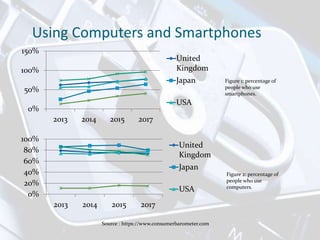
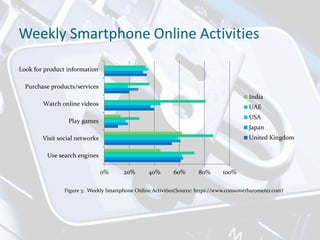
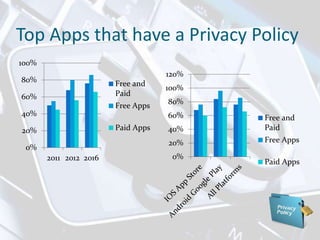
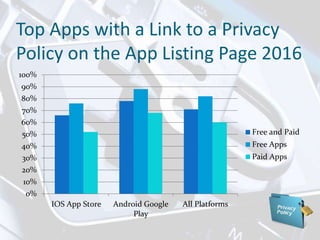
The document discusses privacy issues related to mobile apps. It notes that mobile apps collect large amounts of personal data from users through devices' sensors and capabilities. Many users uninstall apps due to privacy concerns over how their data is collected and shared. The document also outlines challenges in the mobile app ecosystem regarding privacy policies, permission models, and ensuring user data is handled according to legal and regulatory standards.