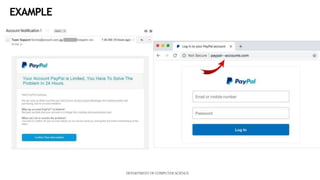
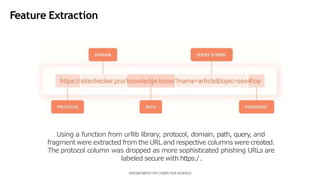
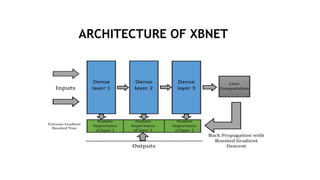
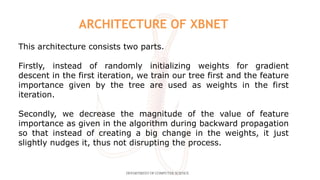
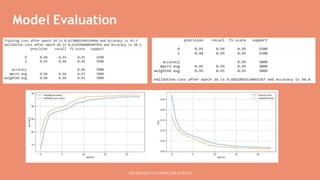
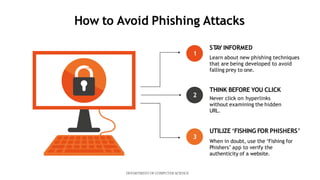
This document describes a mini project using an XBNet classifier to detect phishing attacks. XBNet is a combination of tree-based models and neural networks that is highly effective for tabular data classification. The project aims to help individuals identify phishing URLs to provide safer online practices. It extracts features from URLs and uses XBNet to classify them as legitimate or phishing. The model achieves good performance but is limited to tabular data and requires significant resources for training. Future work could focus on extending XBNet for unstructured data.