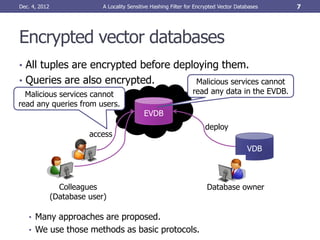
This document describes a locality sensitive hashing (LSH) filter for encrypted vector databases. The LSH filter allows cloud servers to filter database tuples without decrypting encrypted data, improving query efficiency. A whitening transformation is applied to encrypted vectors before inserting them into the LSH index to reduce skew in the vector space. When a query is received, the server computes the LSH of the encrypted query vector to identify candidate tuple groups for similarity checking based on the LSH hash values. Tuples with low estimated similarity are skipped, while those with high similarity have their actual encrypted similarity computed.










![Dec. 4, 2012 A Locality Sensitive Hashing Filter for Encrypted Vector Databases 12
Locality sensitive hashing (LSH)
• Approximate similarities with small data
• LSH consists of m functions: hi (I = 1, 2, …, m)
1; v・bi ≧ 0
hi(v) = (bi is the base vector of function hi)
0; otherwise
• LSH value of a vector v
• lsh(v) = (h1(v), h2(v), …, hm(v))
• Property
cos(u, v ) cos( (1 Pr[ lsh (u ) lsh ( v )]))
• Pr[lsh(u)=lsh(v)]:
how many hash values of the two vectors u and v have same values
i.e. hi(u) = hi(v)](https://image.slidesharecdn.com/paris2012kawamoto-121207050417-phpapp02/85/A-Locality-Sensitive-Hashing-Filter-for-Encrypted-Vector-Databases-12-320.jpg)
![Dec. 4, 2012 A Locality Sensitive Hashing Filter for Encrypted Vector Databases 13
Locality sensitive hashing (LSH)
• eg.
b1
• lsh(u) = (1, 1, 0) u
• lsh(v) = (1, 1, 1)
v
• Pr[lsh(u) = lsh(v)] = 2/3 b2
• cos(u, v) 〜 cos(π(1 – 2/3)) = 1/2
b3
• The accuracy of the approximation depends on
• the number of base vectors m
• the distribution of target vectors](https://image.slidesharecdn.com/paris2012kawamoto-121207050417-phpapp02/85/A-Locality-Sensitive-Hashing-Filter-for-Encrypted-Vector-Databases-13-320.jpg)








![Dec. 4, 2012 A Locality Sensitive Hashing Filter for Encrypted Vector Databases 22
Filtering
• After receiving queries, server computes lsh of quey vector
Estimate similarity between Compute lsh(Encq*(q))
Encq*(q) and this group by
Pr[(1,0,…,0)=lsh(Encq*(q))]
find Enck*(k) s.t.
Enck*(k)・Encq*(q)≧α*
LSH value tuple
(1, 0, ……, 0) ((1, 0, ….., 0), Enck*(k1), Encv(v1))
((1, 0, ….., 0), Enck*(k2), Encv(v2))
Database user
(1, 1, ……, 0) ((1, 1, ….., 0), Enck*(k1), Encv(v1))
where α* = α–μ・Encq(q)](https://image.slidesharecdn.com/paris2012kawamoto-121207050417-phpapp02/85/A-Locality-Sensitive-Hashing-Filter-for-Encrypted-Vector-Databases-22-320.jpg)
![Dec. 4, 2012 A Locality Sensitive Hashing Filter for Encrypted Vector Databases 23
Filtering
• After receiving queries, server computes lsh of quey vector
Estimate similarity between Compute lsh(Encq*(q))
Encq*(q) and this group by
Pr[(1,0,…,0)=lsh(Encq*(q))]
find Enck*(k) s.t.
Enck*(k)・Encq*(q)≧α*
LSH value tuple
(1, 0, ……, 0) ((1, 0, ….., 0), Enck*(k1), Encv(v1))
If the estimated similarity <α*, ((1, 0, ….., 0), Enck*(k2), Encv(v2))
skip this group
Database user
(1, 1, ……, 0) ((1, 1, ….., 0), Enck*(k1), Encv(v1))
where α* = α–μ・Encq(q)](https://image.slidesharecdn.com/paris2012kawamoto-121207050417-phpapp02/85/A-Locality-Sensitive-Hashing-Filter-for-Encrypted-Vector-Databases-23-320.jpg)
![Dec. 4, 2012 A Locality Sensitive Hashing Filter for Encrypted Vector Databases 24
Filtering
• After receiving queries, server computes lsh of quey vector
Estimate similarity between Compute lsh(Encq*(q))
Encq*(q) and this group by
Pr[(1,1,…,0)=lsh(Encq*(q))]
find Enck*(k) s.t.
Enck*(k)・Encq*(q)≧α*
LSH value tuple
(1, 0, ……, 0) ((1, 0, ….., 0), Enck*(k1), Encv(v1))
((1, 0, ….., 0), Enck*(k2), Encv(v2))
Database user
(1, 1, ……, 0) ((1, 1, ….., 0), Enck*(k1), Encv(v1))
where α* = α–μ・Encq(q)](https://image.slidesharecdn.com/paris2012kawamoto-121207050417-phpapp02/85/A-Locality-Sensitive-Hashing-Filter-for-Encrypted-Vector-Databases-24-320.jpg)
![Dec. 4, 2012 A Locality Sensitive Hashing Filter for Encrypted Vector Databases 25
Filtering
• After receiving queries, server computes lsh of quey vector
Estimate similarity between Compute lsh(Encq*(q))
Encq*(q) and this group by
Pr[(1,1,…,0)=lsh(Encq*(q))]
find Enck*(k) s.t.
Enck*(k)・Encq*(q)≧α*
LSH value tuple
(1, 0, ……, 0) ((1, 0, ….., 0), Enck*(k1), Encv(v1))
If the estimated similarity ≧α*,
((1, 0, ….., 0), Enck*(k2), Encv(v2))
check the actual query condition
for all tuples in this group
Database user
(1, 1, ……, 0) ((1, 1, ….., 0), Enck*(k1), Encv(v1))
where α* = α–μ・Encq(q)](https://image.slidesharecdn.com/paris2012kawamoto-121207050417-phpapp02/85/A-Locality-Sensitive-Hashing-Filter-for-Encrypted-Vector-Databases-25-320.jpg)
![Dec. 4, 2012 A Locality Sensitive Hashing Filter for Encrypted Vector Databases 26
Filtering
• After receiving queries, server computes lsh of quey vector
Estimate similarity between Compute lsh(Encq*(q))
Encq*(q) and this group by
Pr[(1,1,…,0)=lsh(Encq*(q))]
find Enck*(k) s.t.
Enck*(k)・Encq*(q)≧α*
LSH value tuple
(1, 0, ……, 0) ((1, 0, ….., 0), Enck*(k1), Encv(v1))
If the estimated similarity ≧α*,
((1, 0, ….., 0), Compute), Encv(v2))
Enck*(k2
check the actual query condition
for all tuples in this group Enck*(k)・Encq*(q)
Database user
(1, 1, ……, 0) ((1, 1, ….., 0), Enck*(k1), Encv(v1))
We can omit to computing similarity for less similar vectors
where α* = α–μ・Encq(q)](https://image.slidesharecdn.com/paris2012kawamoto-121207050417-phpapp02/85/A-Locality-Sensitive-Hashing-Filter-for-Encrypted-Vector-Databases-26-320.jpg)








