Embed presentation
Download as PDF, PPTX


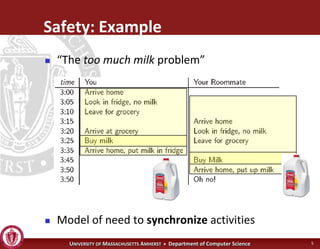
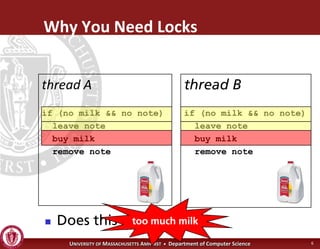




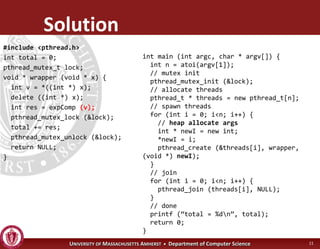

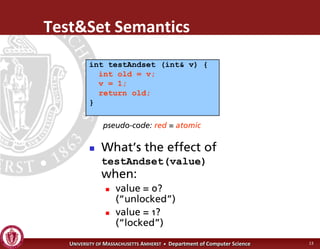
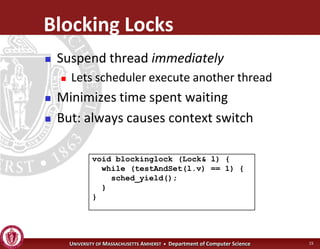
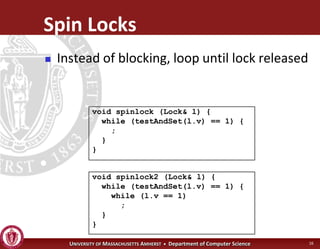


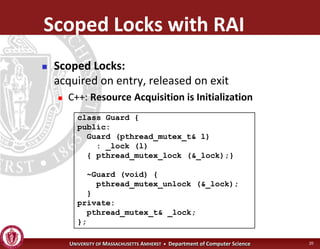


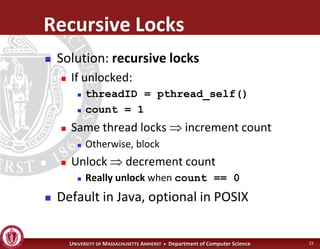
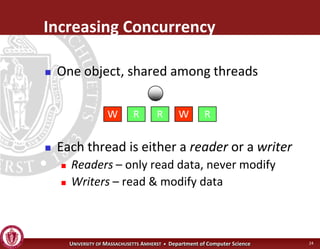
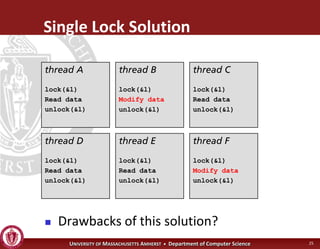

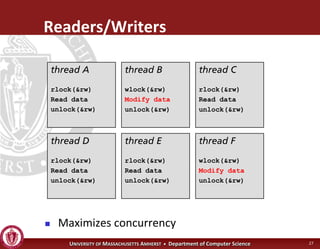




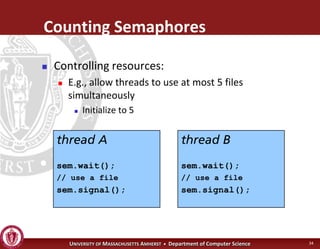



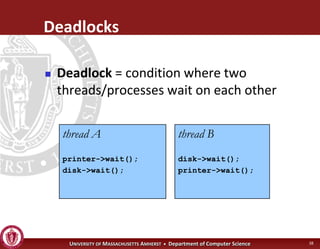
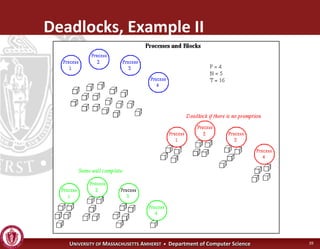

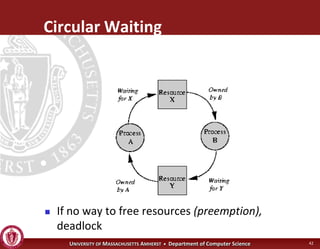
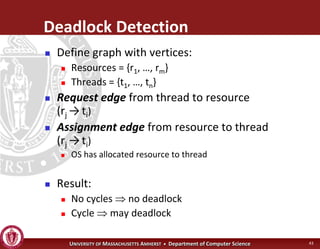
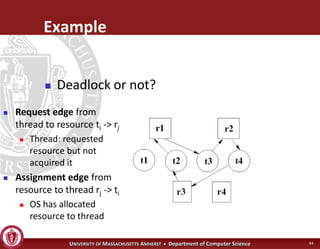
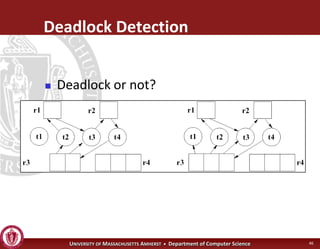
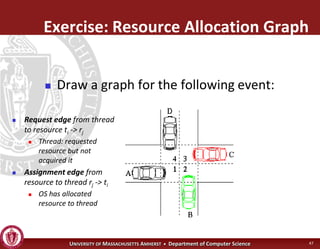
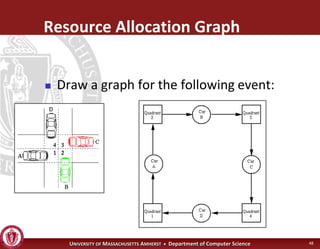
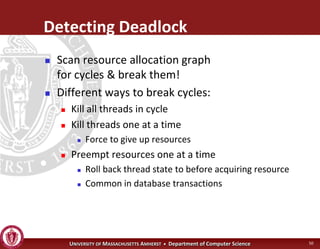







This document discusses synchronization in operating systems and computer science. It covers topics like locks, mutexes, semaphores, and condition variables. Locks are used for mutual exclusion to ensure only one thread accesses a critical section at a time. Semaphores generalize locks and can be used to coordinate threads and signal events. Readers-writer locks allow multiple reader threads but only one writer thread for optimization. Common synchronization issues like deadlocks, priority inversion, and failures to unlock are also addressed.























































