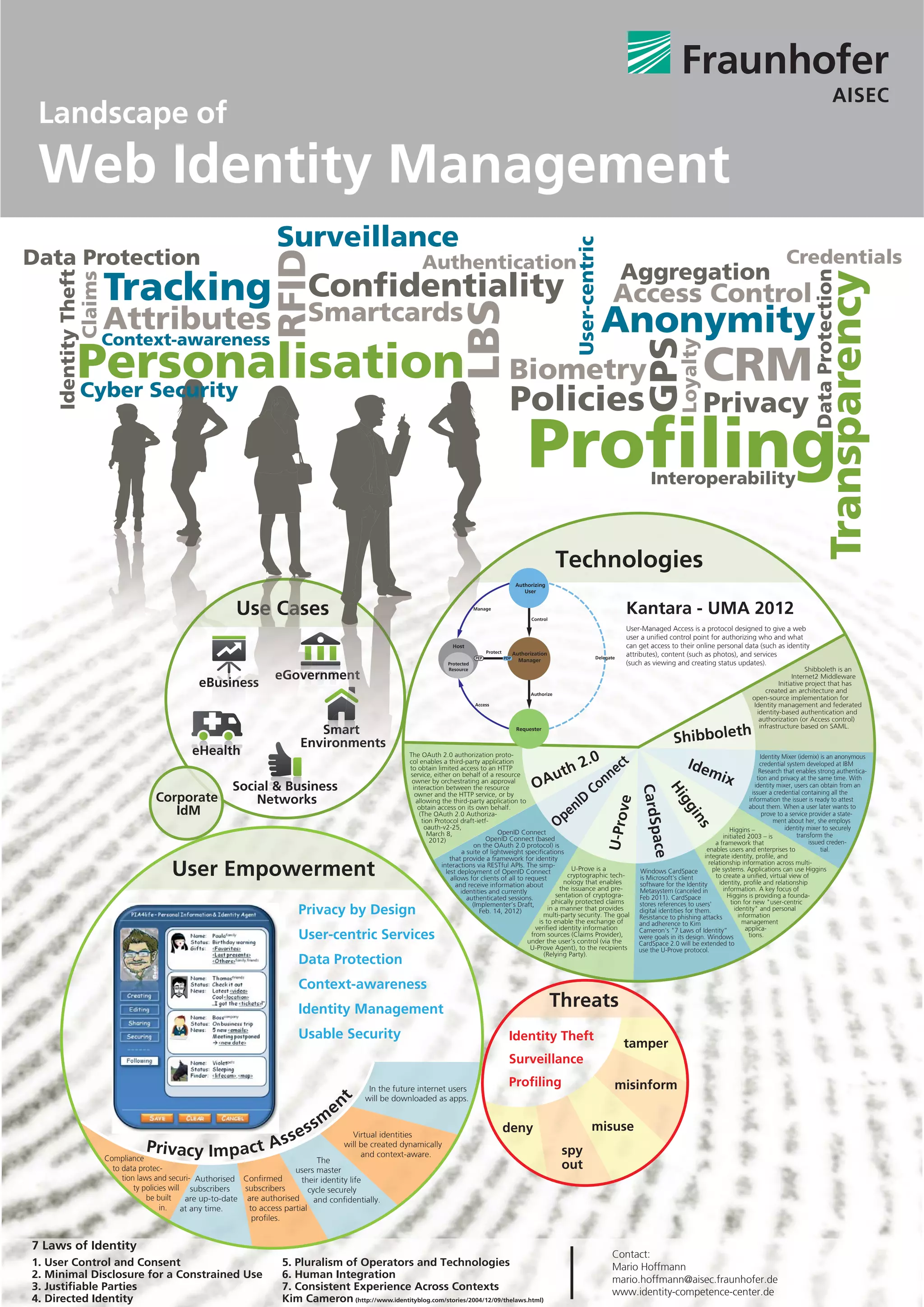
This document summarizes various technologies related to web identity management and user-centric data protection. It includes technologies for authentication, authorization, anonymity, credentials, access control, privacy, and identity federation. Formats include OAuth, OpenID Connect, U-Prove, Higgins, Shibboleth, and Idemix. Design principles are also covered, such as the 7 Laws of Identity and privacy by design. The landscape shows technologies that empower users to control their online identities and personal data.