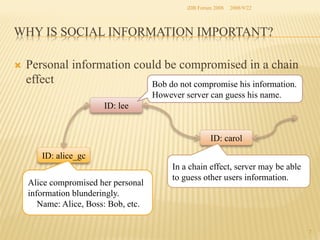
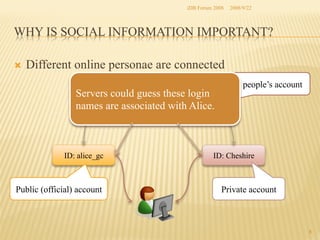
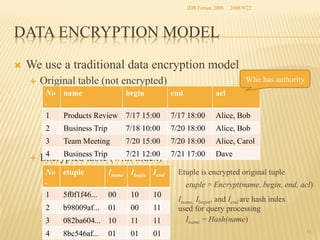
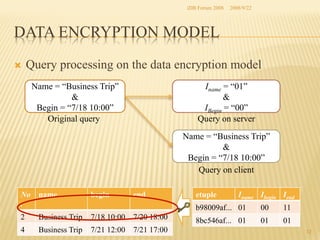
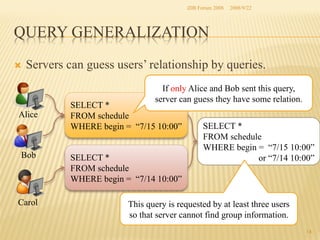
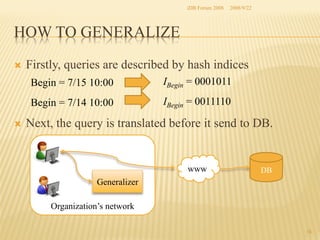
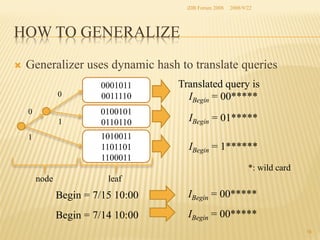
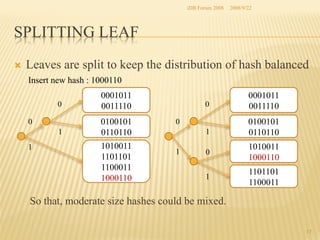
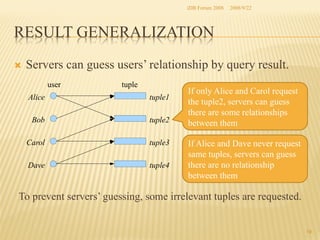
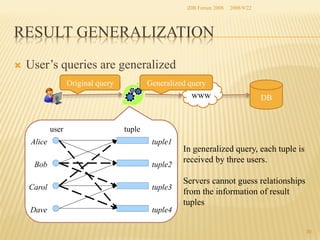
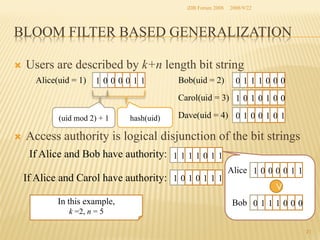
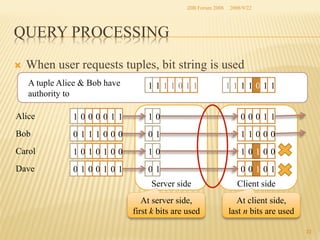
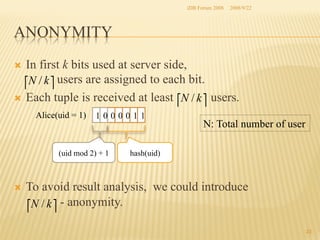
The document presents two methods for securing social information when databases are outsourced: Query Generalization by Dynamic Hash and Result Generalization by Bloom Filter. Queries are generalized through dynamic hashing to mix user queries and prevent determining relationships. Results are generalized using Bloom filters by including irrelevant tuples to mask which users requested the same tuples. The goal is to protect users' social information and relationships from being discovered by the outsourced database provider. Future work involves implementing and evaluating these methods on a real outsourced database service.