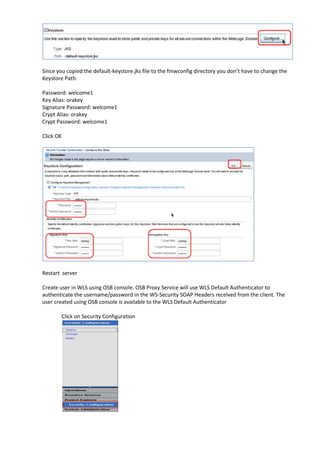
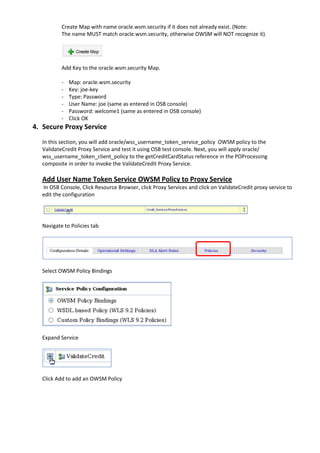
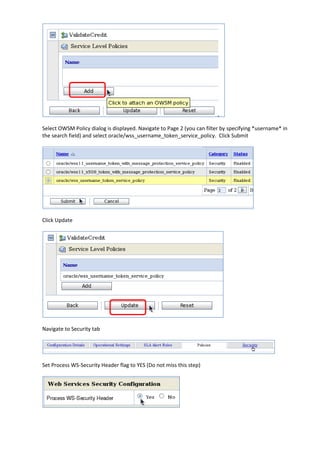
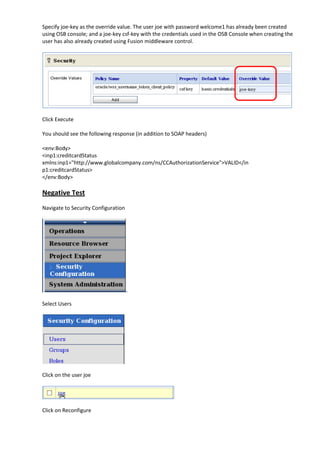
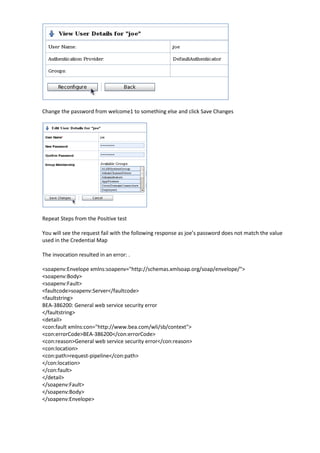
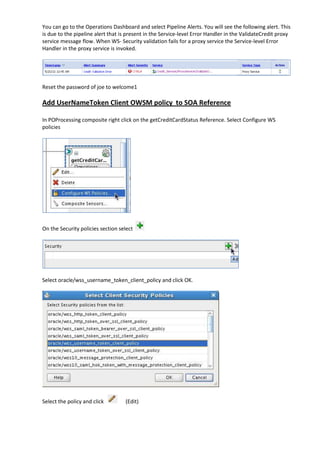
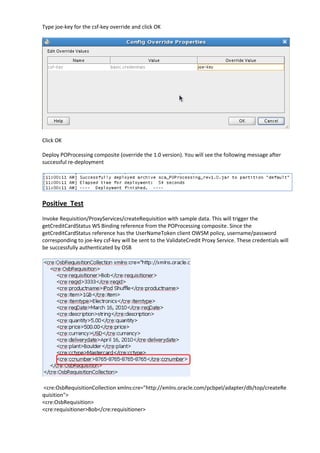
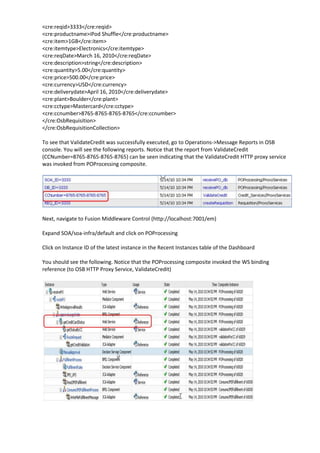
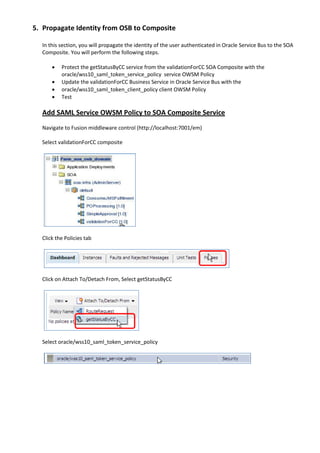
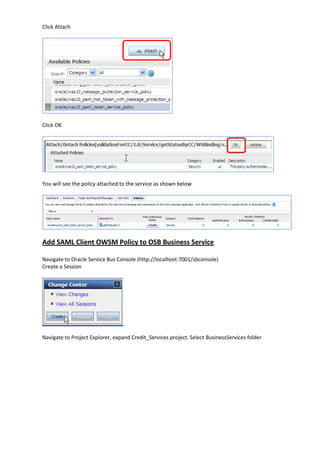
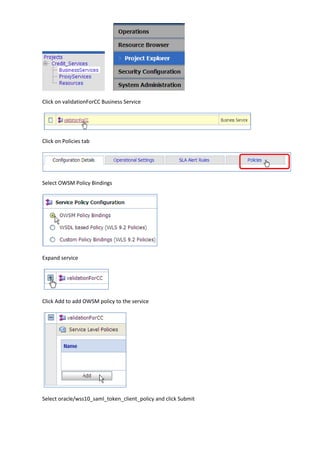
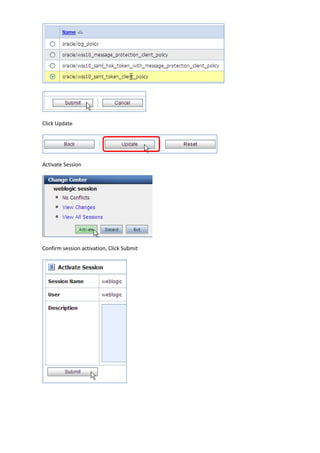
The document describes how to leverage Oracle Service Bus and SOA Composite to invoke a proxy service requiring user name token authentication from a SOA composite and propagate the identity of the authenticated user from Oracle Service Bus to the SOA composite. Specifically, it involves securing a ValidateCredit proxy service with a username token policy, invoking it from a SOA composite by adding a username token client policy to a reference, and propagating the authenticated user's identity to another SOA composite using SAML policies.