Embed presentation
Download as PDF, PPTX




![Decomposing the PingAccess / Jenkins scenario
Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 6
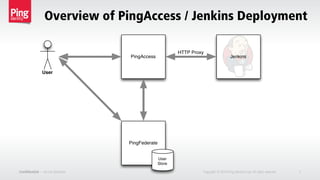
• HTTP Reverse Proxy deployment, therefore Jenkins is a Site.
• Jenkins is comprised of several URLs that will be defined as Resources within
an Application.
• Jenkins is equipped with a plugin[1] for authentication using HTTP Headers
via a Reverse Proxy. This is accomplished using Identity Mappings.
[1]https://wiki.jenkins-ci.org/display/JENKINS/Reverse+Proxy+Auth+Plugin](https://image.slidesharecdn.com/oyvalv0ztbypjdmrnuwn-signature-e77353a5531666e85fadeb0e4ebdcbd4e7522e2f525b50388570d11bd88051f3-poli-140804132128-phpapp02/85/CIS14-PingAccess-in-Action-6-320.jpg)


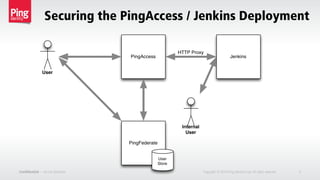

The document outlines a deployment scenario for integrating PingAccess with Jenkins as an identity-enabled HTTP reverse proxy to enhance authentication processes for users. It details the components involved, including identity mappings, a virtual host, and the use of PingFederate. The objective is to streamline user sign-ins and improve security in the Jenkins environment.





![Decomposing the PingAccess / Jenkins scenario
Confidential — do not distribute Copyright © 2014 Ping Identity Corp.All rights reserved. 6
• HTTP Reverse Proxy deployment, therefore Jenkins is a Site.
• Jenkins is comprised of several URLs that will be defined as Resources within
an Application.
• Jenkins is equipped with a plugin[1] for authentication using HTTP Headers
via a Reverse Proxy. This is accomplished using Identity Mappings.
[1]https://wiki.jenkins-ci.org/display/JENKINS/Reverse+Proxy+Auth+Plugin](https://image.slidesharecdn.com/oyvalv0ztbypjdmrnuwn-signature-e77353a5531666e85fadeb0e4ebdcbd4e7522e2f525b50388570d11bd88051f3-poli-140804132128-phpapp02/85/CIS14-PingAccess-in-Action-6-320.jpg)


