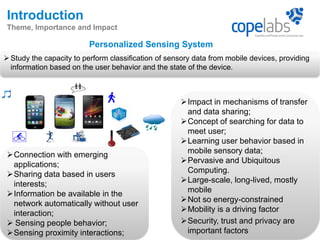
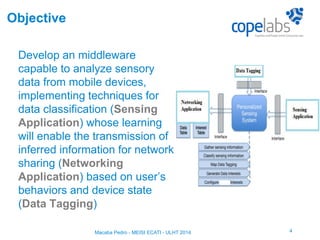
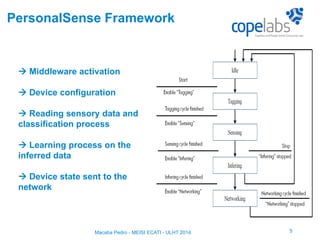
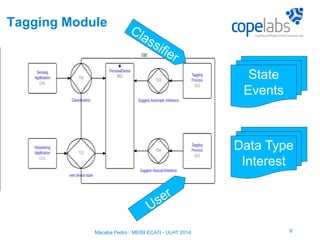
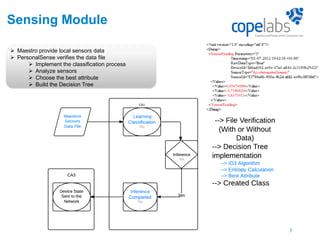
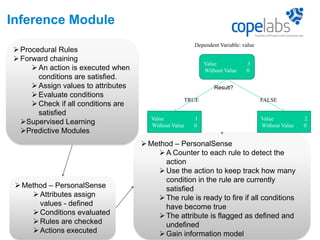
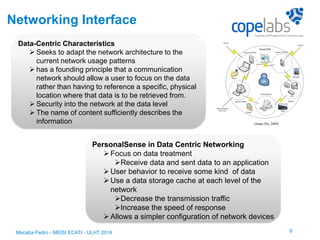
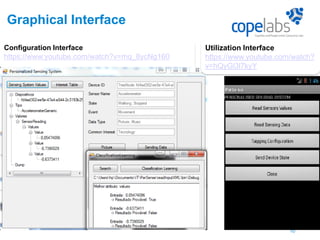
The document discusses a personalized sensing system developed for mobile devices aimed at classifying sensory data according to user behavior and device status, emphasizing the importance of data sharing and security. It outlines the framework comprising tagging and sensing modules, an inference module with procedural rules for predictive analytics, and a data-centric networking interface designed for efficient data retrieval. Final considerations include the integration of services, behavioral profiling through data classification, and future testing with various mobile sensors.