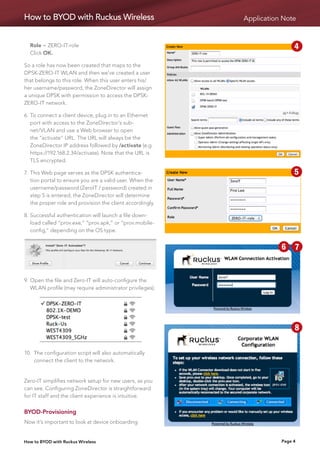
Ruckus provides a solution for BYOD implementations using Dynamic Pre-Shared Keys (DPSK) and Zero-IT Activation that simplifies setup while maintaining security. DPSK assigns unique credentials to each user/device instead of using a shared passphrase. Zero-IT Activation automates configuration of client devices upon first connection by generating and deploying DPSKs without IT intervention. A provisioning network can also be created to securely configure mobile devices on an open wireless network and then connect them to the corporate network.