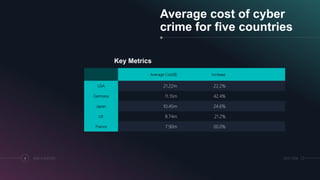
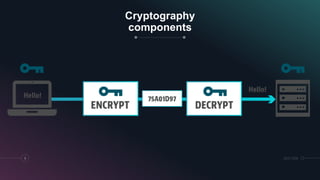
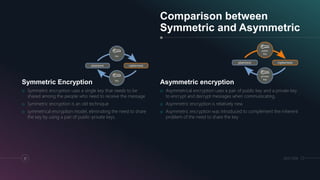
The presentation discusses network security, which consists of policies and practices to prevent unauthorized access to computer networks and resources. It highlights the increasing threat of cyberattacks, particularly in sectors like financial services and utilities, emphasizing the necessity for robust cybersecurity measures, including authentication and cryptography. The document also compares symmetric and asymmetric cryptography, detailing how each method secures data transmission.