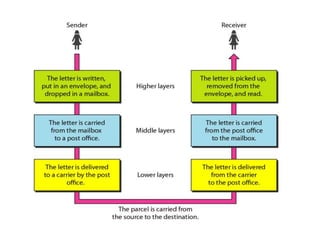
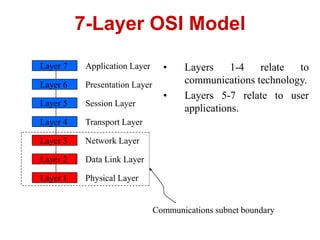
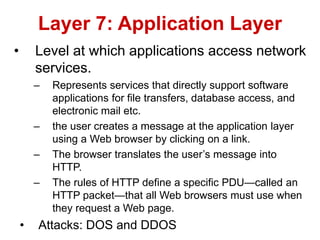
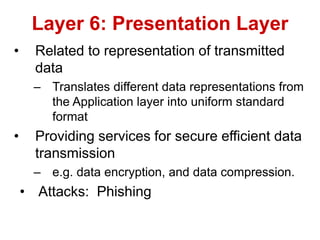
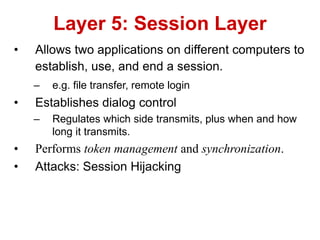
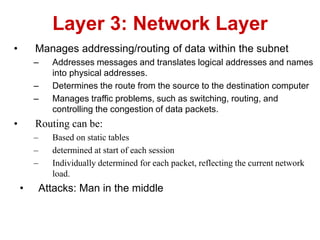
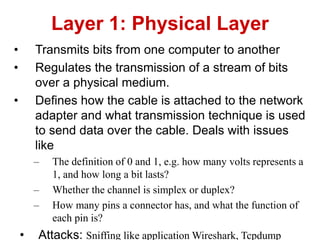
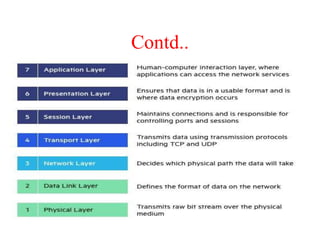
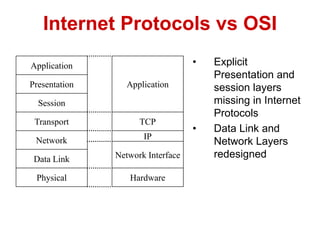
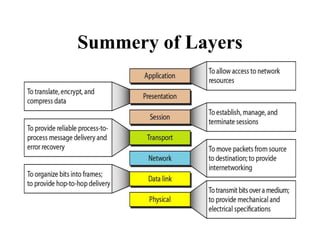
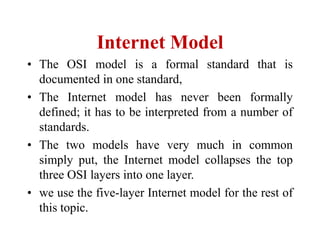
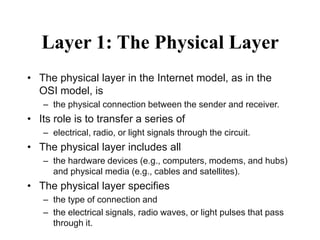
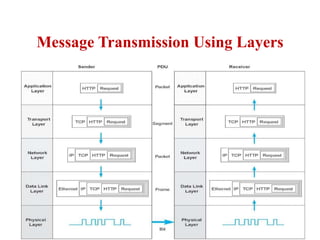
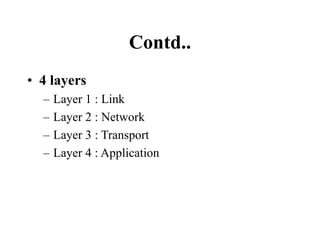
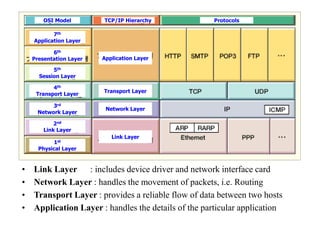
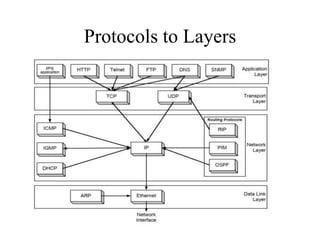
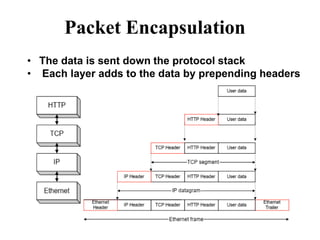
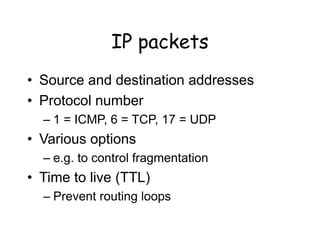
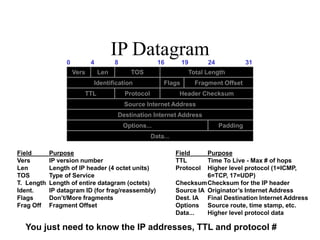
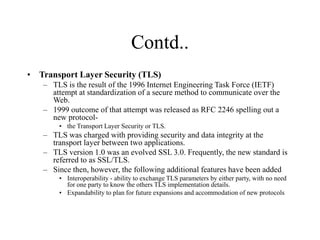
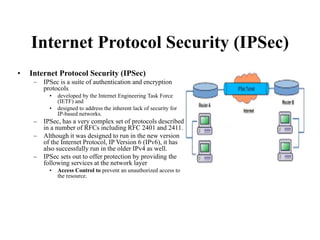
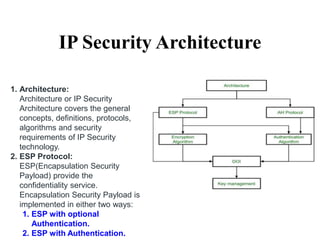
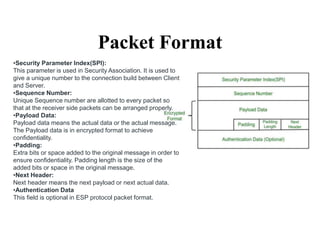
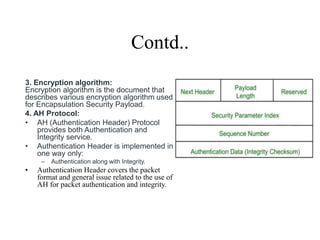
The document discusses network security models and the OSI reference model. It describes the seven layers of the OSI model from the physical layer to the application layer. It then discusses the TCP/IP reference model and its four layers from the link layer to the application layer. The document summarizes key protocols associated with each layer, including IP, TCP, UDP, and protocols that provide security at the transport and network layers like SSL/TLS and IPSec.