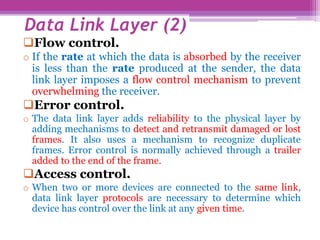
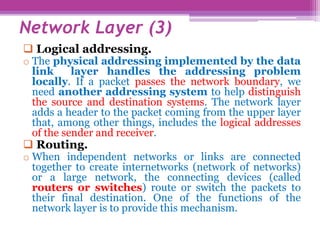
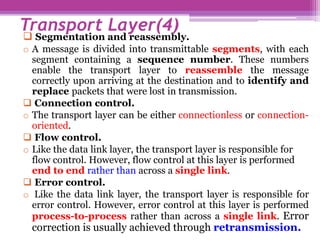
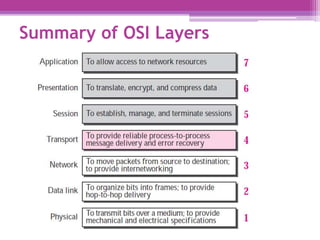
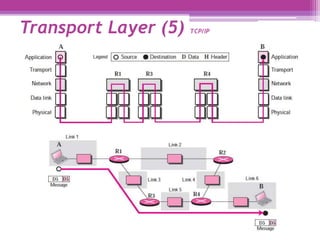
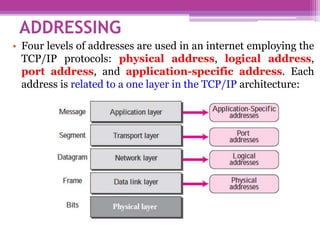
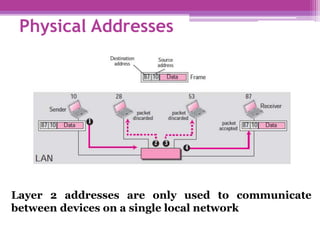
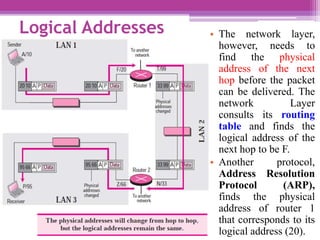
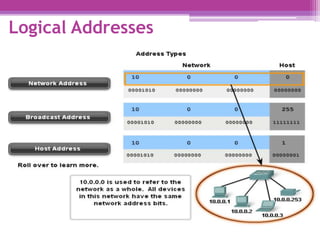
The document discusses the OSI model and the TCP/IP protocol suite, outlining their layered architecture and interrelationships between different layers. While the OSI model was intended for standardization in data communications, the TCP/IP protocol suite became the dominant model due to its extensive use in the internet. Key differences between the two models are highlighted, particularly the absence of session and presentation layers in TCP/IP, and the roles each layer plays in facilitating communication across networks.