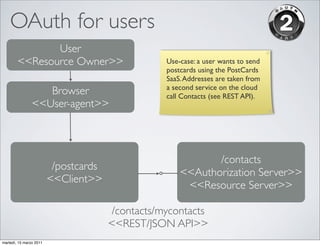
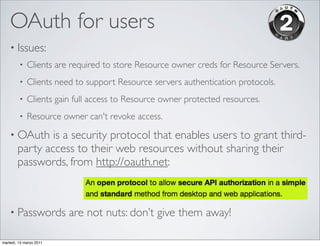
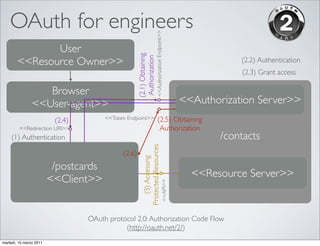
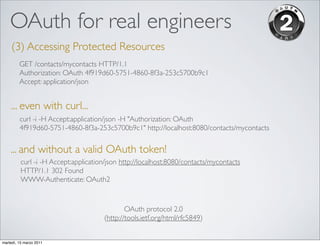
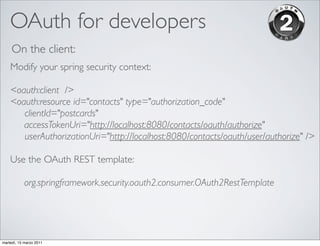
OpenID and OAuth are protocols for online identity and authorization. OpenID allows users to sign in to multiple websites using a single digital identity. It provides single sign-on capabilities. OAuth allows websites and applications to access protected resources from another service, without requiring users to share their passwords. It enables authorization for third party applications to access protected resources. Both protocols address common needs around user authentication and authorization on the web.

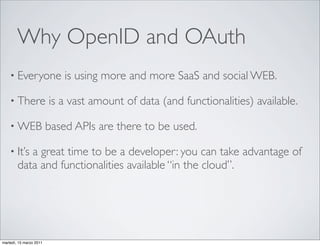




![OpenID for engineers
(2) Normalization,
Discovery of OP endpoint (5) Authentication
(7) Verification
(3) Association OpenID
Relying Party
Provider
(4) Authentication request:
HTTP 302
(6) Authentication response:
HTTP 302 + Assertion
(1) Initiation: HTTP POST [positive, negative]
openid_identifier
User-agent
OpenID Authentication protocol 2.0
(http://openid.net/developers/specs/)
martedì, 15 marzo 2011](https://image.slidesharecdn.com/openidandoauthv3-110517025030-phpapp01/85/OpenID-and-OAuth-12-320.jpg)




![]]>
</OpenID>
<!-- Here we begin with OAuth -->
<OAuth terminology="OAuth">
<








![]]>
</OAuth>
martedì, 15 marzo 2011](https://image.slidesharecdn.com/openidandoauthv3-110517025030-phpapp01/85/OpenID-and-OAuth-32-320.jpg)