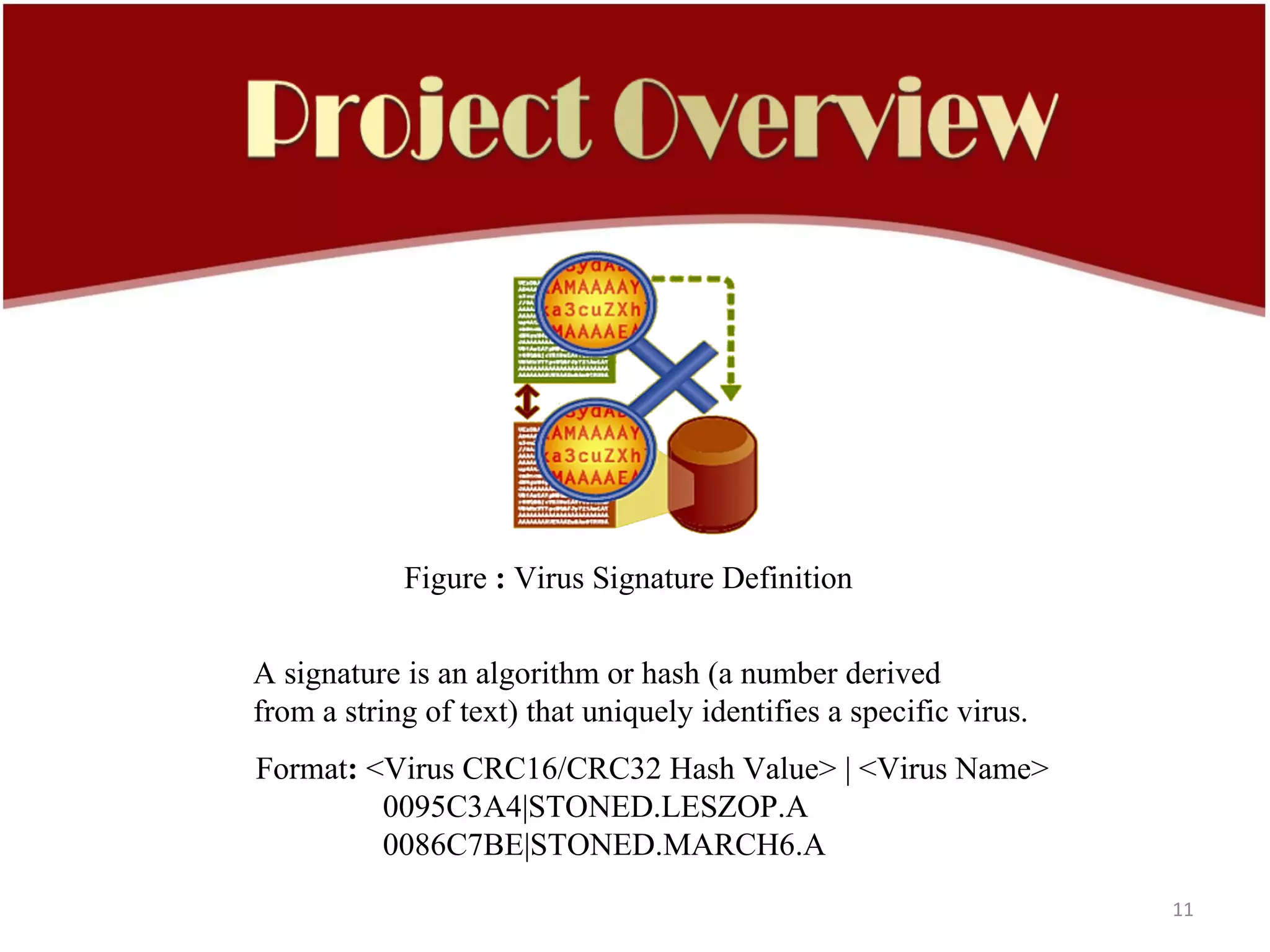
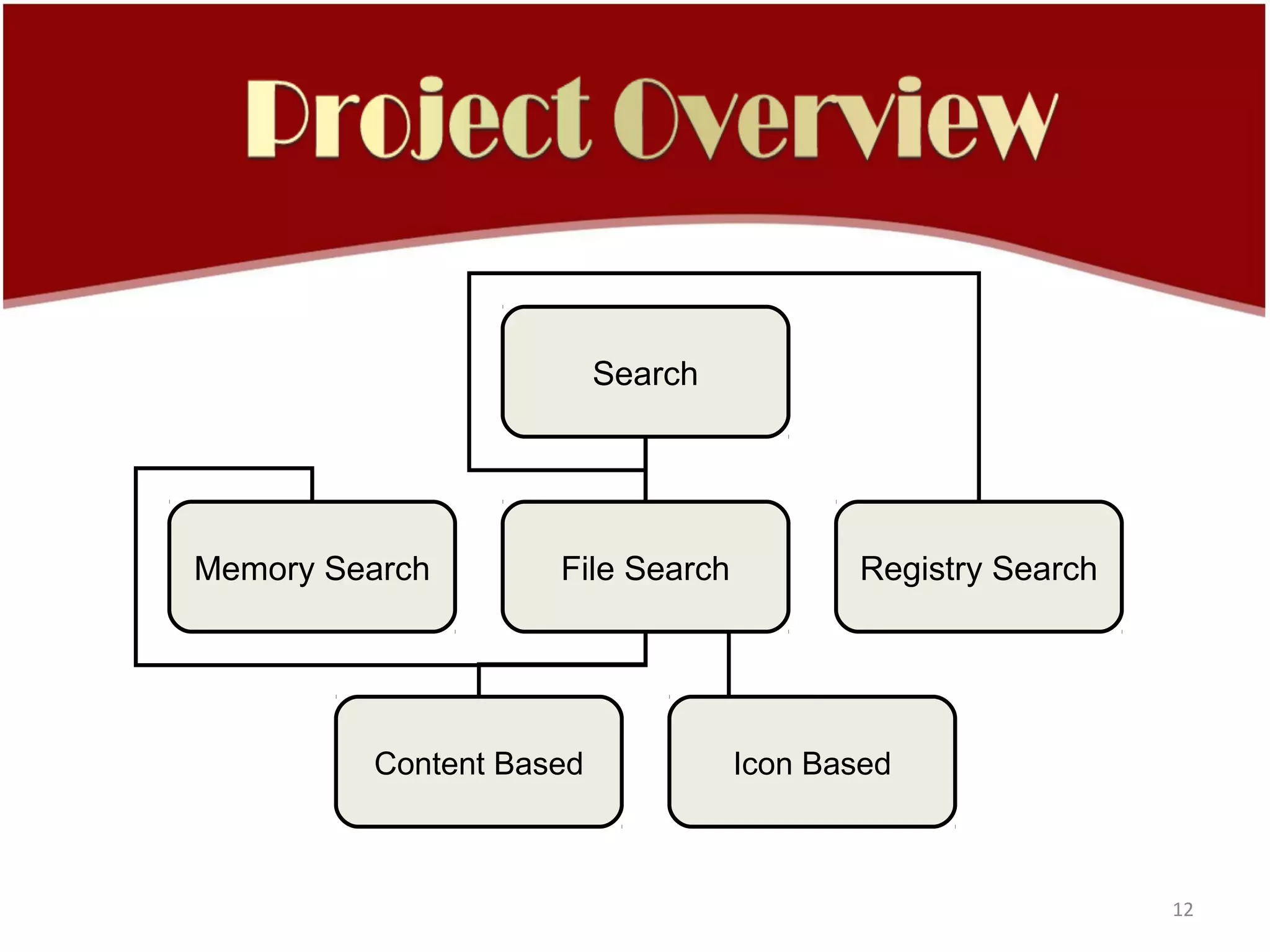
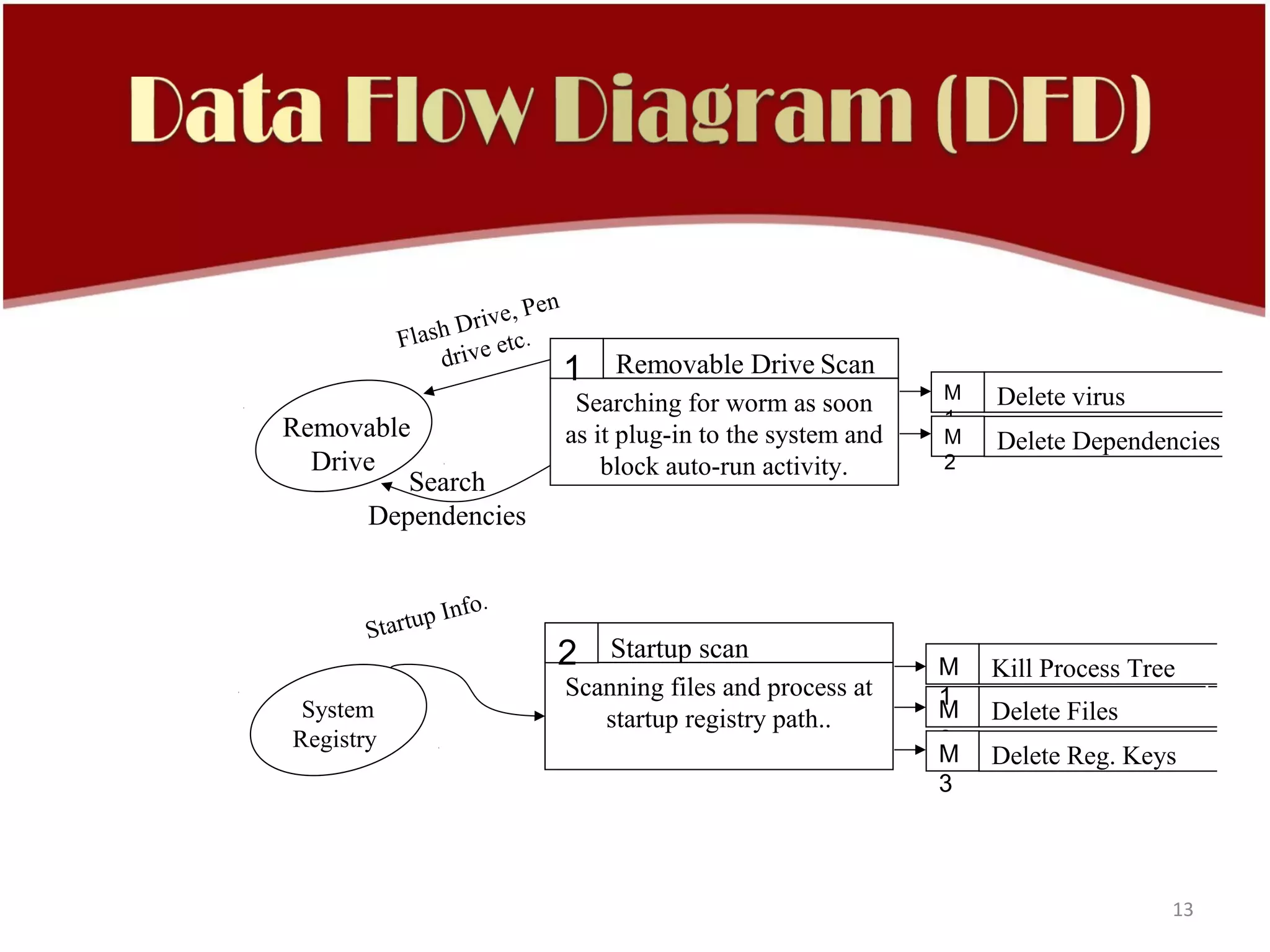
This document discusses computer viruses and antivirus software. It provides an overview of infection strategies used by viruses, methods to identify viruses, and statistics on the impacts of viruses. It then covers the history of early computer viruses from 1971 to 1986. The document also includes diagrams depicting virus encounter vectors and the impact of vulnerabilities. It describes virus signature definitions and scanning techniques used by antivirus software to detect and remove viruses from systems and networks.



![1. The first virus was born in the very beginning of 1970s.
2 Creeper was an experimental self-replicating program written by Bob
Thomas at BBN in 1971.
3. Creeper gained access via the ARPANET and copied itself to the remote
system.
4. The Reaper program was created to delete Creeper. [First Antivirus]
5. "Rother J" was the first computer virus to appear first time the lab where it
was created. Written in 1981 by Richard Skrenta,
6. The first PC virus in the wild was a boot sector virus dubbed Brain.
created in 1986 by the Farooq Alvi Brothers.
7. Macro viruses have become common since the mid-1990s.
8](https://image.slidesharecdn.com/presentation-121029010325-phpapp02/75/Signature-based-virus-detection-and-protection-system-8-2048.jpg)