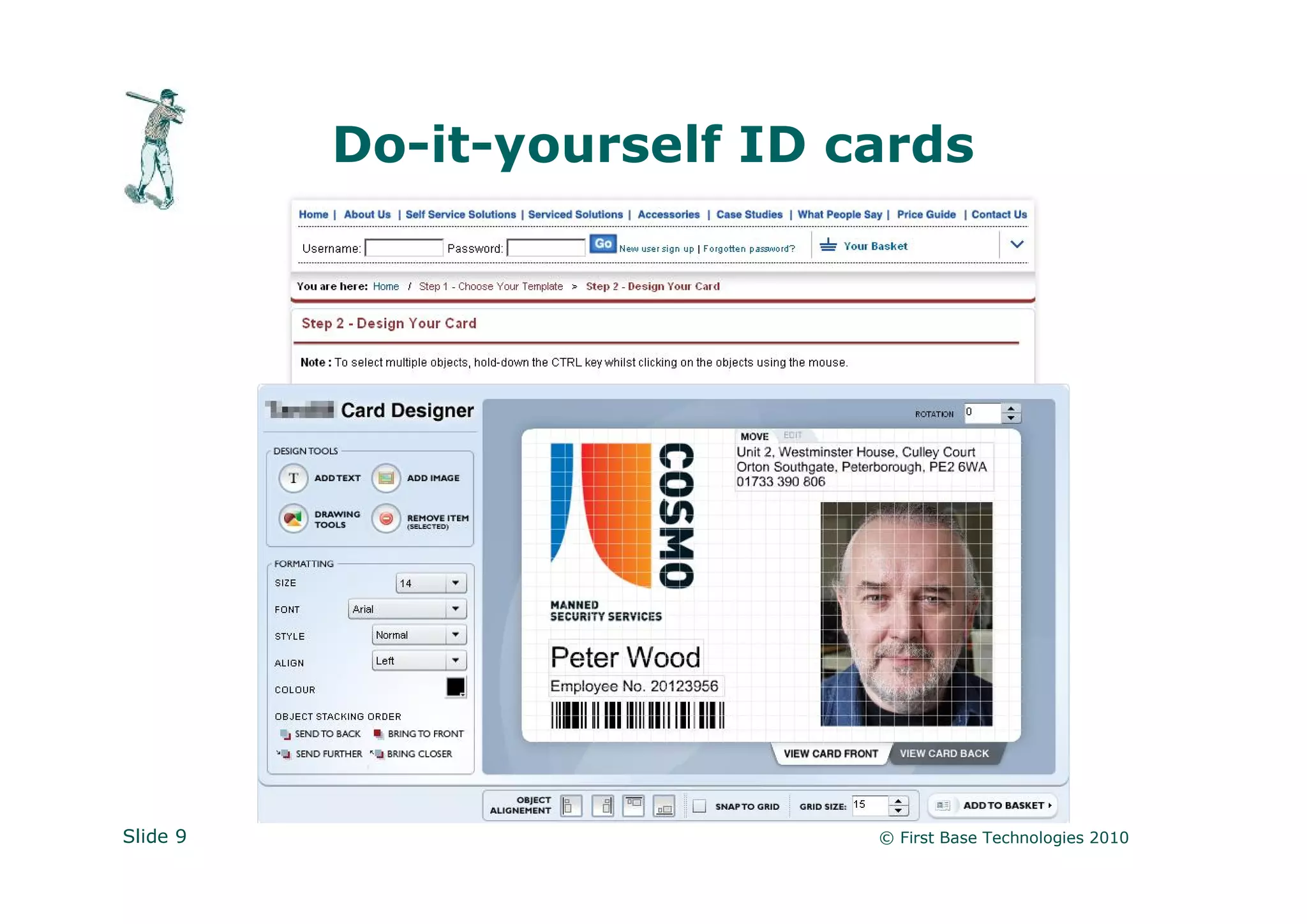
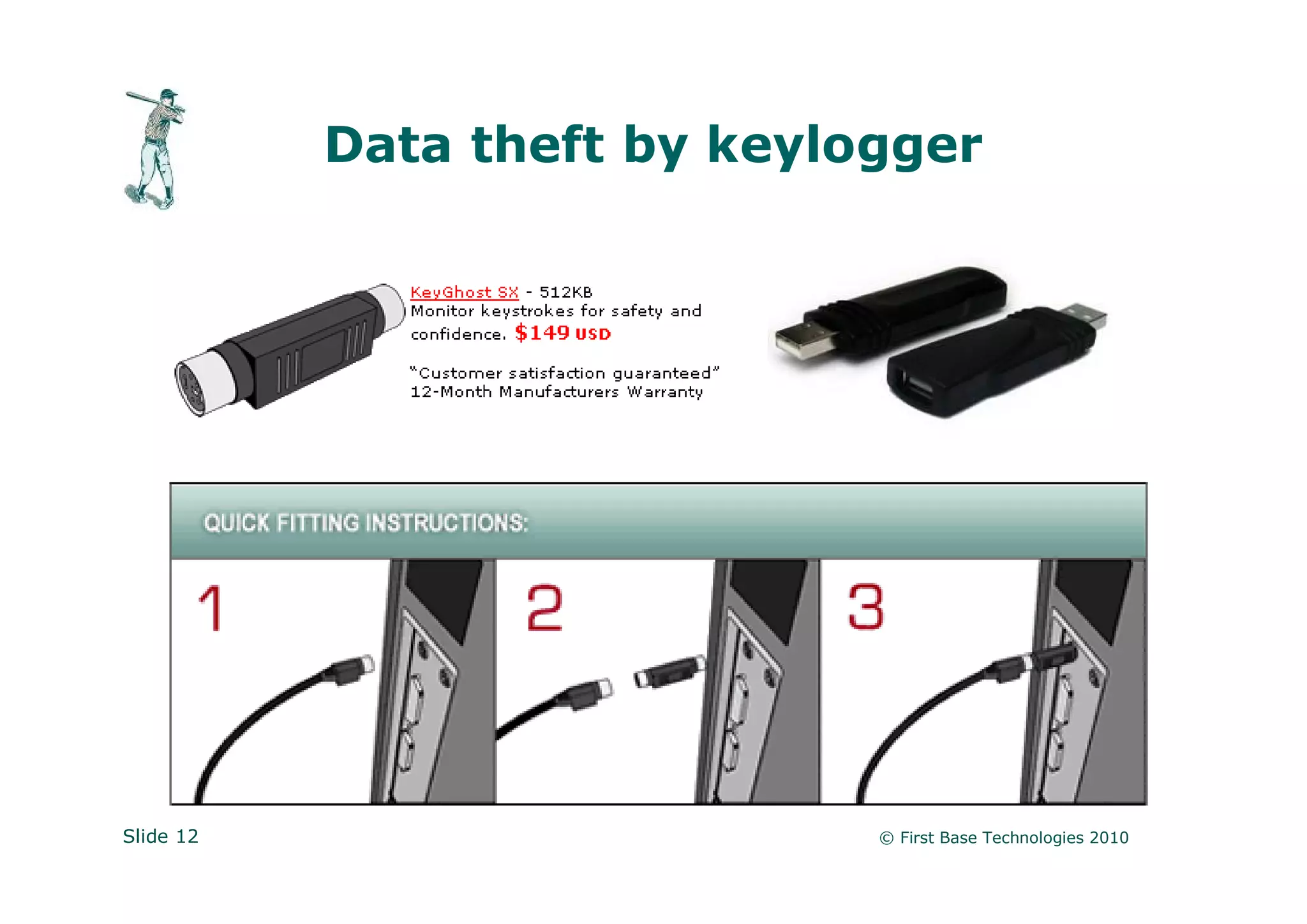
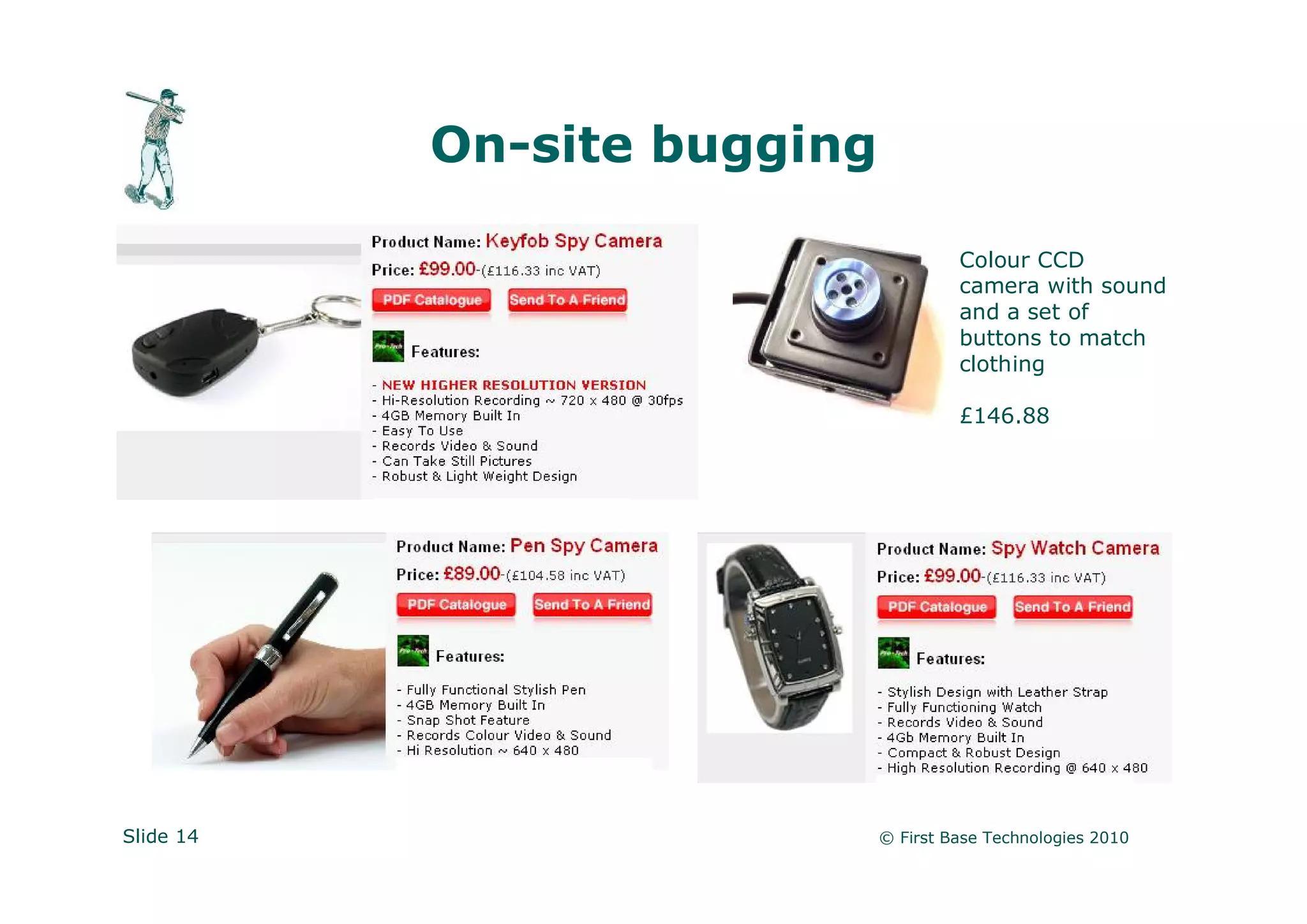
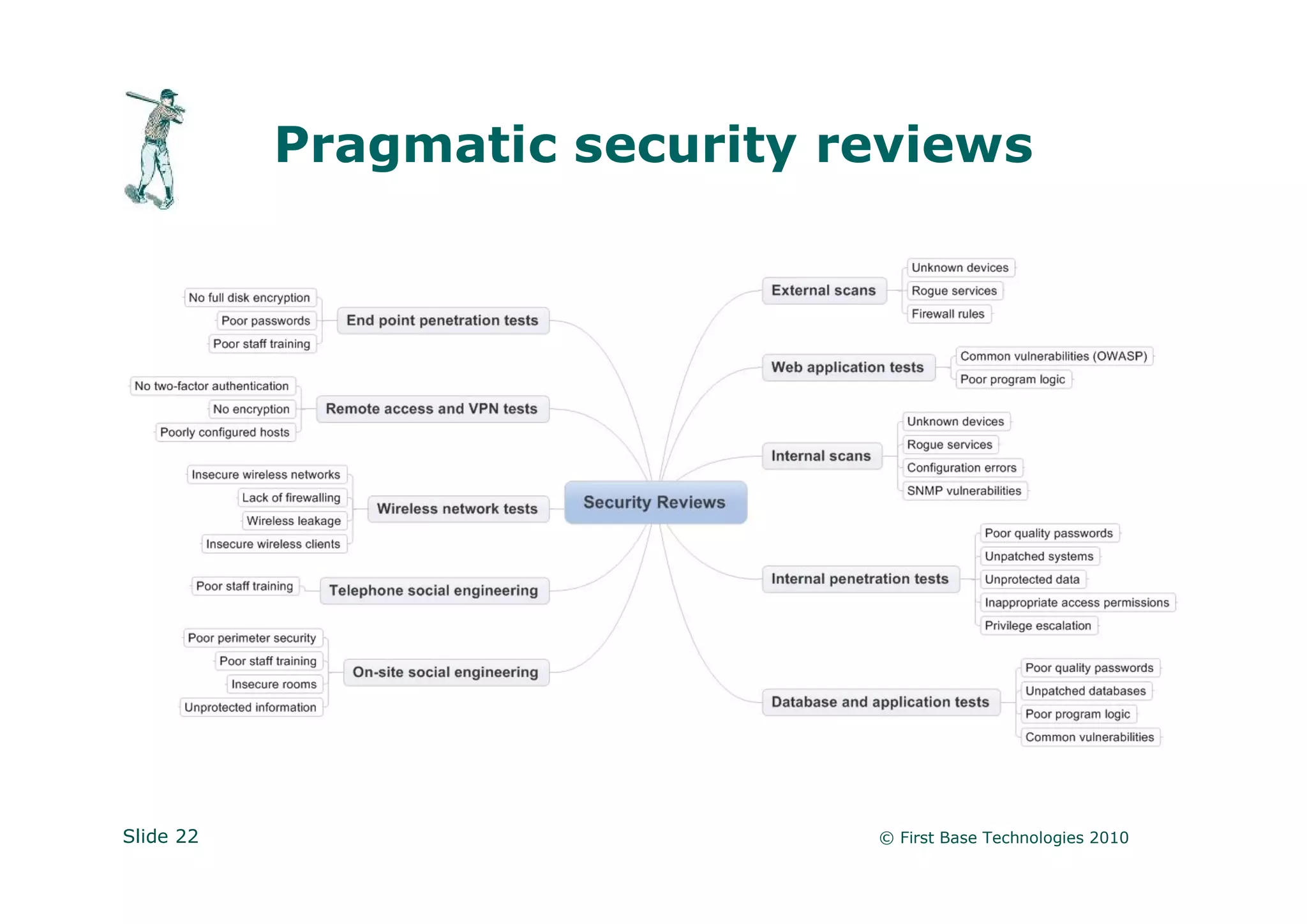
Peter Wood is the CEO of First Base Technologies, an ethical hacking firm. He advocates thinking like a hacker to identify security vulnerabilities, such as impersonating employees or cleaning staff to gain physical access, using USB devices to steal data, or exploiting lack of wireless encryption to eavesdrop on traffic. Traditional defenses like firewalls and antivirus are not enough; organizations must consider alternative attack scenarios to find and address soft spots before attackers do.


![Thinking like a hacker
• Hacking is a way of thinking
A hacker is someone who thinks outside the box. It's
someone who discards conventional wisdom, and does
something else instead. It's someone who looks at the
edge and wonders what's beyond. It's someone who
sees a set of rules and wonders what happens if you
don't follow them. [Bruce Schneier]
• Hacking applies to all aspects of life
- not just computers
Slide 3 © First Base Technologies 2010](https://image.slidesharecdn.com/think-like-a-hacker-110508104225-phpapp02/75/The-Ultimate-Defence-Think-Like-a-Hacker-3-2048.jpg)