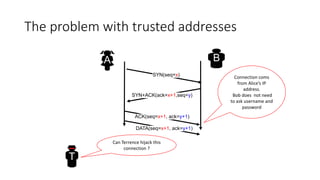
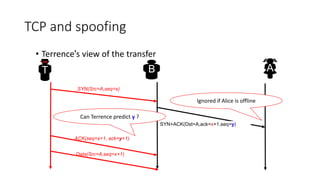
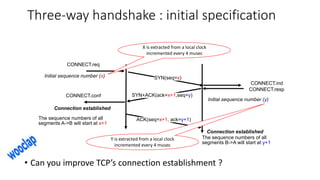
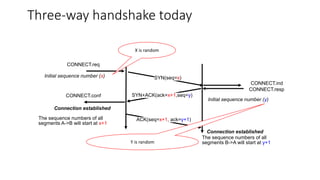
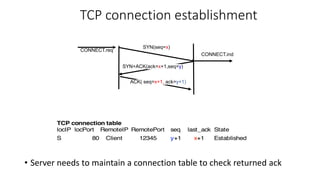
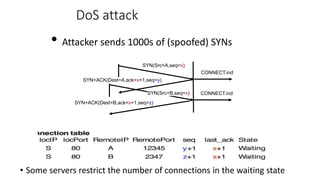
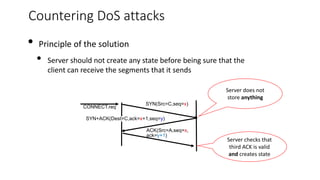
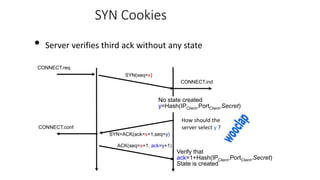
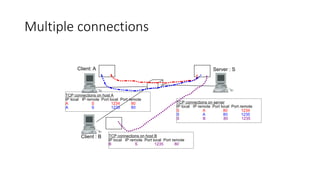
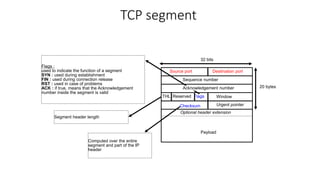
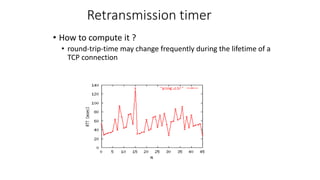
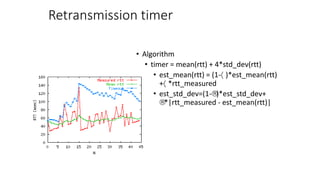
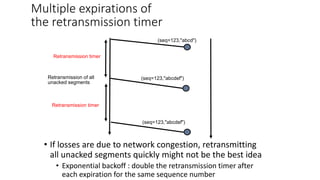
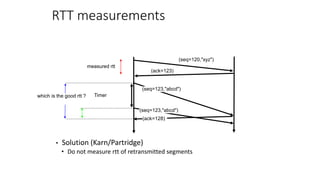
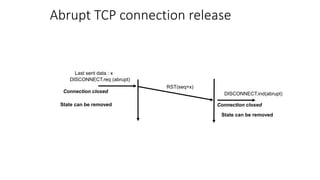
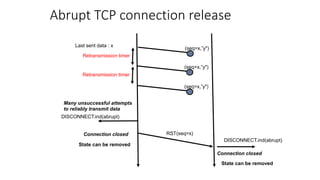
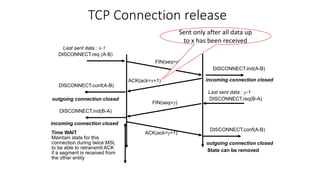
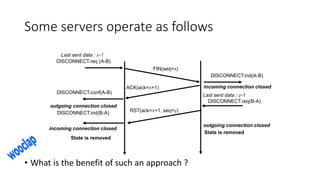
The document summarizes key aspects of TCP (Transmission Control Protocol) including connection establishment, data transfer, and connection release.
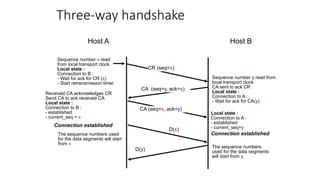
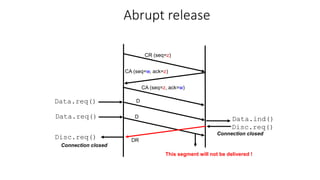
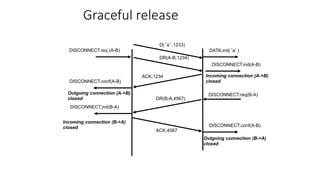
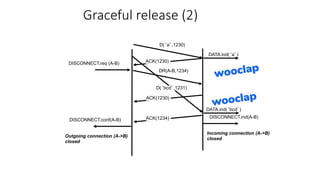
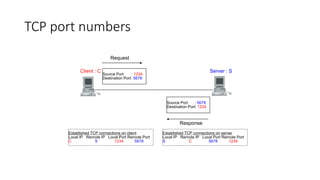
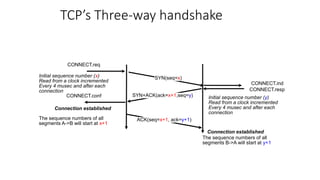
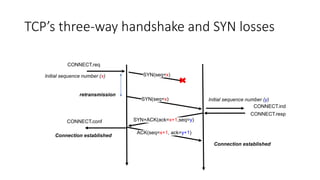
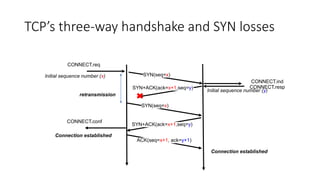
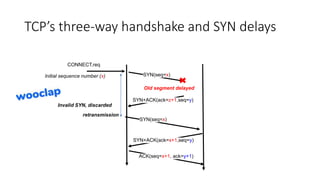
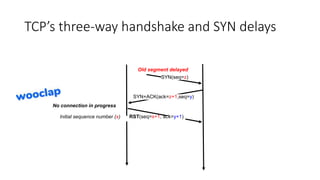
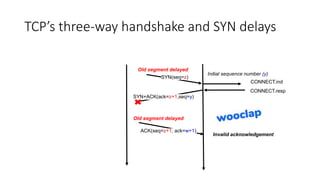
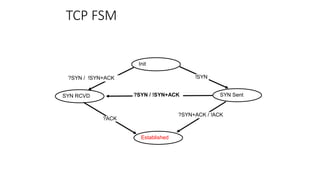
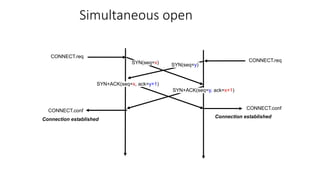
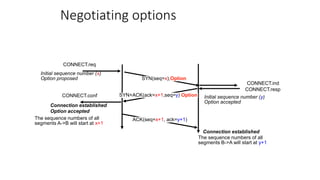
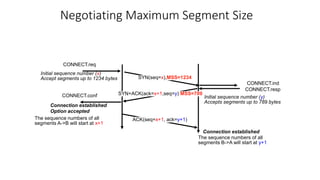
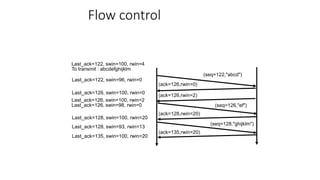
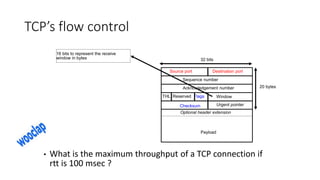
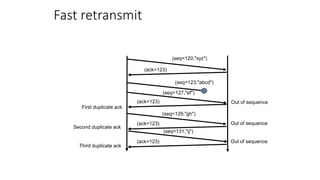
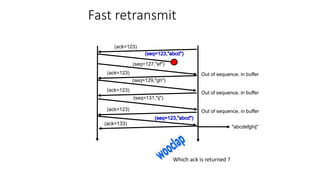
It describes TCP's three-way handshake used to reliably establish a connection with sequence numbers. It discusses how TCP provides reliable data transfer using acknowledgements, retransmissions, and flow control with a sliding window. It also covers how TCP handles connection release using FIN packets and the TIME_WAIT state to ensure all data is received before closing connections.










![TCP connection release
FIN Wait1
SYN RCVD
CLOSE Wait
Established
FIN Wait2
LAST-ACK
TIME Wait
Closing
Closed
?FIN/!ACK
!FIN
?ACK
Timeout[2MSL]
?FIN/!ACK
?ACK
!FIN
?ACK
?FIN/!ACK
!FIN](https://image.slidesharecdn.com/part4-reliable-tcp-230315124828-a39a1449/85/Part4-reliable-tcp-pptx-47-320.jpg)