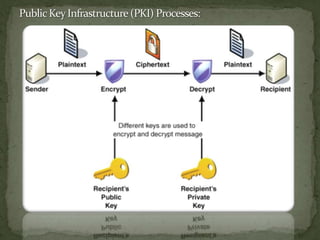
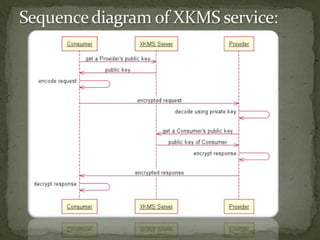
The document discusses how XML Key Management Services (XKMS) provides a standard for managing public keys and certificates through web services, allowing for simpler and more interoperable security such as XML signatures and encryption for web services. XKMS acts as a central repository for public keys that can be accessed through web methods, reducing the complexity and cost of traditional PKI solutions while still enabling secure authentication, encryption, and validation of signatures. The paper argues that XKMS provides the foundation for secure data exchanges by integrating public key management into a network's authentication and authorization systems.