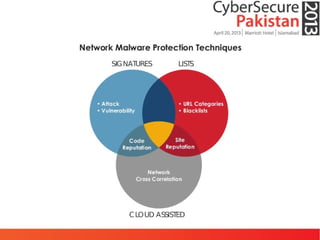
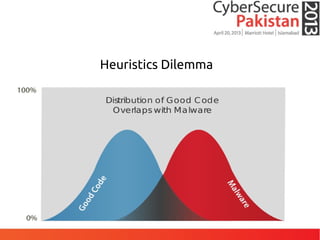
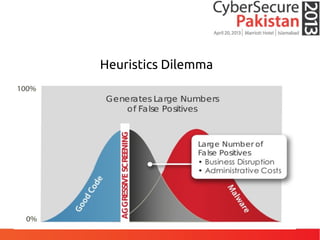
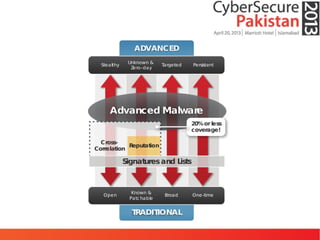
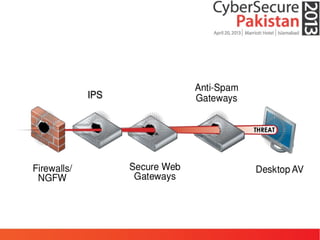
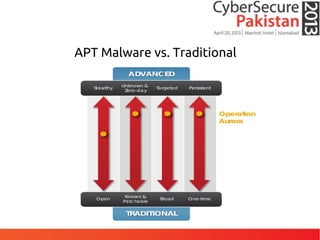
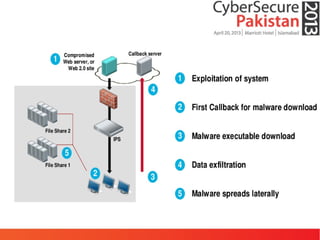
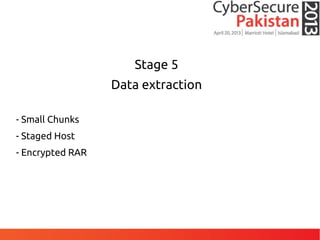
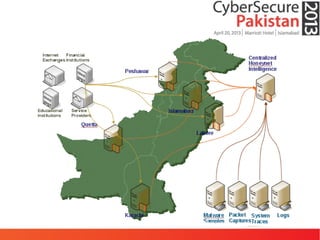
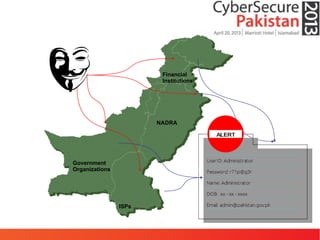
This document discusses advanced persistent threats (APTs) and malware, highlighting challenges facing traditional defenses. It notes that malware events occur every 3 minutes on average at organizations. The document outlines APT attack lifecycles involving exploitation, malware deployment, communication with command and control servers, and lateral movement. It also discusses case studies, forensic challenges posed by obfuscated code, and a signatureless next-generation threat protection approach.