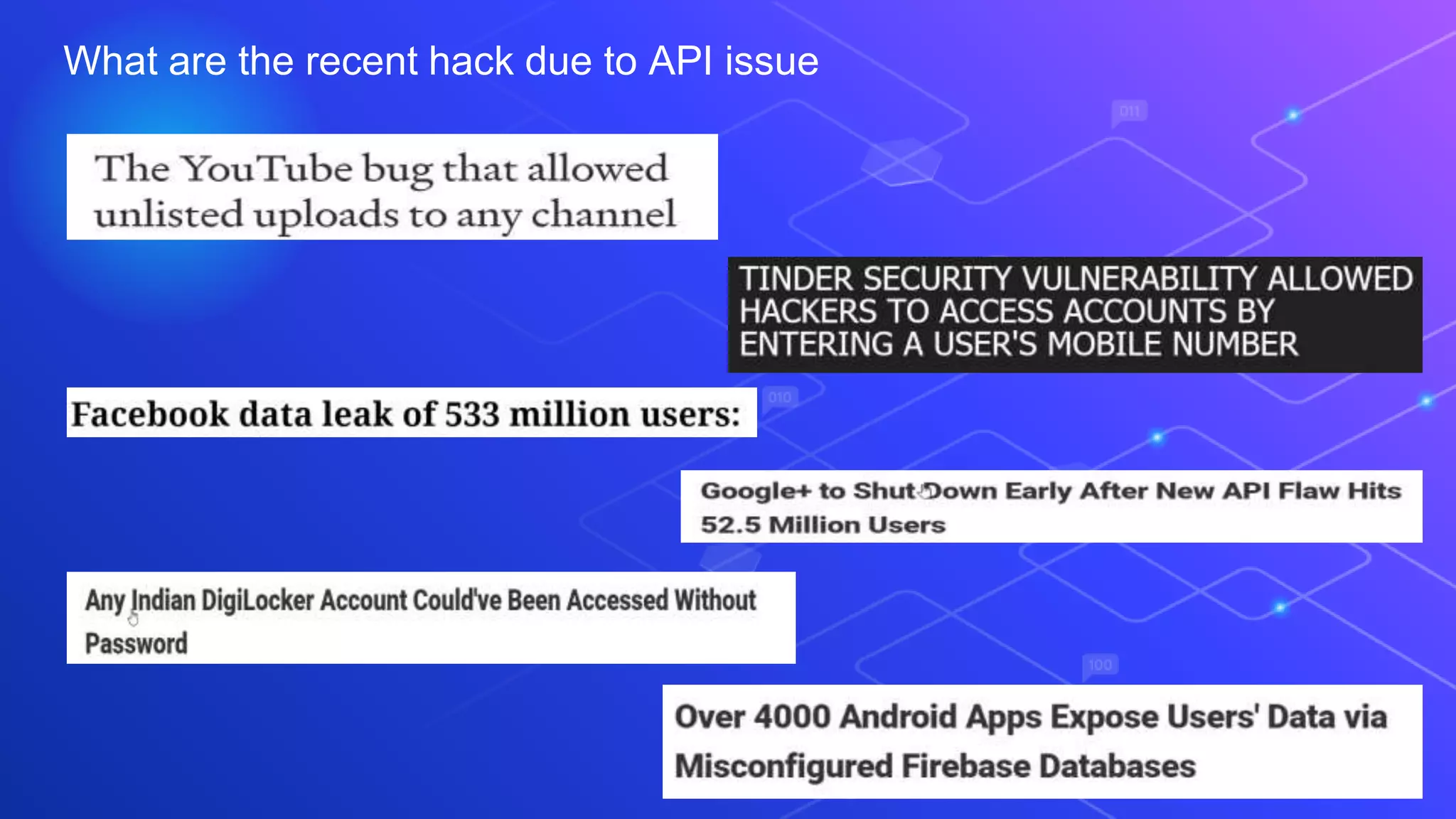
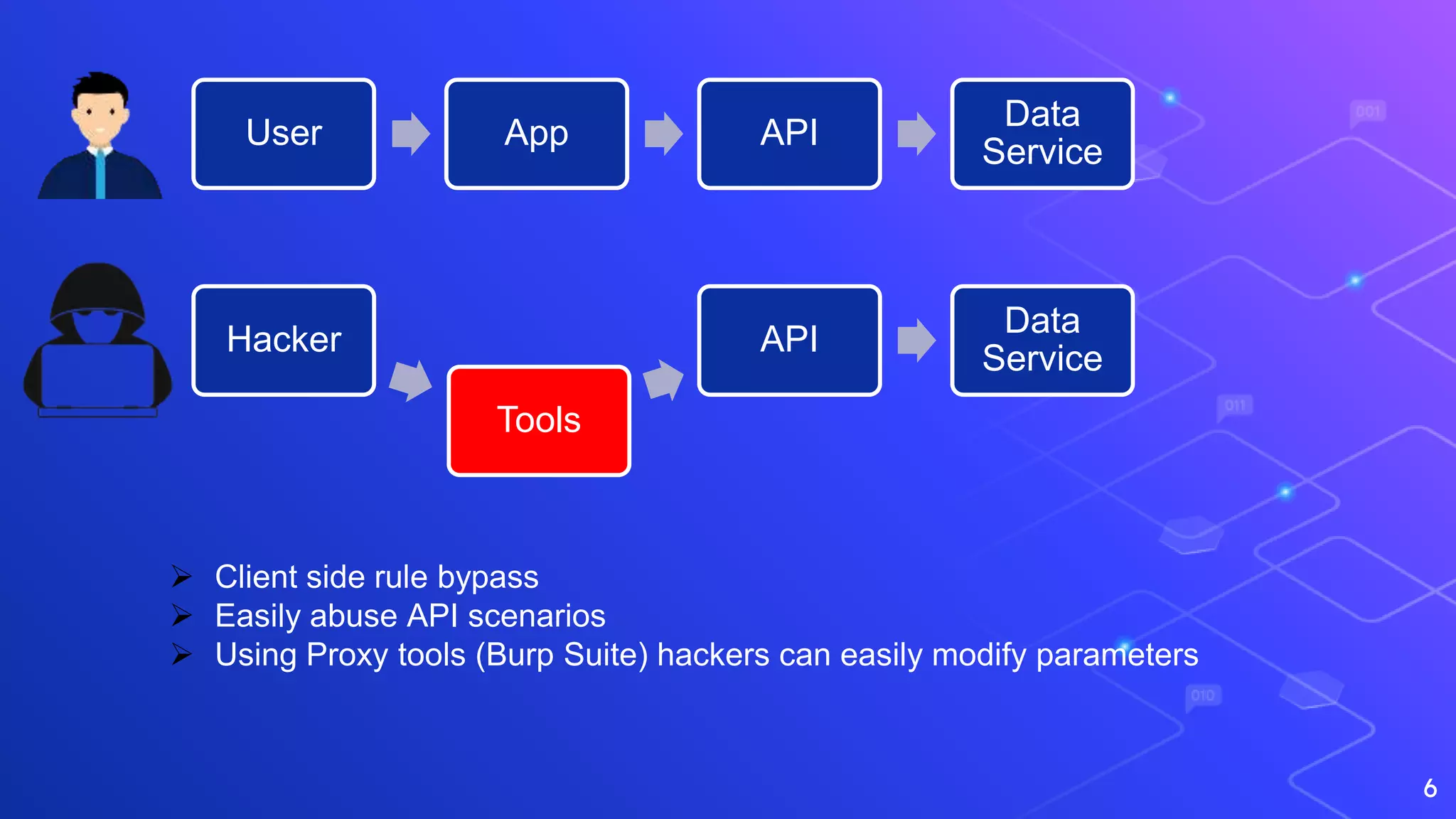
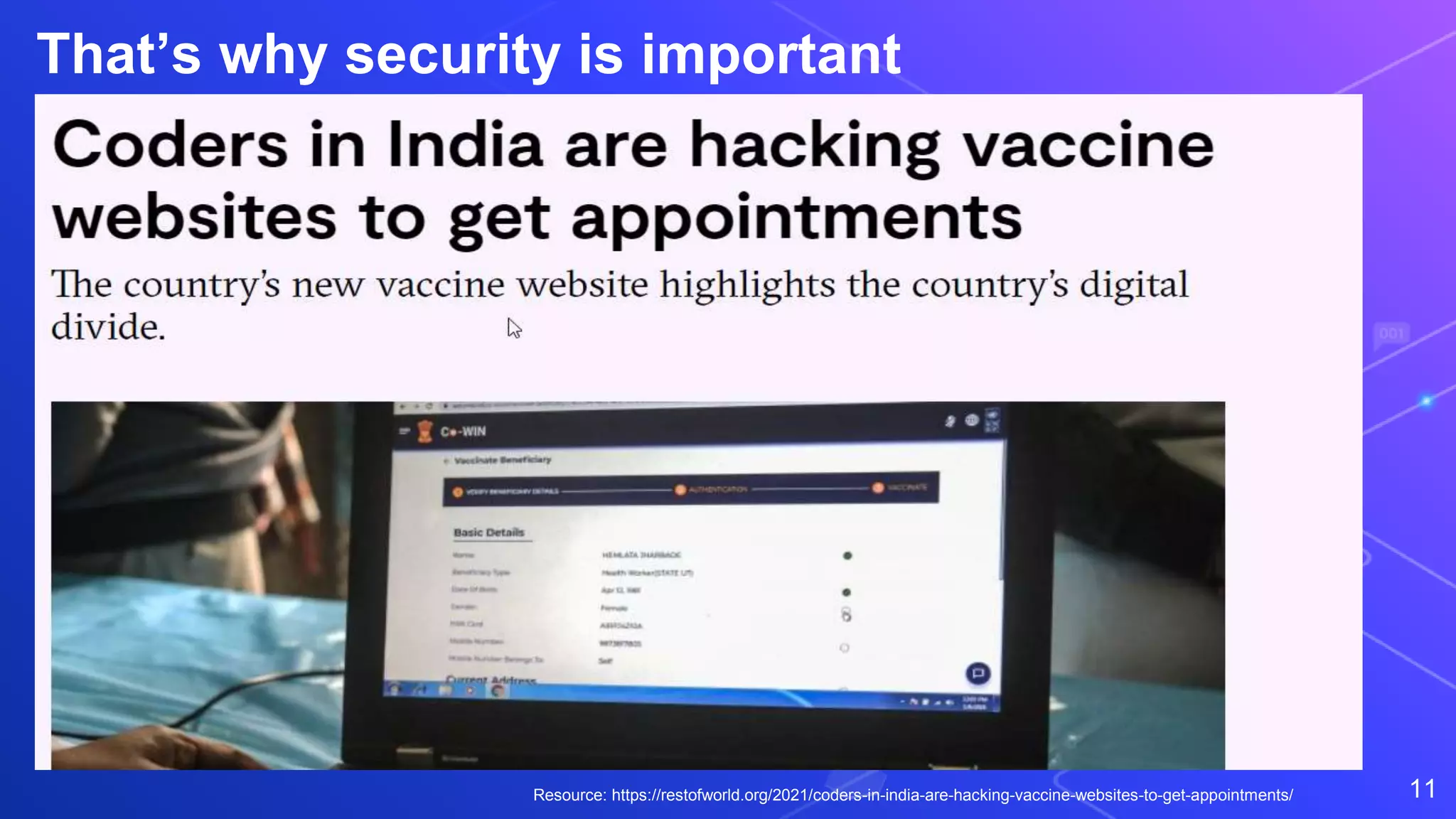
The document discusses API security from a hacker's perspective. It notes that exploiting APIs has become easier as infrastructure security has improved, but APIs themselves are often not properly secured. The main API vulnerabilities discussed are rate limiting issues, misconfigurations, injections, authentication and authorization bypassing, and flaws in business logic flows. Critical vulnerabilities that can give attackers control include authentication/authorization issues and business logic flows. The document emphasizes that penetration testing alone is not sufficient and continuous assessment of API security is needed to identify and address vulnerabilities.