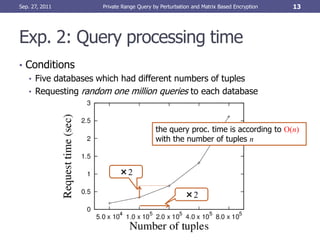
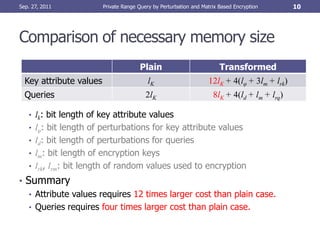
This document proposes a new method called Inner Product Predicate (IPP) for performing private range queries over encrypted data. The IPP method adds perturbations to attribute values and queries through matrix-based encryption to prevent frequency analysis attacks. Experimental results show the transformed query distributions are different from the originals and query processing time is linear in the number of tuples. Open problems remain around reducing computational costs and defending against attacks using aggregate query results.




![Sep. 27, 2011 Private Range Query by Perturbation and Matrix Based Encryption 7
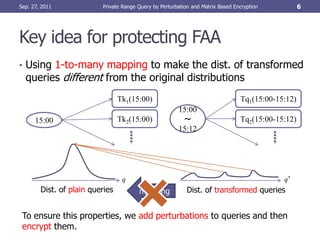
Inner Product Predicate (IPP) method
• Employs polynomials f(k) as queries to add perturbations
• Query [a, b] is described as f(k) ≤ 0 with perturbation r.
f(k) NOT match f(k)
match
-r’ 0
a b k
-r 0 k
a b Different r produces different query.
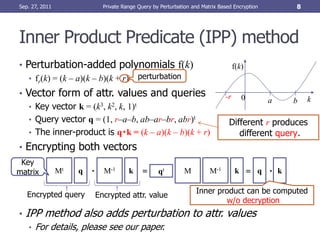
• Uses matrix based encryption
• Matrix based encryption enables query processing w/o decryption
• Query f(k) ≤ 0 are expressed by vector q, k as q・k ≤ 0
• Encryption key is a regular matrix M
• q and k are encrypted as Mtq and M-1k
• The inner product is computed as Mtq・M-1k = qtMM-1k = q・k
canceled](https://image.slidesharecdn.com/kawamotoicdim2011slide-111002020732-phpapp02/85/Private-Range-Query-by-Perturbation-and-Matrix-Based-Encryption-7-320.jpg)


![Sep. 27, 2011 Private Range Query by Perturbation and Matrix Based Encryption 12
Exp. 1: Correlations of queries
• Query set
• 1,000 queries which requested [a, a + 100] (a : 1, 2, ・ ・ ・ , 1000).
A range query [500, 600] is mapped to 3.0×1013
Transformed queries
This graph shows only 1st
elem. of query vectors
Query vectors were distributed in
wide range without depending the
plain values.
Left side of plain range queries
• Coefficient of correlations: 0.014679](https://image.slidesharecdn.com/kawamotoicdim2011slide-111002020732-phpapp02/85/Private-Range-Query-by-Perturbation-and-Matrix-Based-Encryption-12-320.jpg)