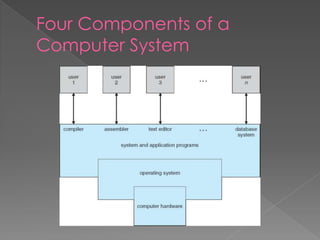
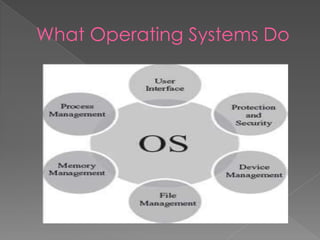
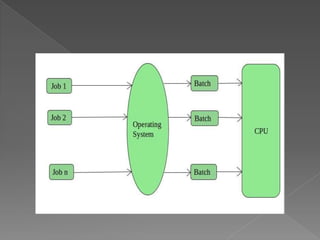
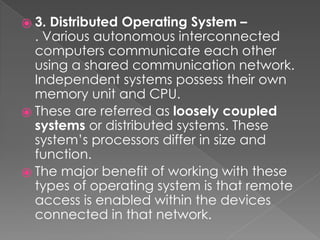
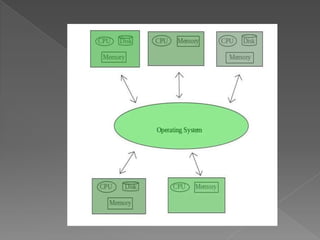
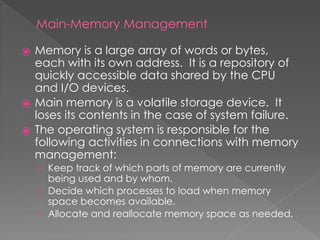
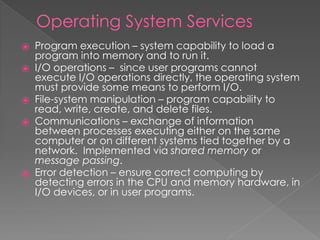
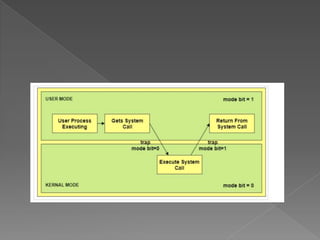
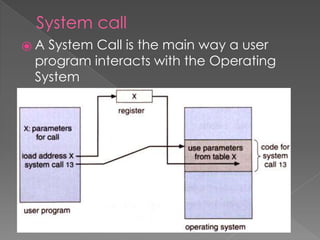
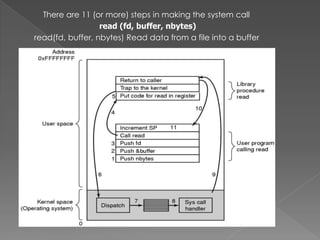
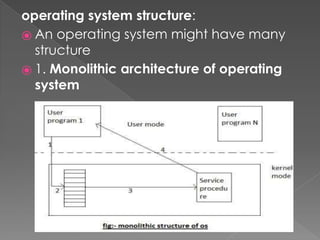
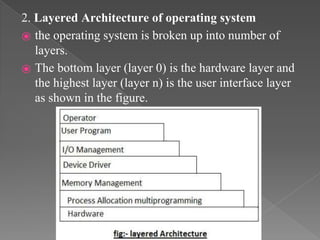
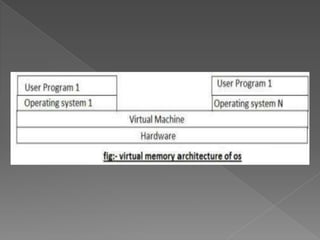
This document provides an overview of operating systems, including their objectives, components, functions, and structures. It describes what an operating system is and its main goals of executing programs, making the computer convenient to use, and using hardware efficiently. The major components covered include process management, memory management, file management, and more. Different types of operating systems are explored such as batch, time-sharing, distributed, real-time, and network operating systems. Operating system structures like monolithic and layered architectures are also summarized.