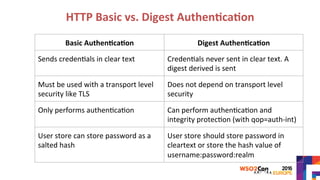
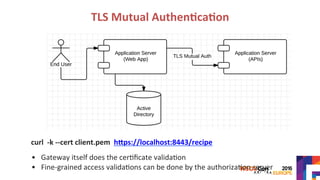
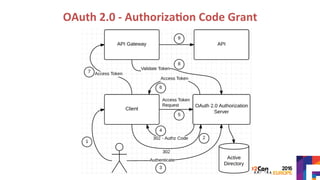
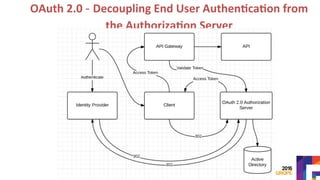
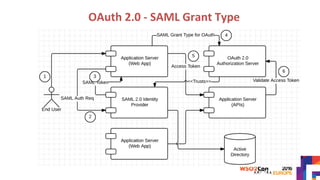
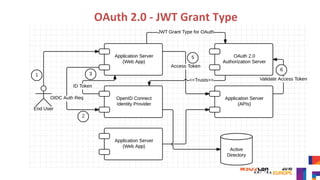
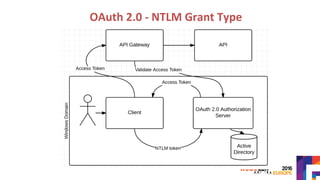
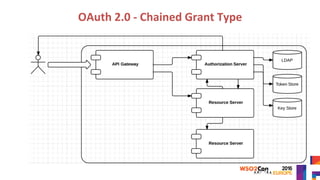
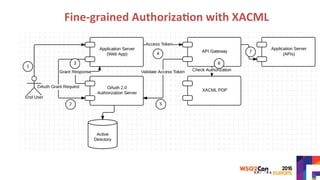
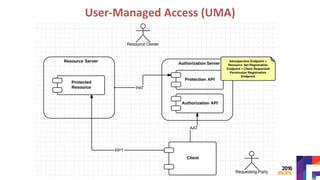
The document discusses securing APIs by outlining essential security attributes such as authentication, authorization, confidentiality, integrity, non-repudiation, auditing, and availability. It compares various authentication methods, particularly HTTP Basic and Digest authentication, and explains the use of OAuth for secure access to resources without sharing credentials. Additionally, it introduces User-Managed Access (UMA) for delegating access rights and emphasizes the importance of transport layer security, integrity measures, and audit logs for ensuring a secure API design.