The document discusses the significance of hardware security in the context of increasing vulnerabilities, particularly highlighting the recent Meltdown and Spectre attacks that exploit hardware design flaws. It emphasizes the challenges circuit designers face in integrating security considerations into hardware design due to added costs and complexity. As the demand for hardware security rises with the growth of IoT applications, collaboration between circuit design and information security experts is essential for addressing these challenges.









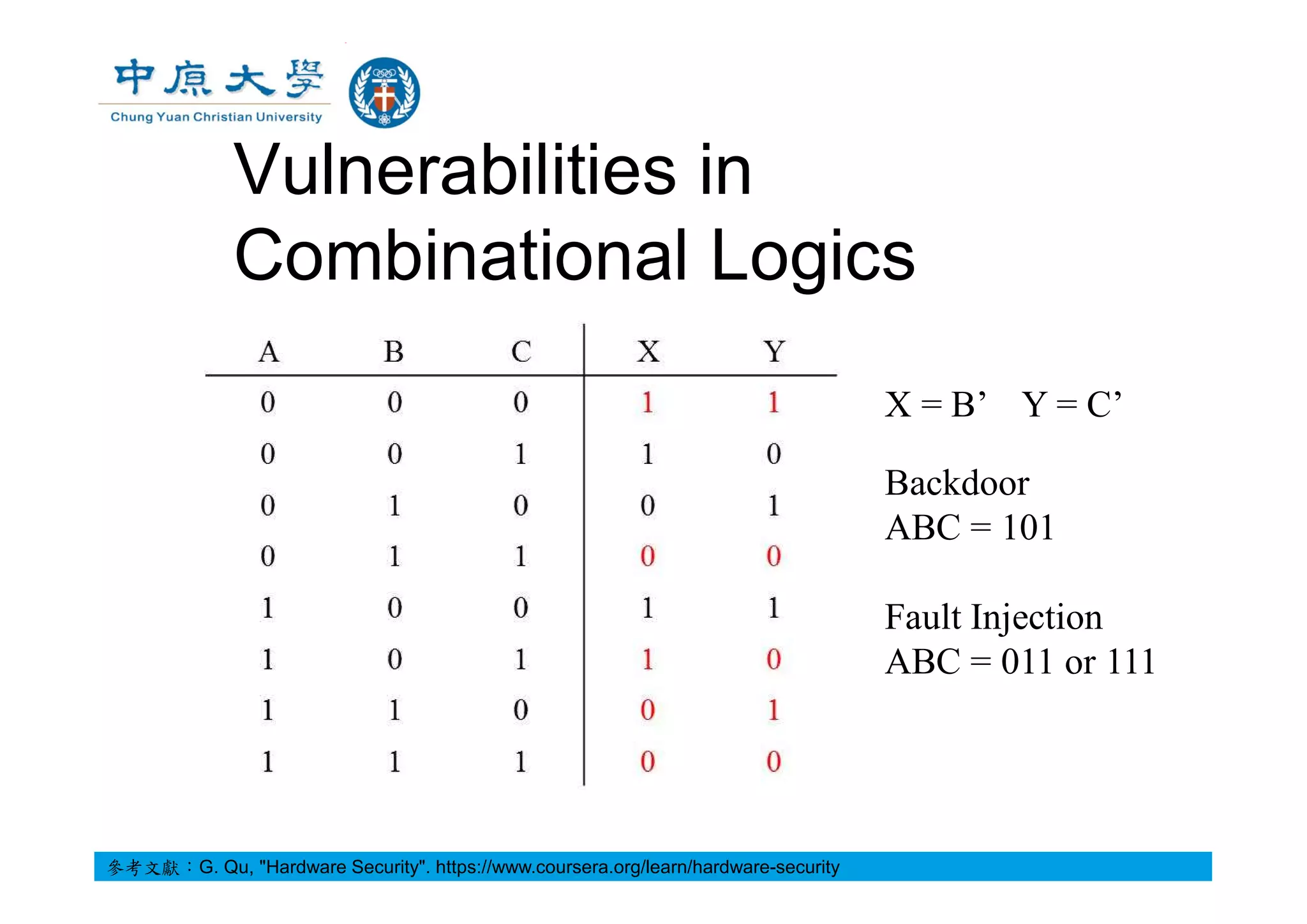

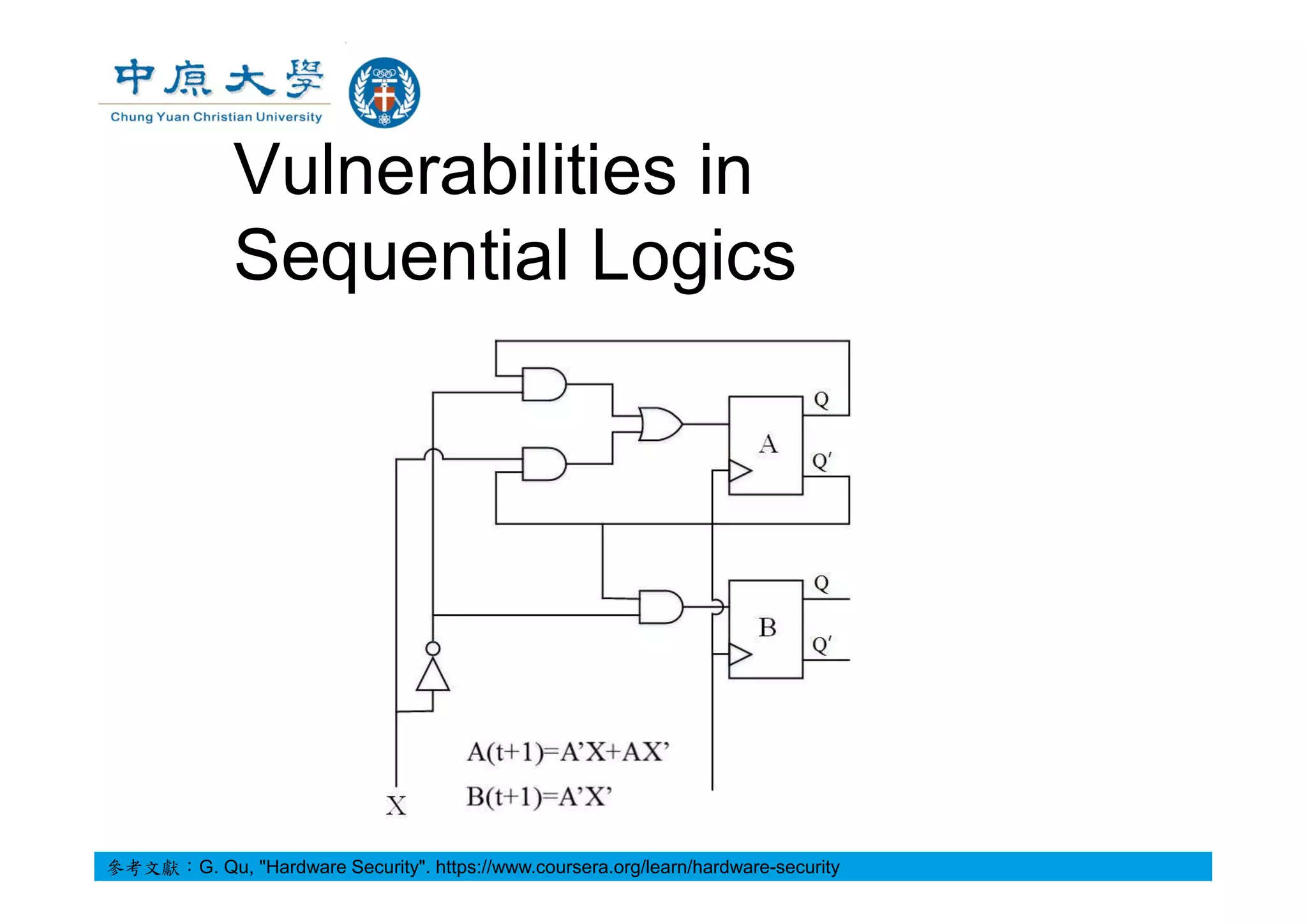

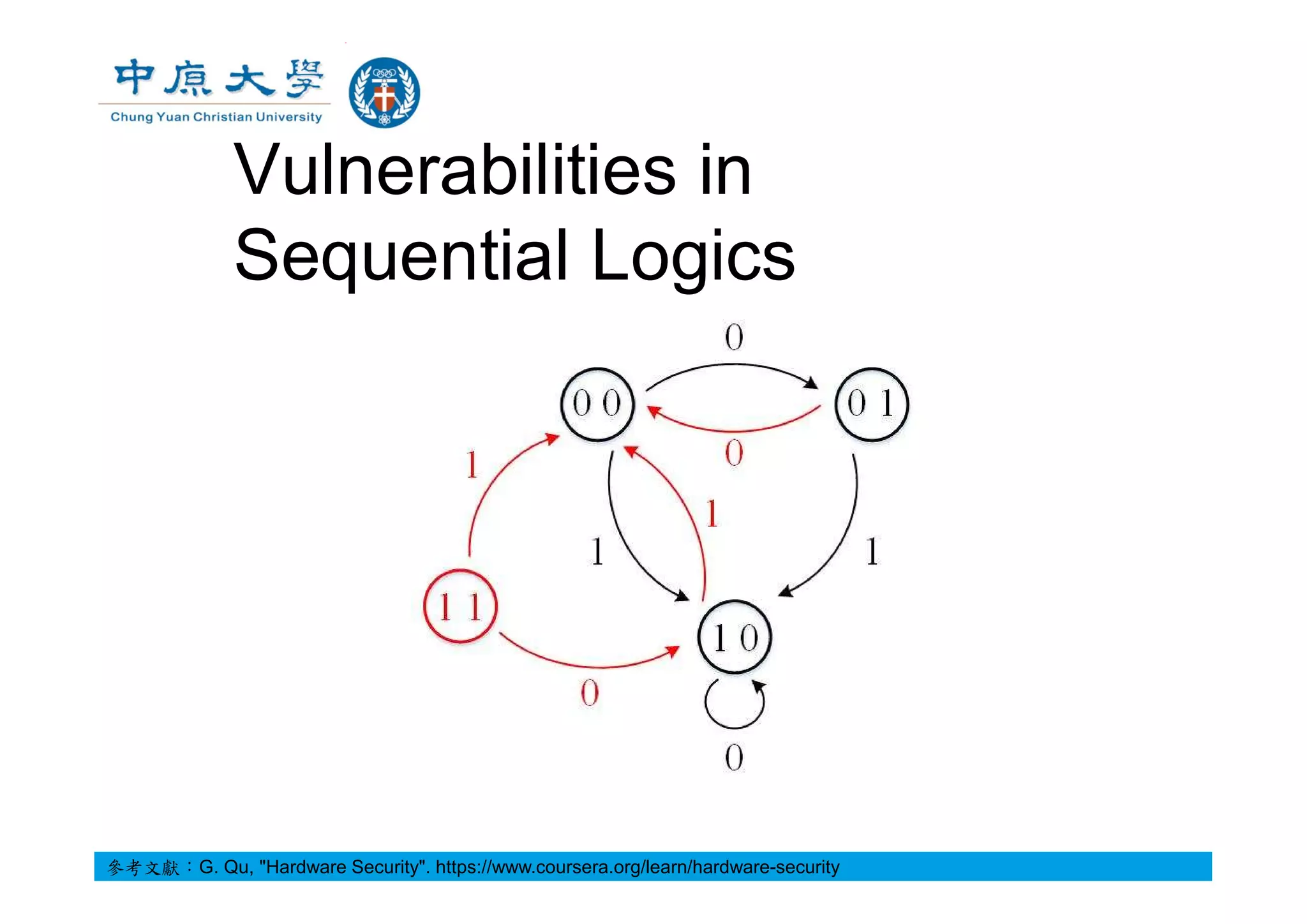





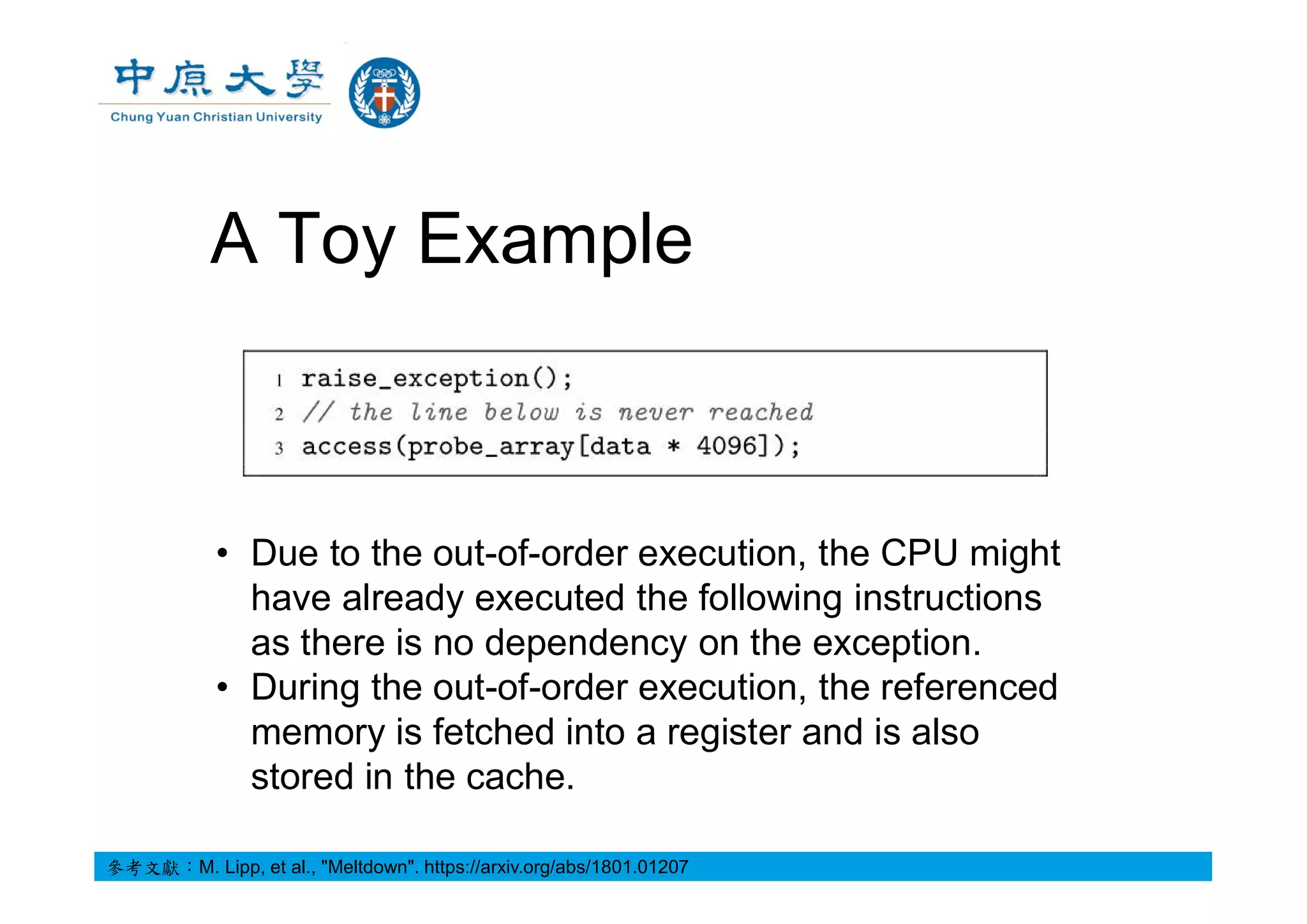



![A Toy Example
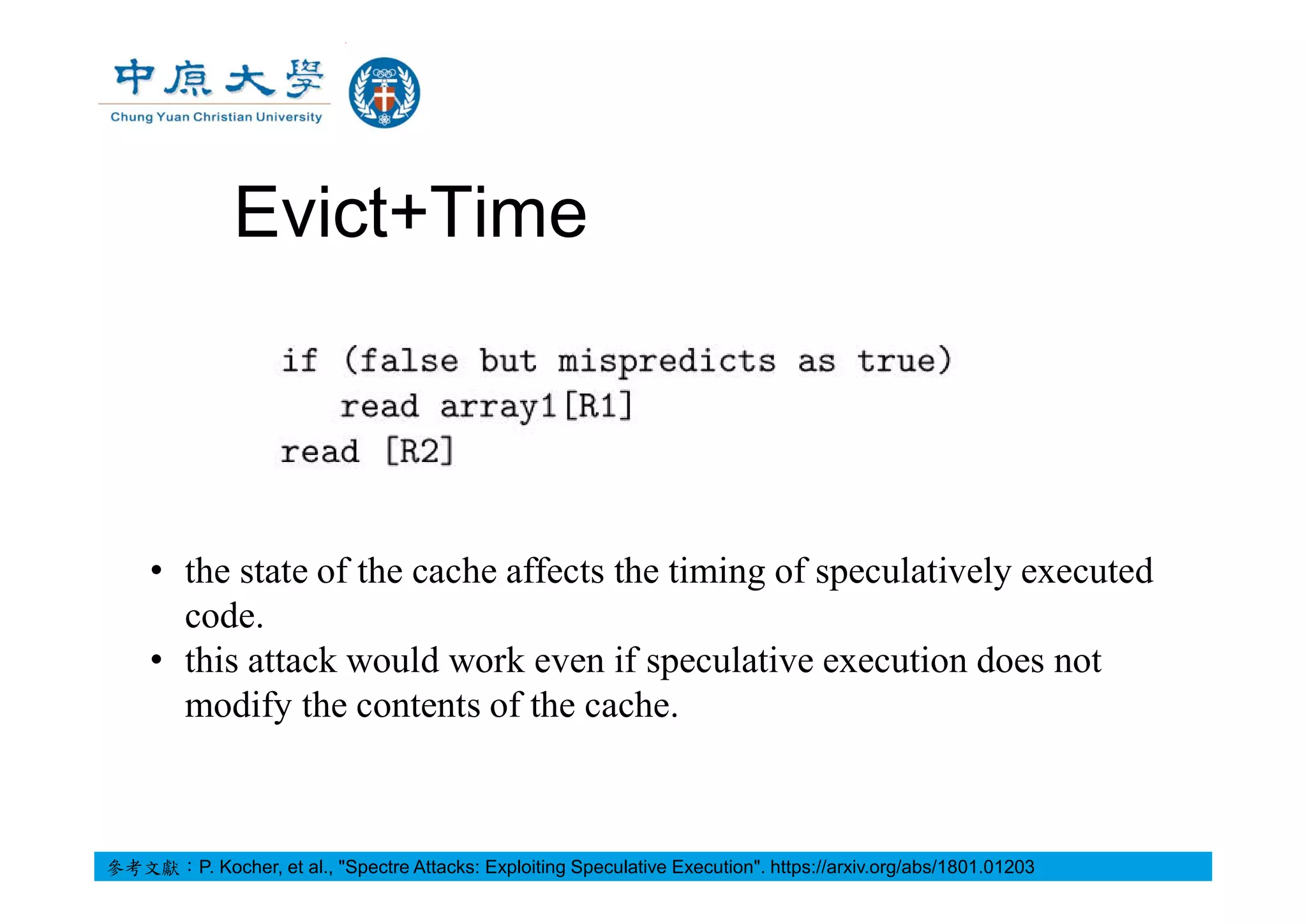
參考文獻:P. Kocher, et al., "Spectre Attacks: Exploiting Speculative Execution". https://arxiv.org/abs/1801.01203
• the value of x is maliciously chosen (and out-of- bounds) such
that array1[x] resolves to a secret byte k somewhere in the
victim’s memory.
• array1 size and array2 are not present in the processor’s cache,
but k is cached.
• previous operations received values of x that were valid, leading
the branch predictor to assume the if will likely be true.](https://image.slidesharecdn.com/random-180130061754/75/HITCON-FreeTalk-2018-27-2048.jpg)