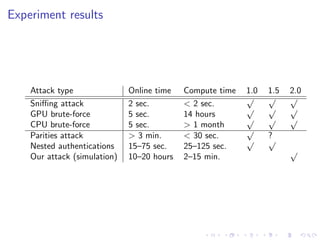
This document summarizes a talk on practical cryptanalysis for hackers. It discusses attacks the speaker carried out on Taiwan's transit payment cards, including the original 悠遊卡 and the upgraded 二代悠遊卡. The speaker describes how earlier 悠遊卡 cards were broken, the upgrades made for 二代悠遊卡, and presents a new card-only attack that can recover keys from 二代悠遊卡 in 10-20 hours without prior knowledge. The talk recommends moving away from the insecure MIFARE Classic technology and discusses how to educate the public about security weaknesses.















![“Reverse-engineering a real-world RFID payment system”
A talk by Harald Welte in 27C3, Dec., 2010
Disclosed “the process of reverse-engineering the actual
content of the [悠遊卡] to discover the public transportation
transaction log, the account balance and how the daily
spending limit work”
As well as “how easy it is to add or subtract monetary value
to/from the card. Cards manipulated as described in the talk
have been accepted by the payment system”](https://image.slidesharecdn.com/practicalcryptanalysisforhackerschen-moucheng-151211092927/85/Practical-cryptanalysis-for-hackers-17-320.jpg)
![“Reverse-engineering a real-world RFID payment system”
A talk by Harald Welte in 27C3, Dec., 2010
Disclosed “the process of reverse-engineering the actual
content of the [悠遊卡] to discover the public transportation
transaction log, the account balance and how the daily
spending limit work”
As well as “how easy it is to add or subtract monetary value
to/from the card. Cards manipulated as described in the talk
have been accepted by the payment system”
“Corporations enabling citizens to print digital money”](https://image.slidesharecdn.com/practicalcryptanalysisforhackerschen-moucheng-151211092927/85/Practical-cryptanalysis-for-hackers-18-320.jpg)