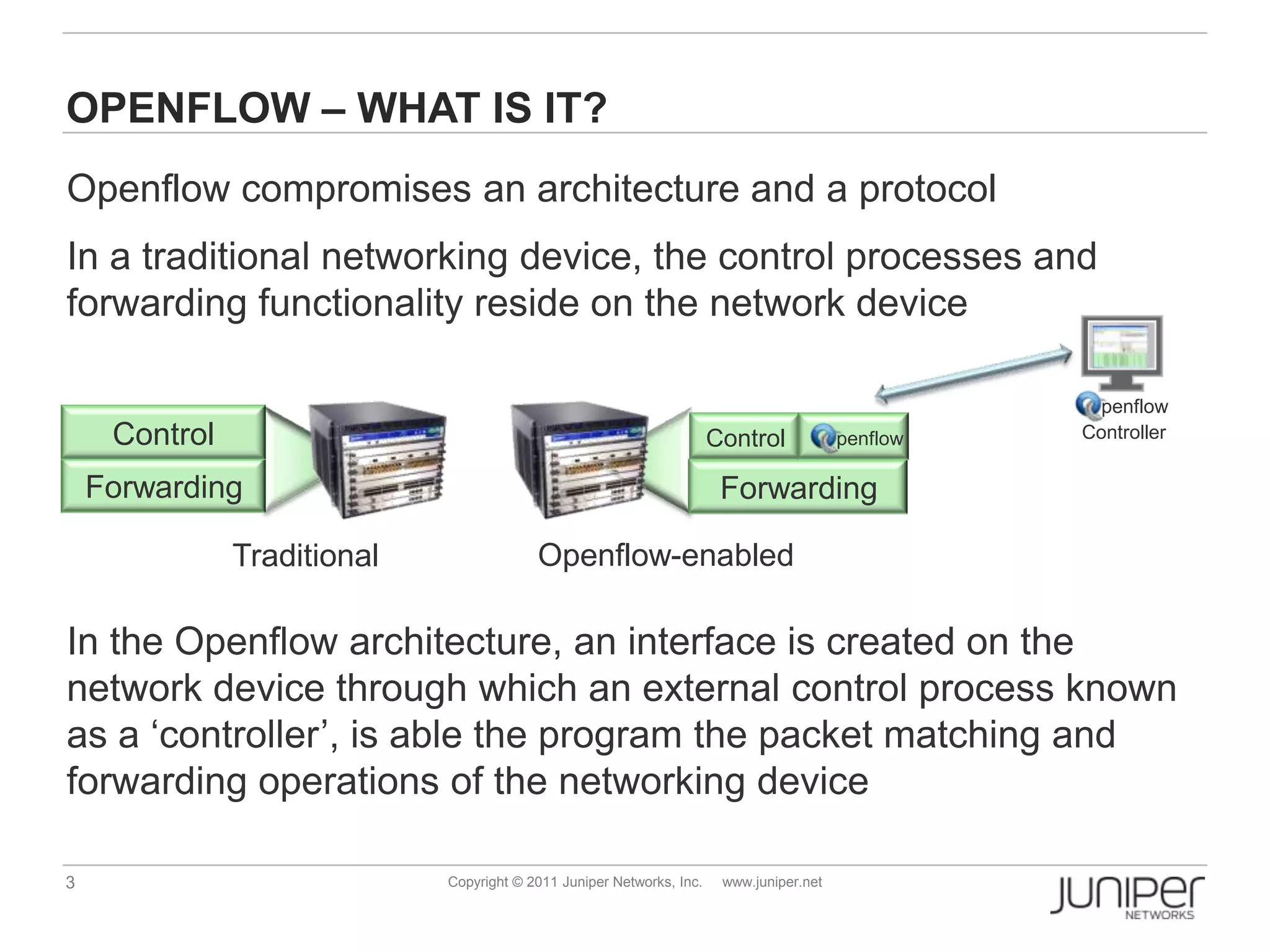
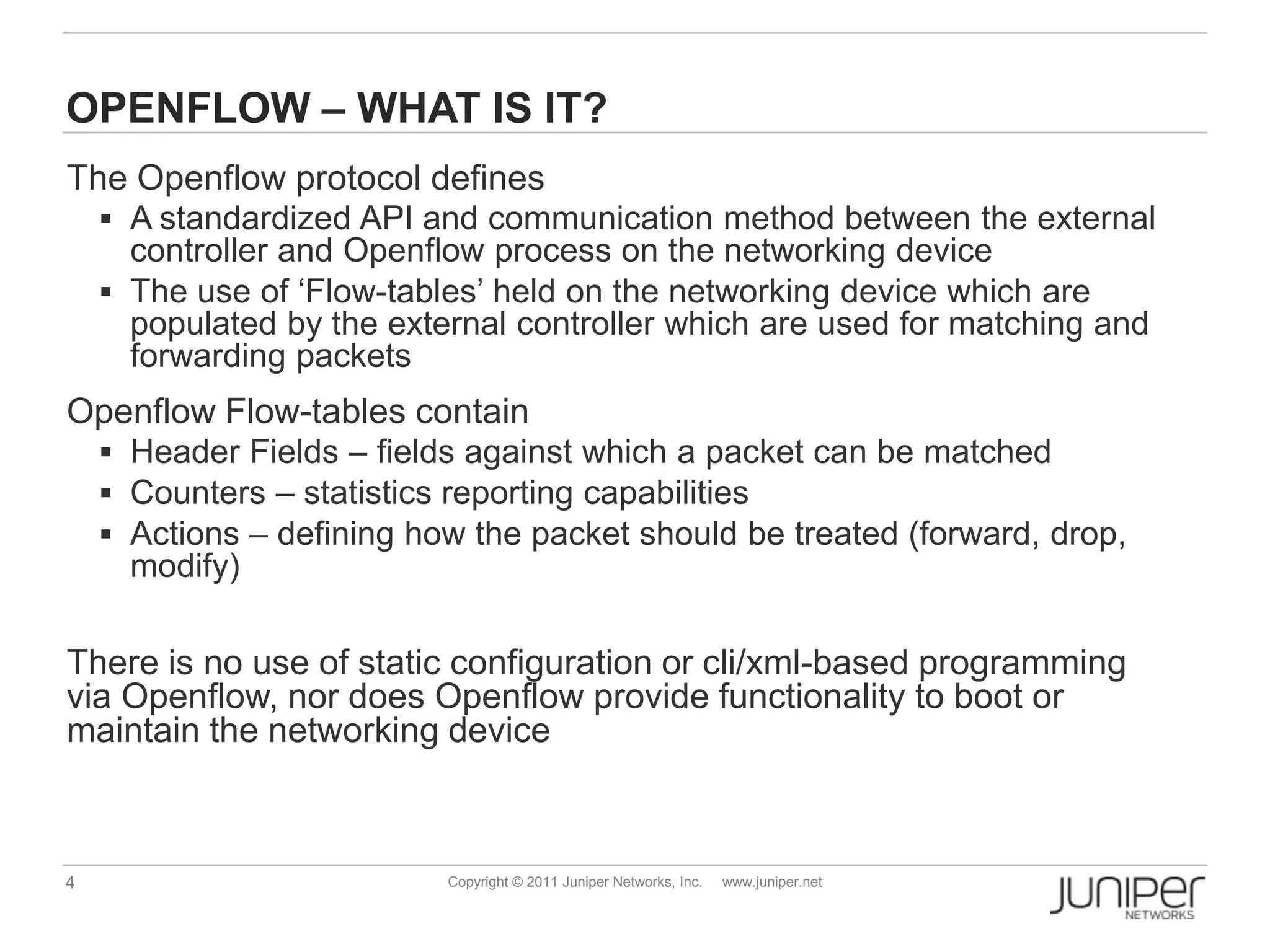
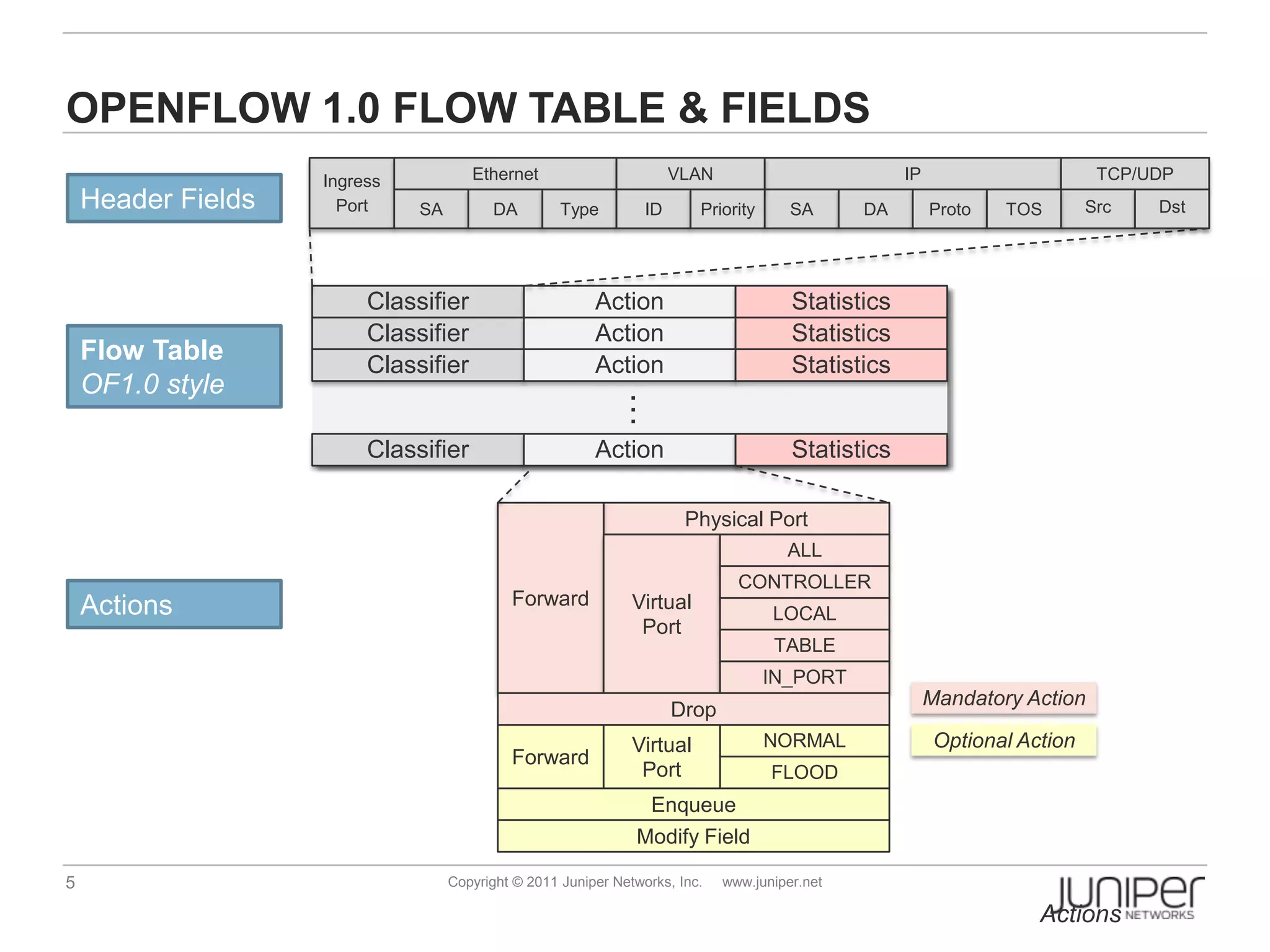
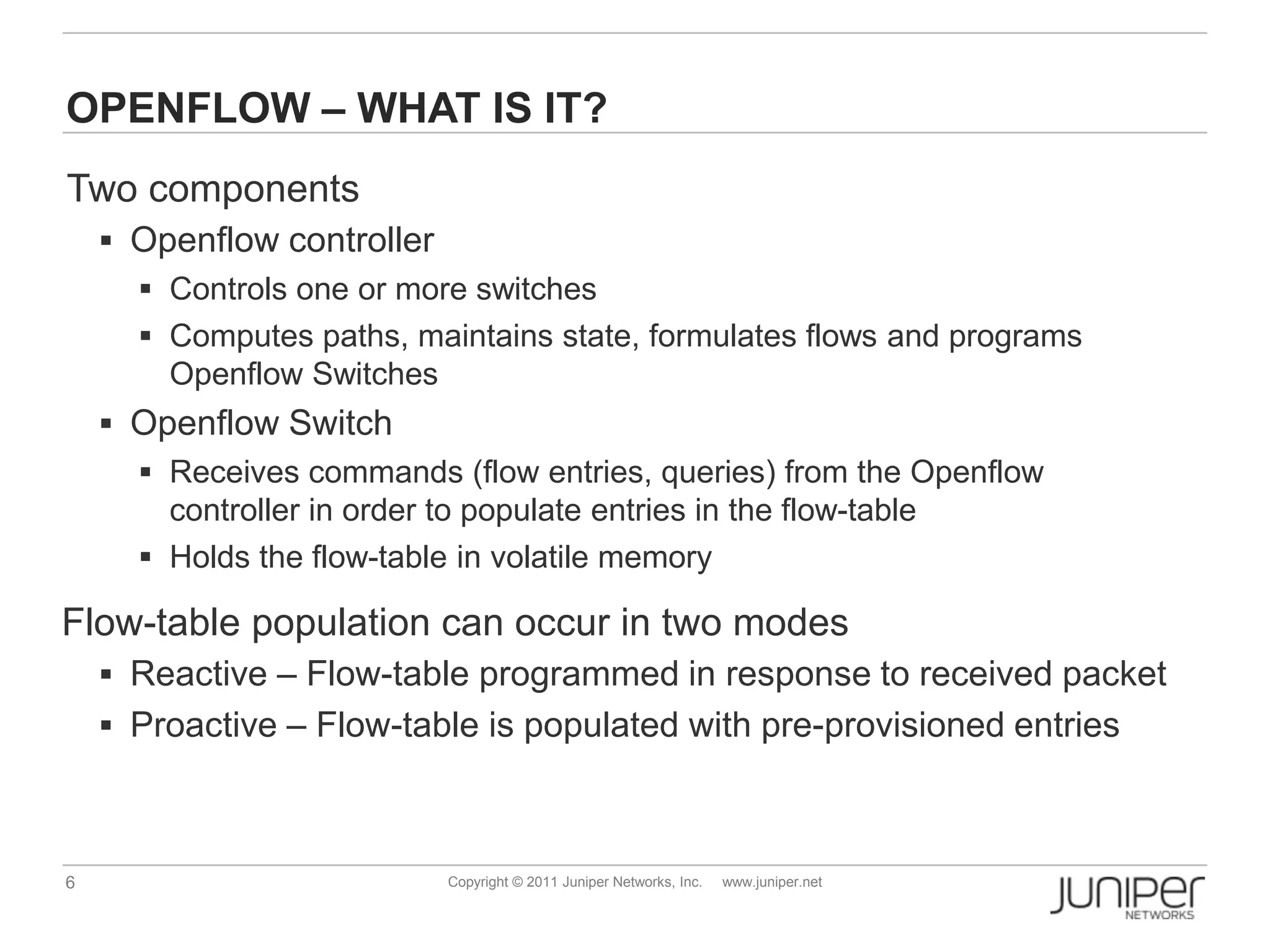
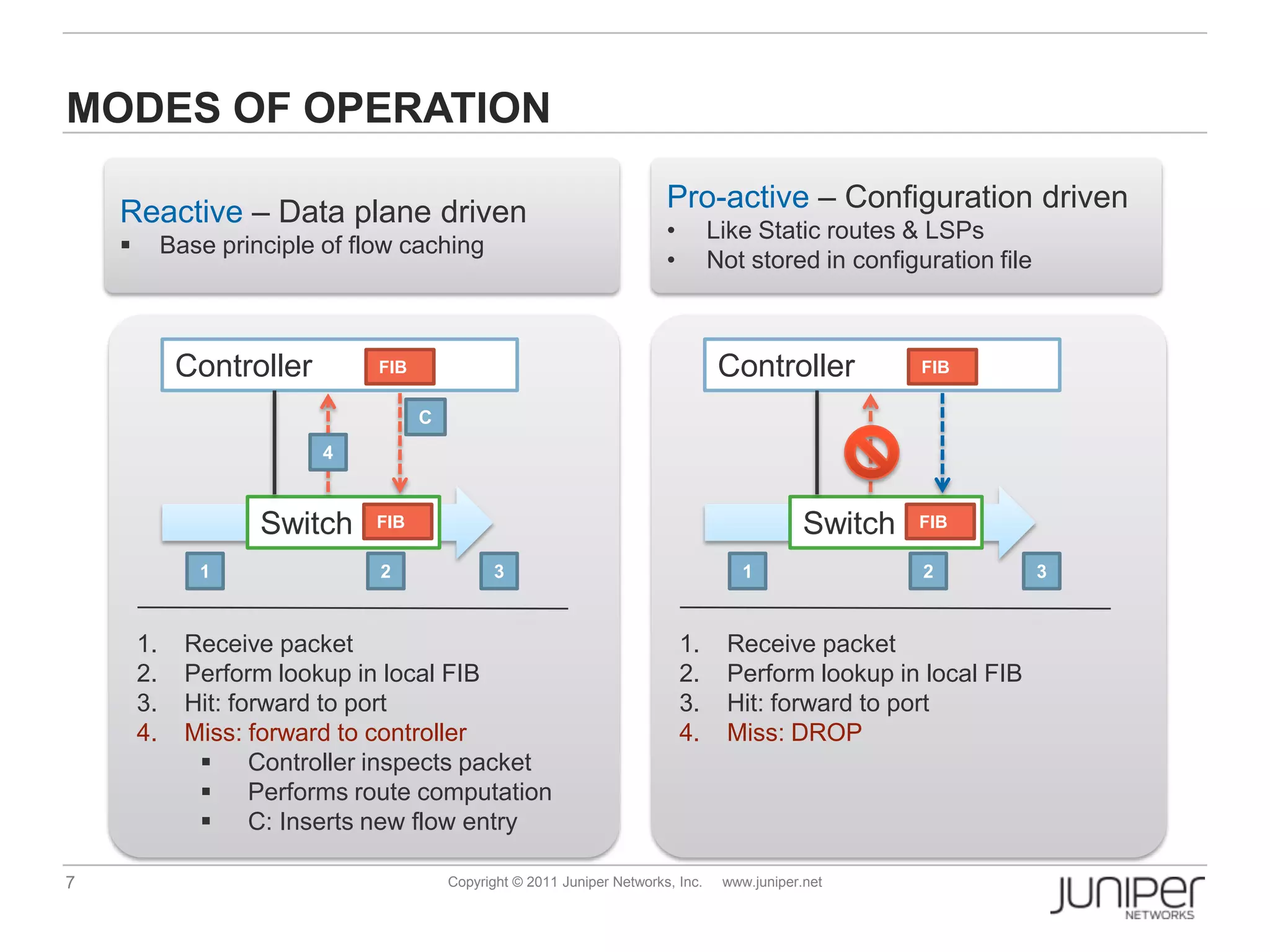
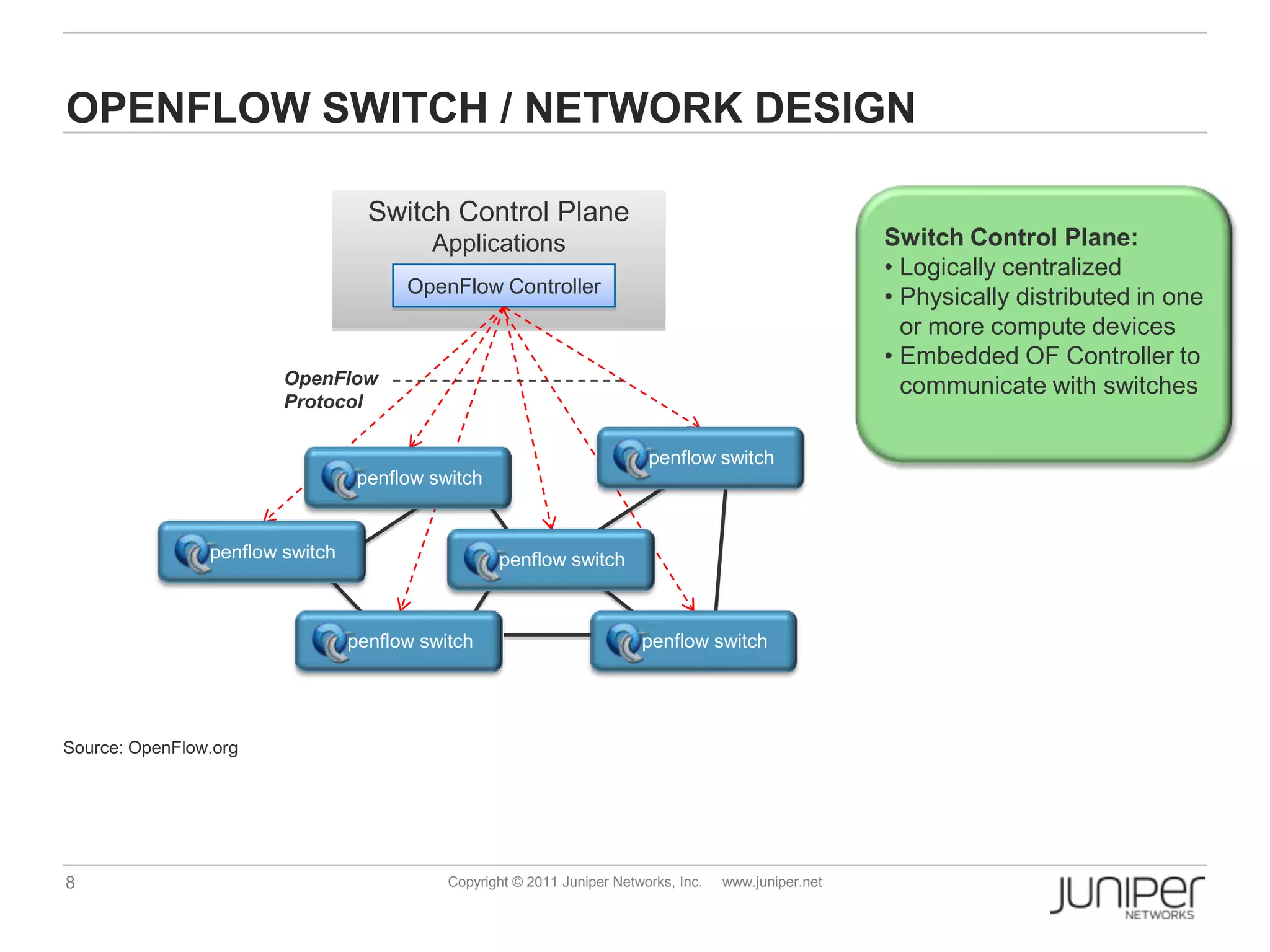
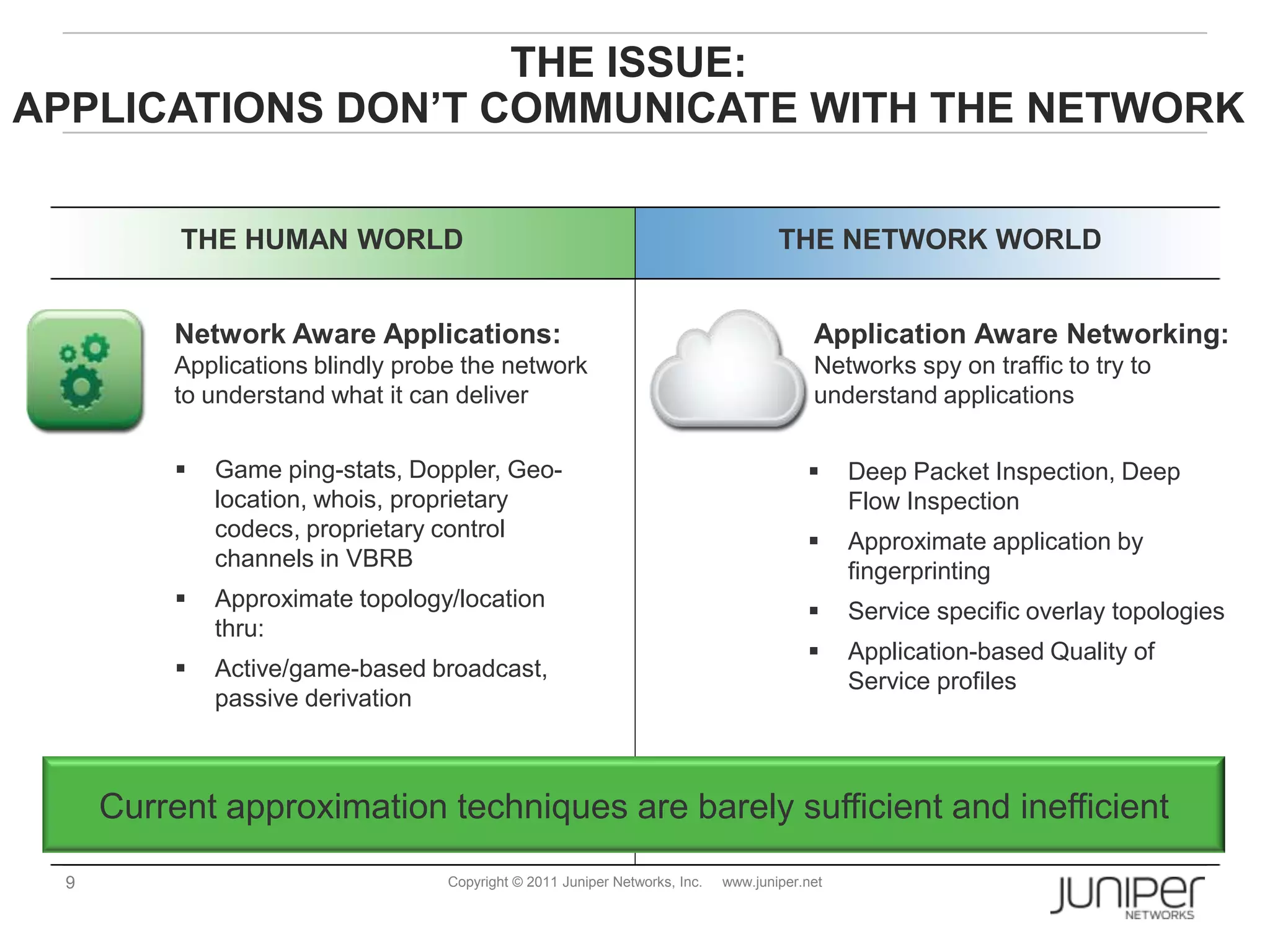
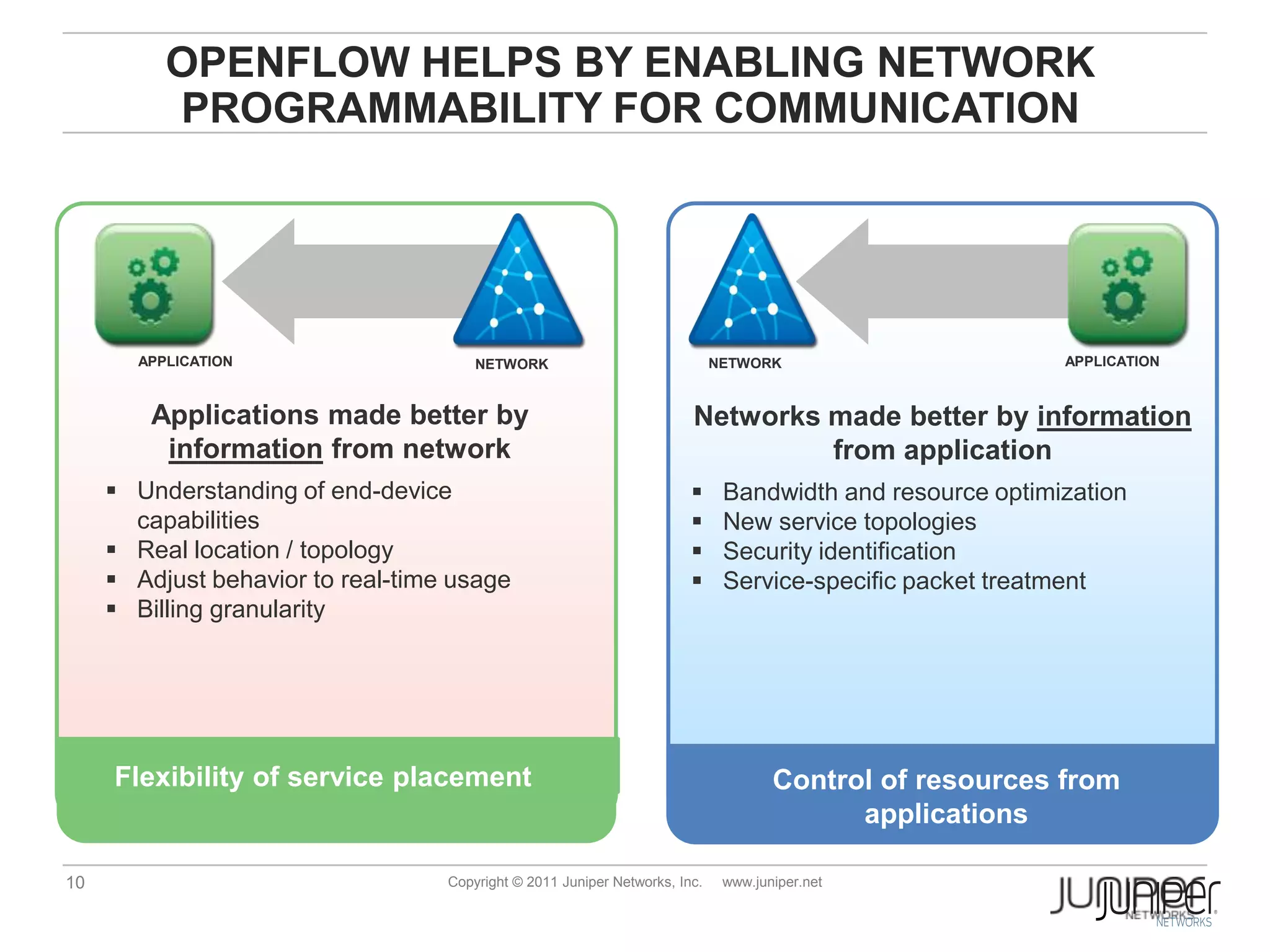
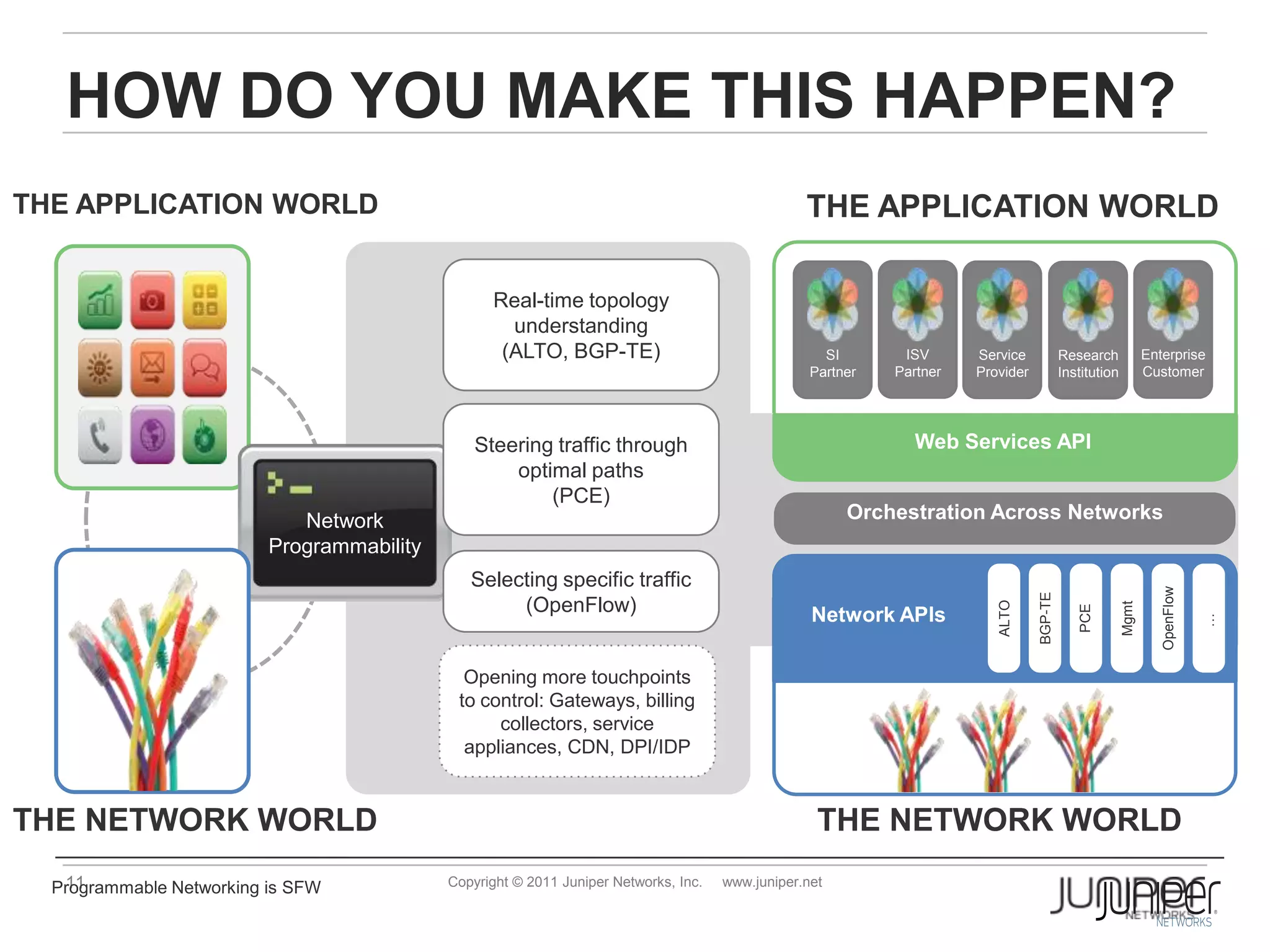
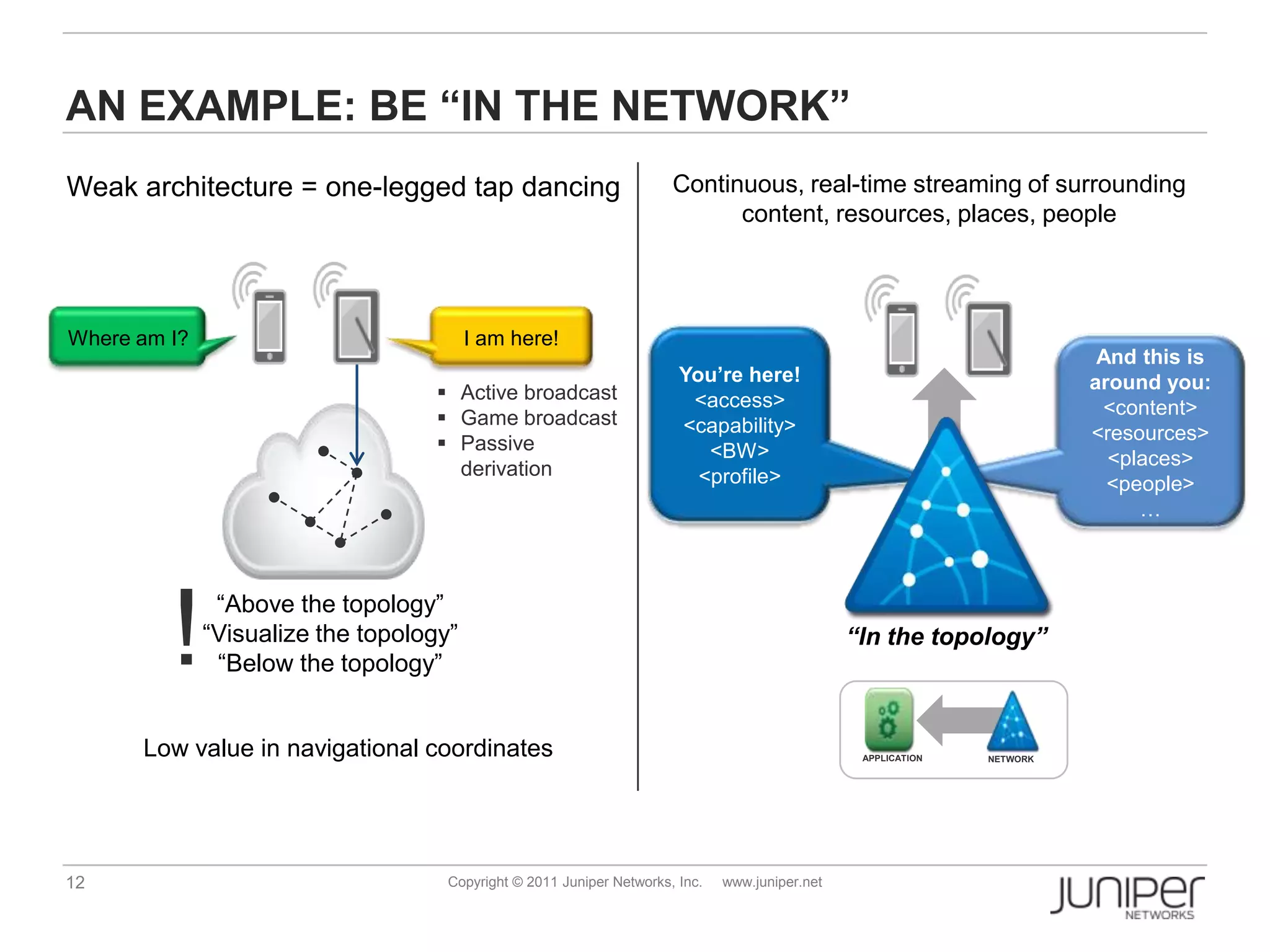
Openflow allows for external control of networking devices through the separation of the control plane and forwarding plane. It defines a standardized protocol and API for an external controller to program the forwarding tables of Openflow-enabled switches. The controller installs flow entries into flow tables on switches to determine how packets should be matched and processed. This provides programmability of the network and flexibility in how traffic is routed.