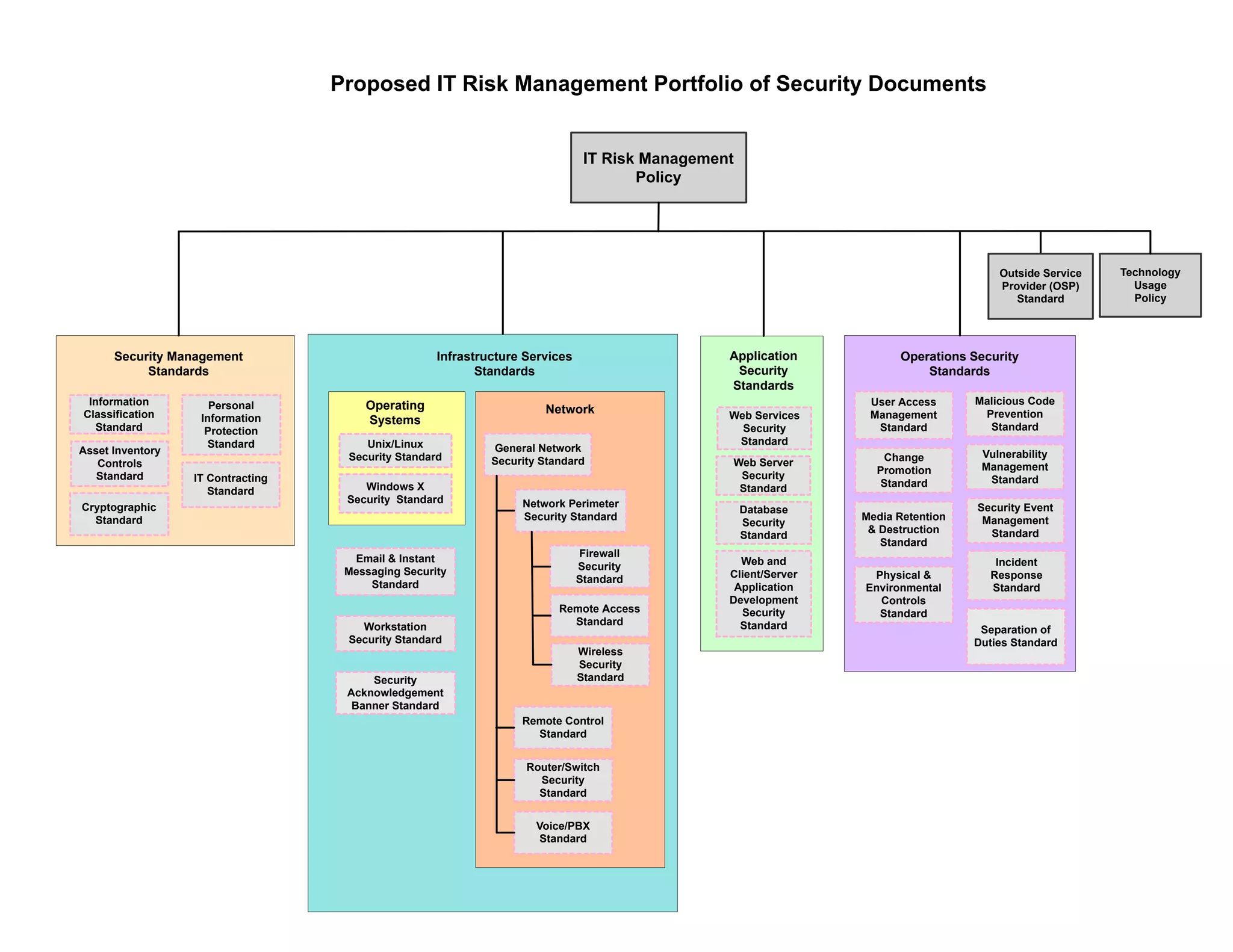
The document proposes a portfolio of security standards to manage IT risks across various domains. The portfolio includes over 30 security standards that cover areas like web application development, databases, networks, operating systems, infrastructure services, access management, malware prevention, and incident response. The standards are designed to establish policies and guidelines around the technology usage, assets, and operations within an organization.