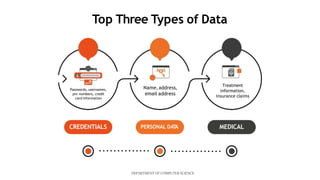
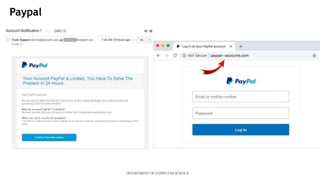
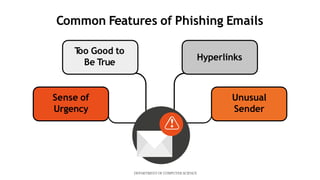
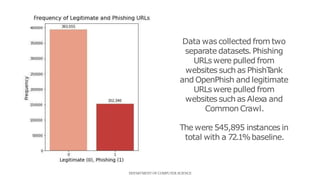
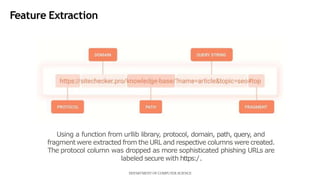
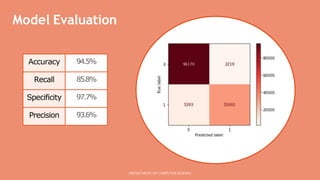
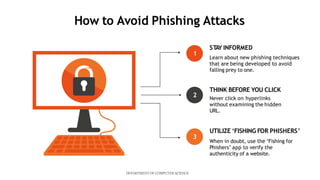
This document presents a mini project on phishing detection using machine learning. It discusses background information on phishing, data collection from phishing and legitimate URLs, pre-processing of the data including feature extraction, selection and evaluation of 10 machine learning models, and conclusions. The best performing model was found to be random forest classifier, achieving 94.5% accuracy, 85.8% recall, 97.7% specificity, and 93.6% precision on the test data. Recommendations are provided on how to avoid phishing attacks by staying informed, using tools to verify website authenticity, and thinking before clicking on links.