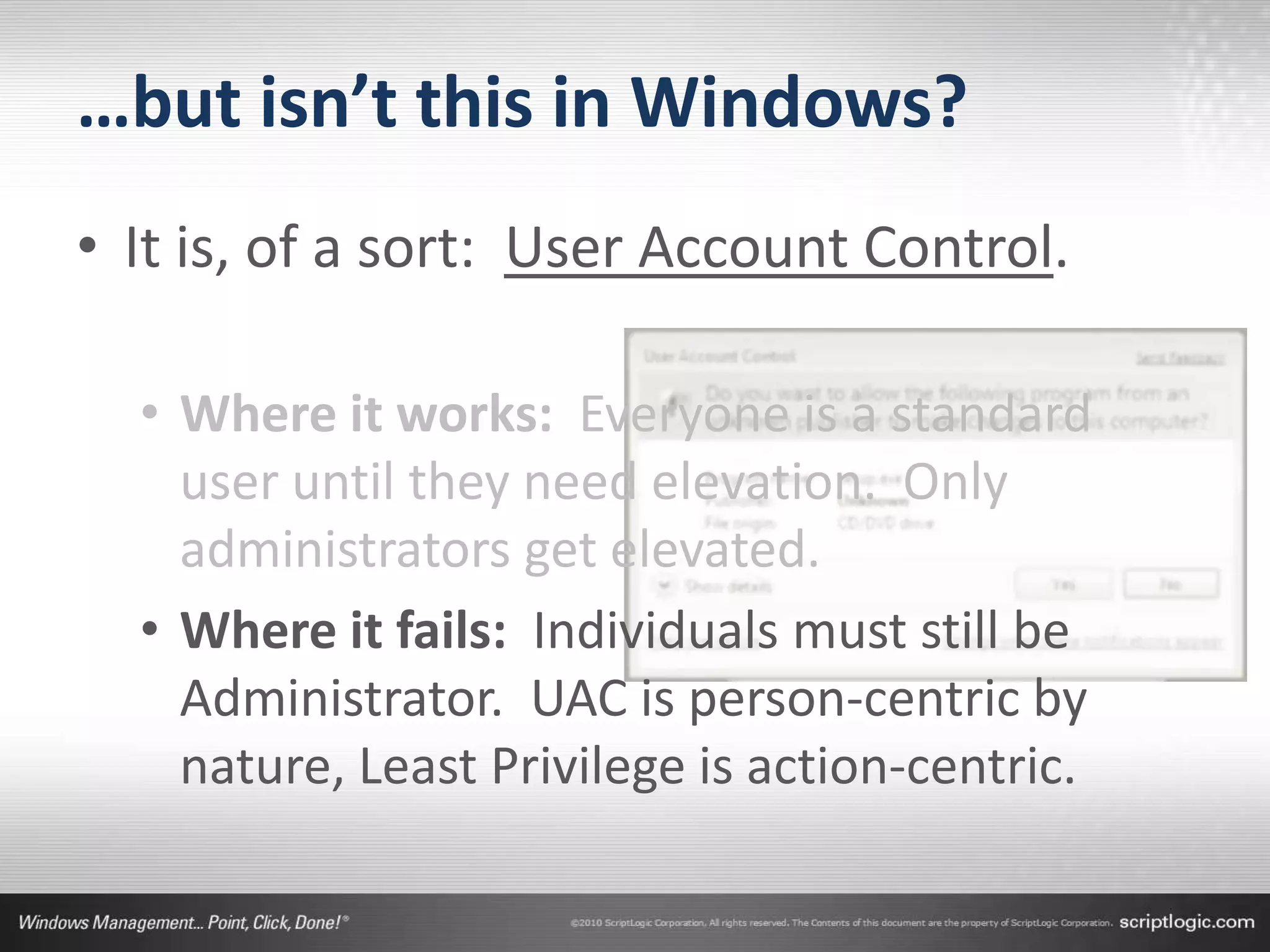
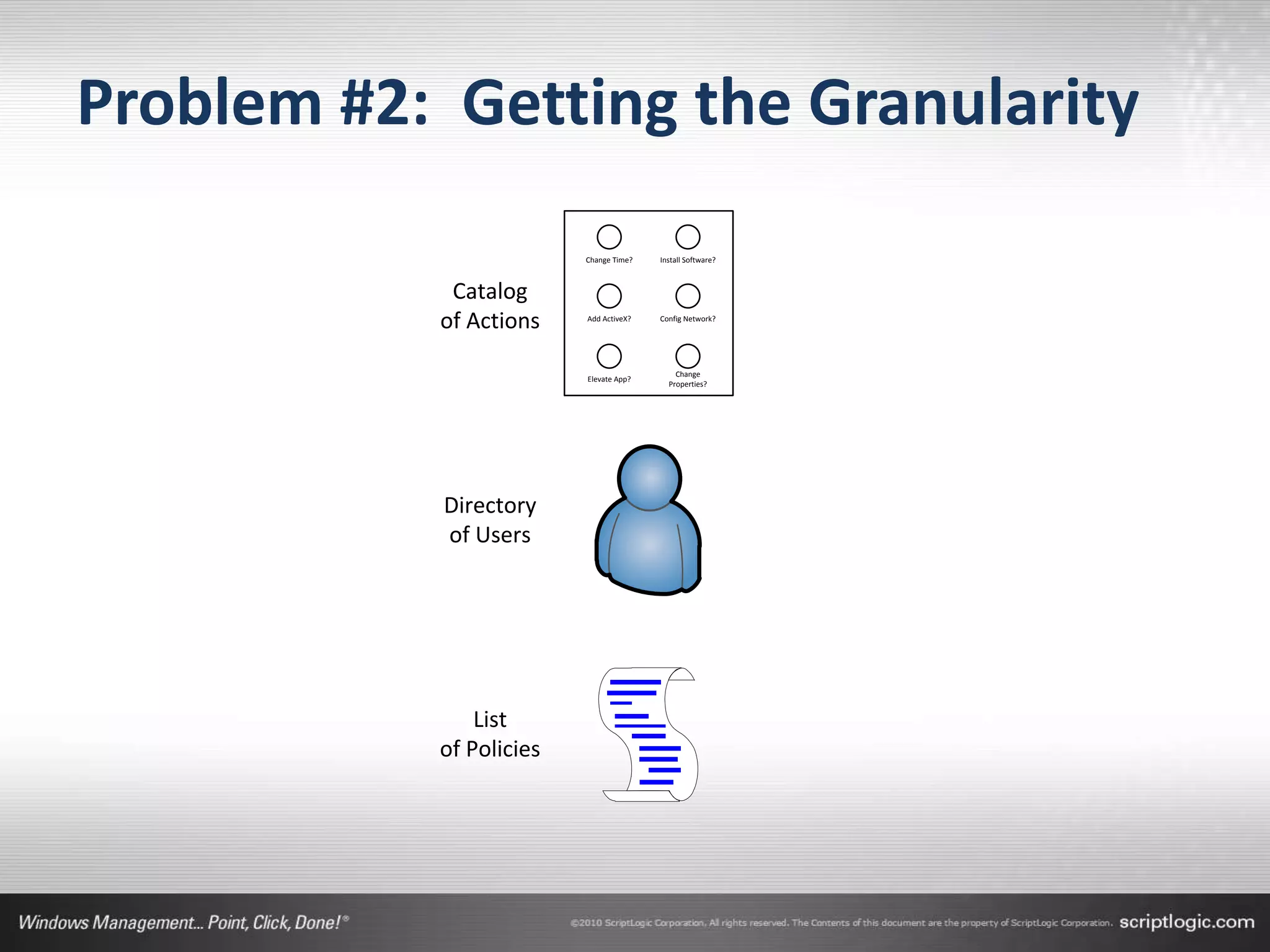
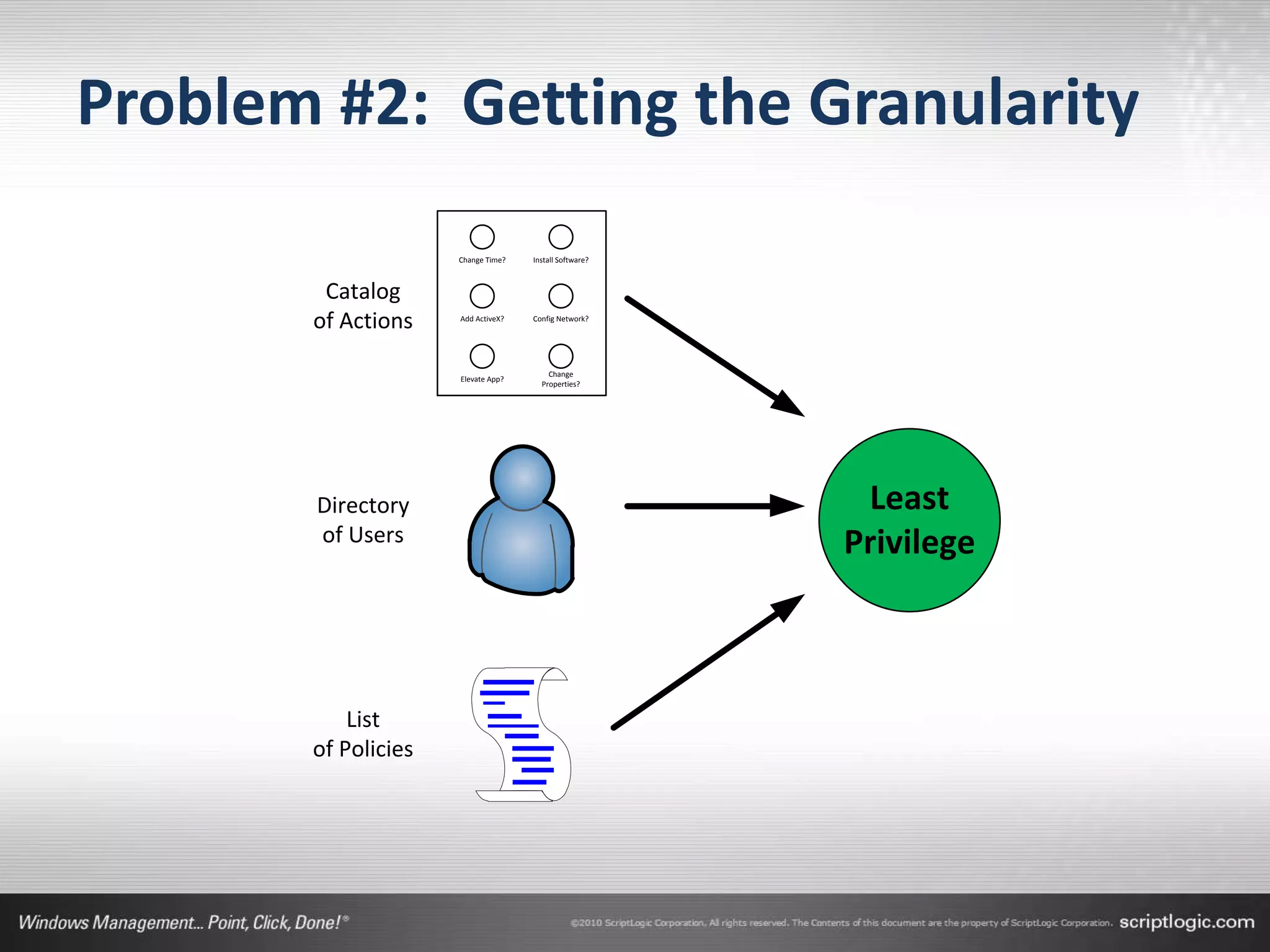
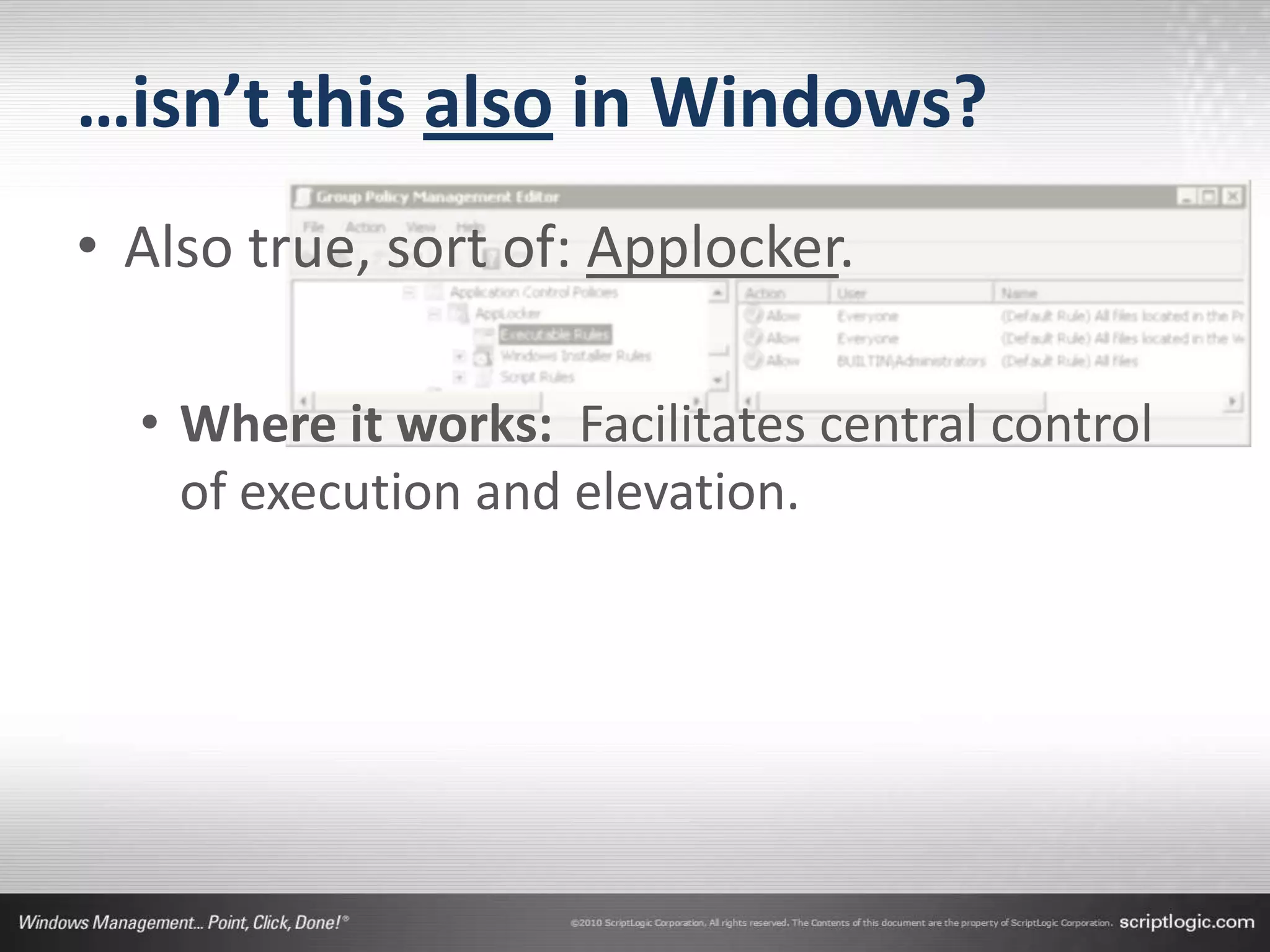
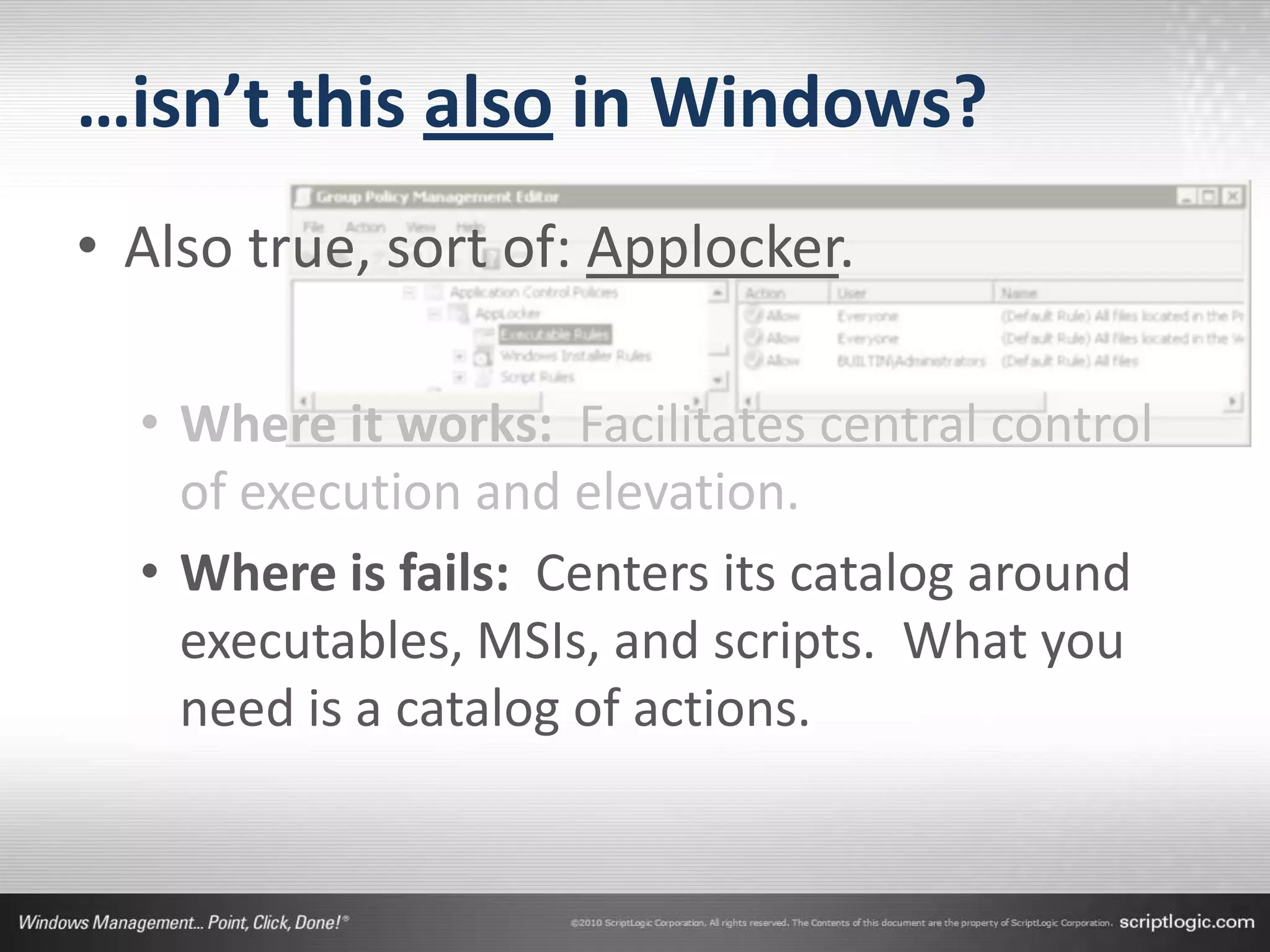
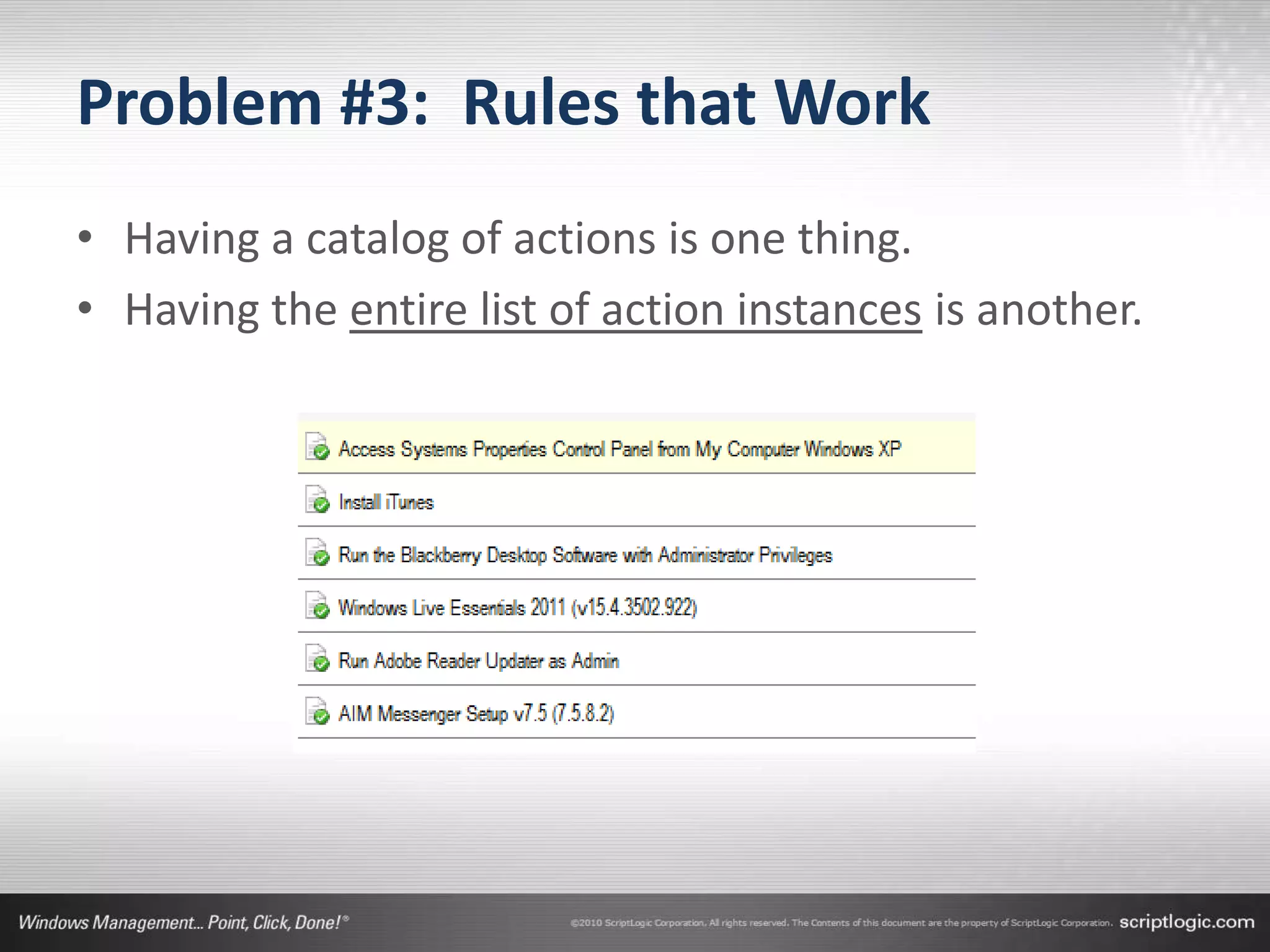
The document presents a discussion on managing administrator rights and implementing the principle of least privilege in Windows environments. It emphasizes the need for granular privilege management to address security and productivity challenges while leveraging external tools. The speakers, Greg Shields and Nick Cavalancia, highlight the importance of community support in developing effective privilege management rules and solutions.


![The Principle of Least Privilege
• “[The Principle of Least Privilege] requires
that…
• each subject in a system be granted the most
restrictive set of privileges…
• …needed for the performance of authorized
tasks.
• The application of this principle limits the
damage that can result from accident, error, or
unauthorized use.”
Source: U.S. Department of Defense](https://image.slidesharecdn.com/redmondwebinarkilladministrator091911-120120160926-phpapp01/75/Kill-Administrator-Fighting-Back-Against-Admin-Rights-7-2048.jpg)