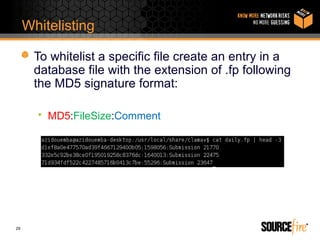
Alain Zidouemba presented on writing signatures for ClamAV. He discussed the different signature formats including .hdb, .mdb, .ndb, and .ldb. He provided examples of generating signatures using hash databases and extended signatures. He also demonstrated how to write logical signatures in .ldb format through a case study of the Worm.Godog malware. Whitelisting techniques were also covered, including adding entries to ignore specific signatures.