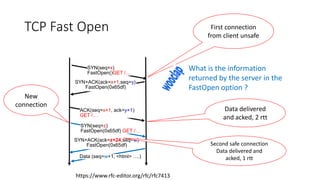
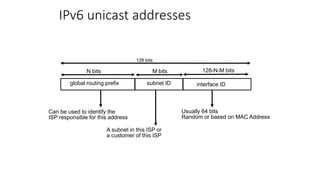
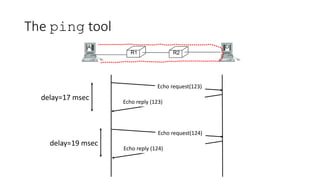
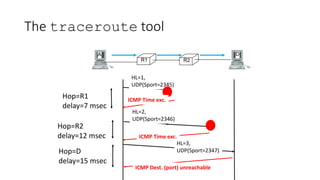
This document discusses modern TCP and IP protocols, highlighting improvements in TCP's three-way handshake, data transfer, and congestion control mechanisms. It covers enhancements like TCP Fast Open, Selective Acknowledgments, and the complexities of IPv6 addressing and packet formatting. Additionally, it addresses issues related to flow control, latency, and the significance of efficient TCP options and acknowledgments in network performance.