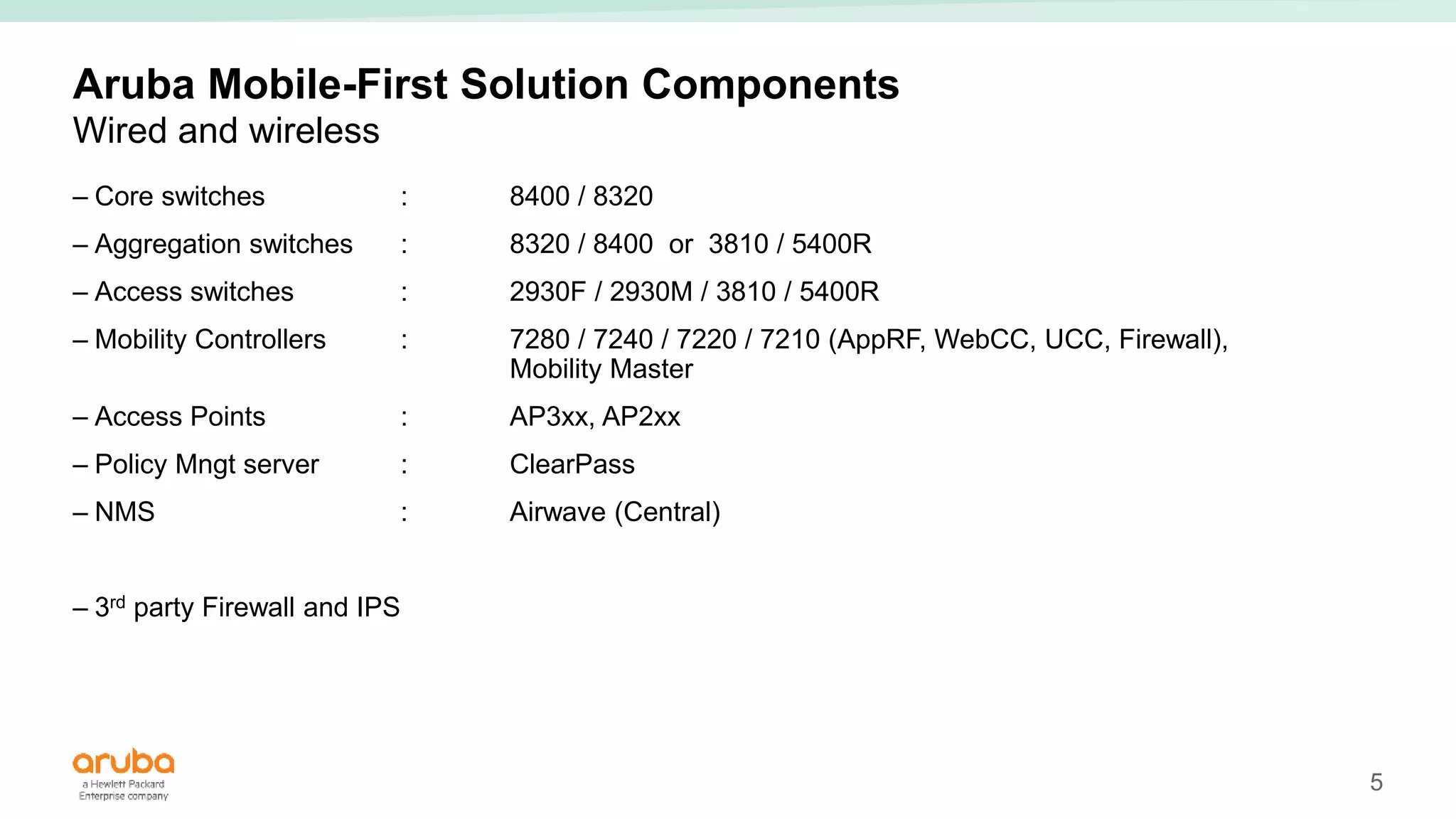
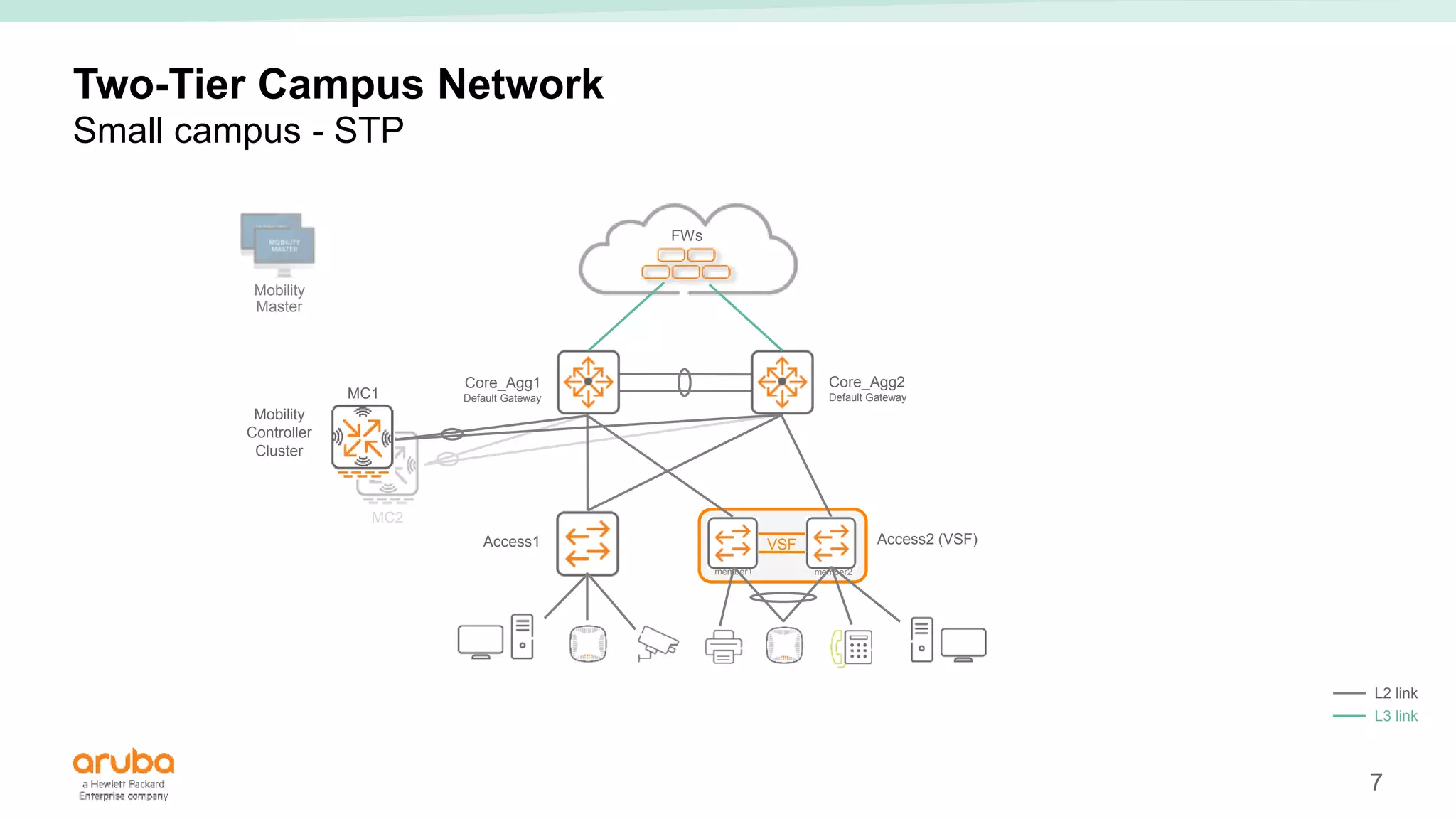
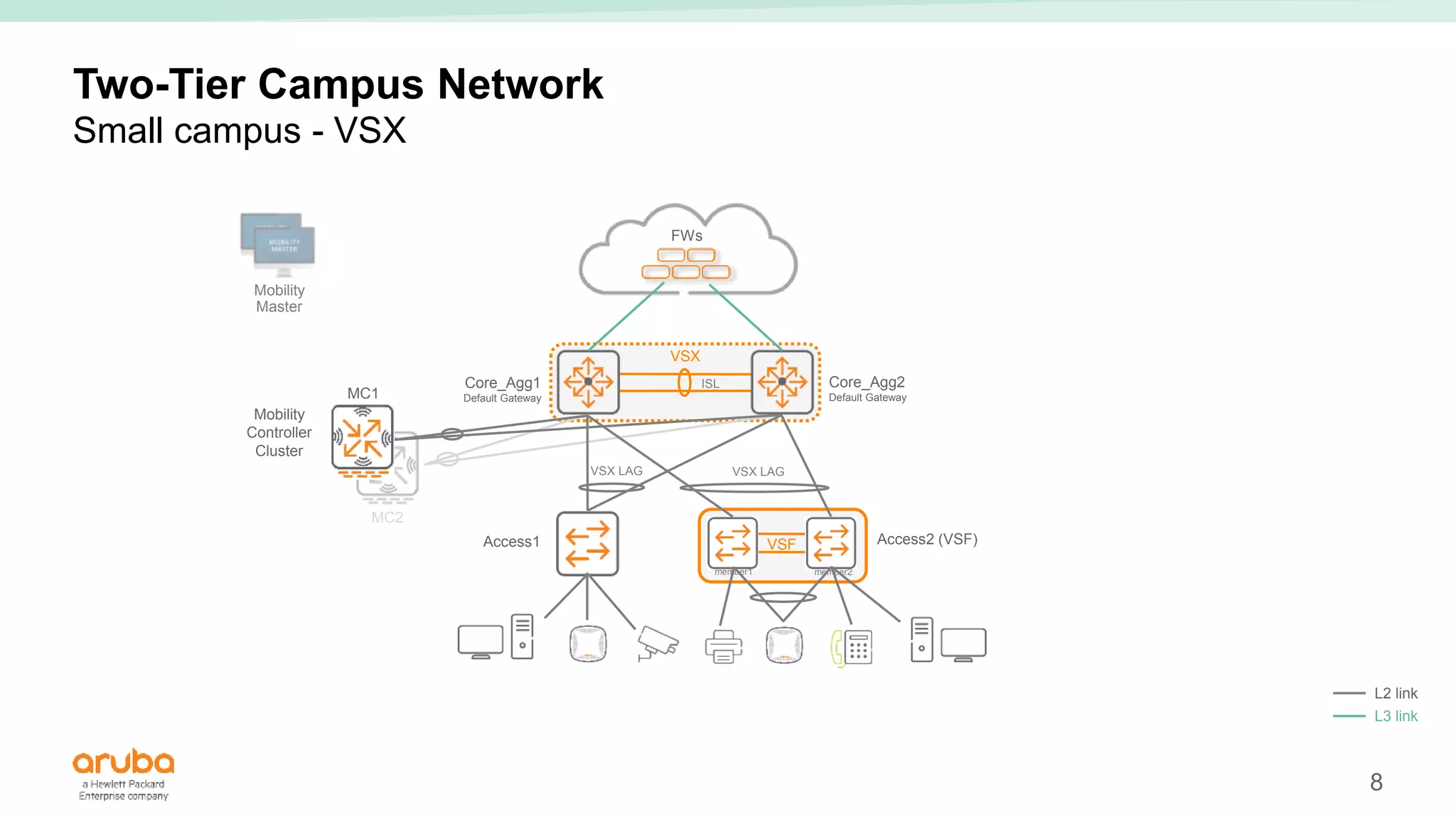
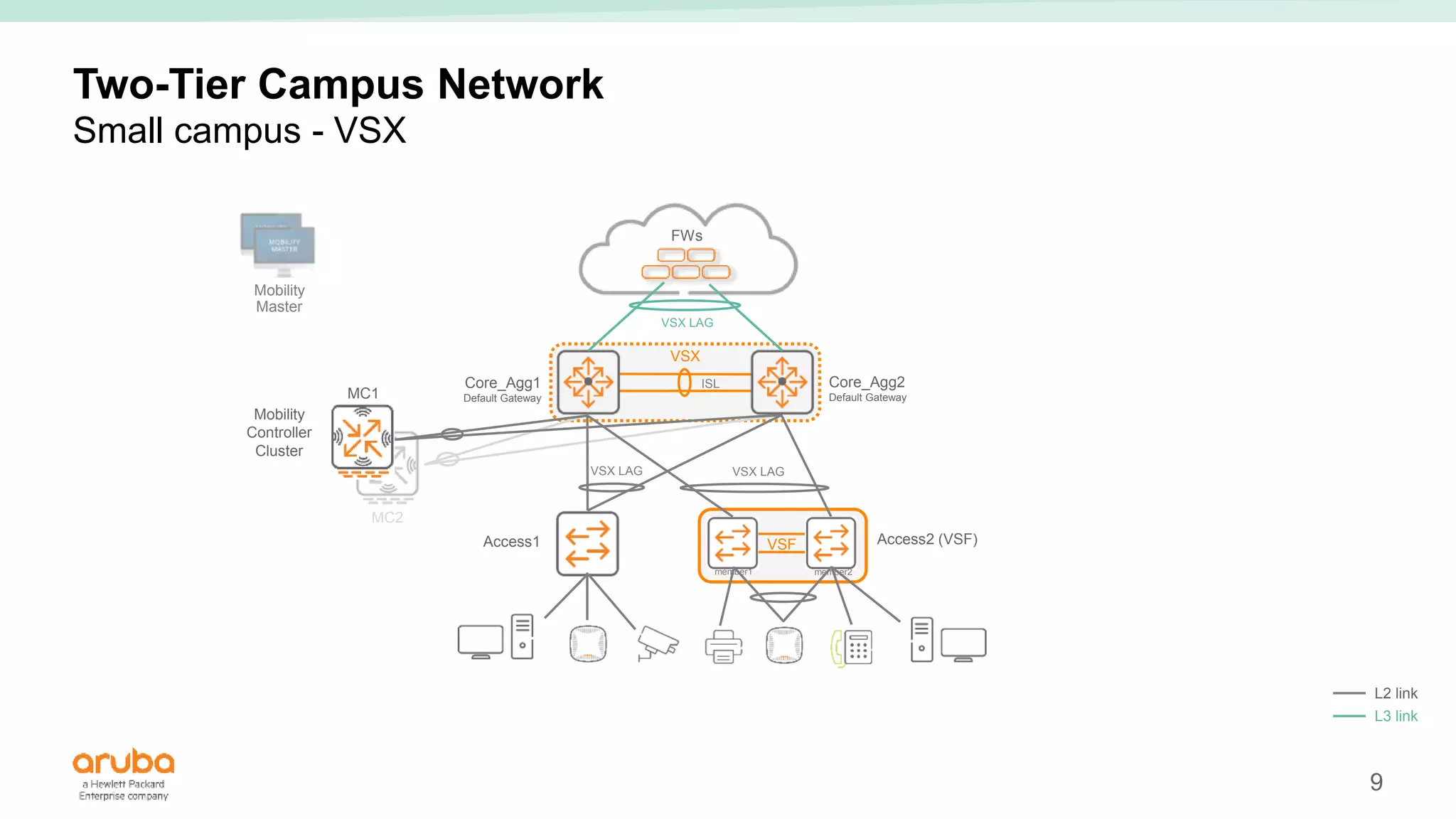
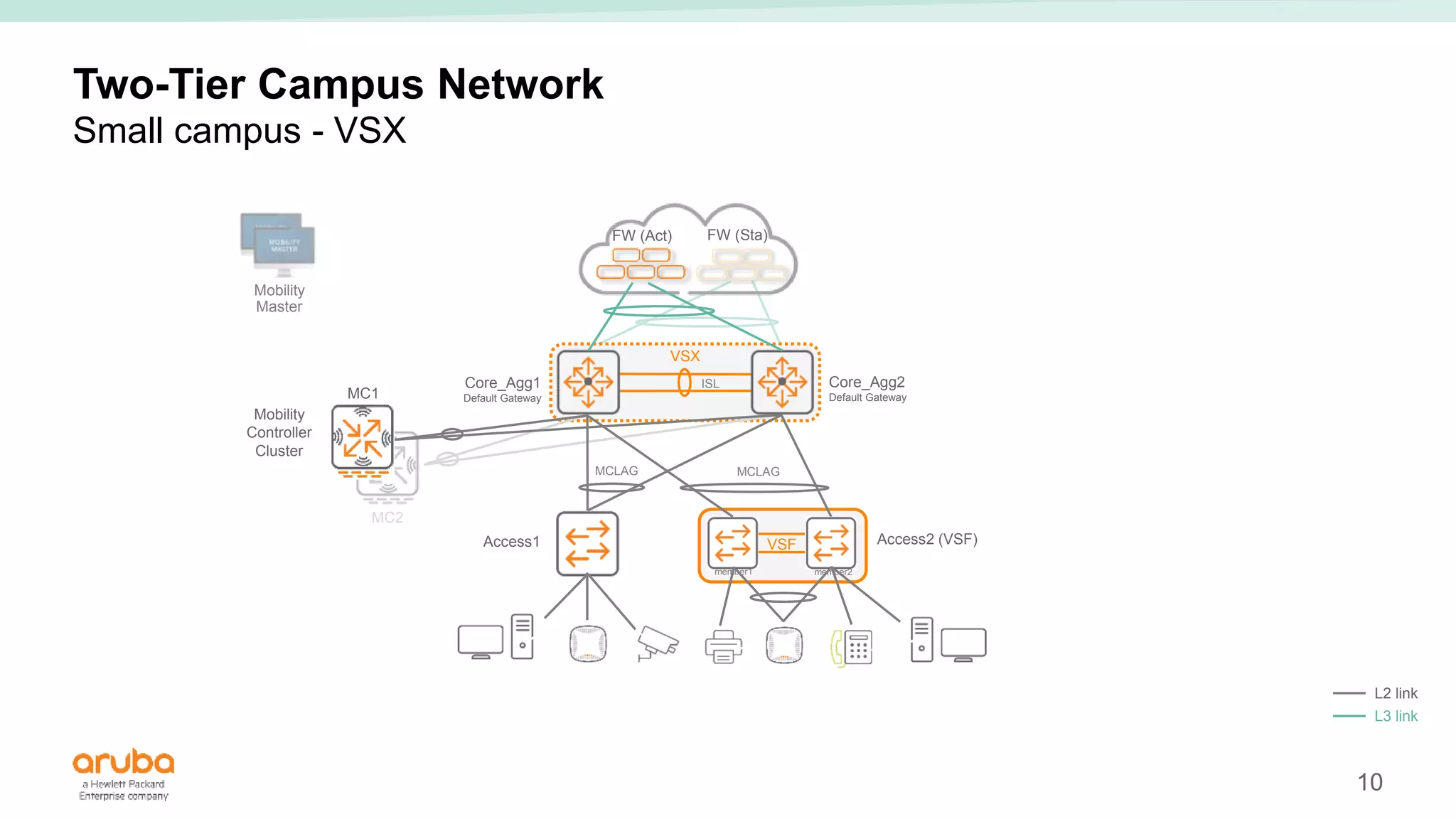
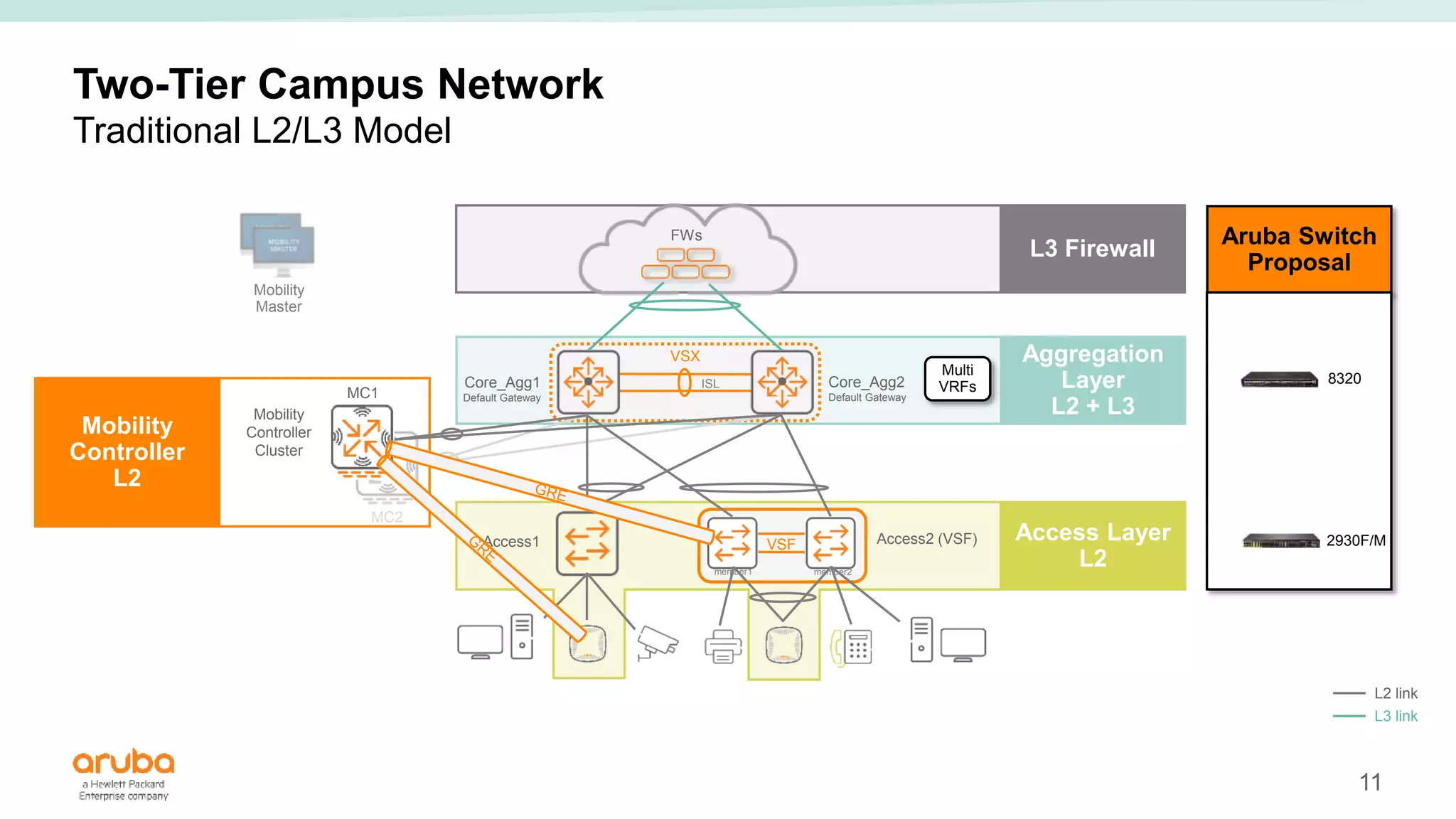
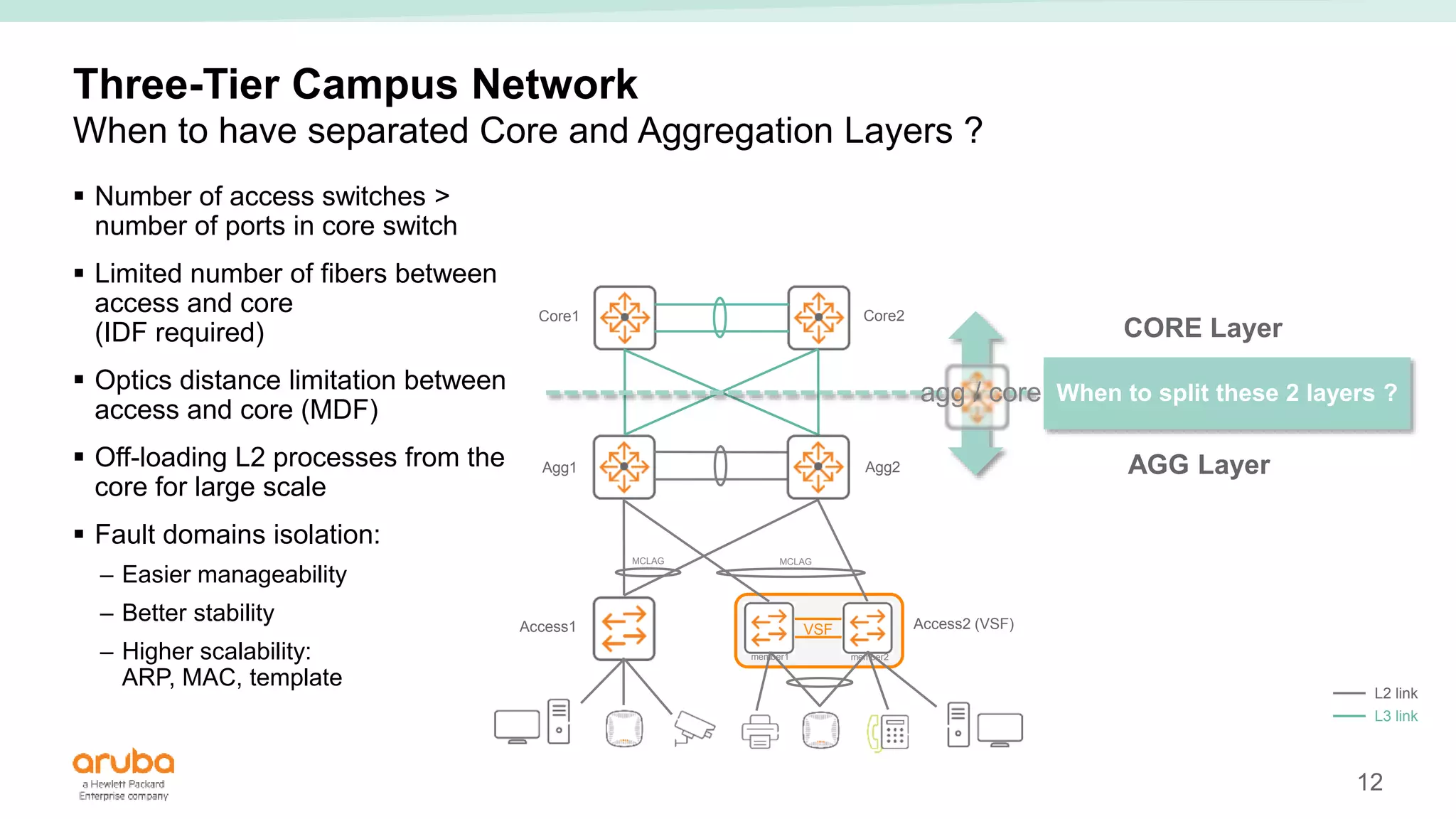
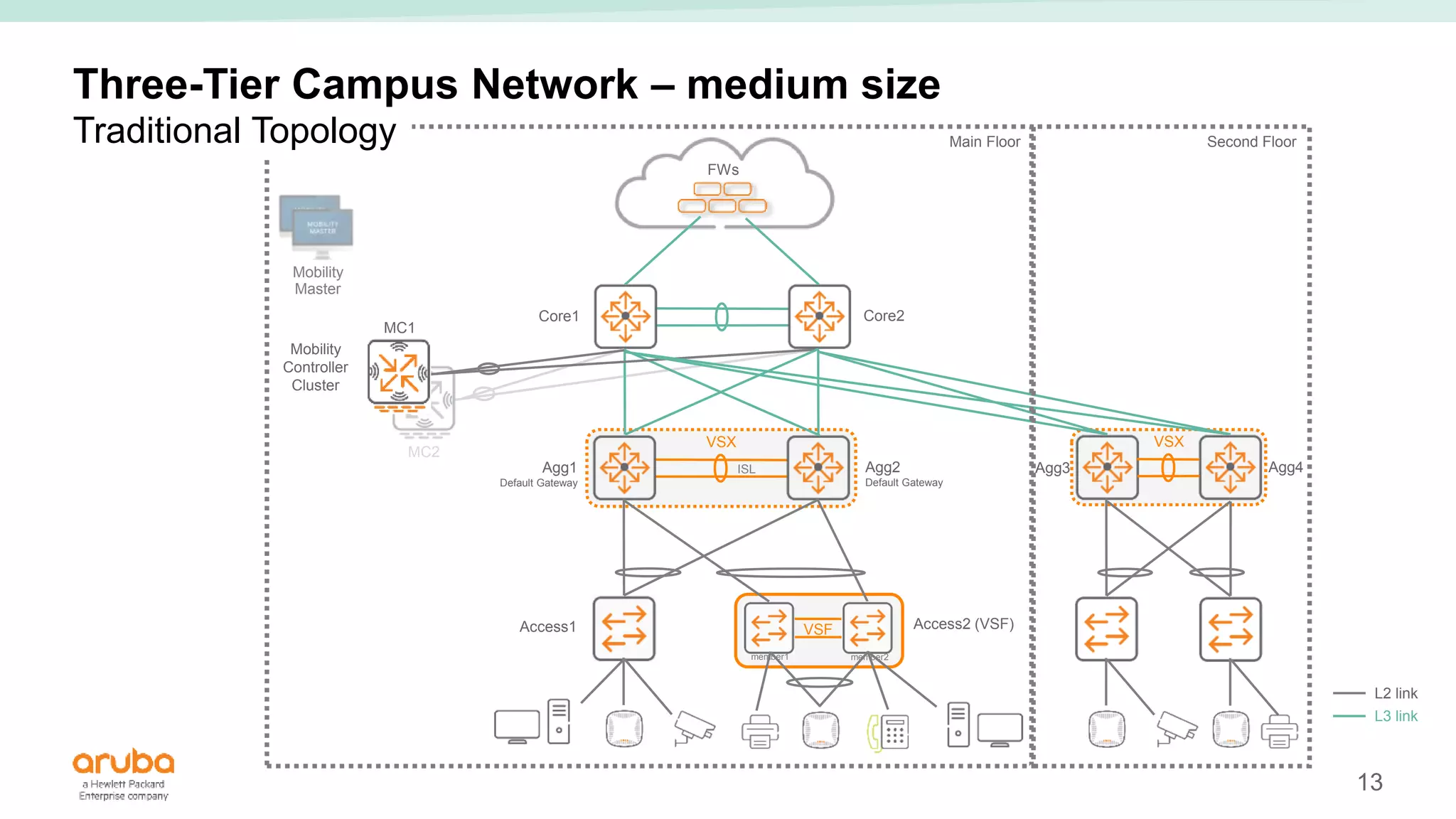
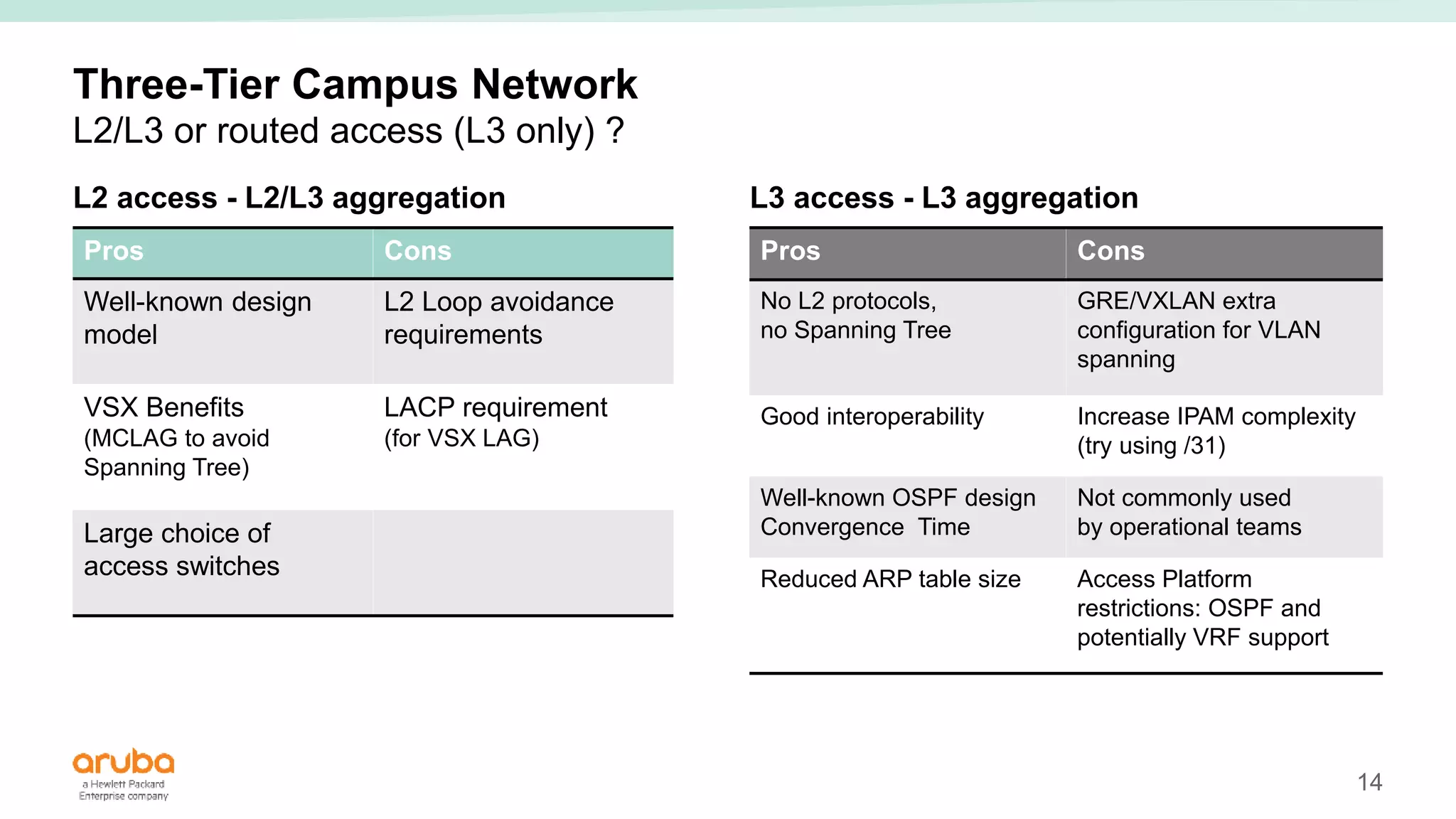
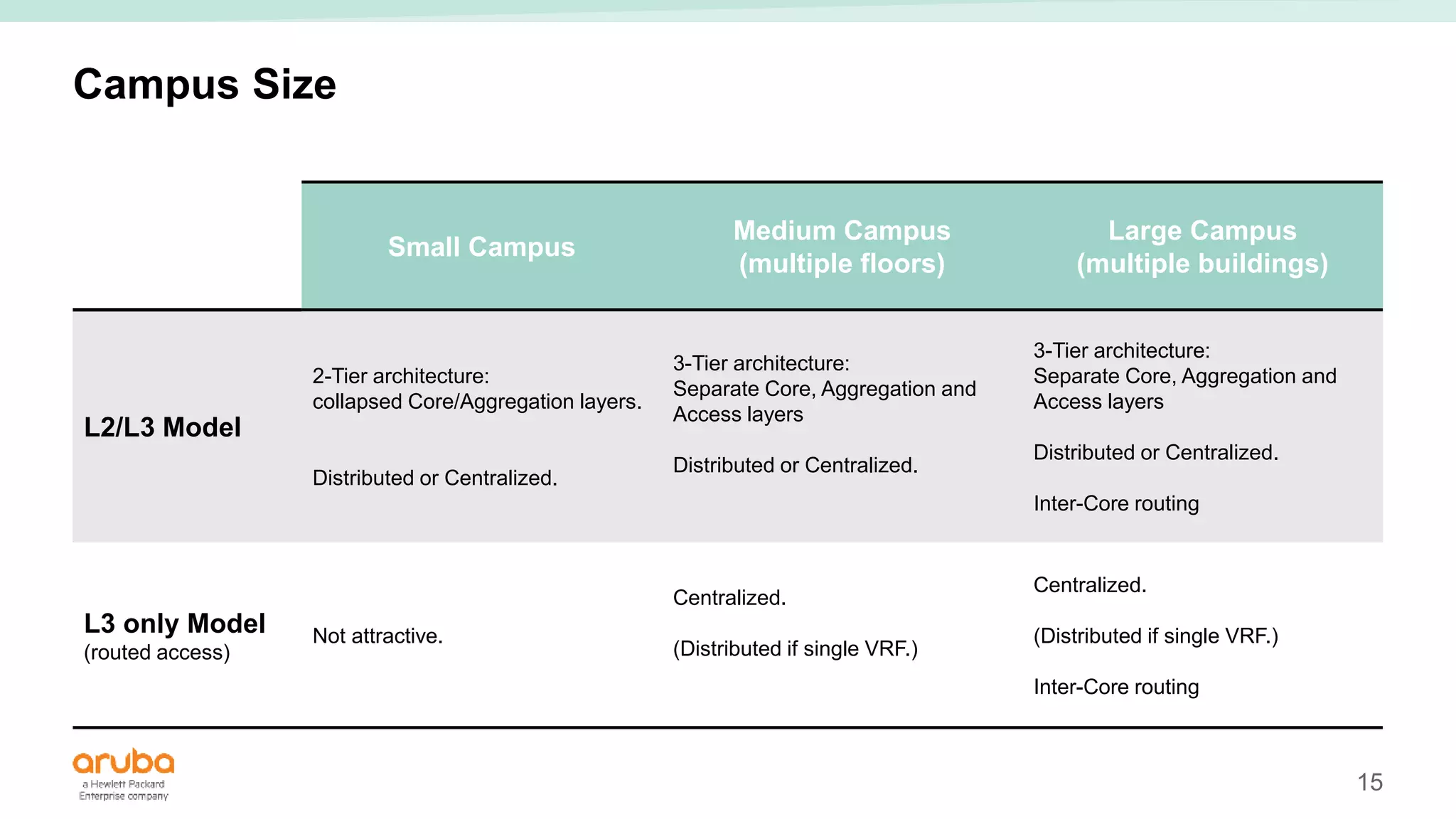
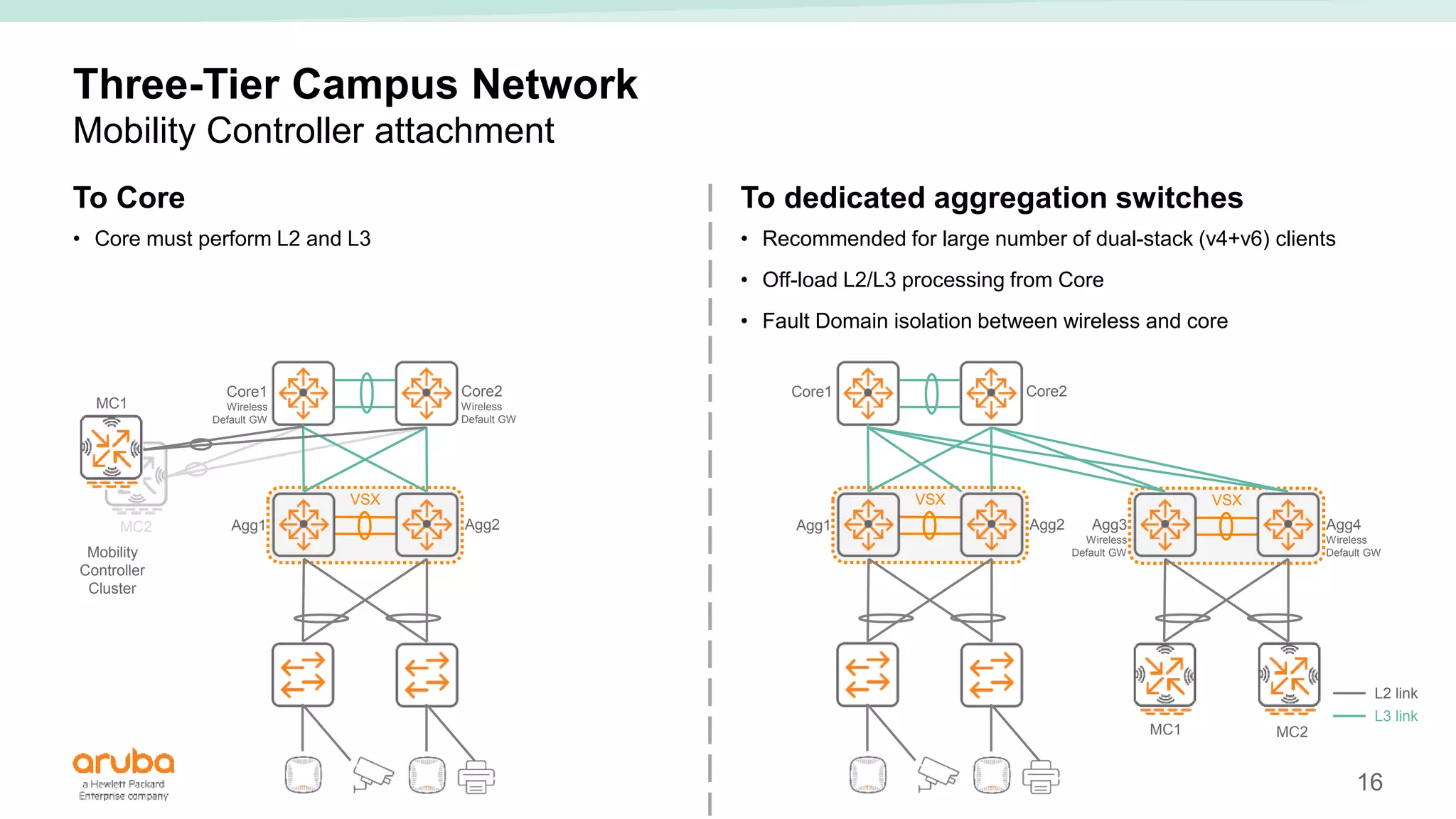
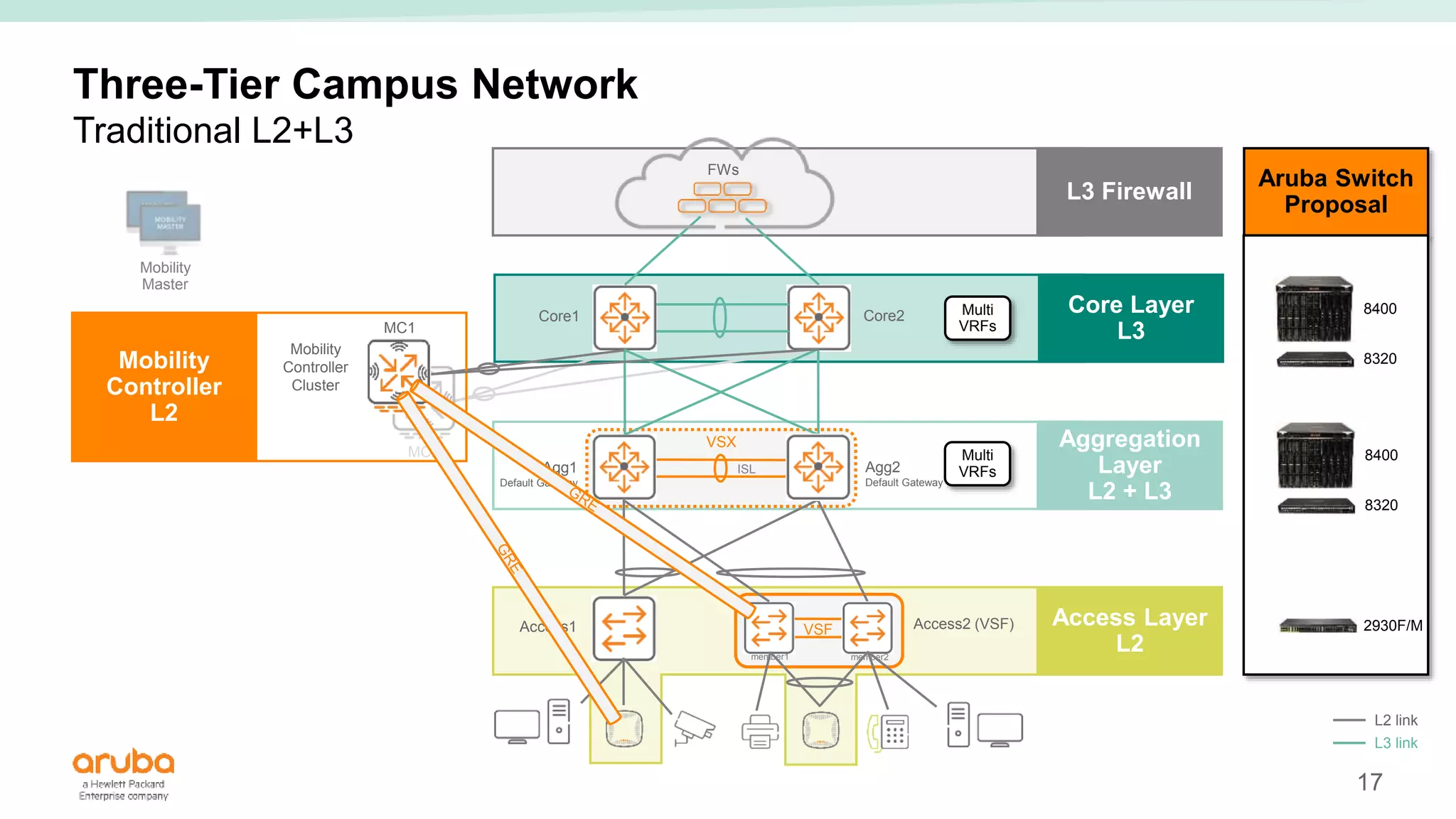
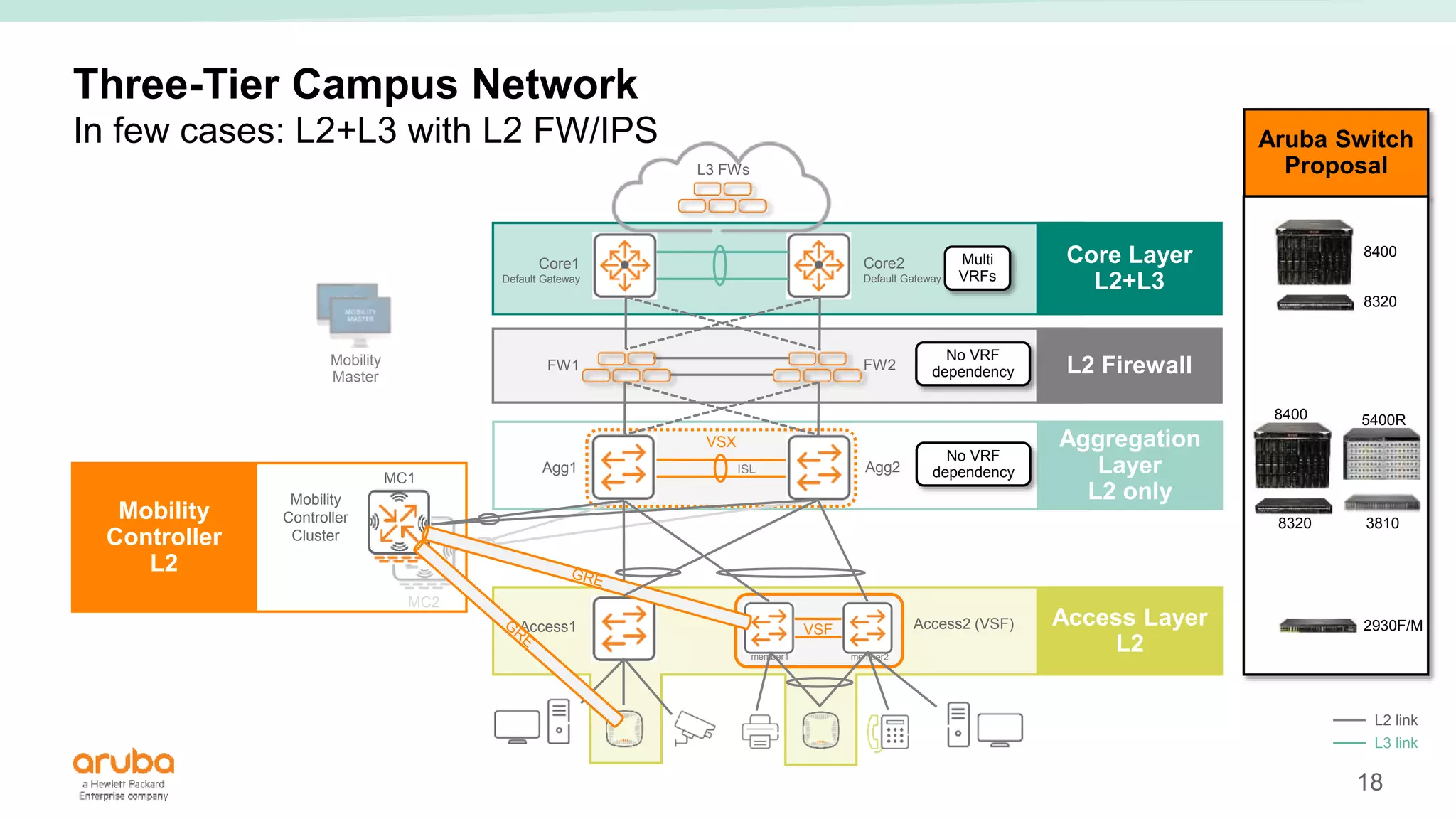
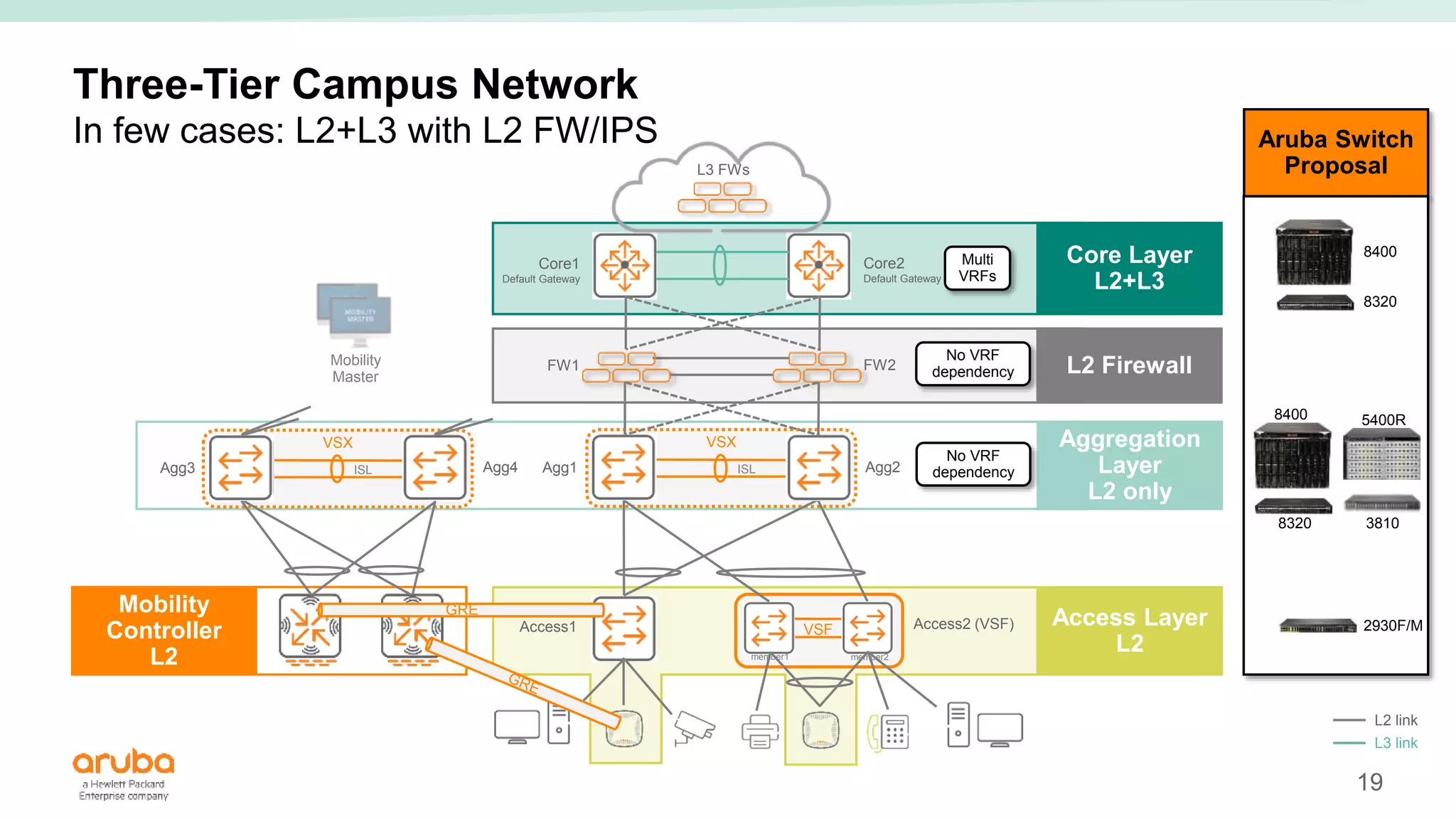
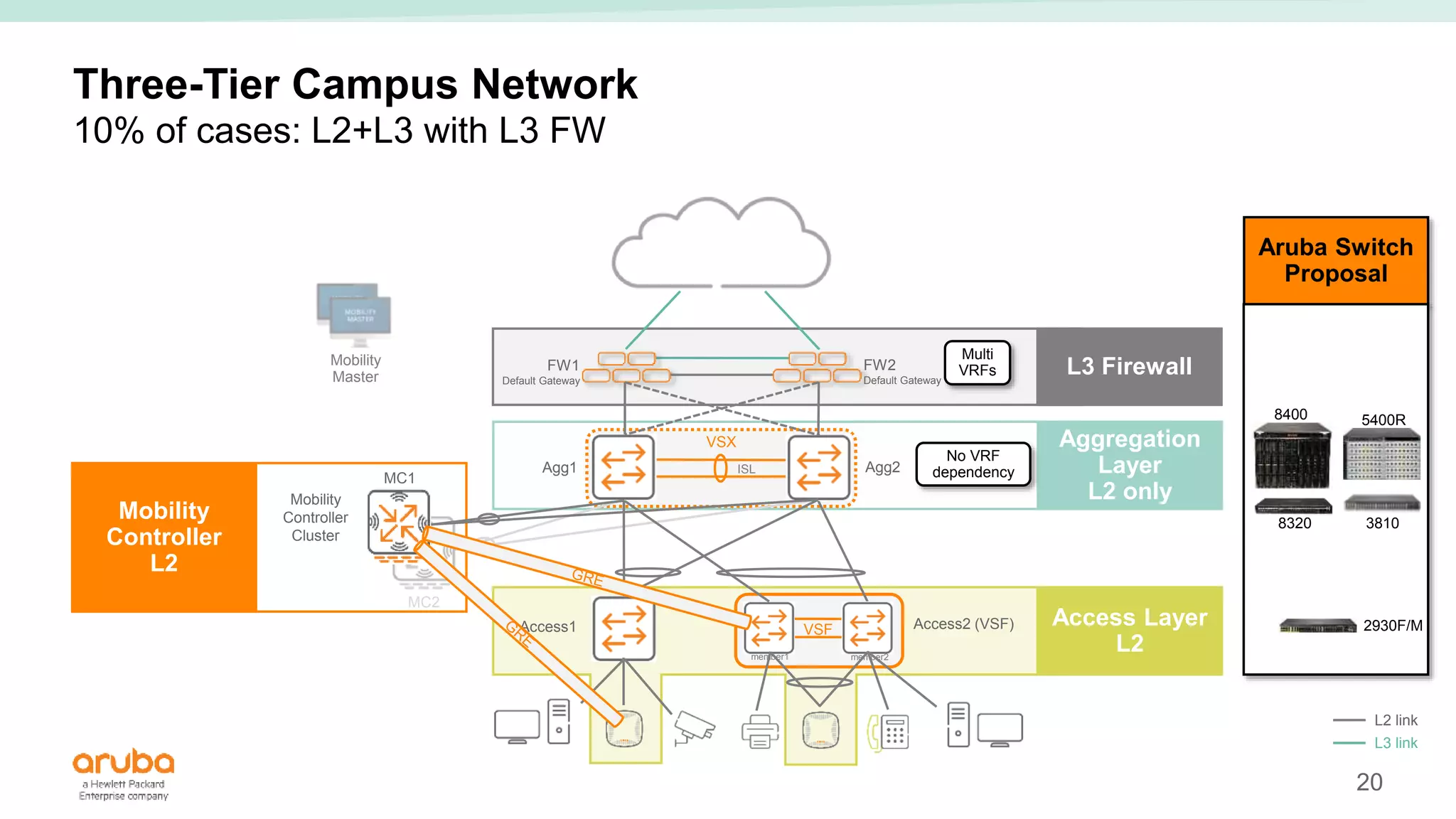
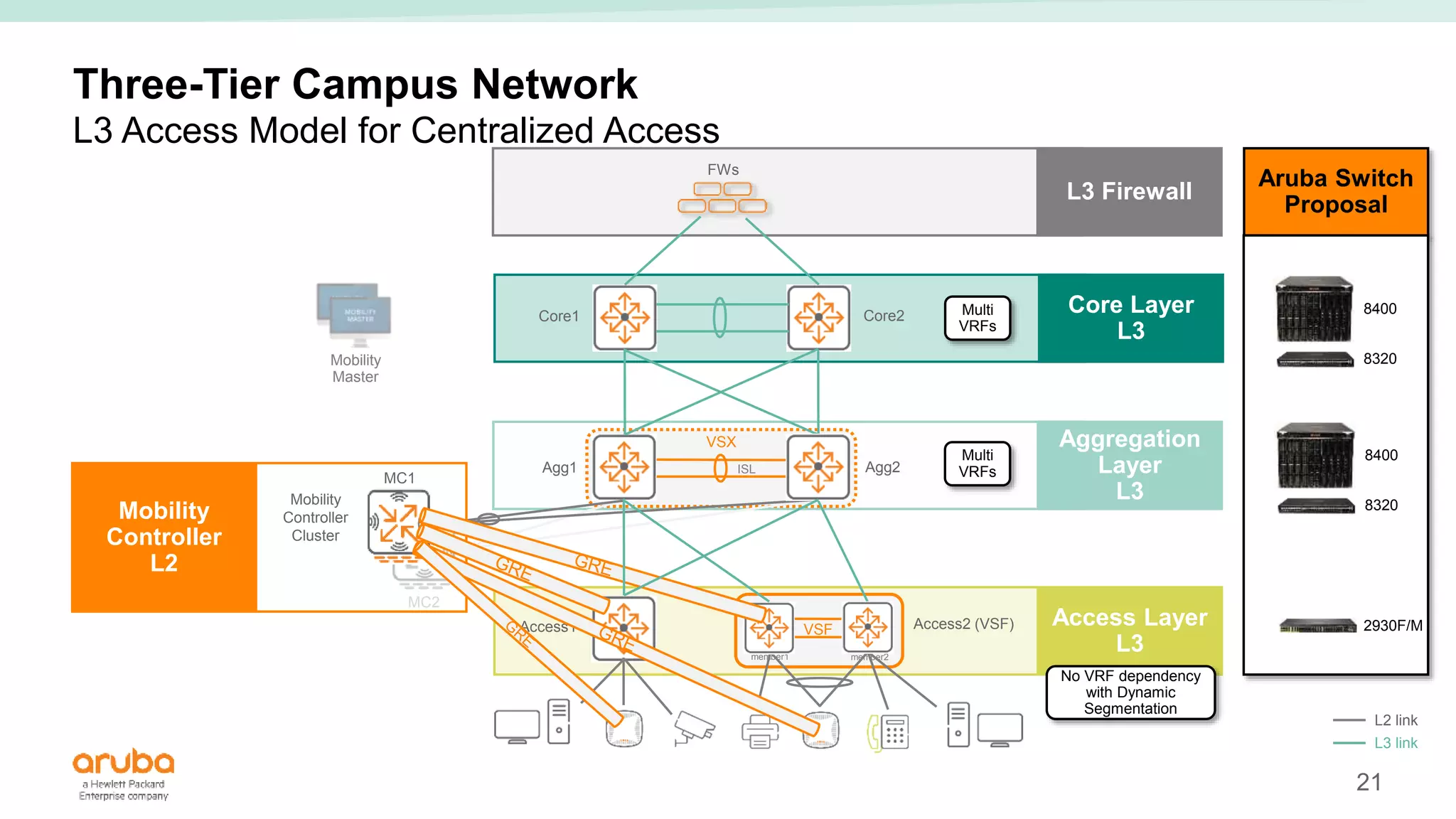
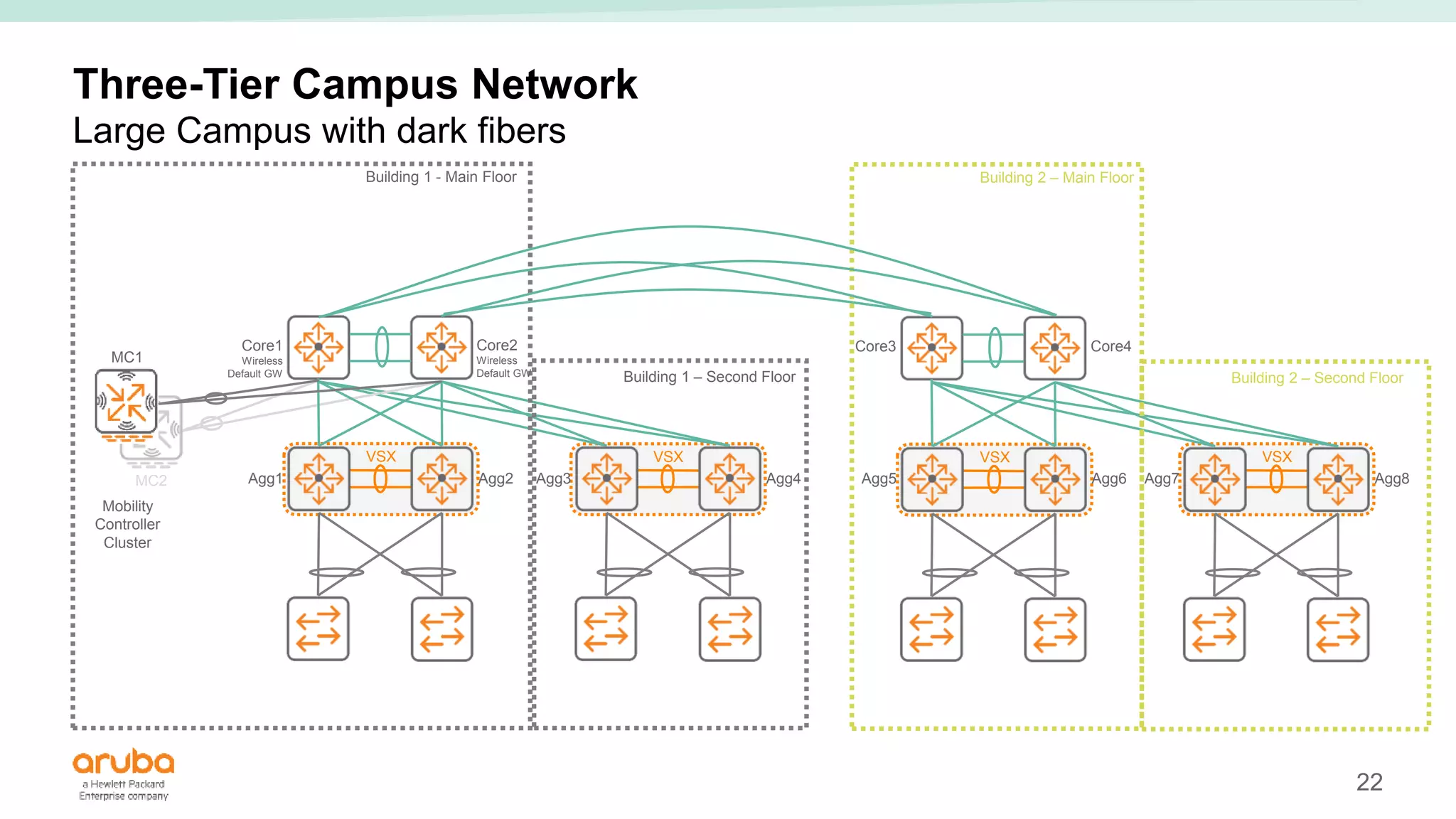
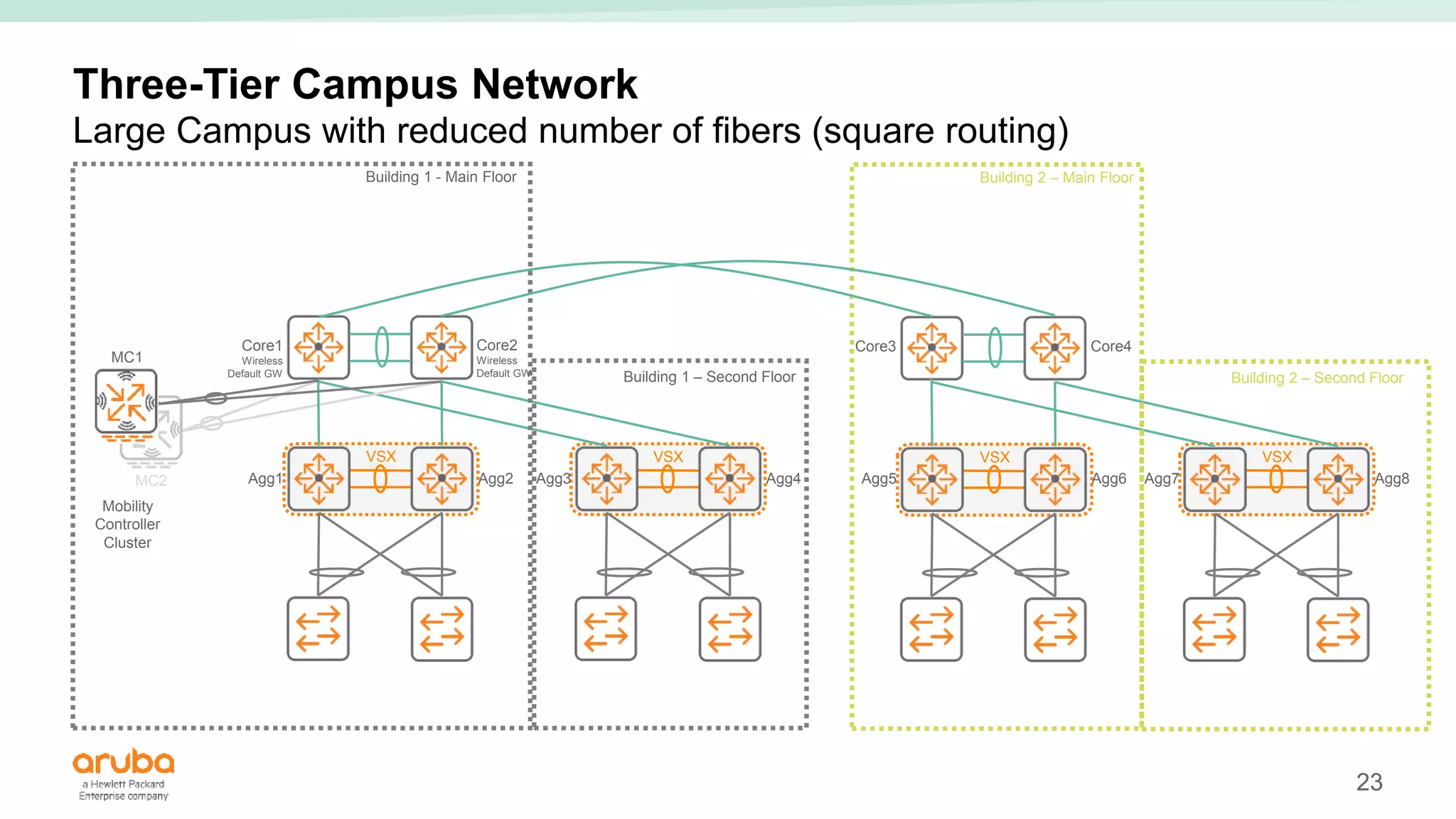
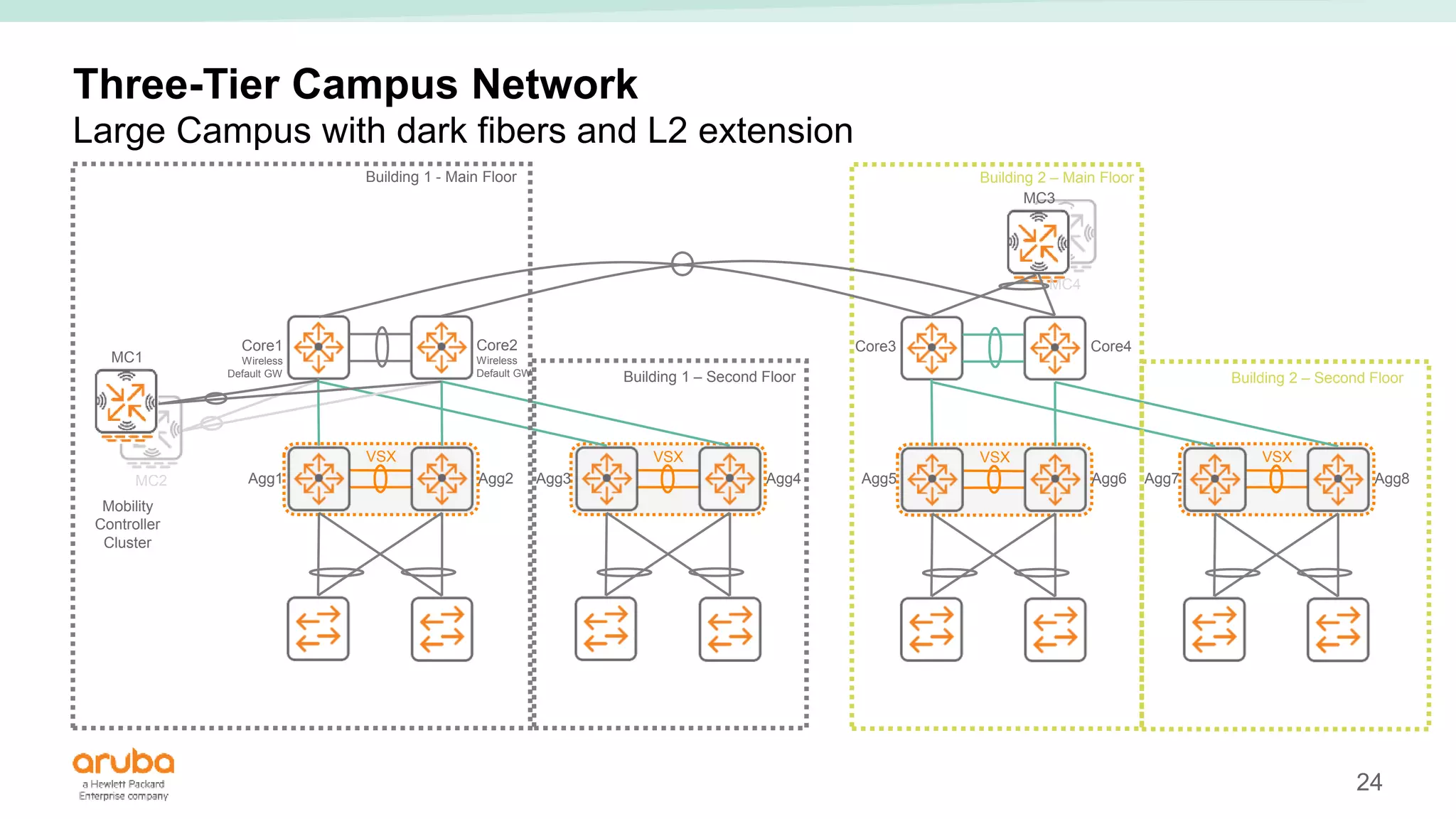
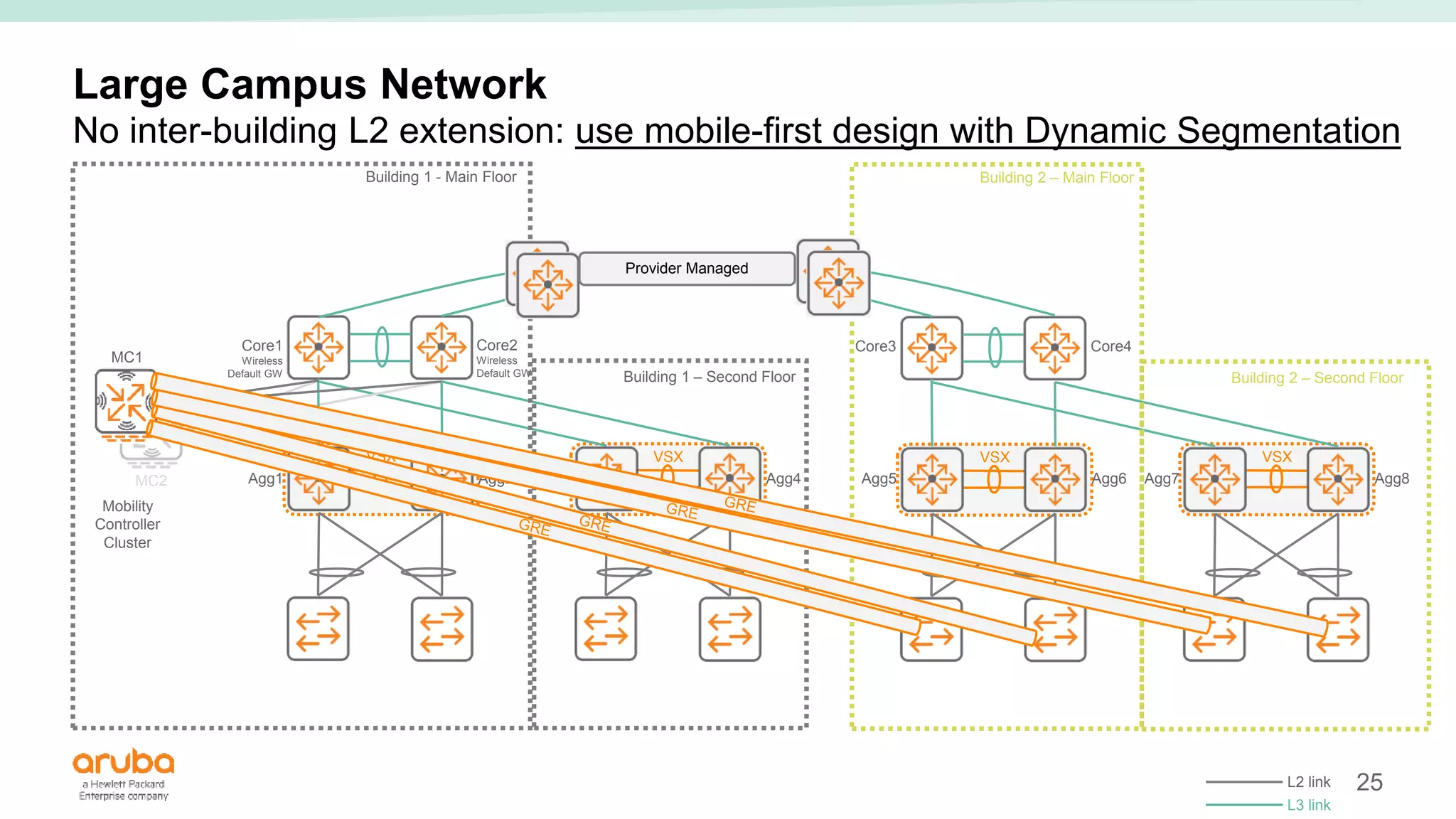
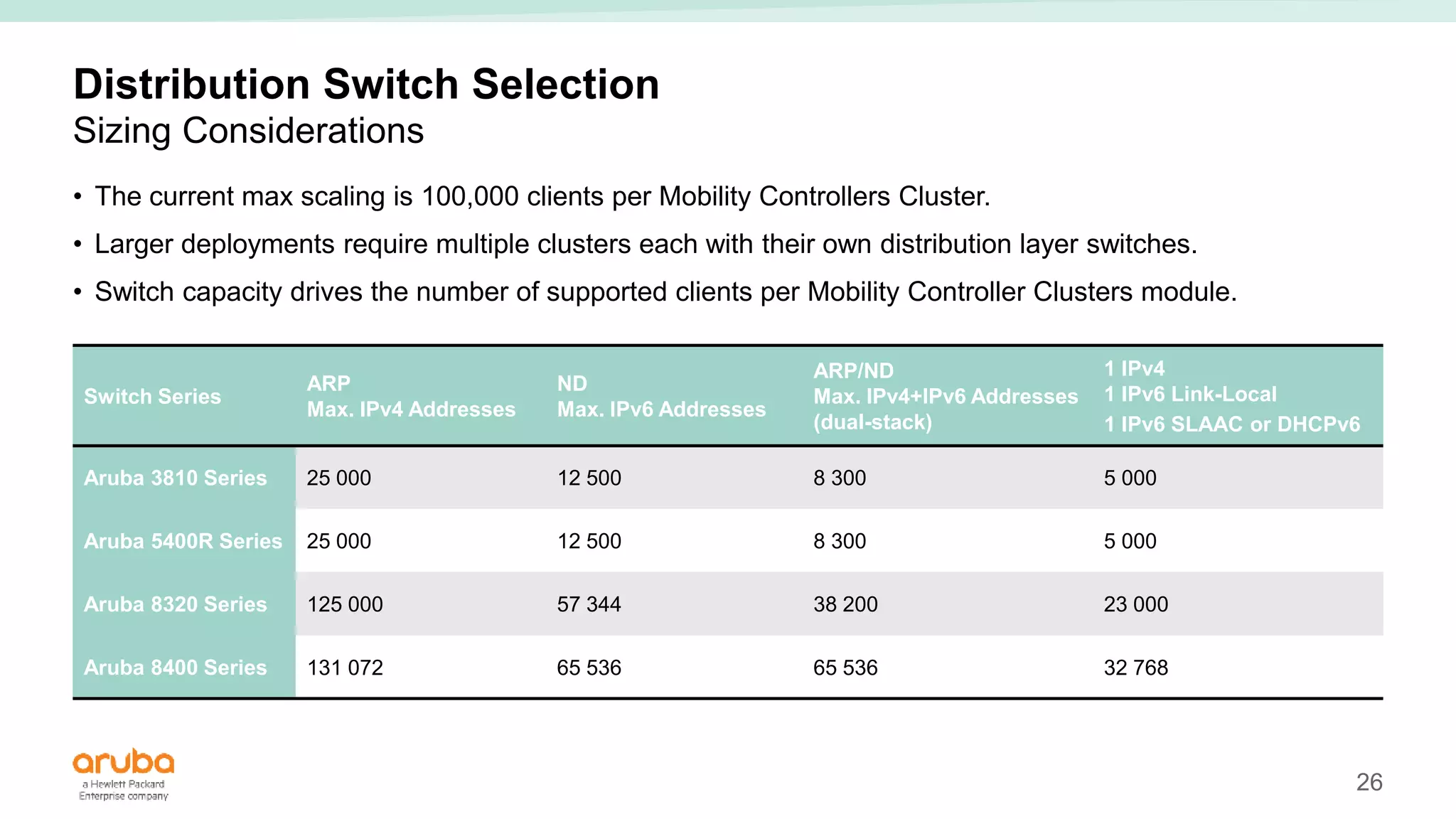
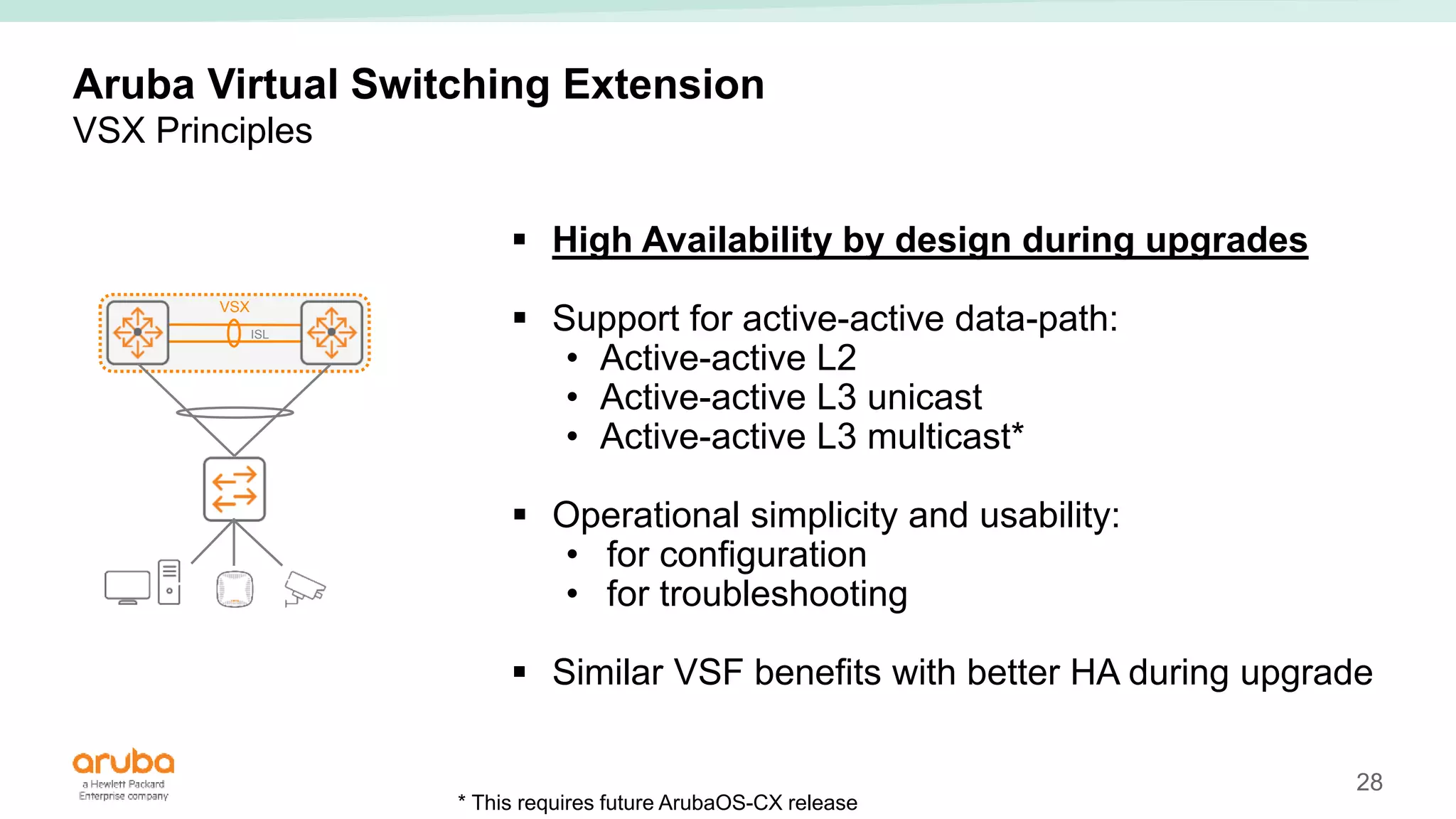
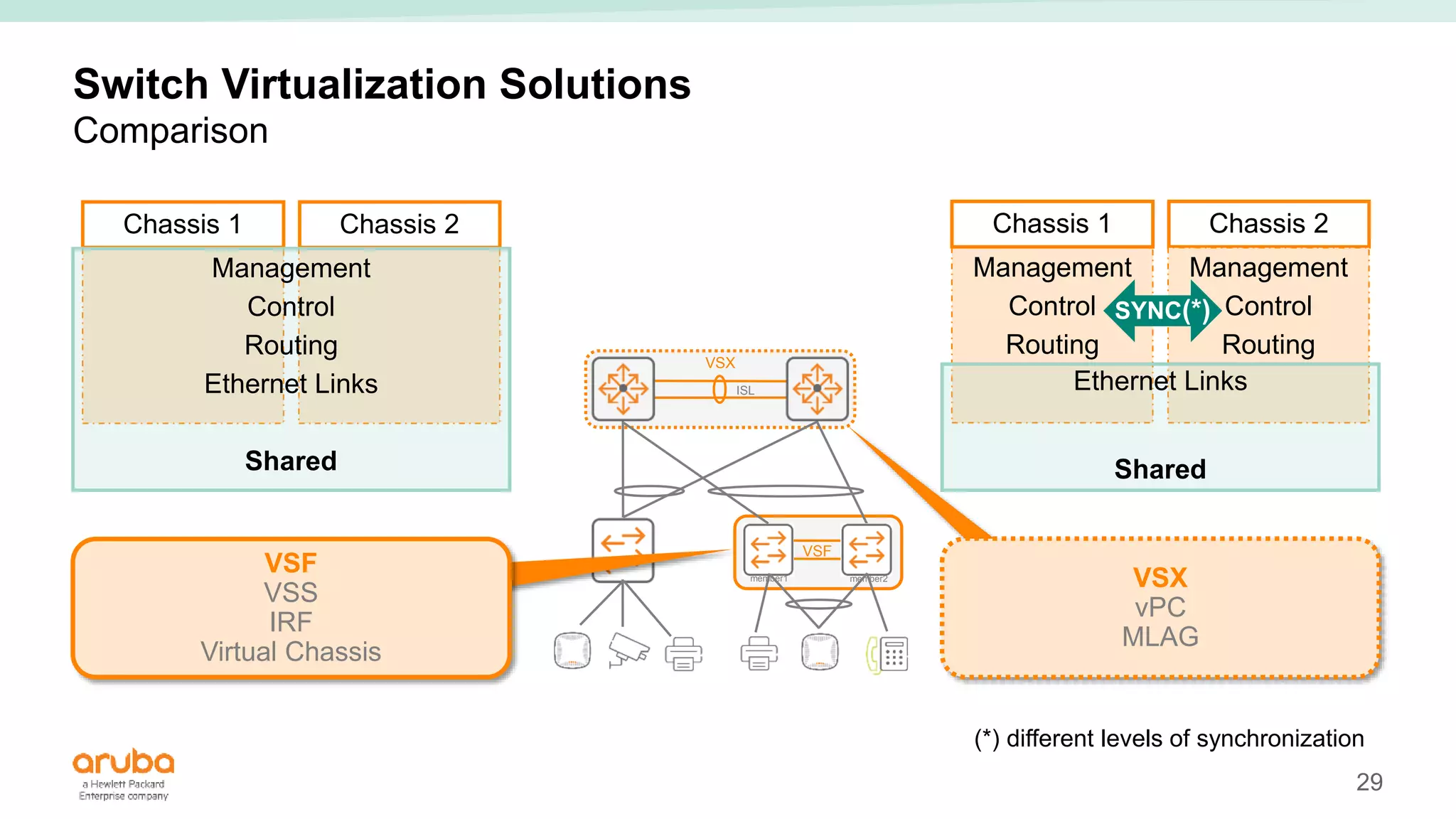
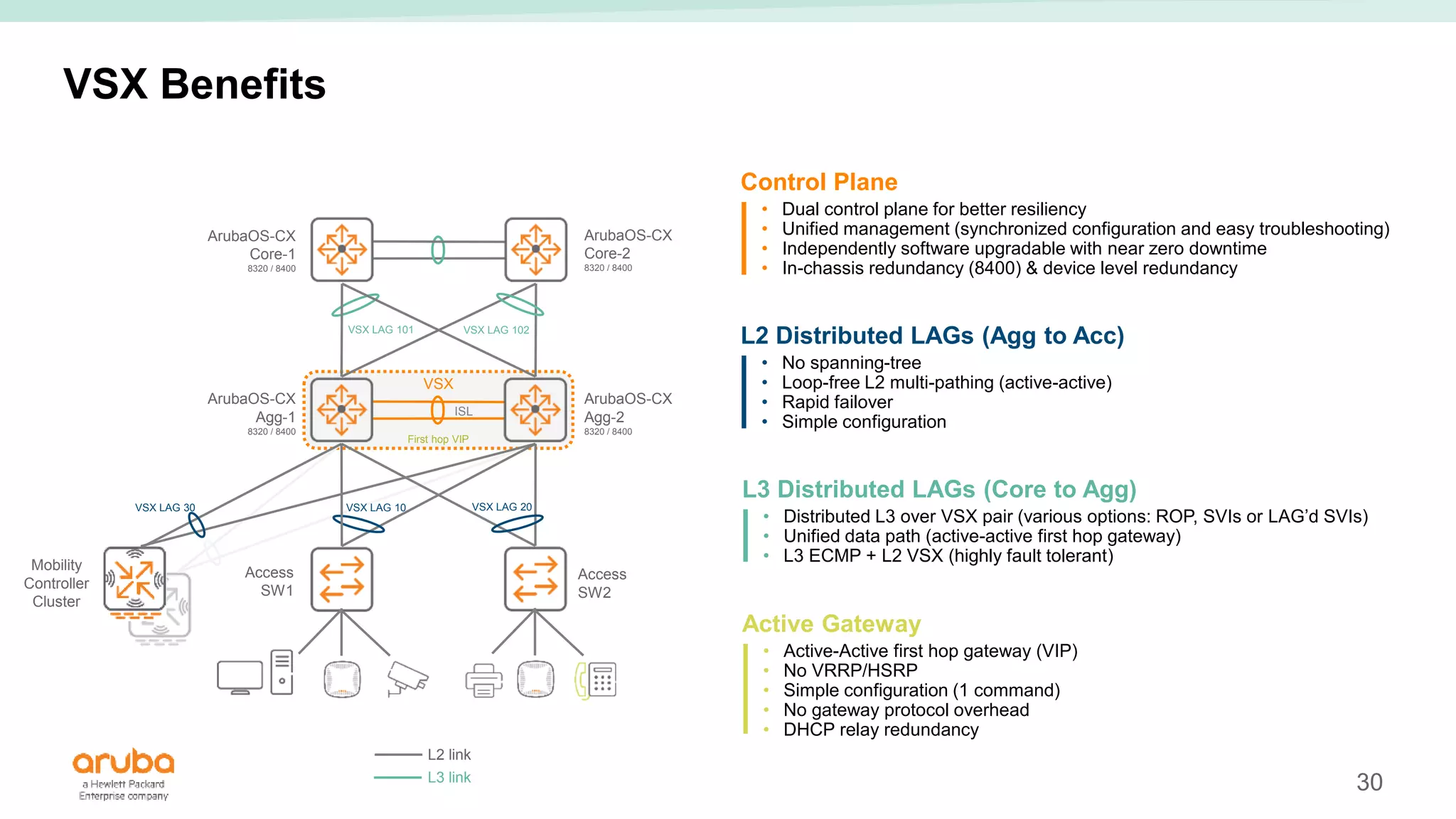
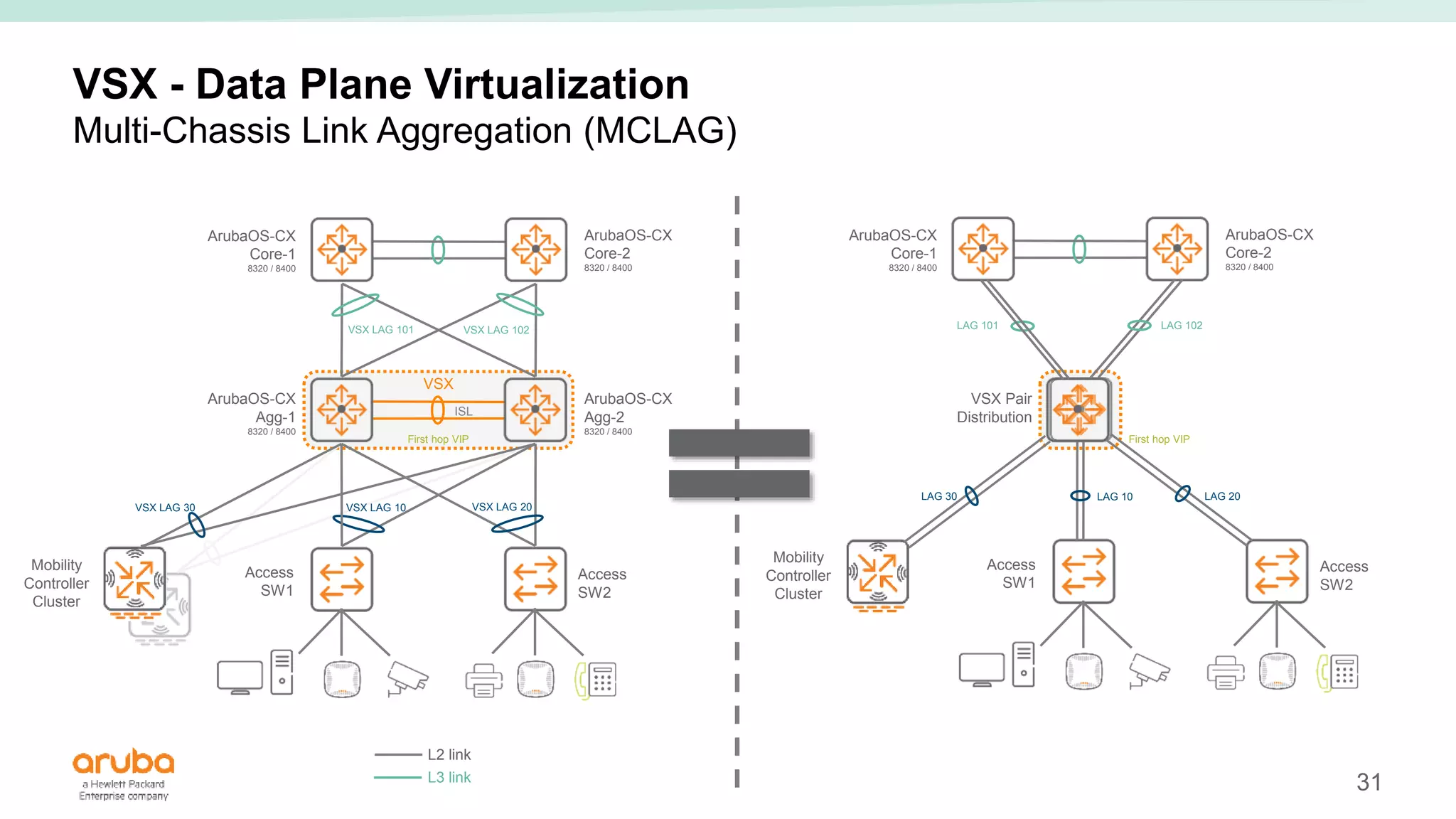
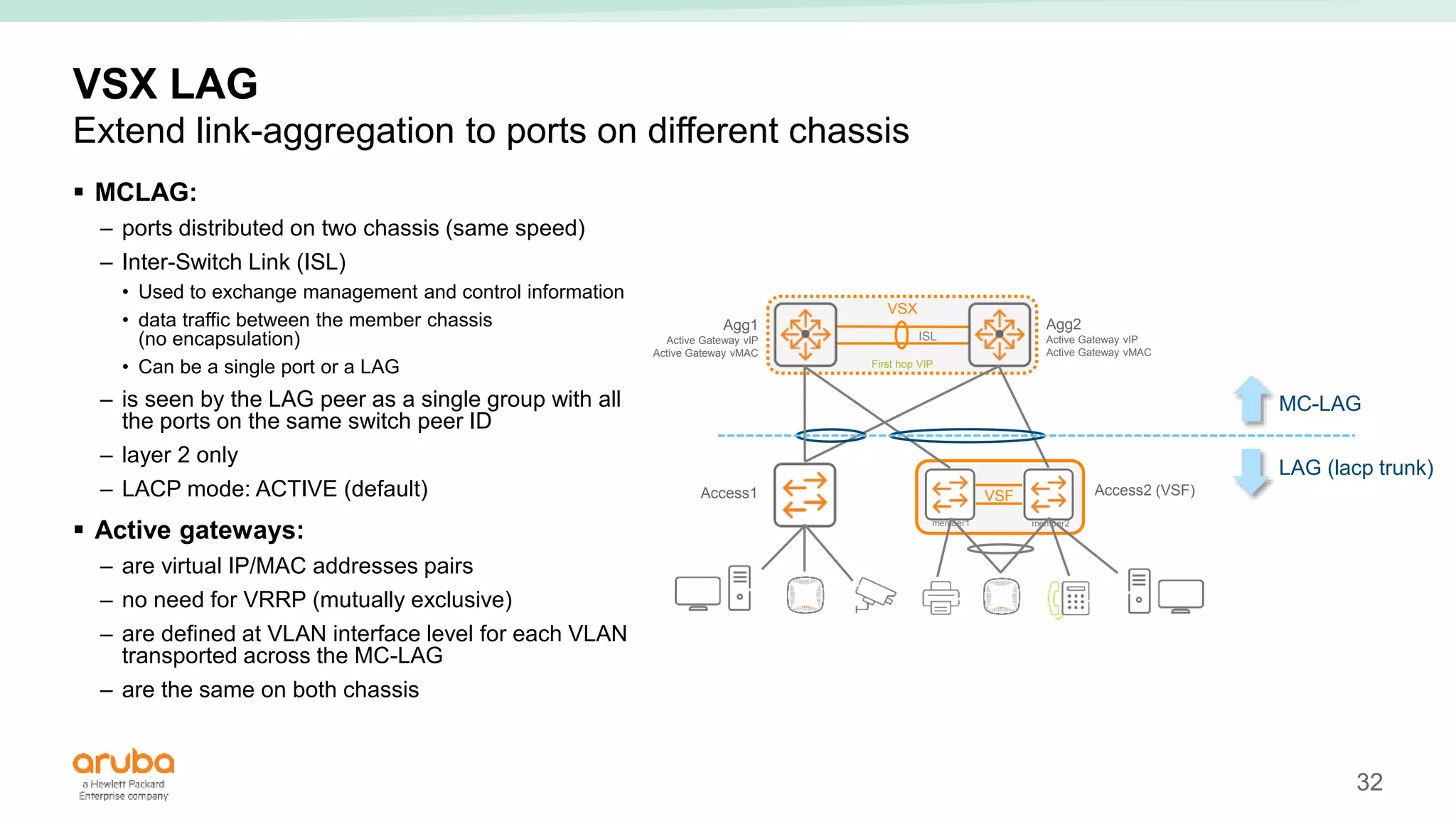
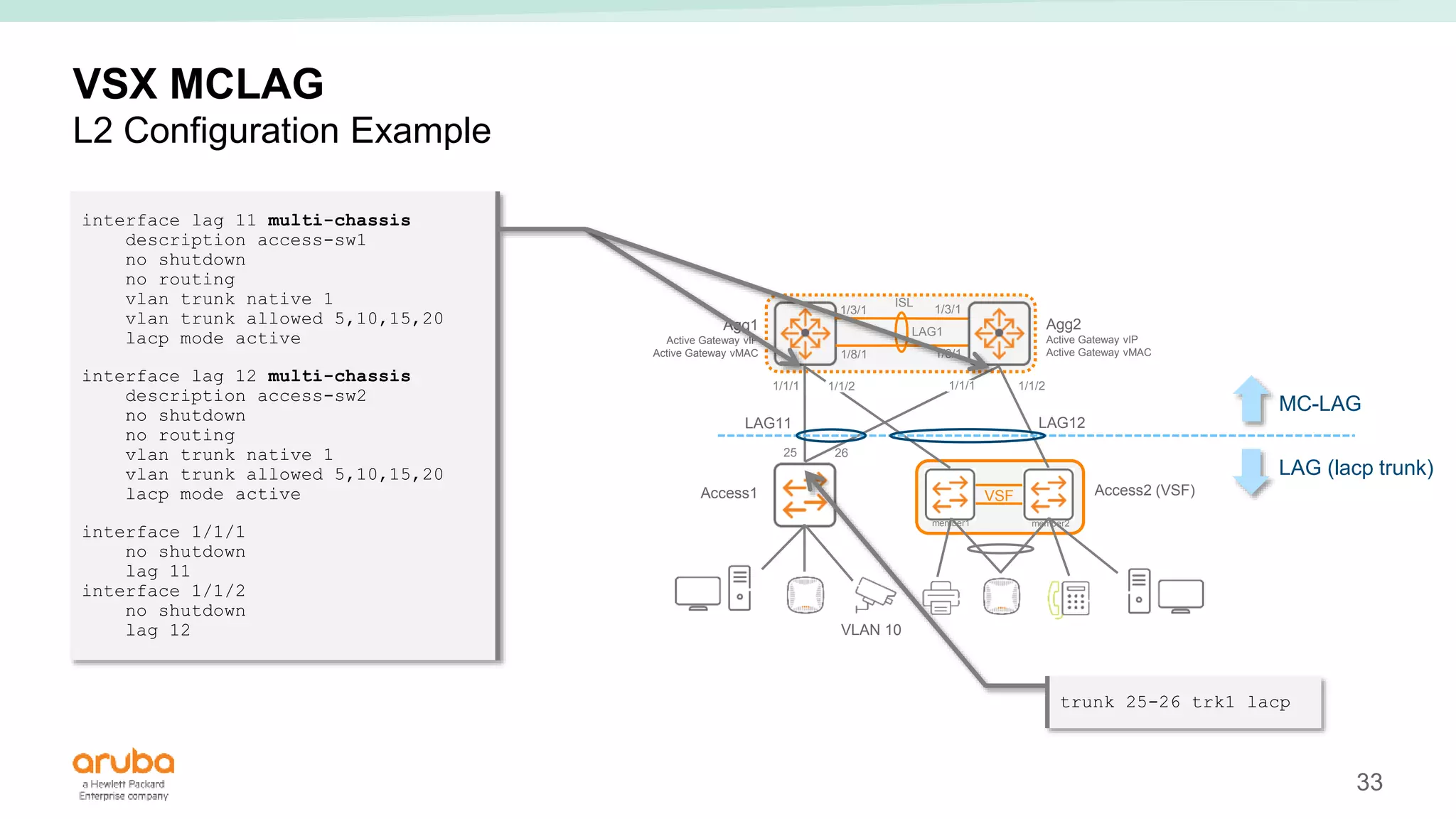
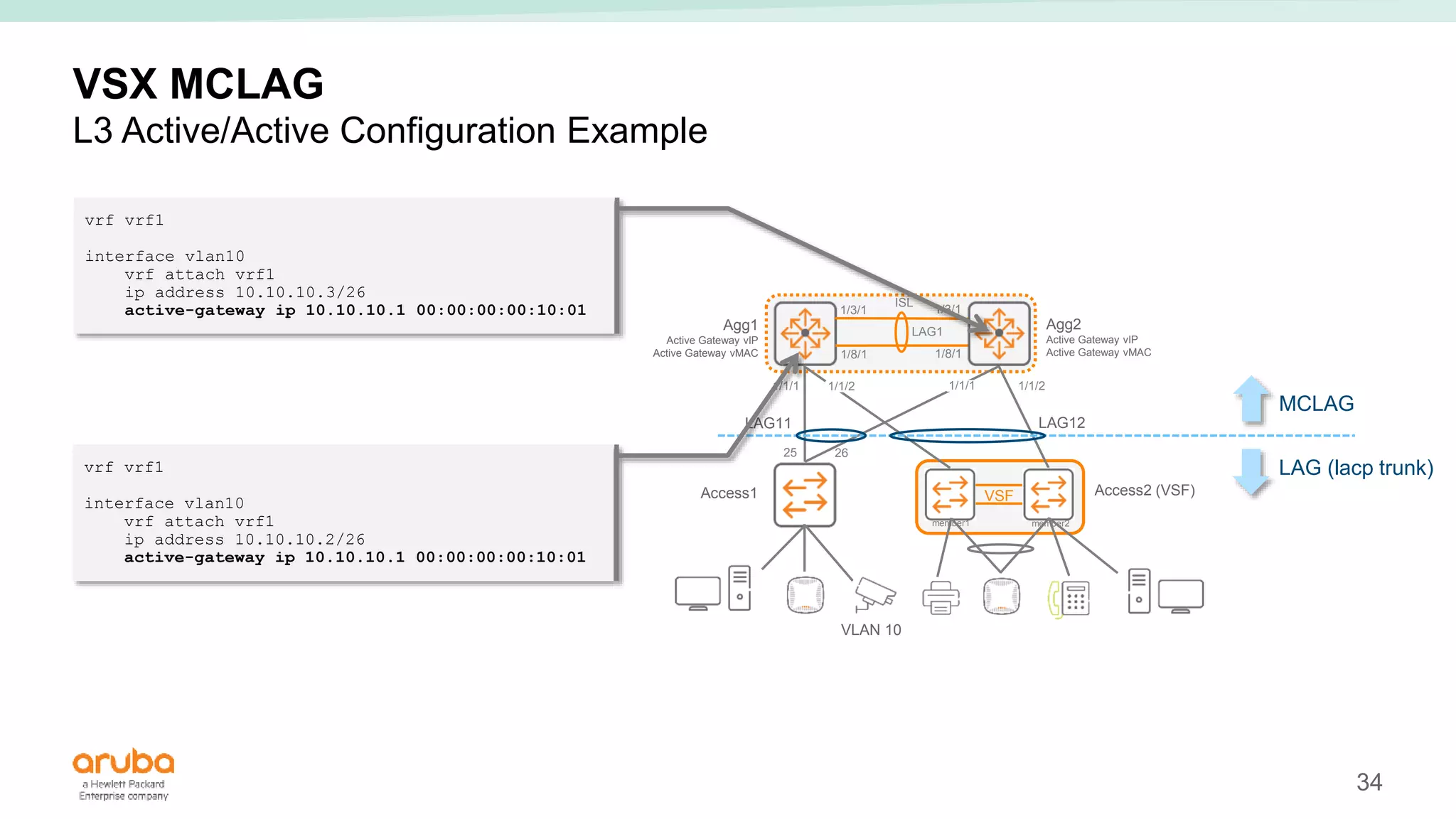
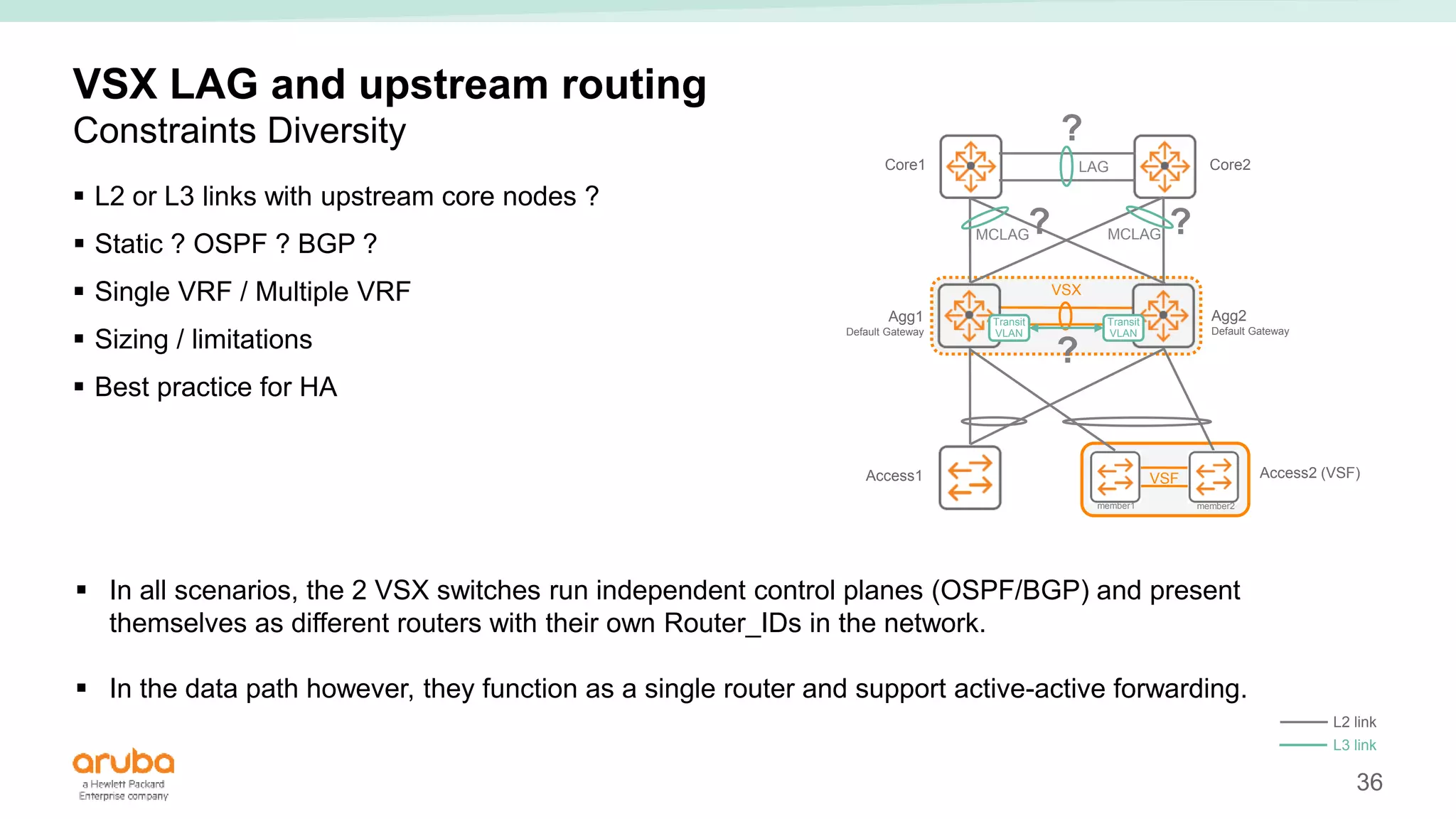
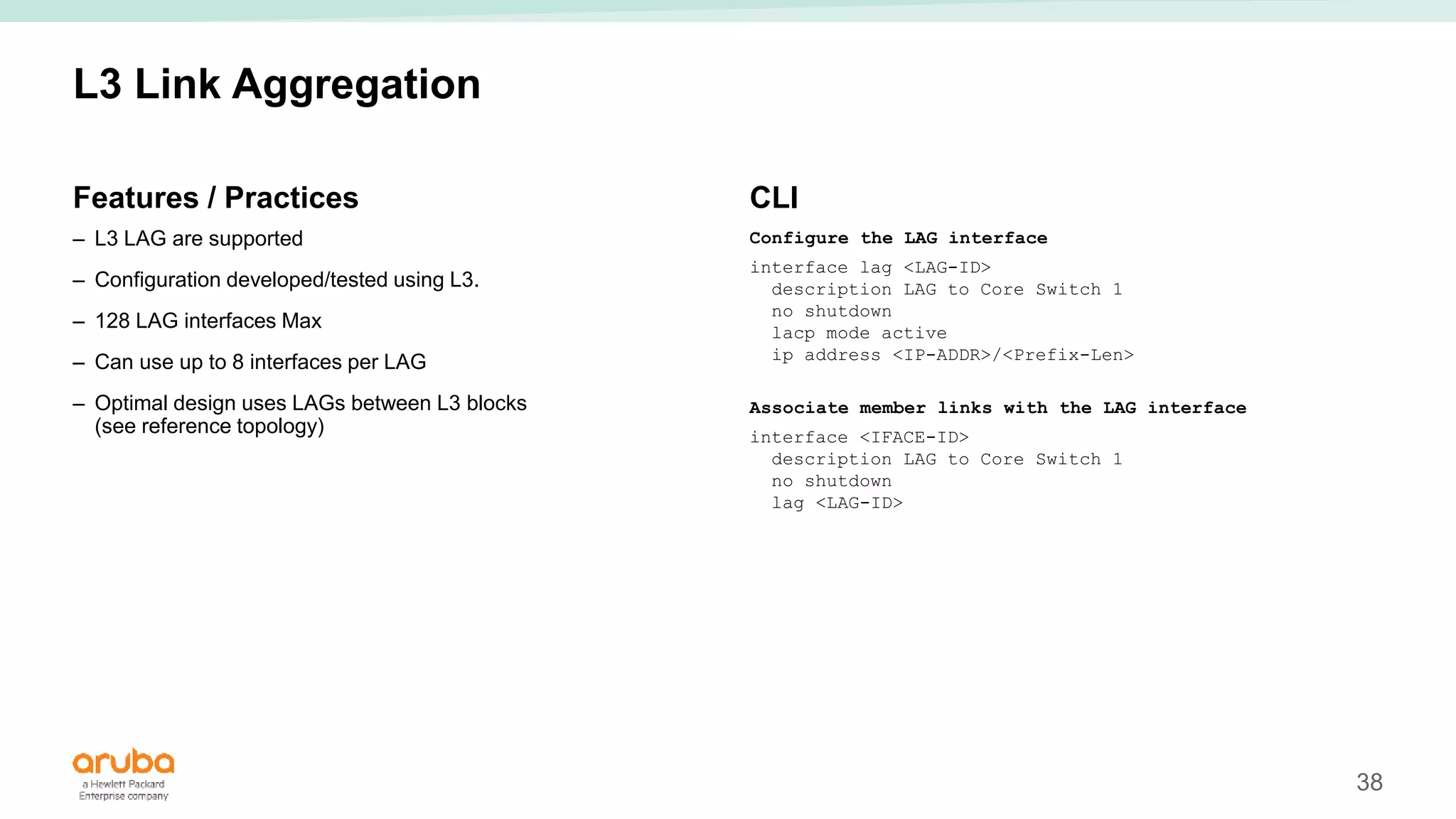
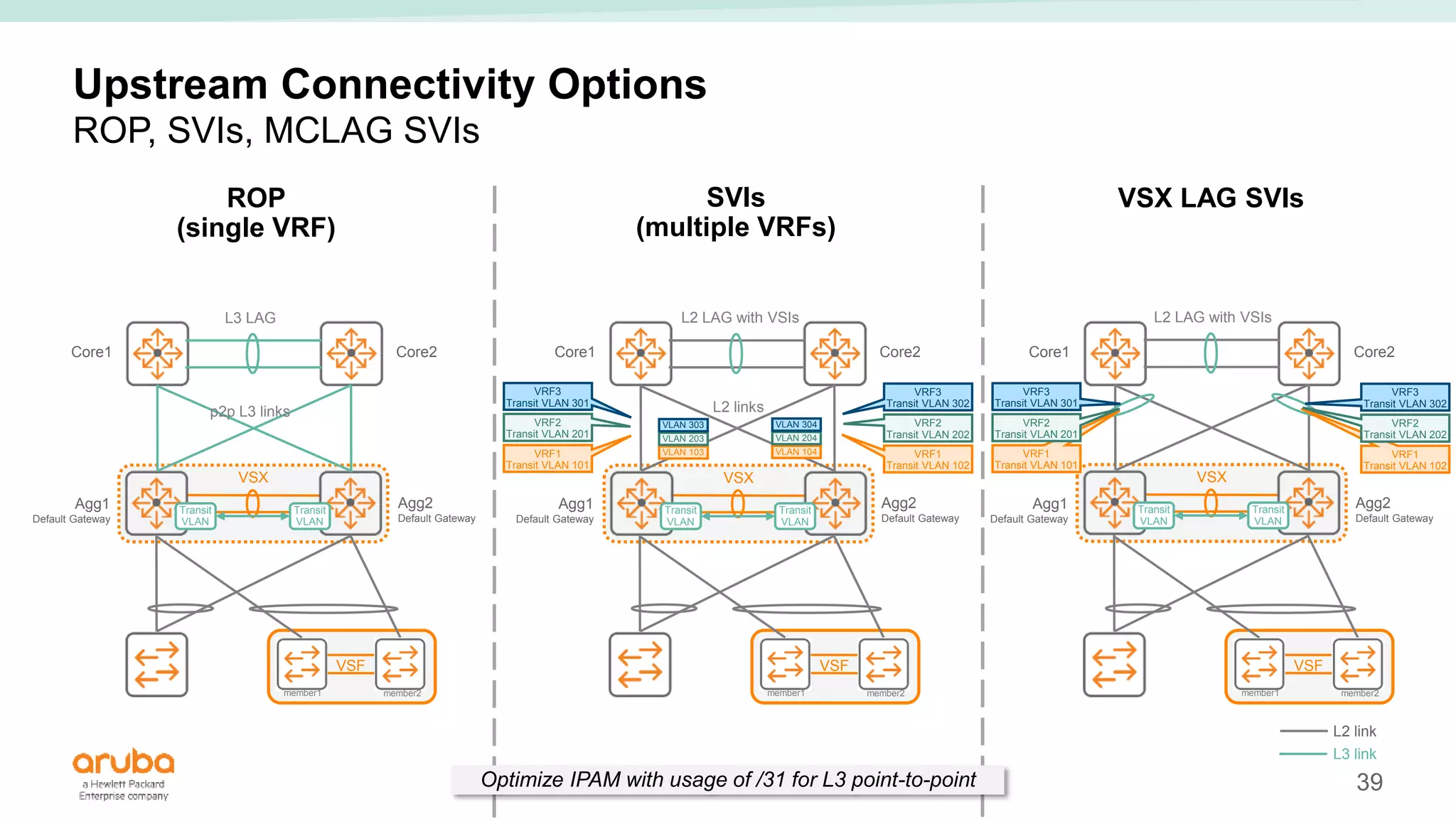
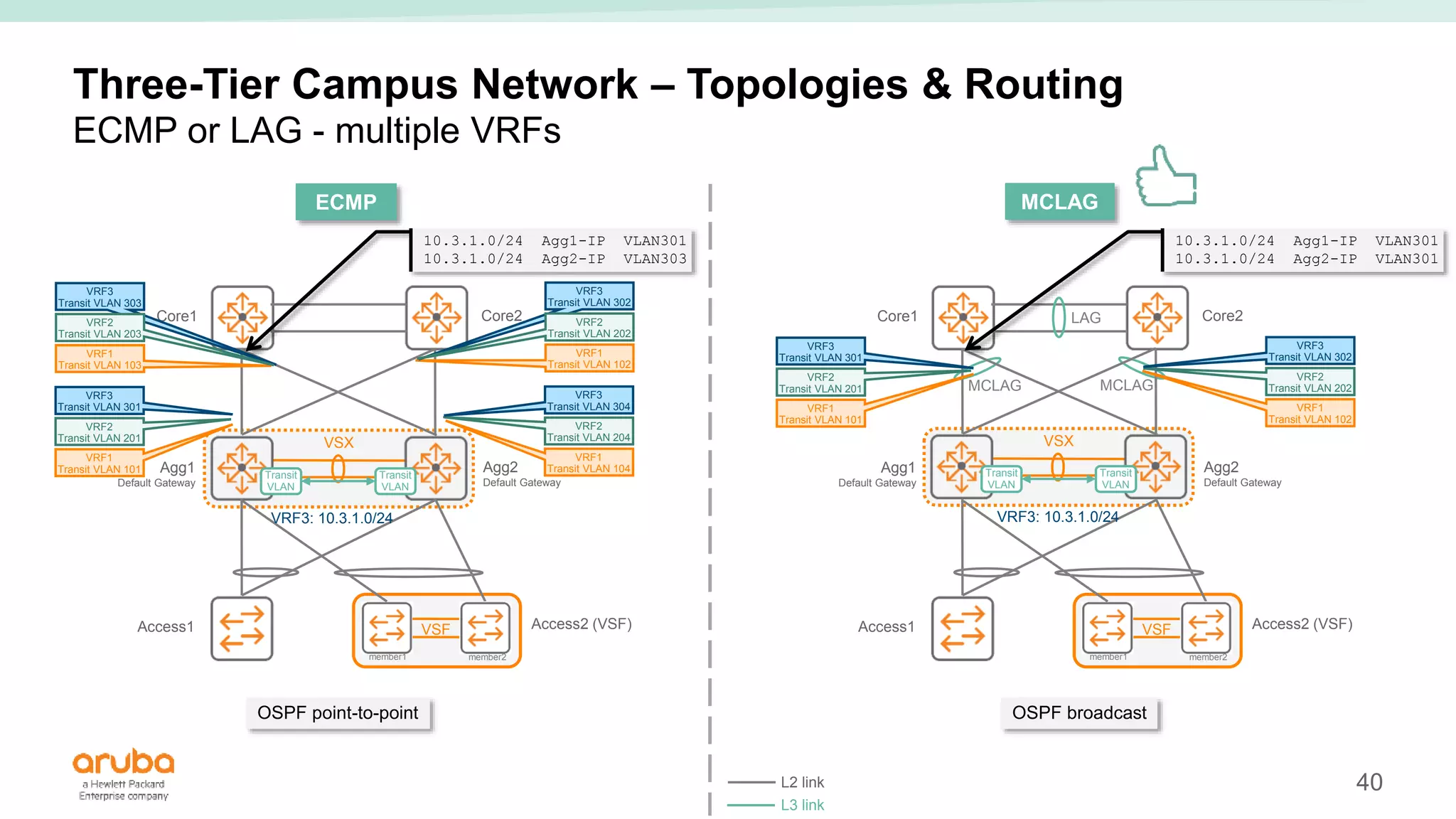
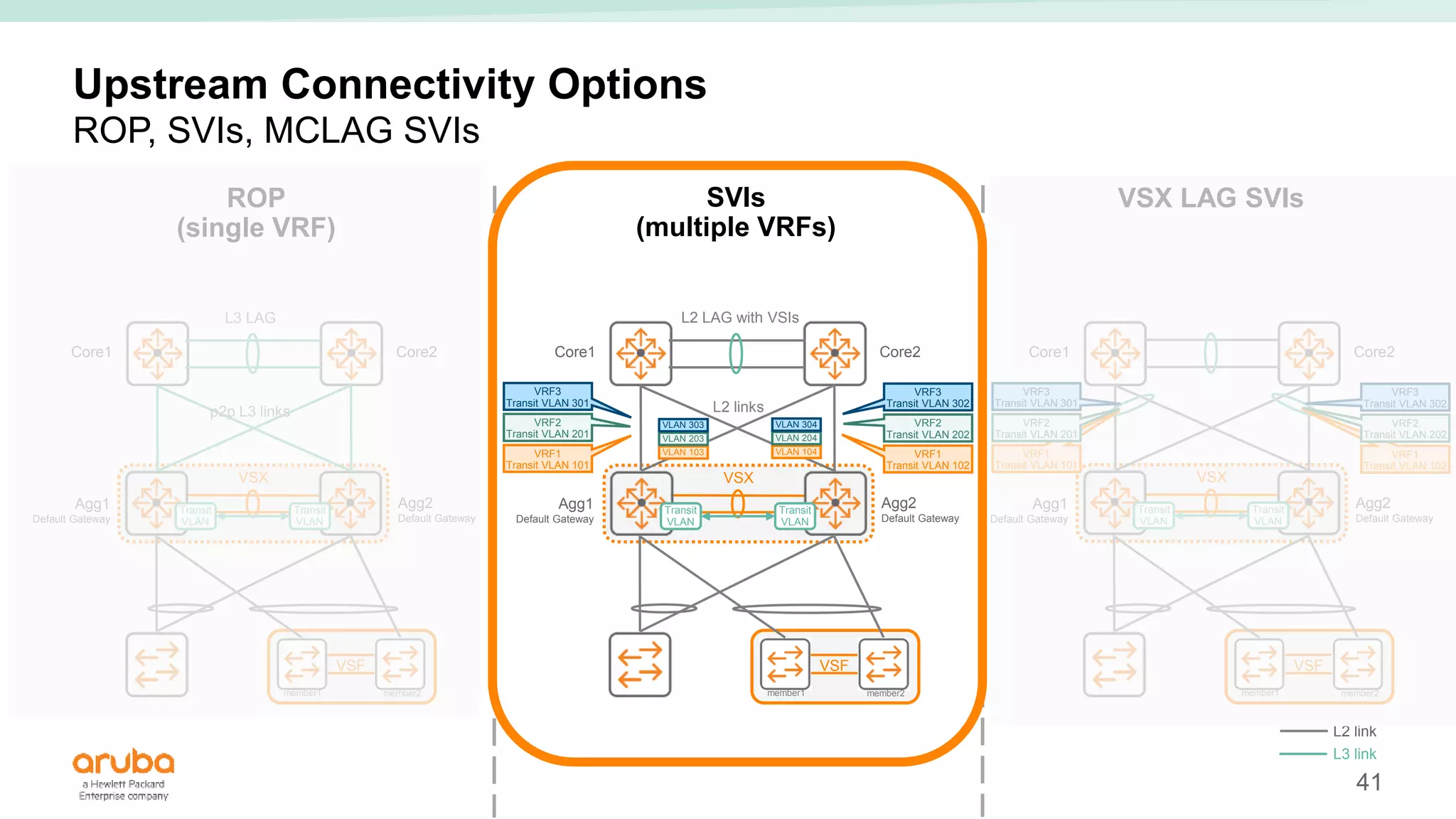
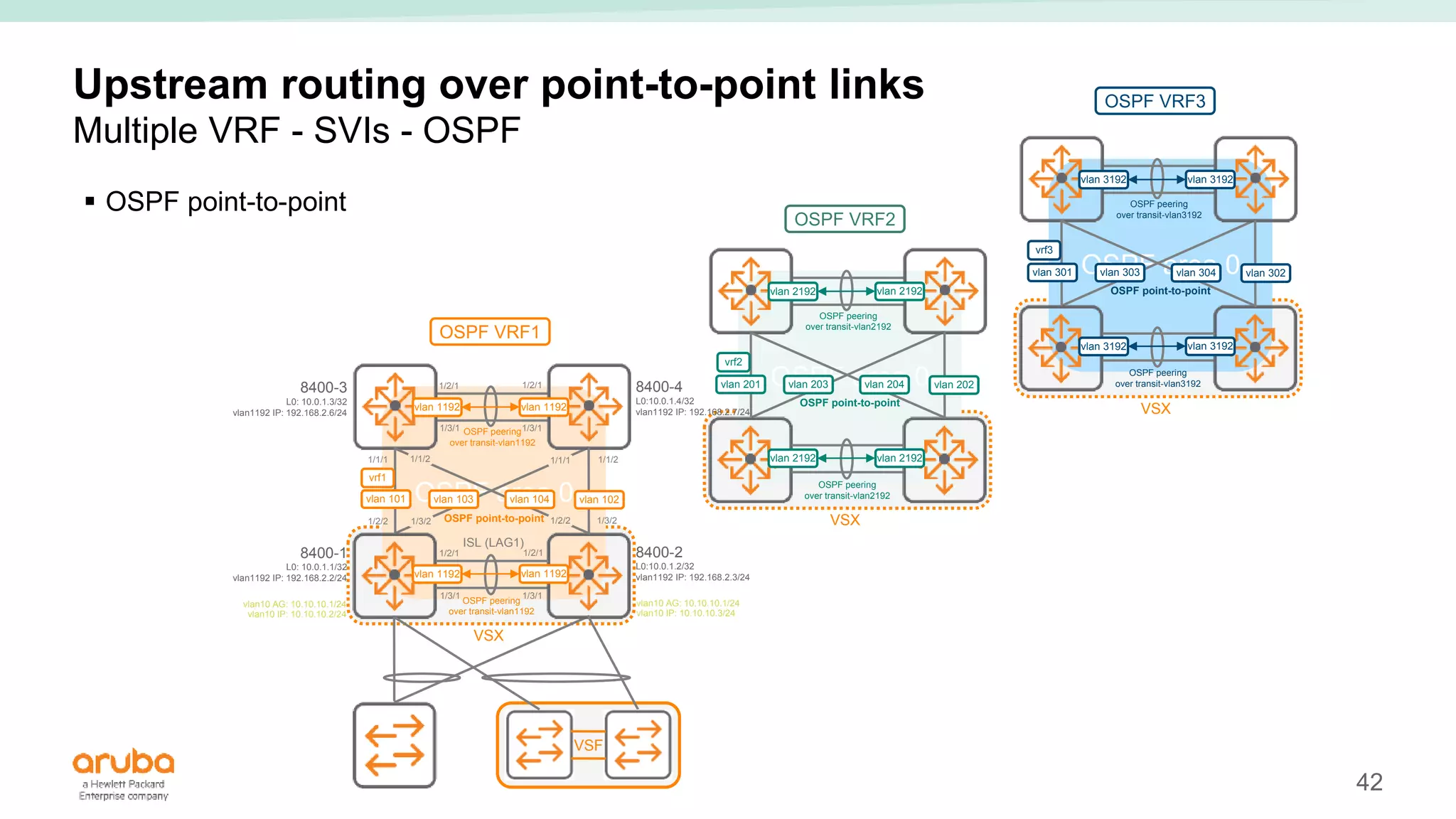
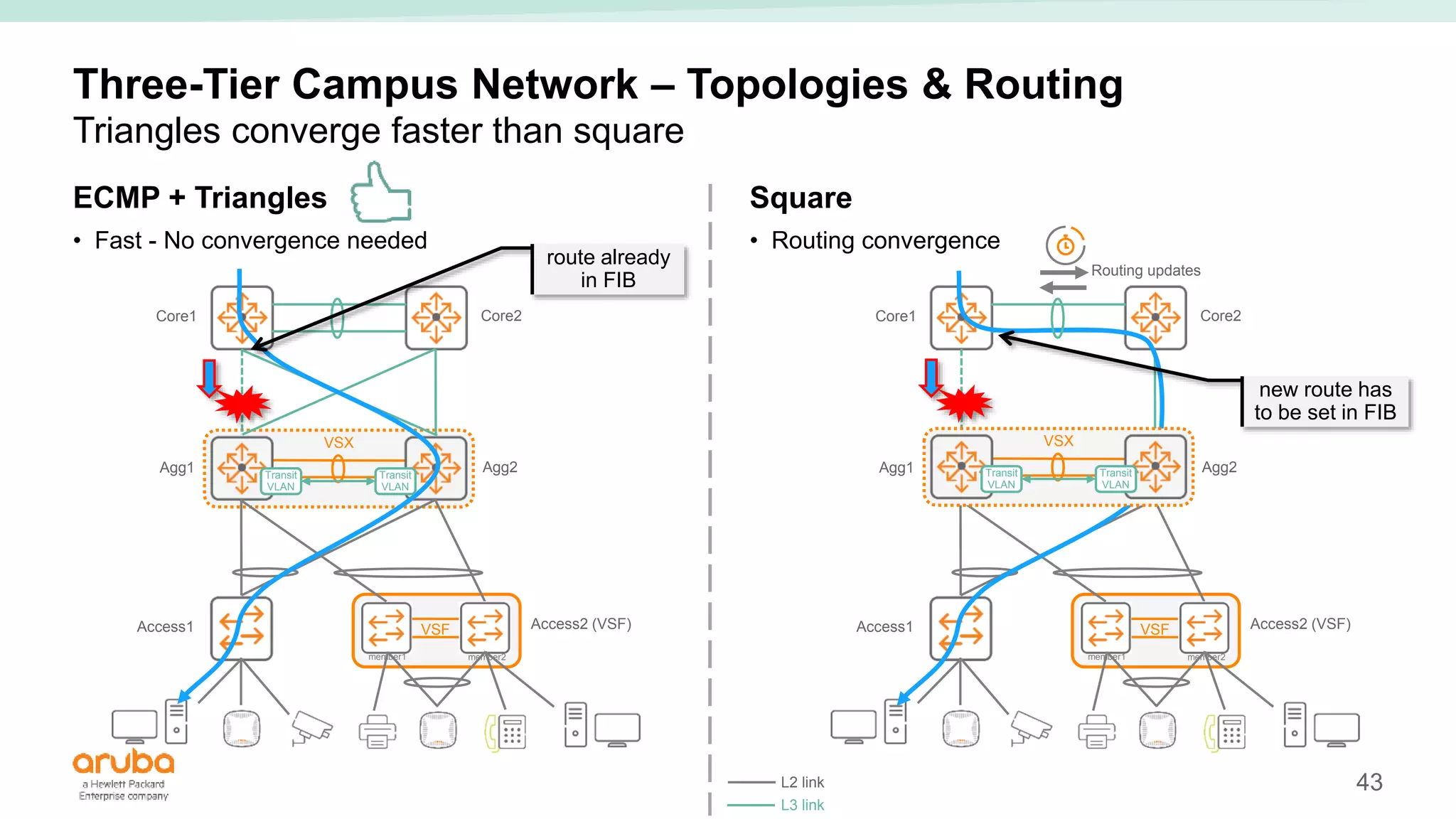
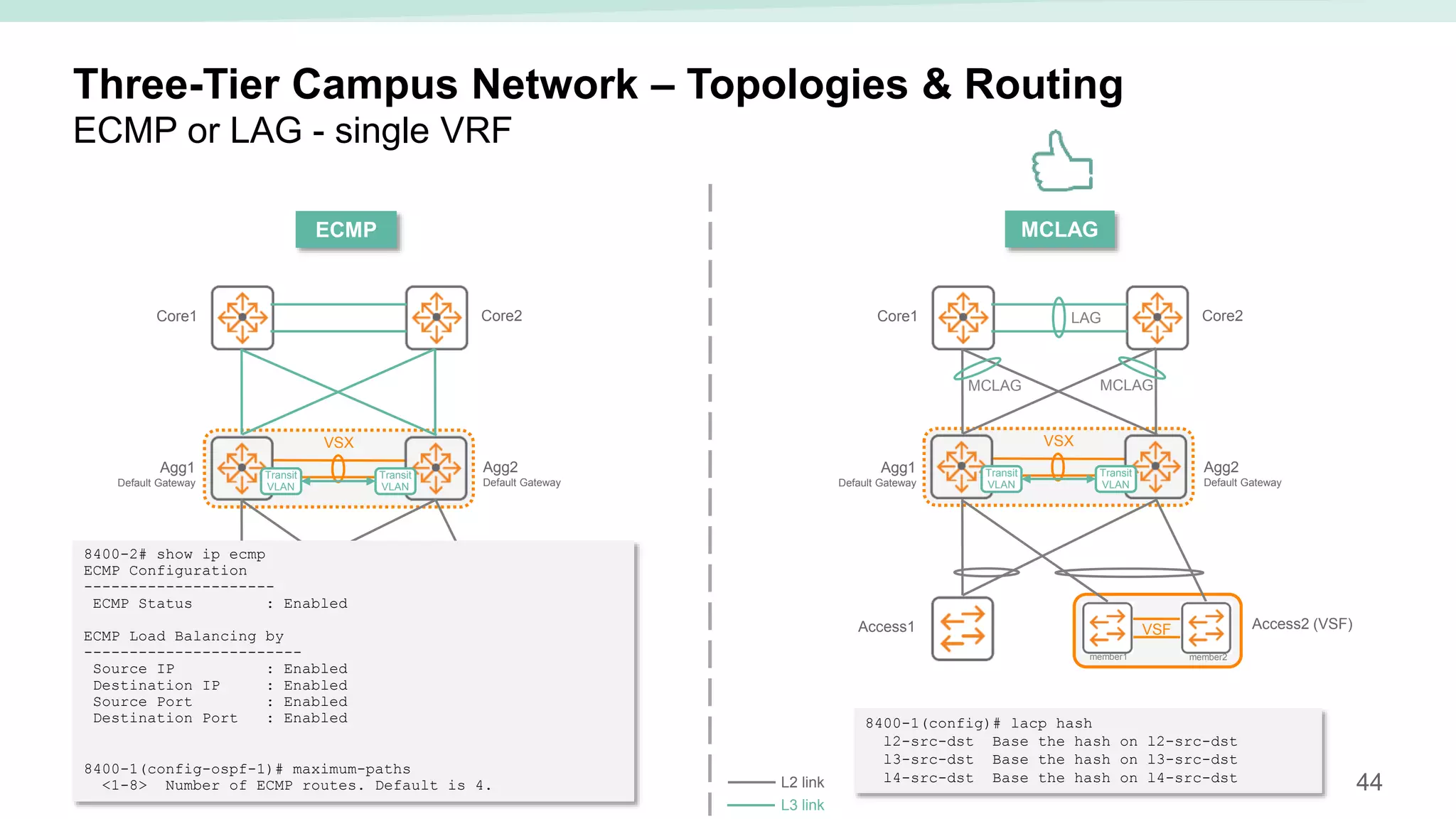
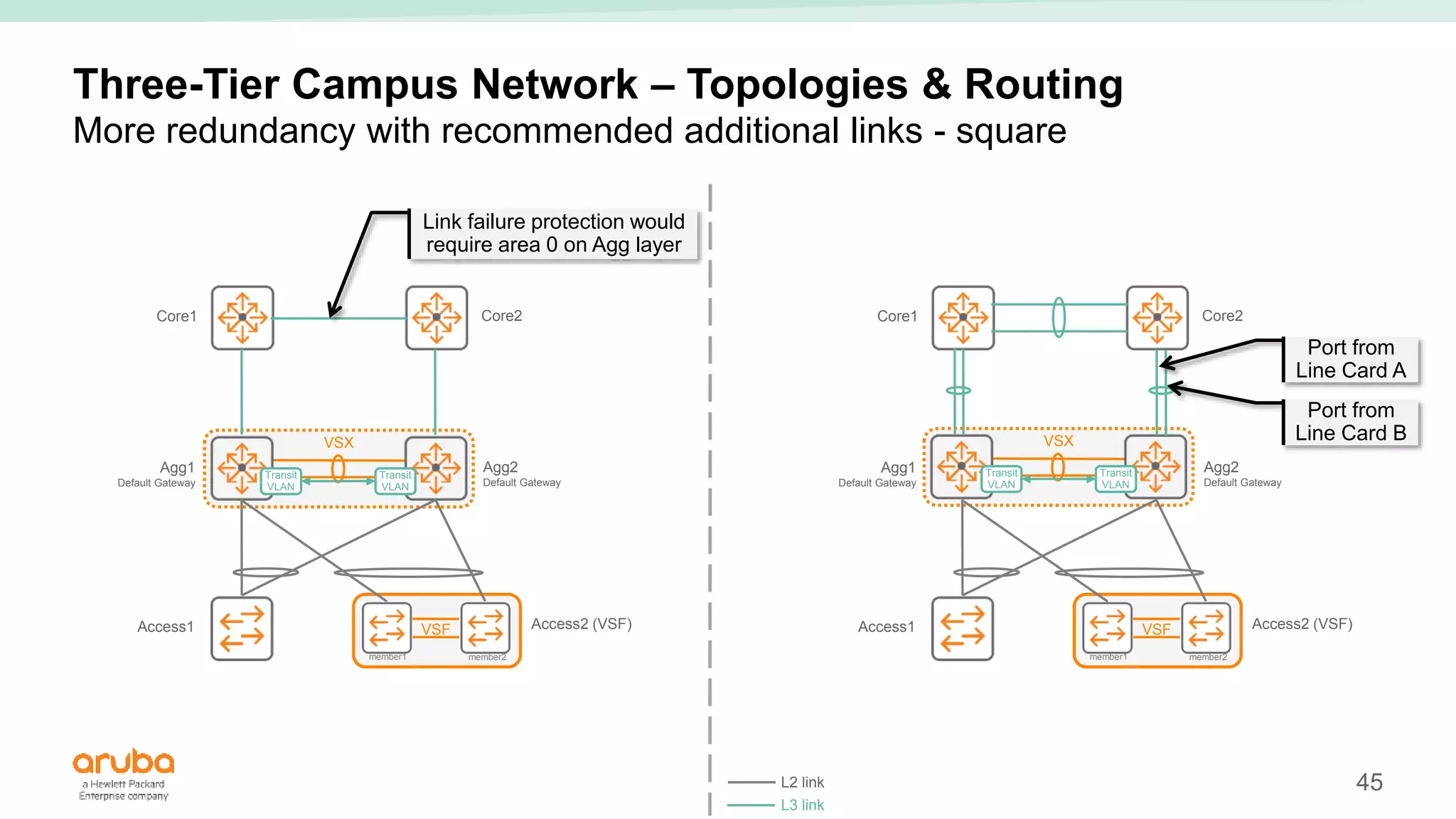
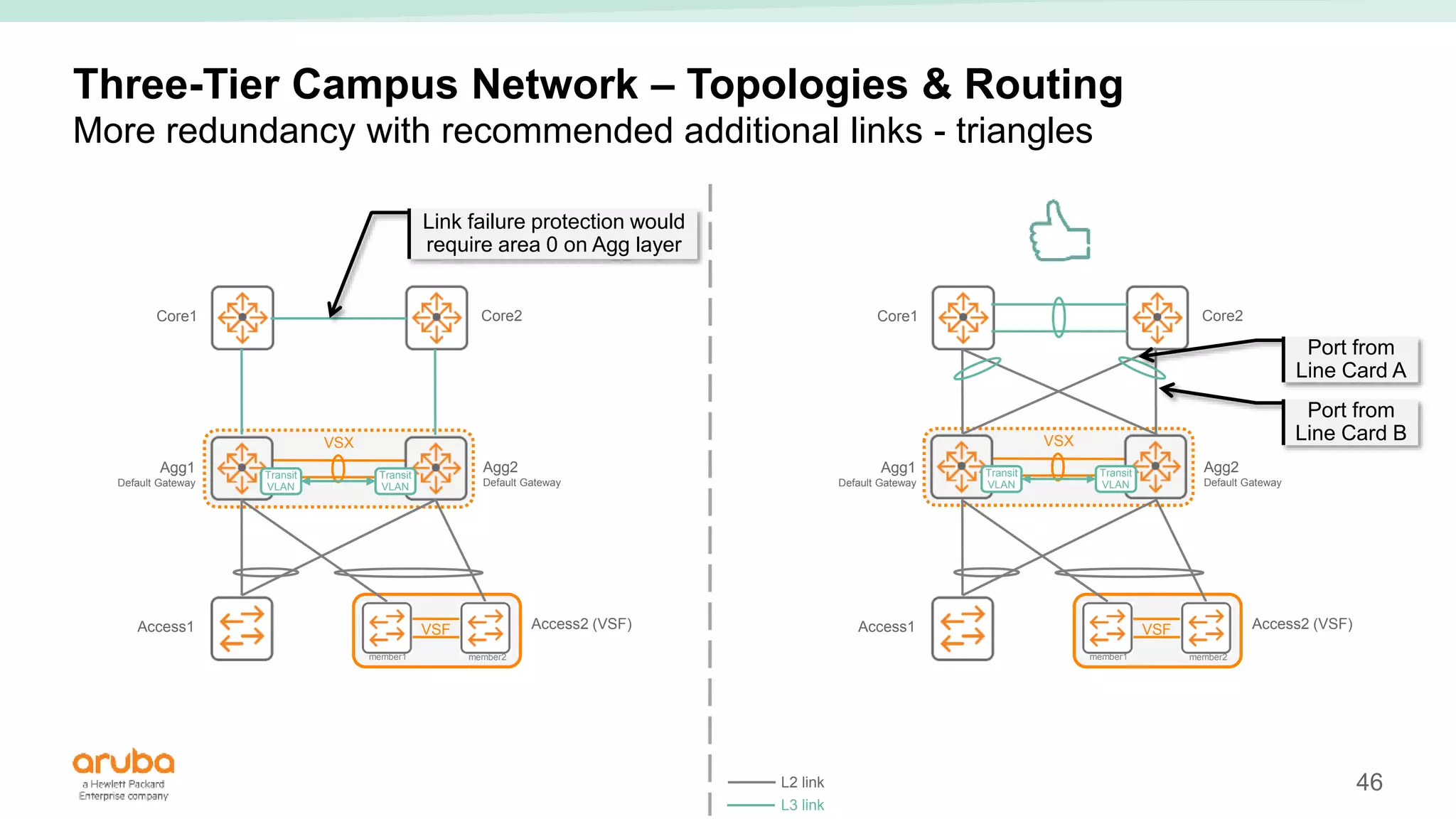
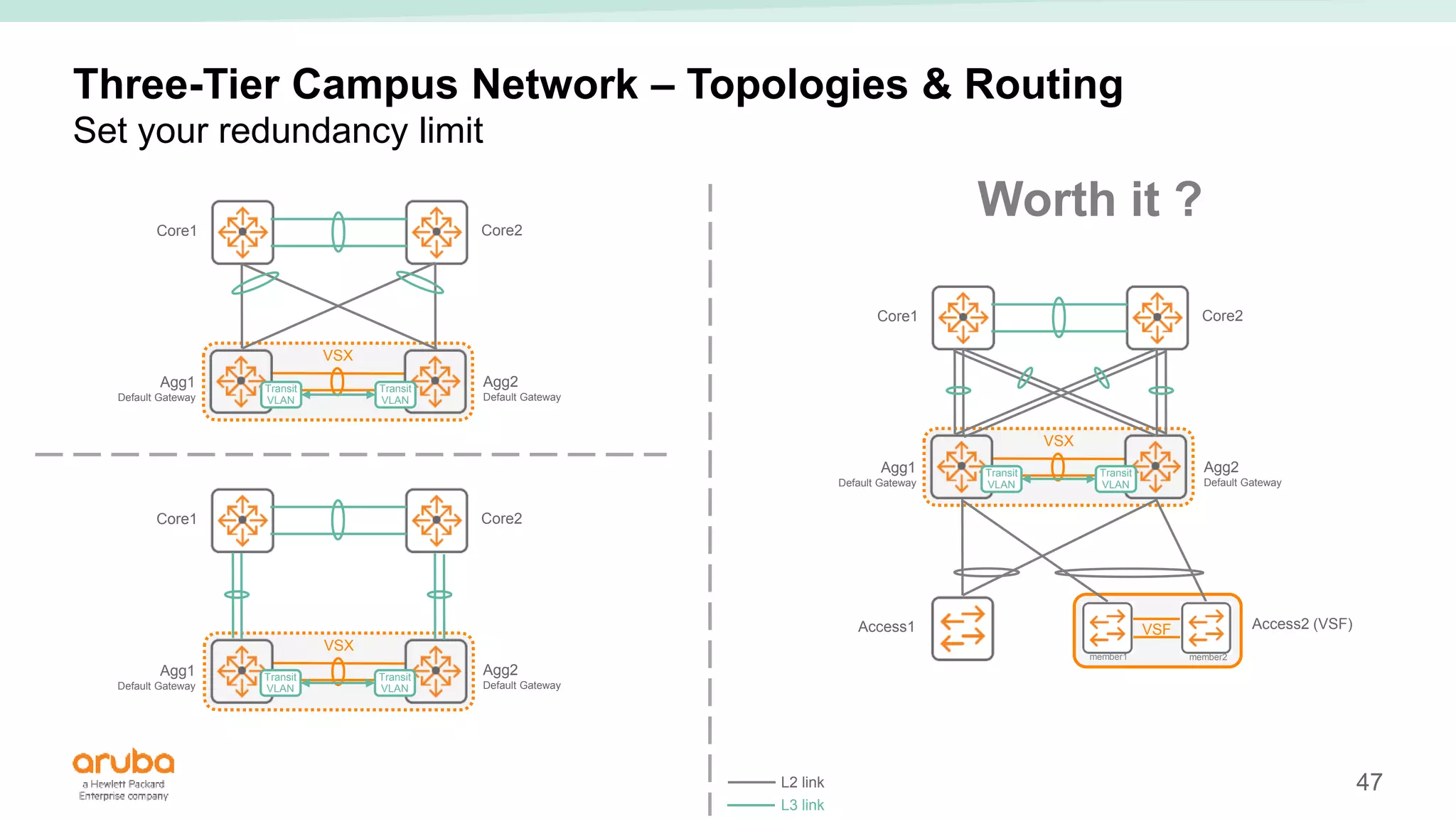
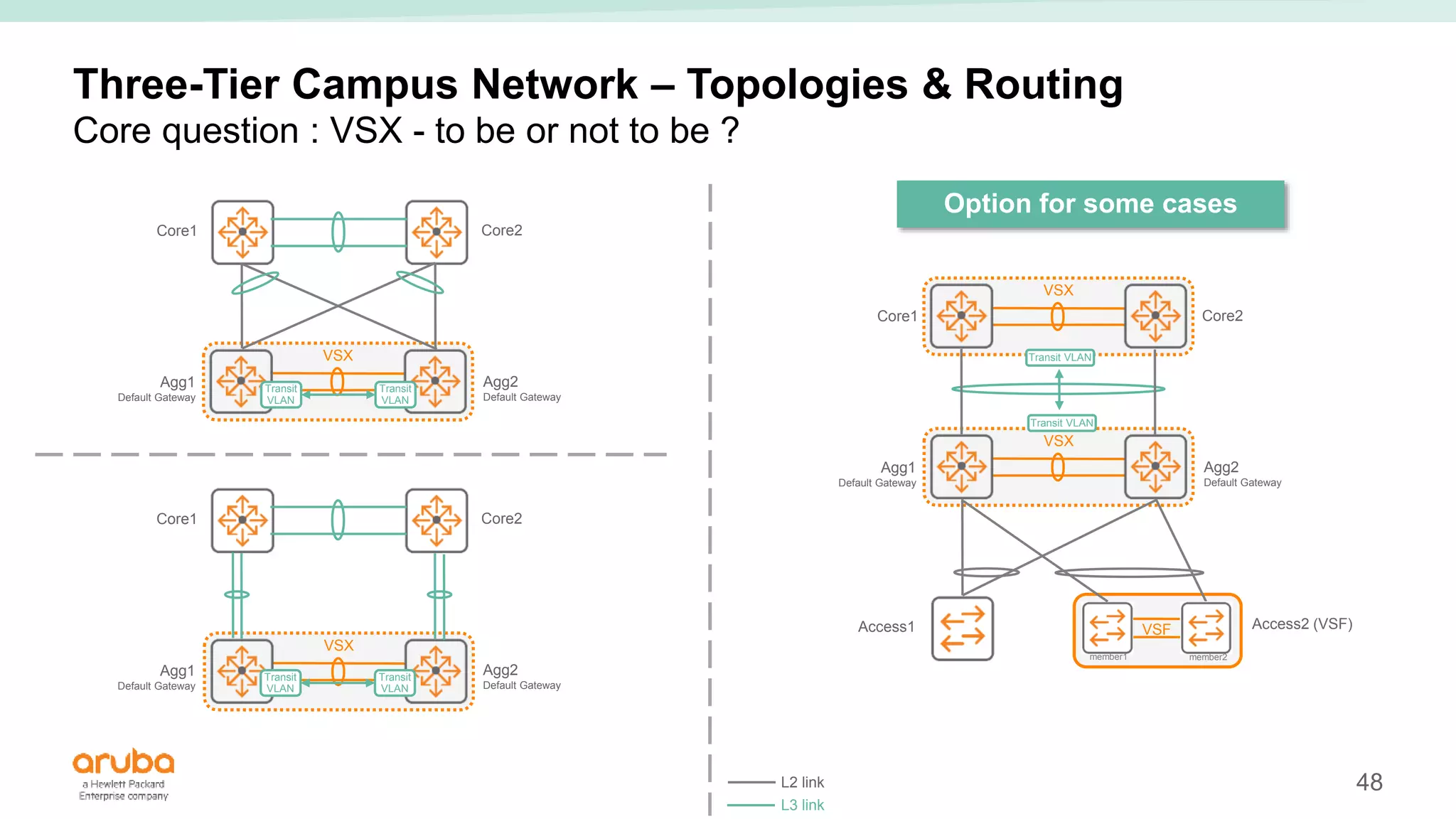
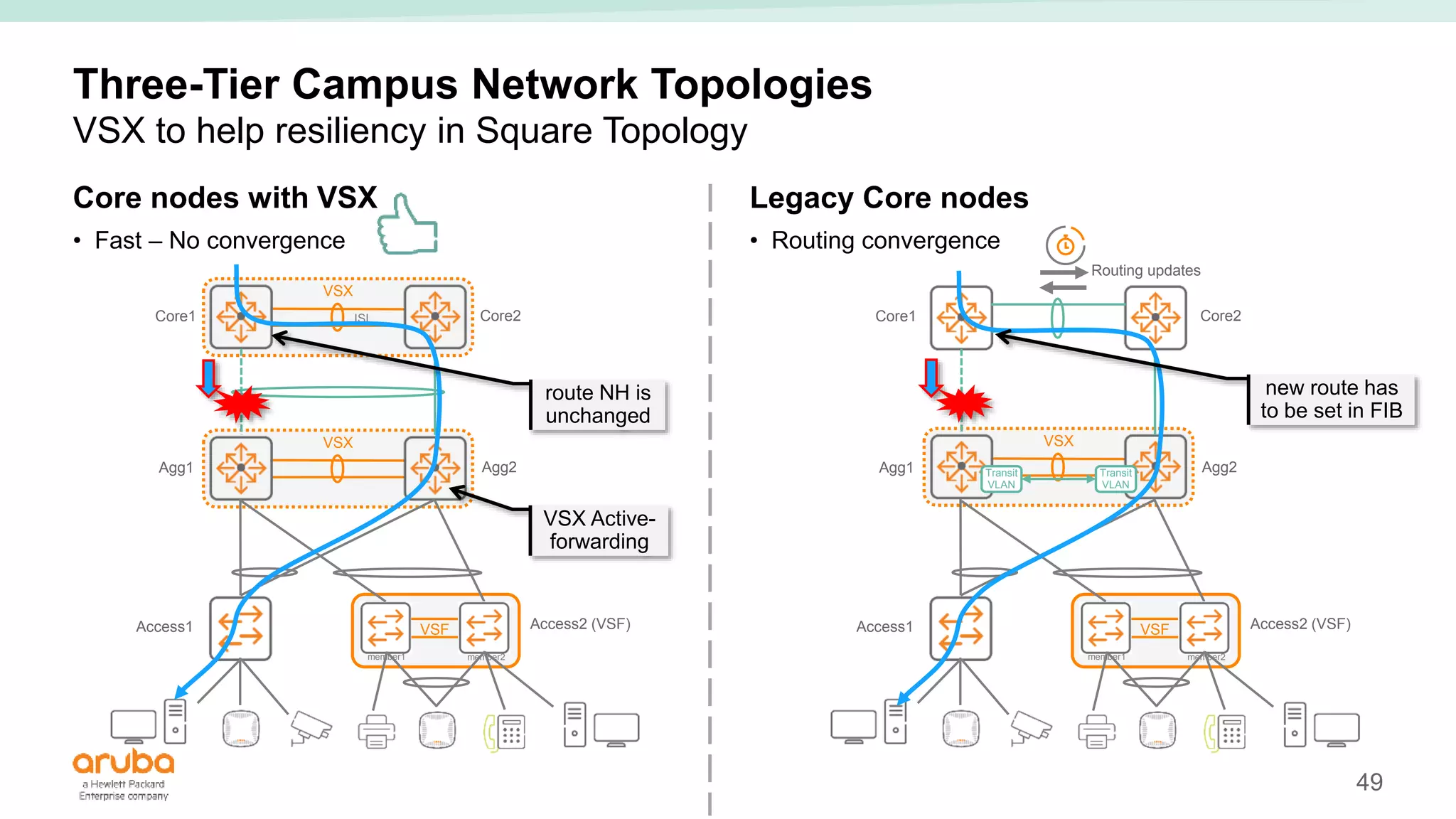
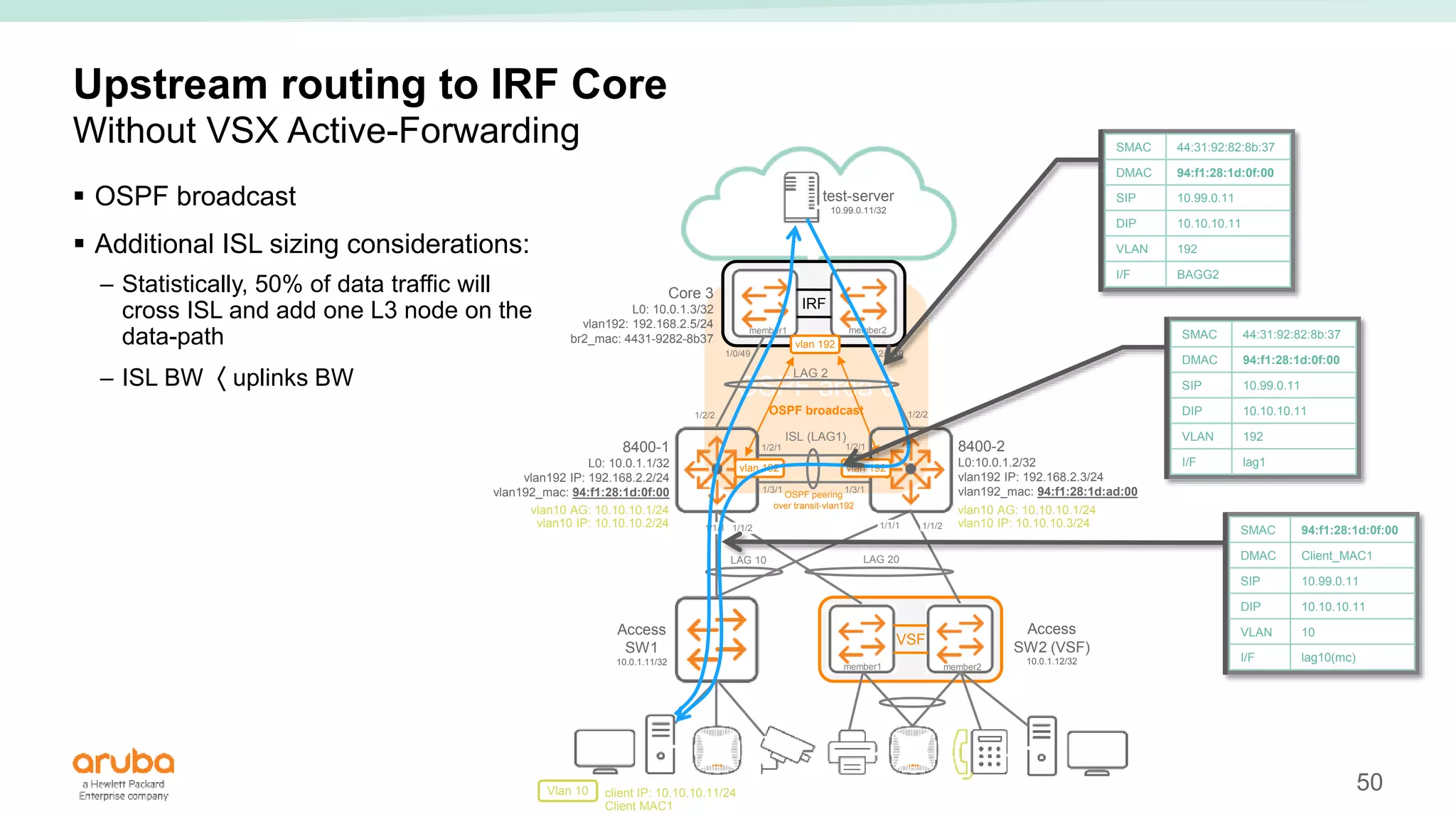
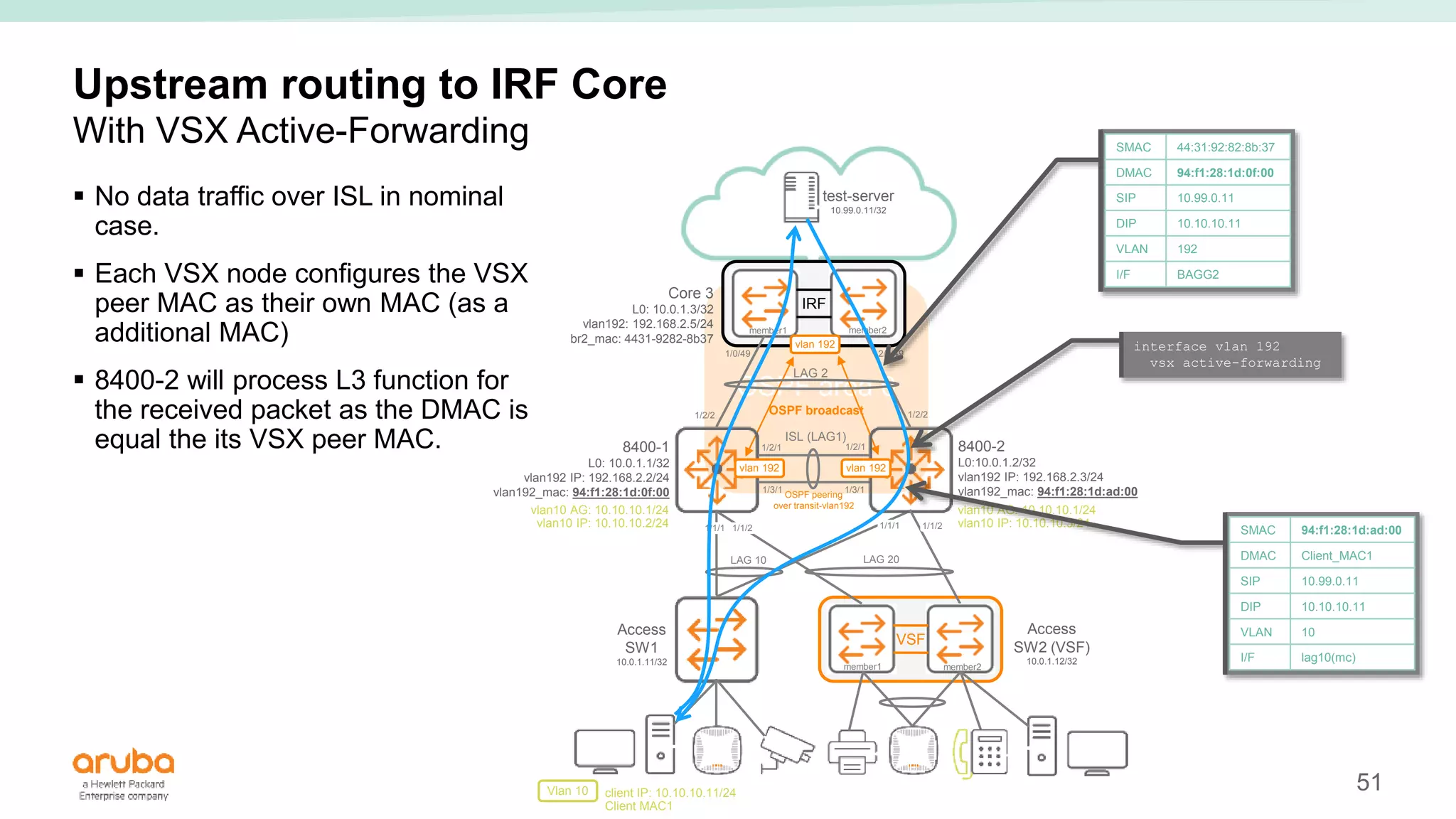
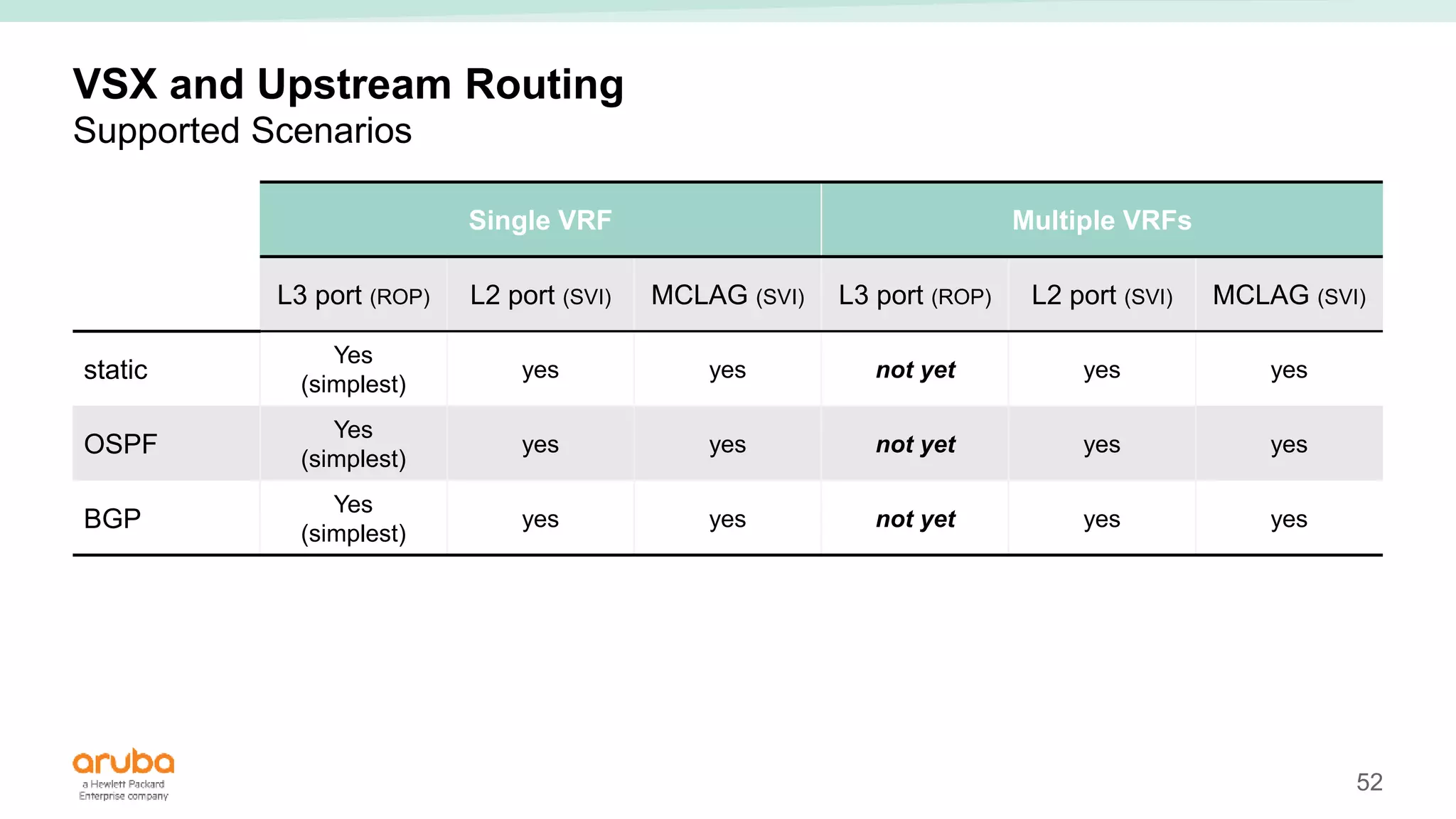
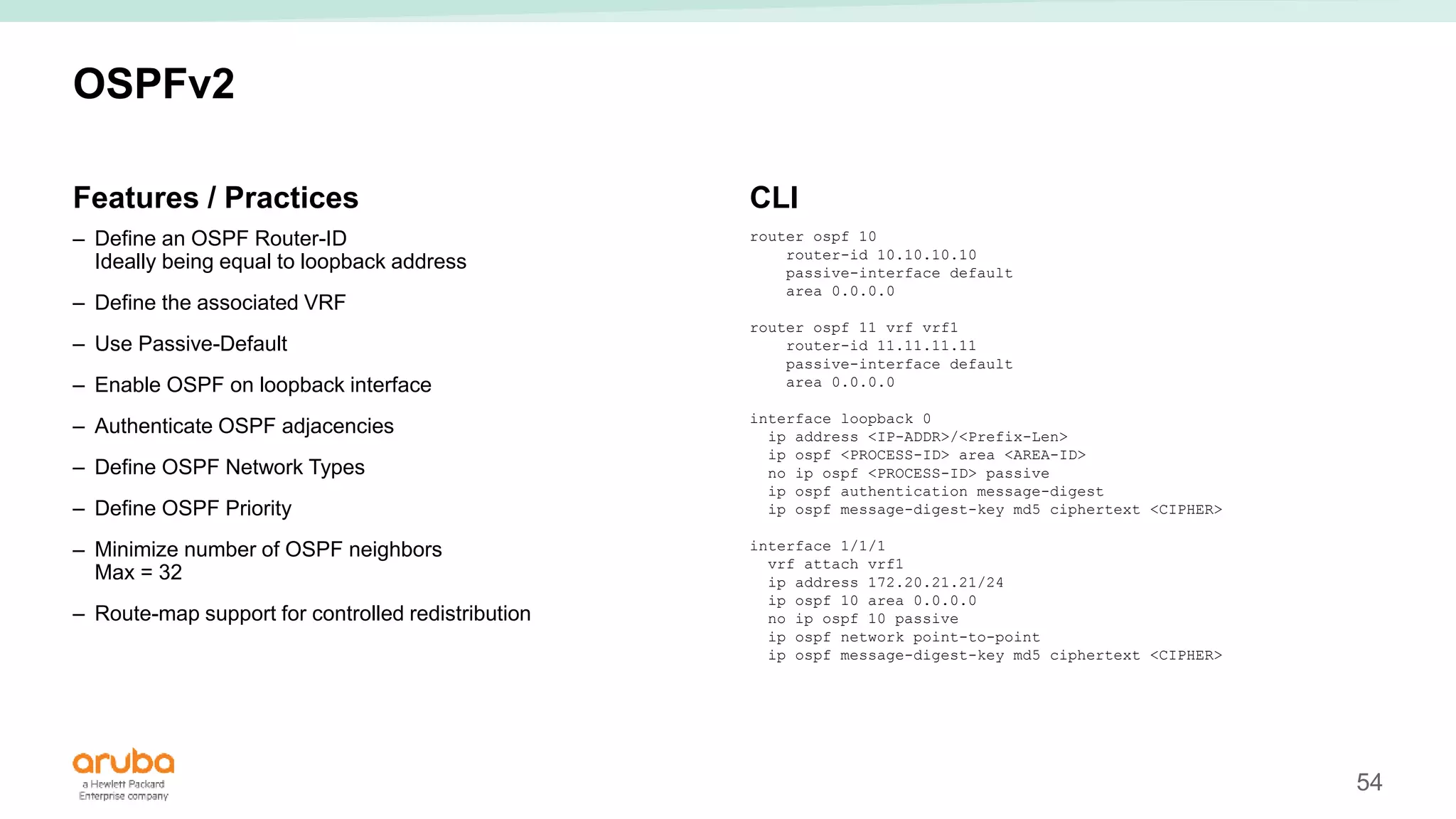
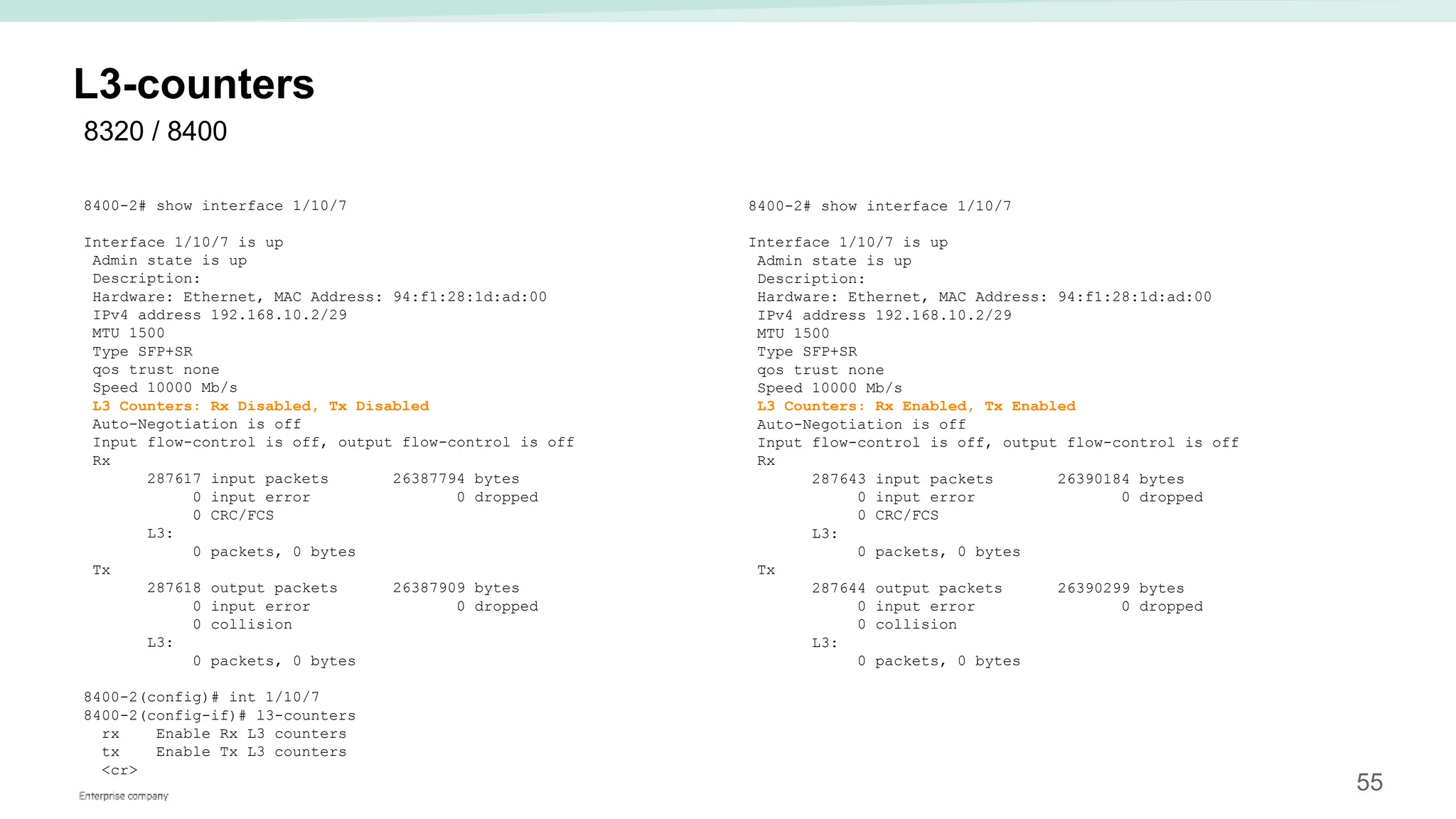
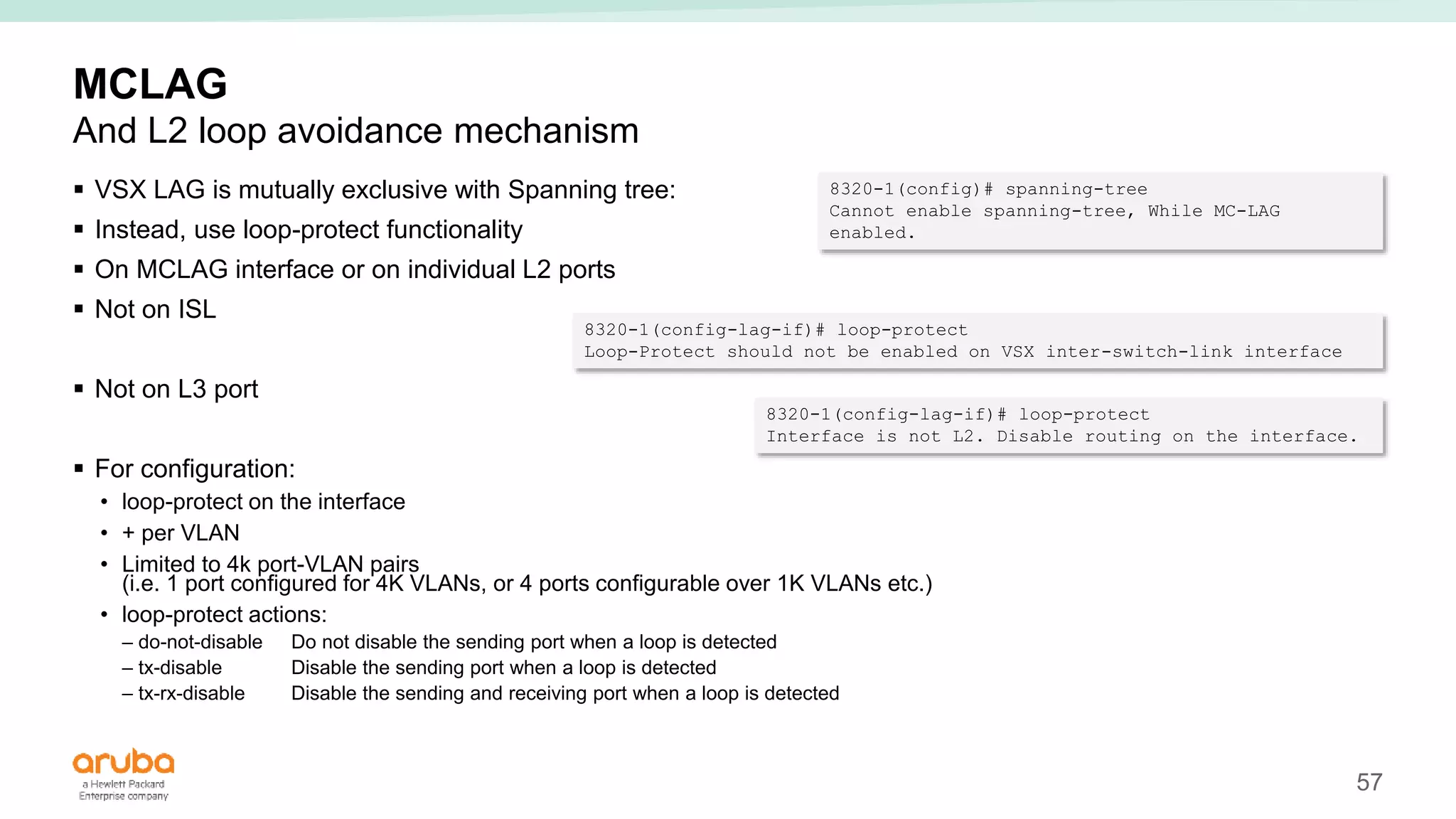
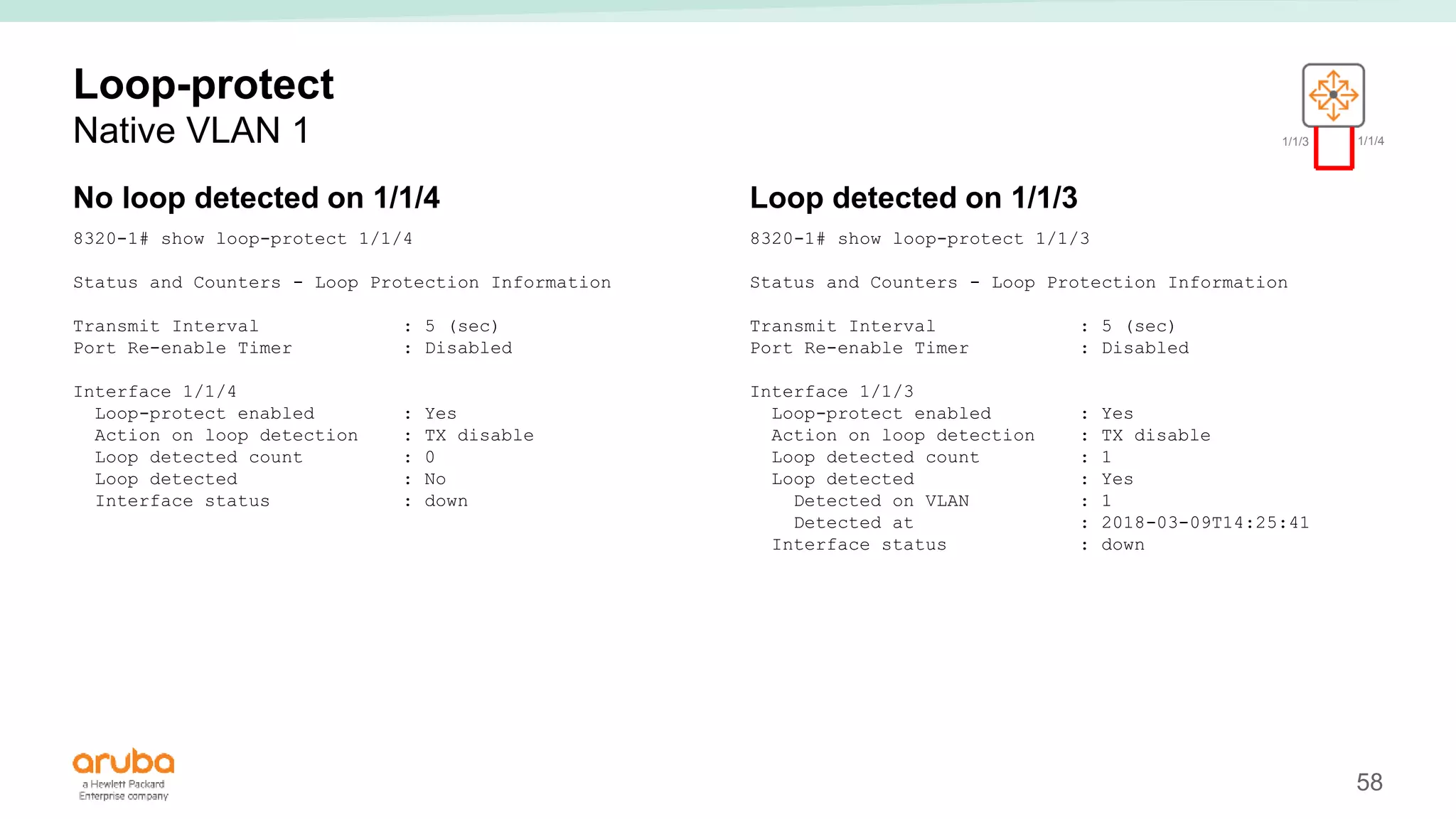
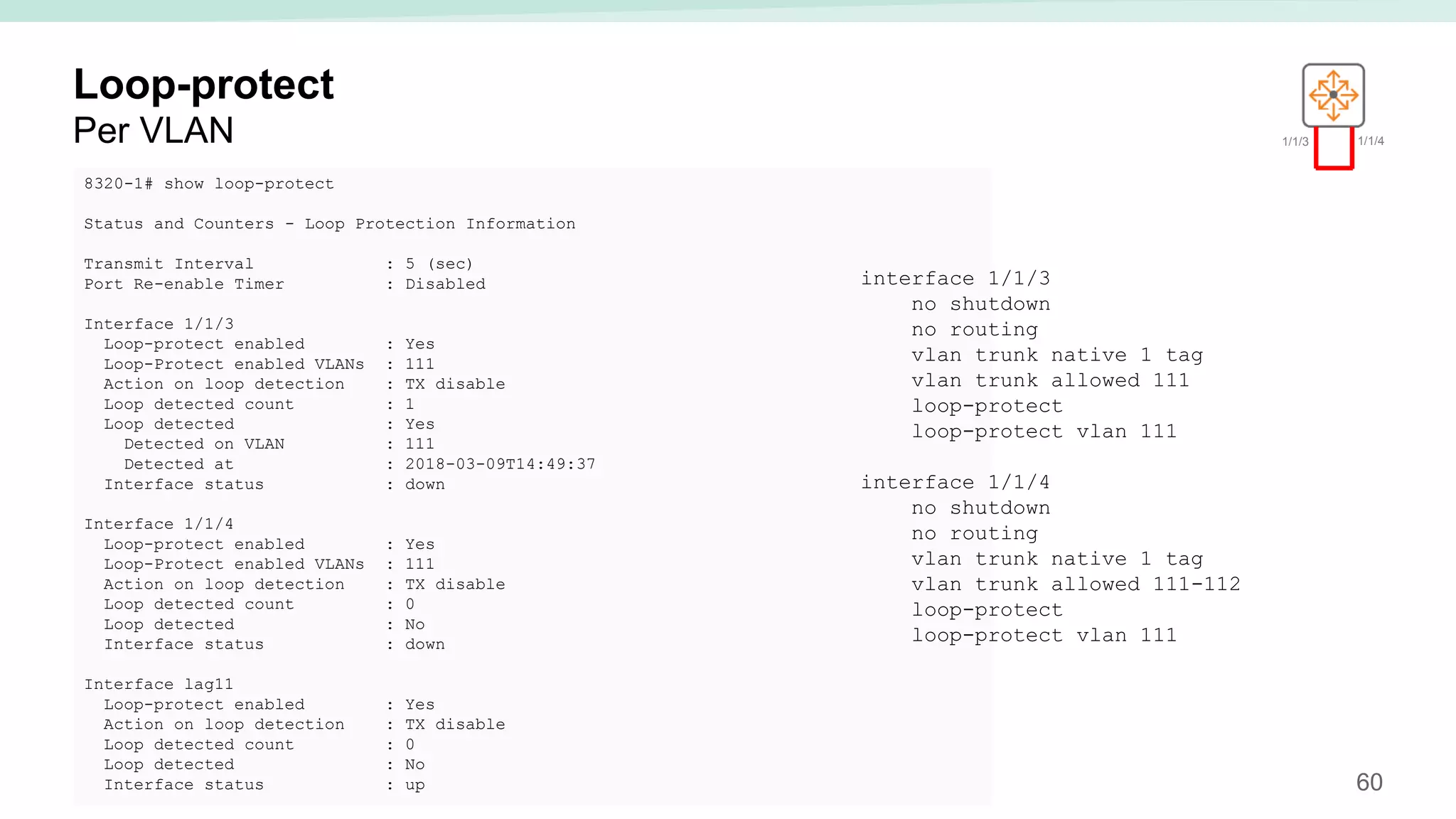
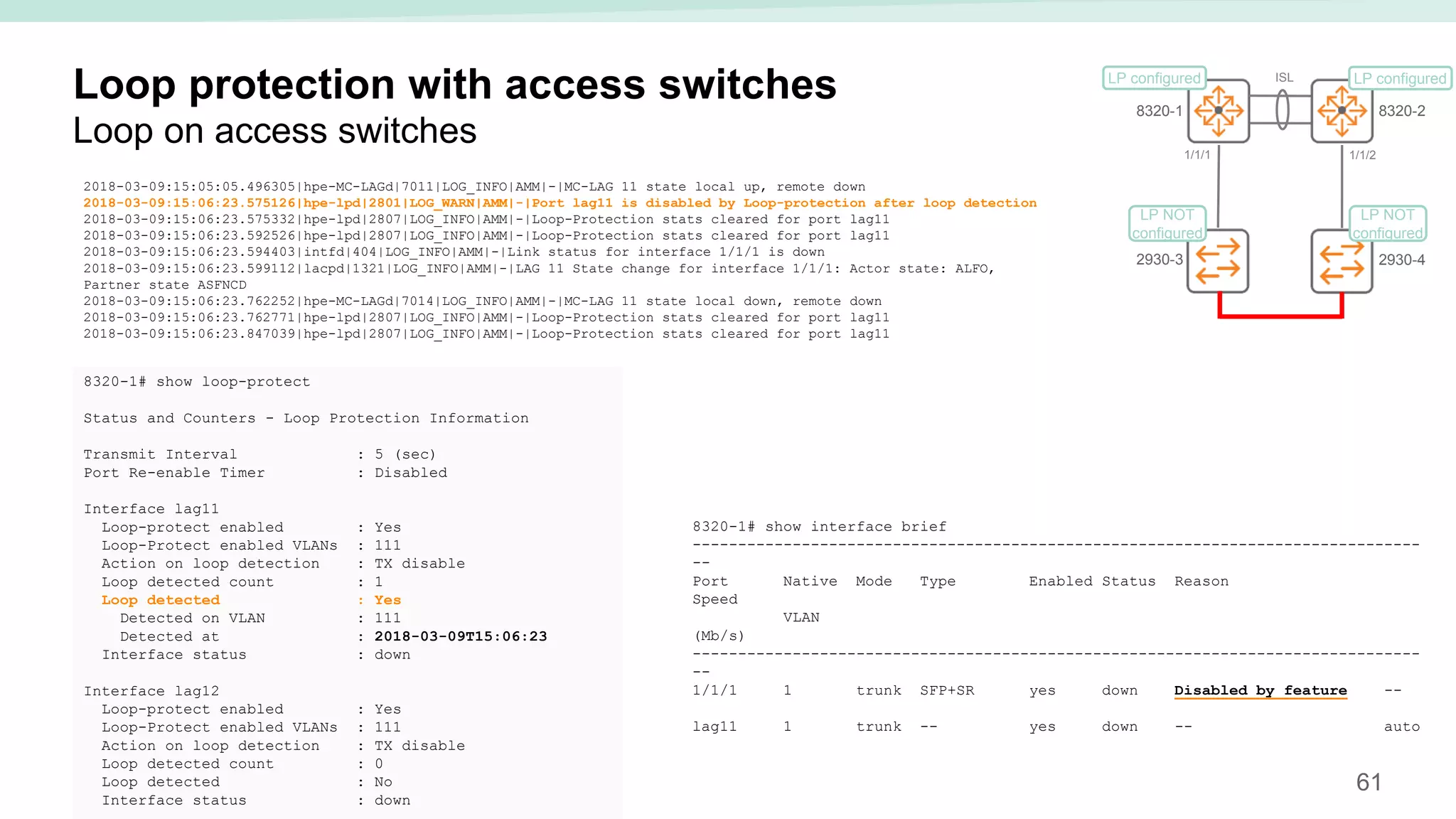
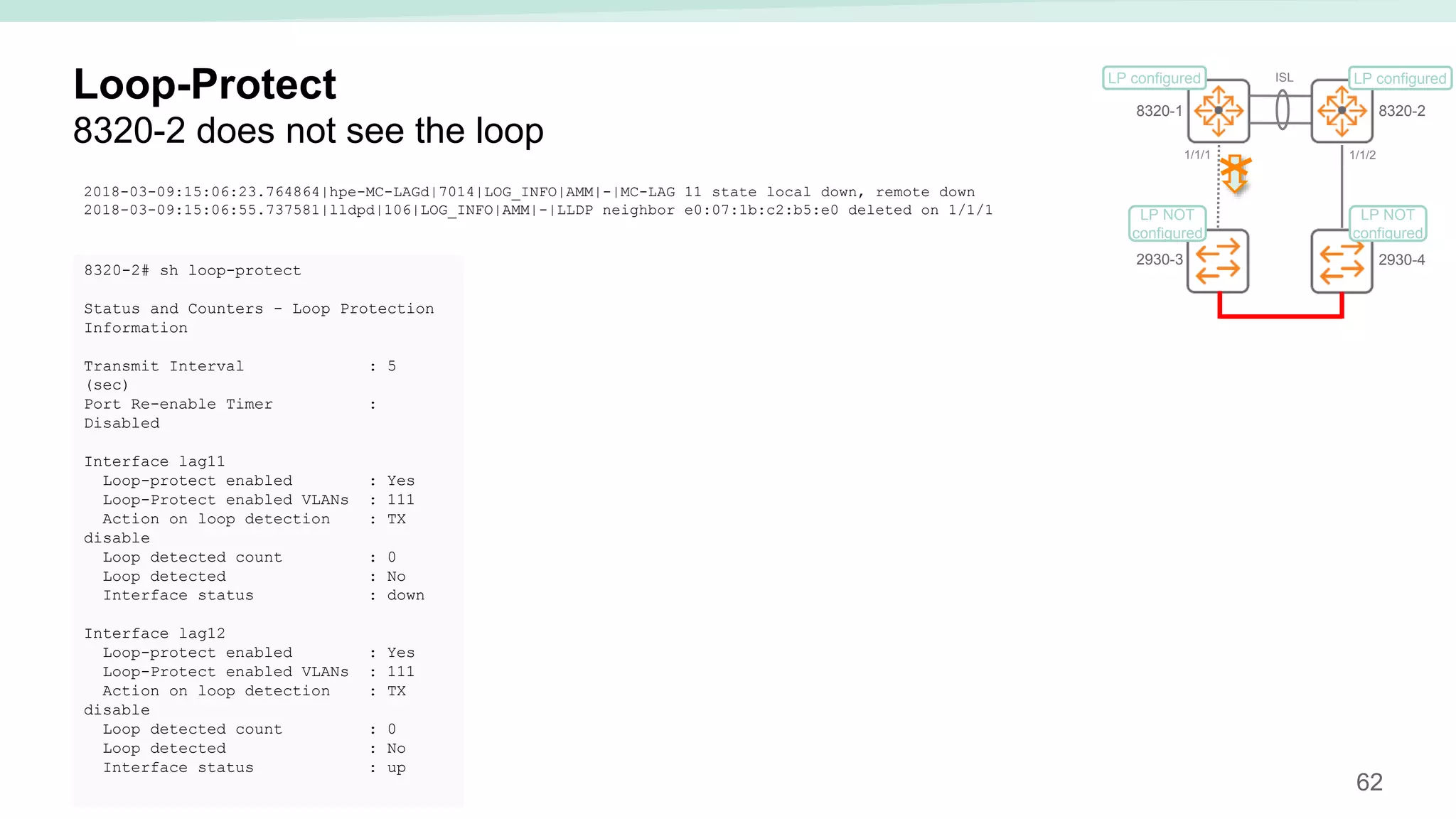
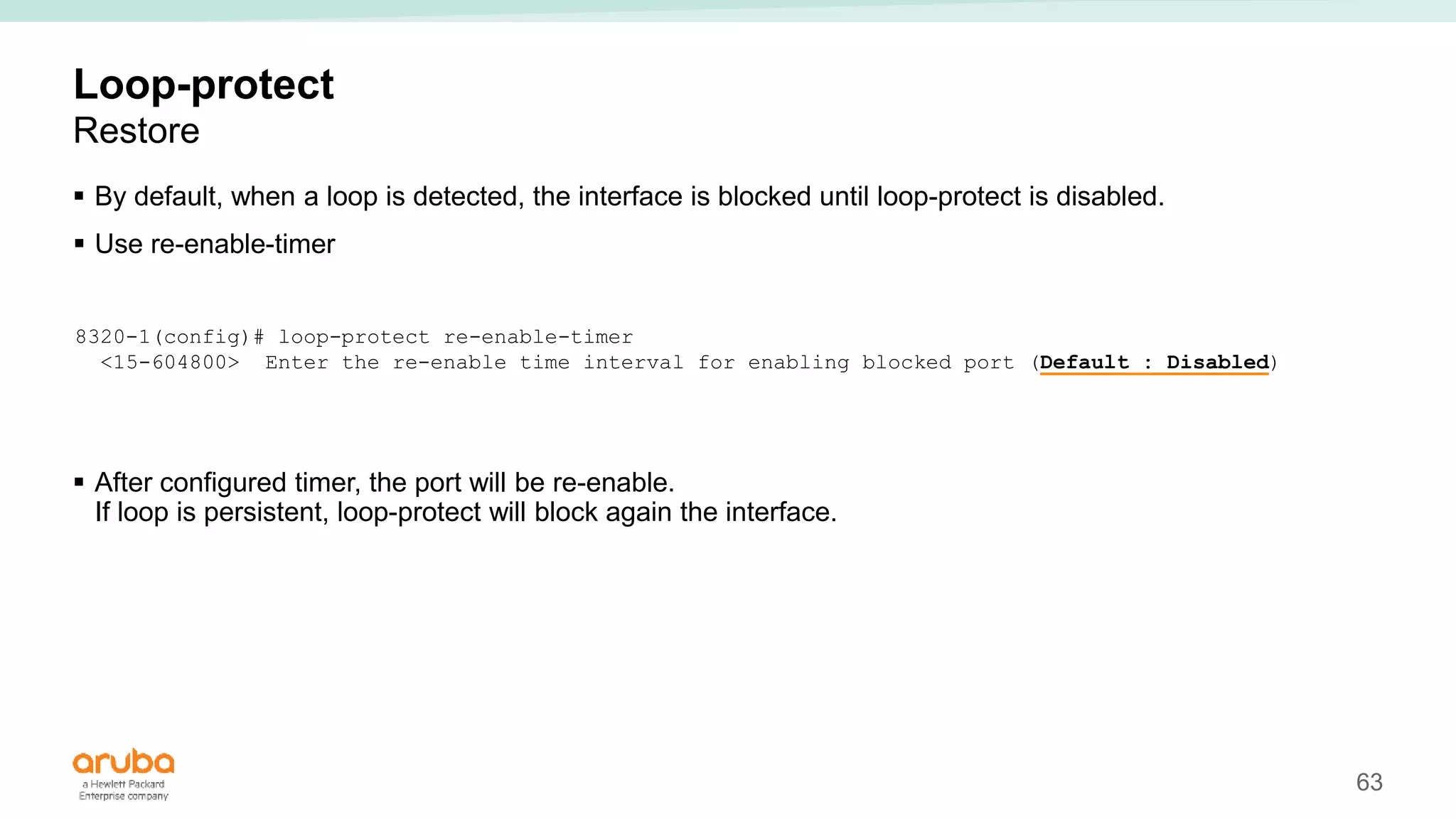
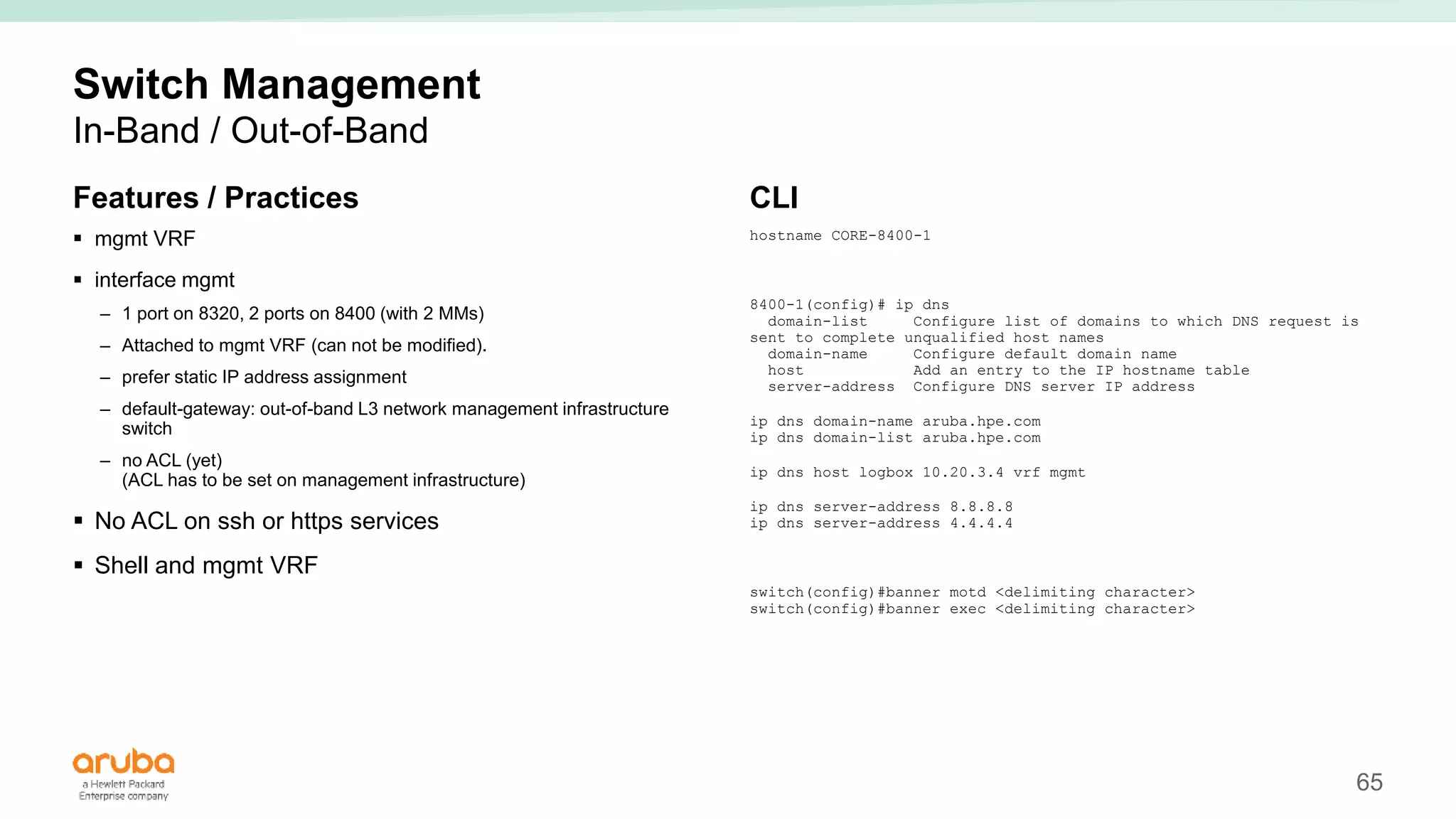
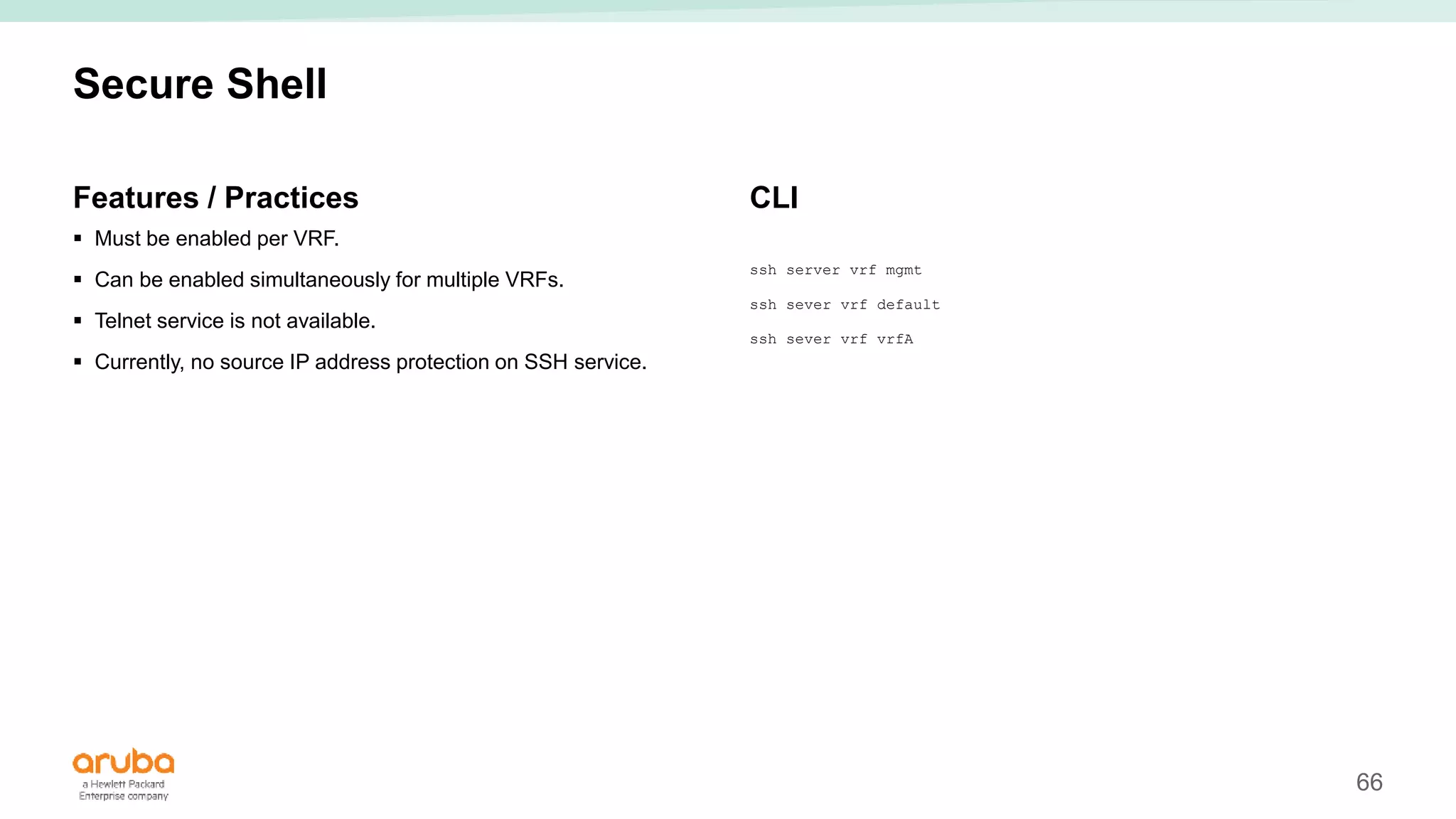
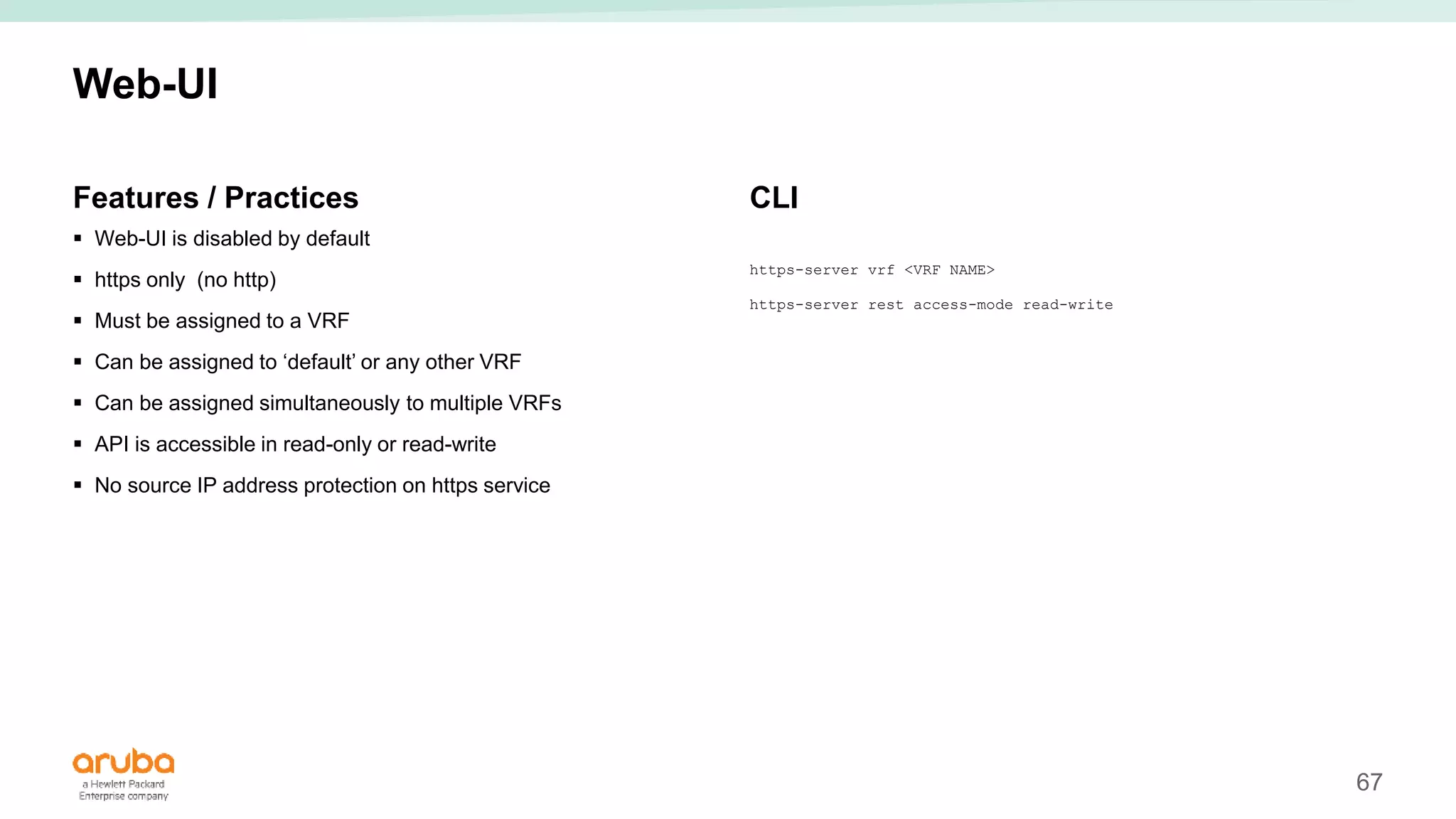
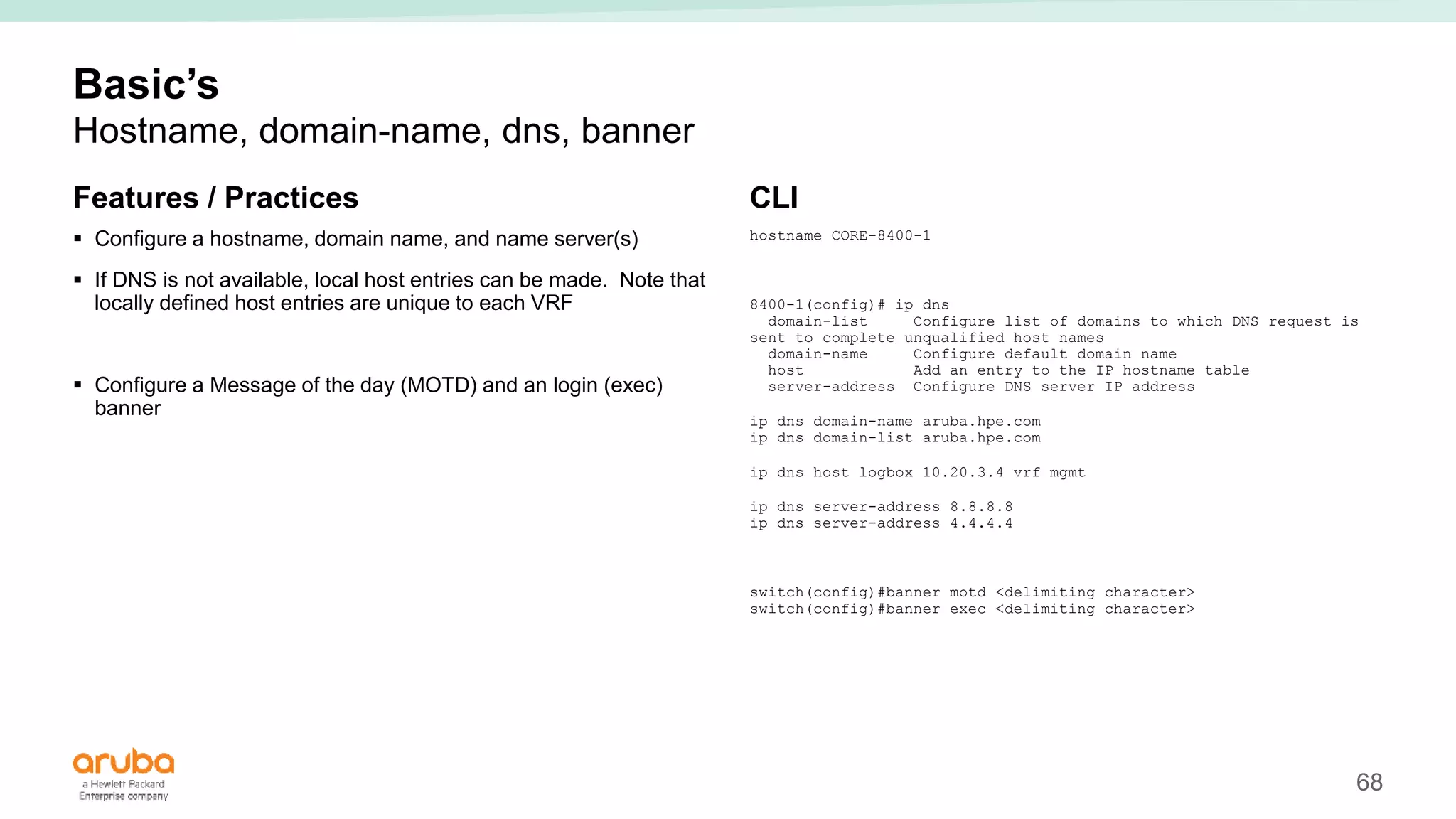
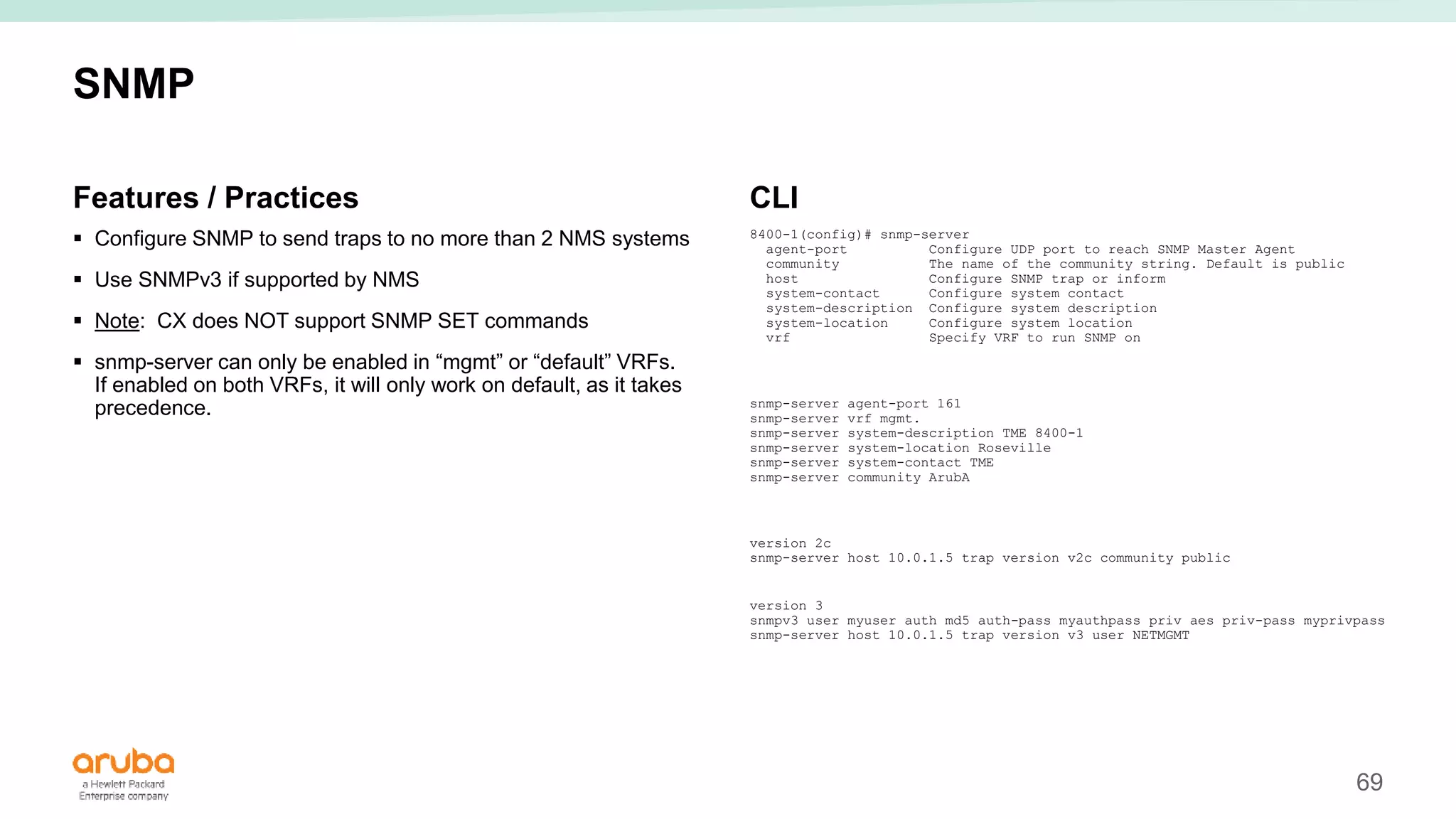
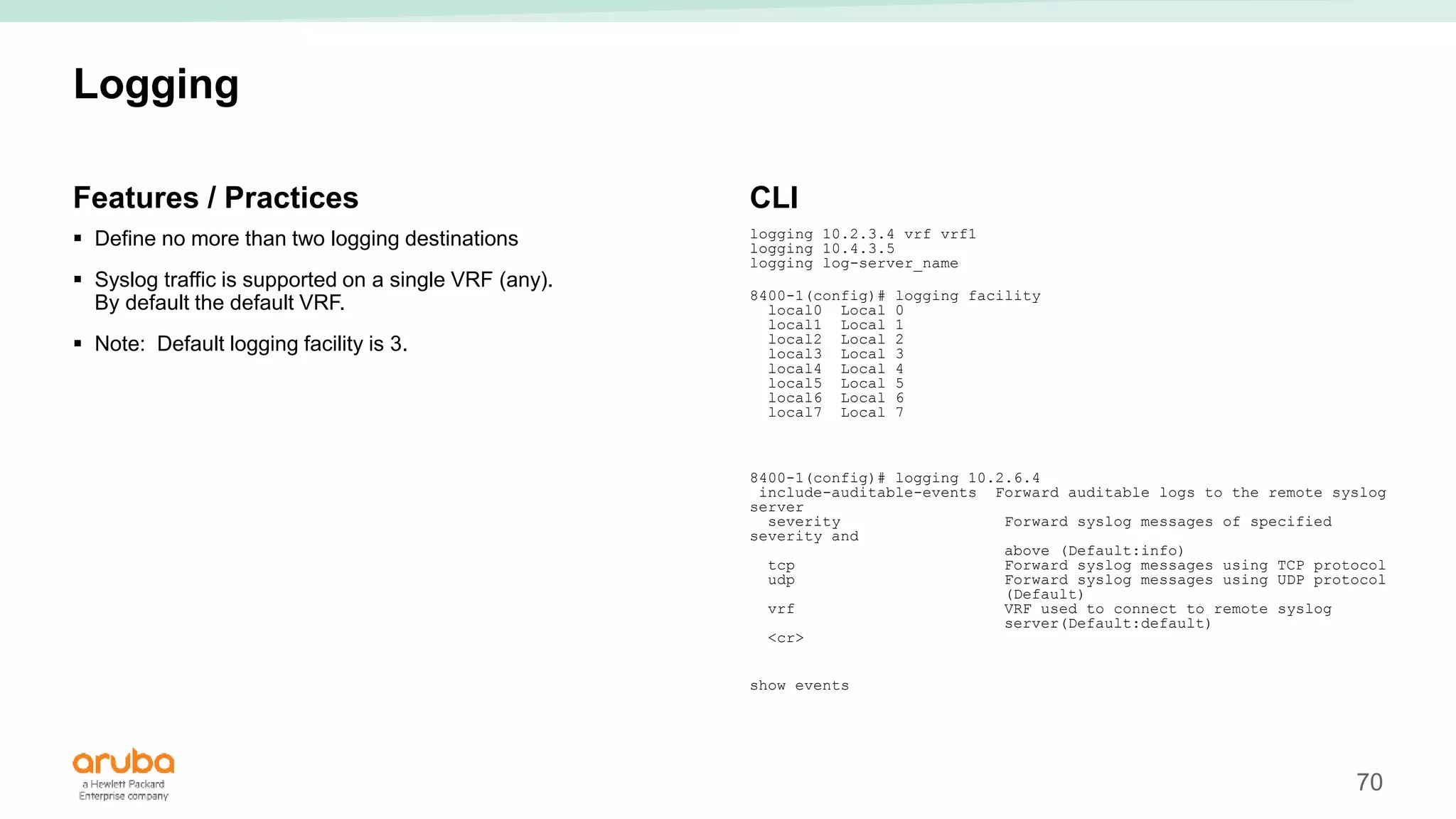
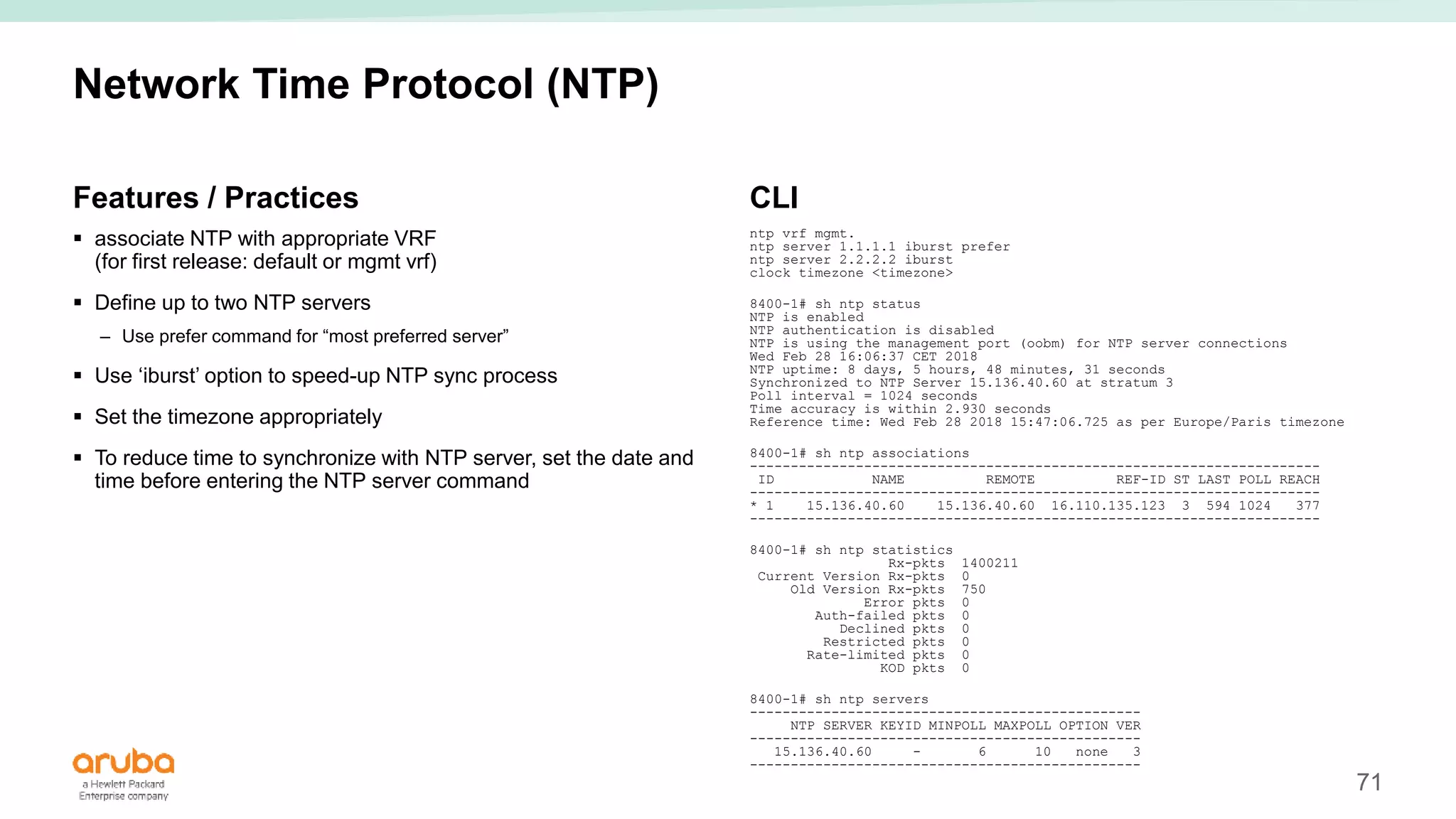
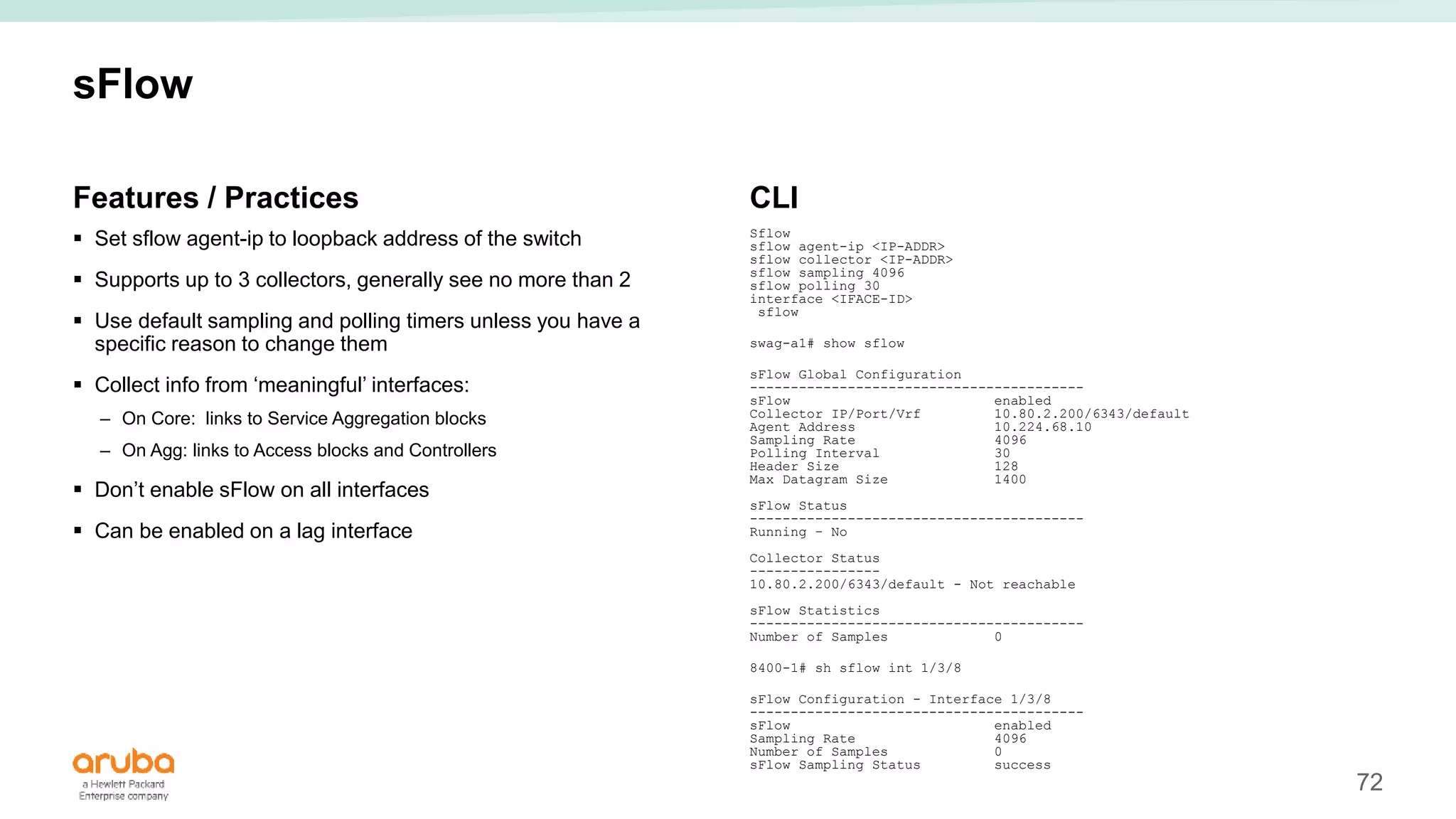
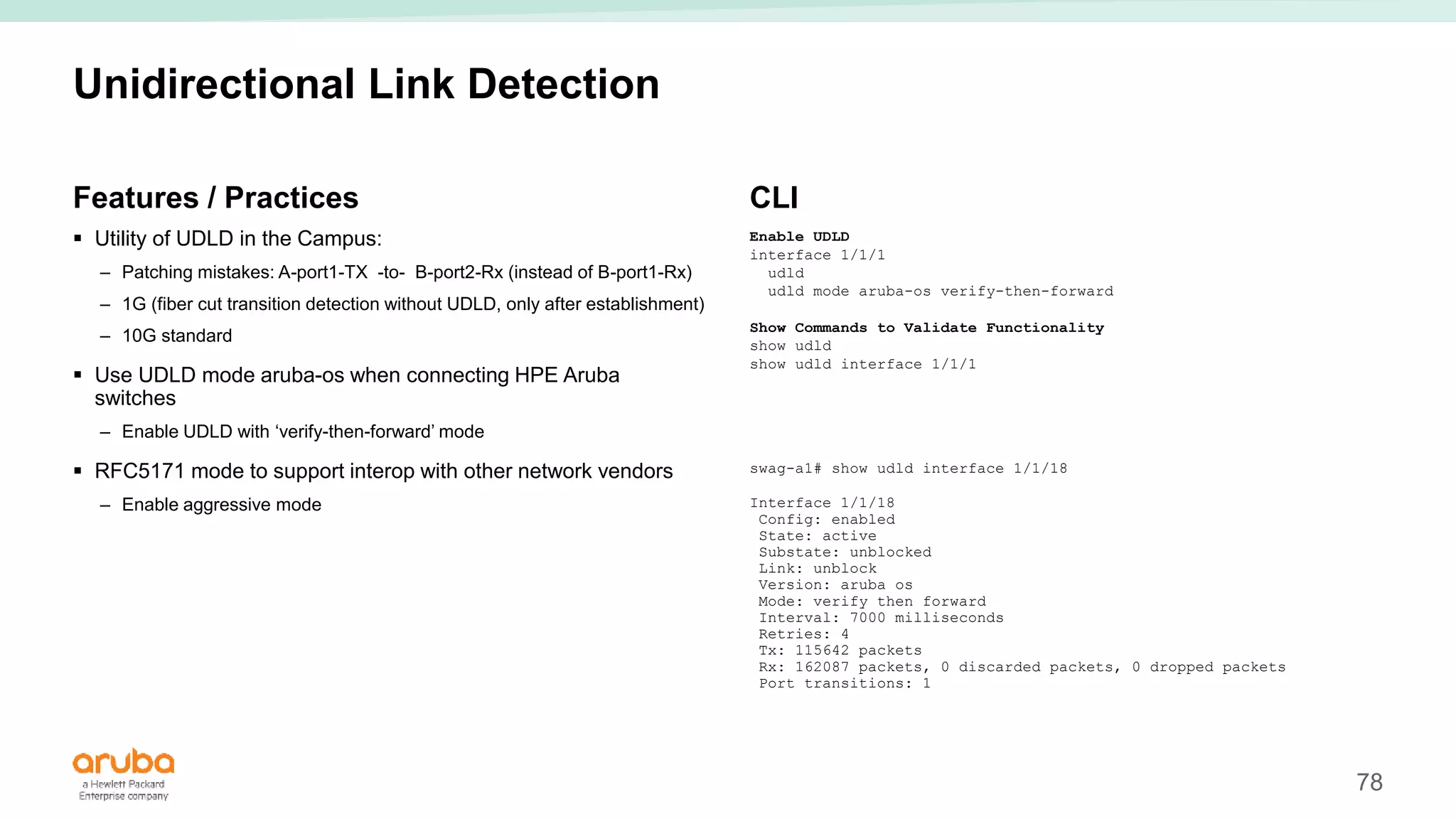
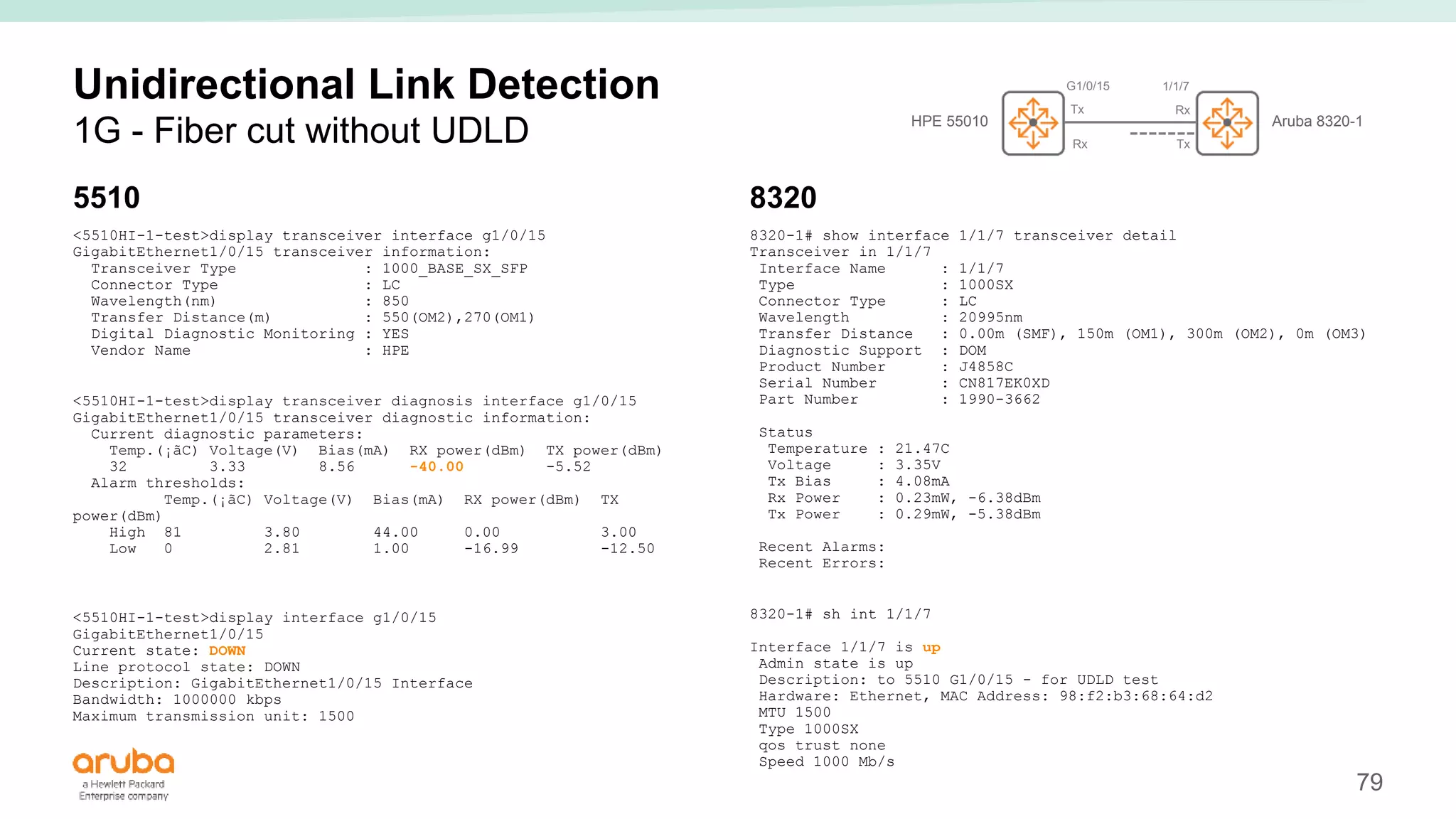
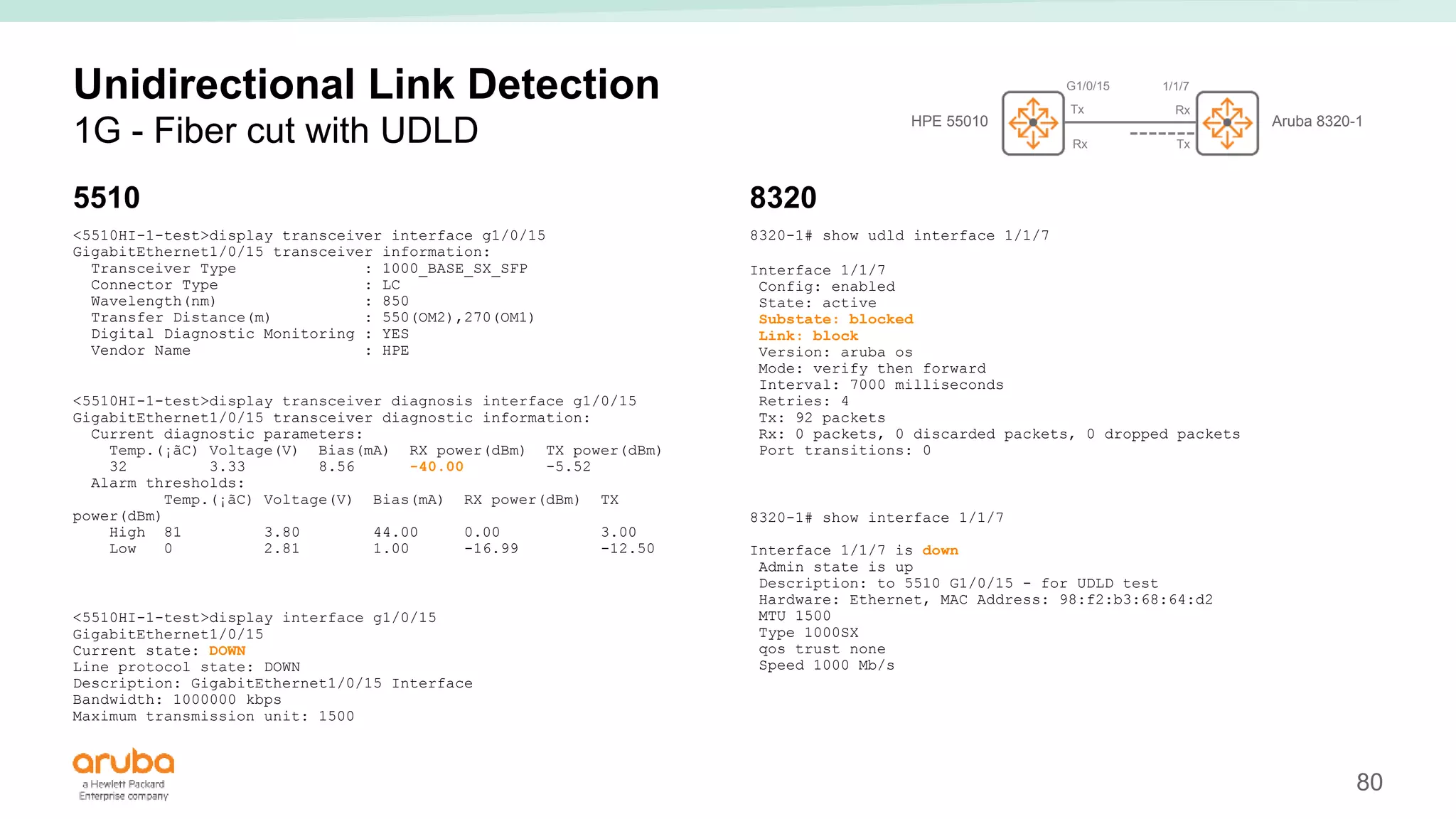
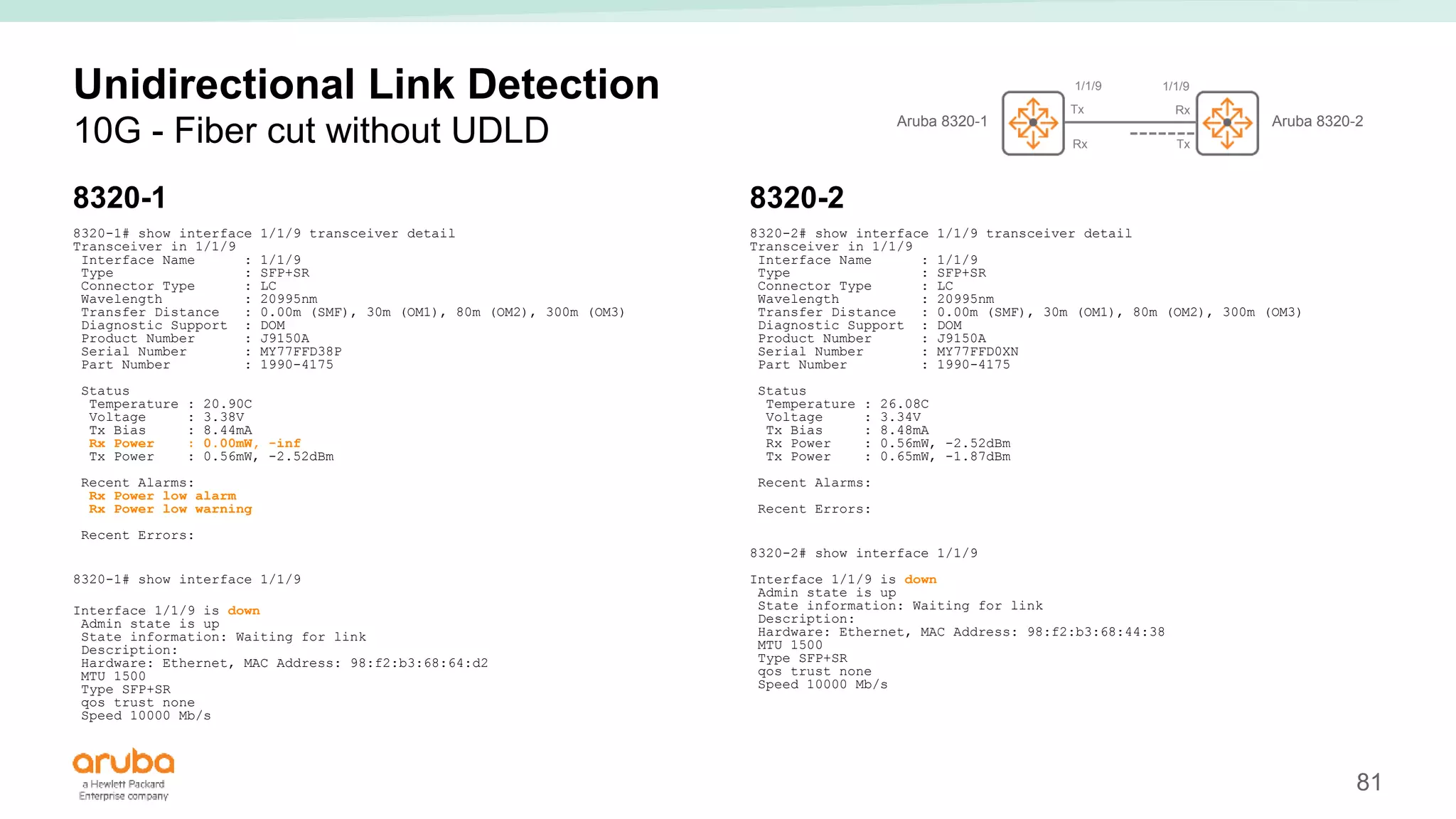
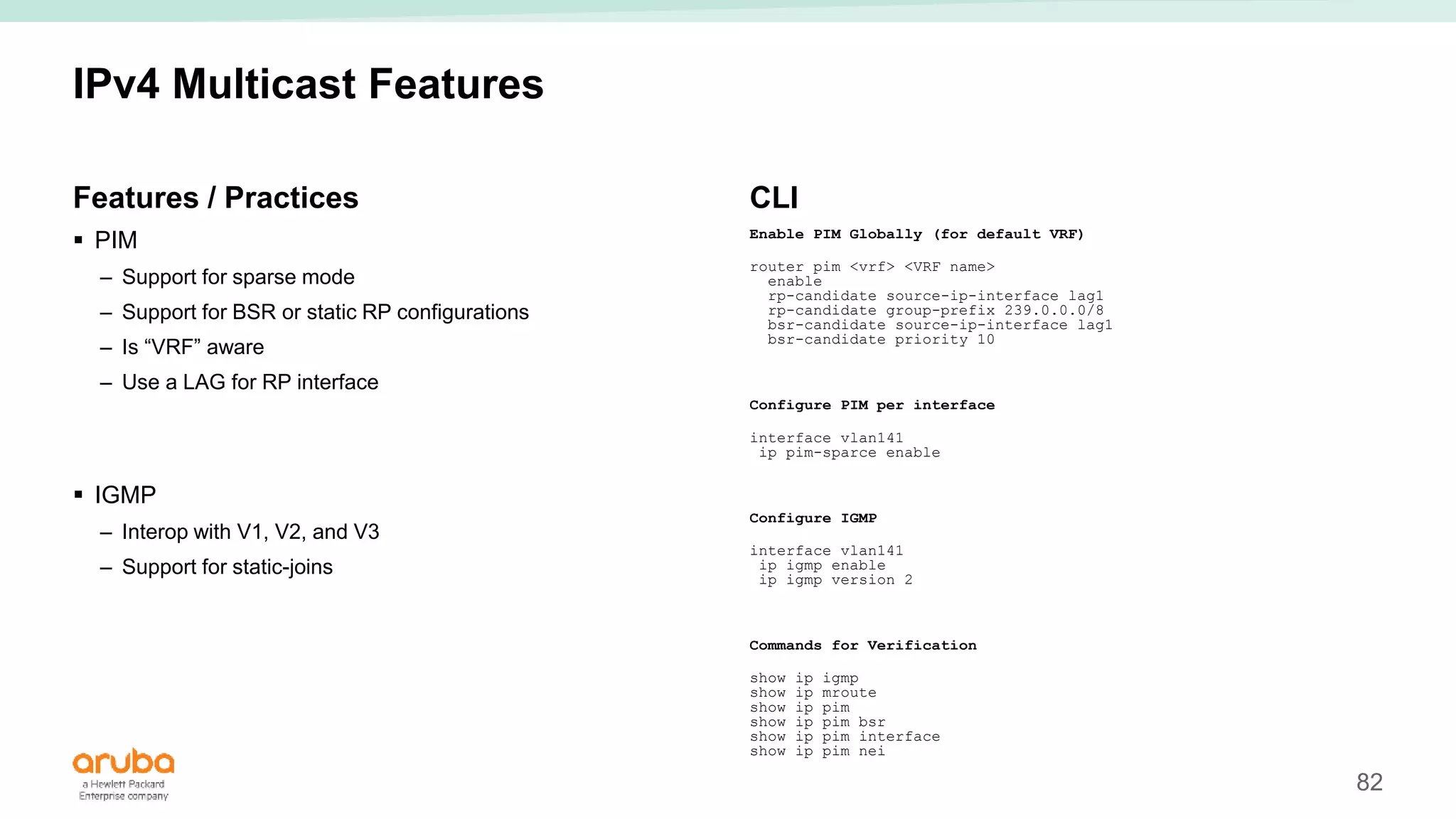
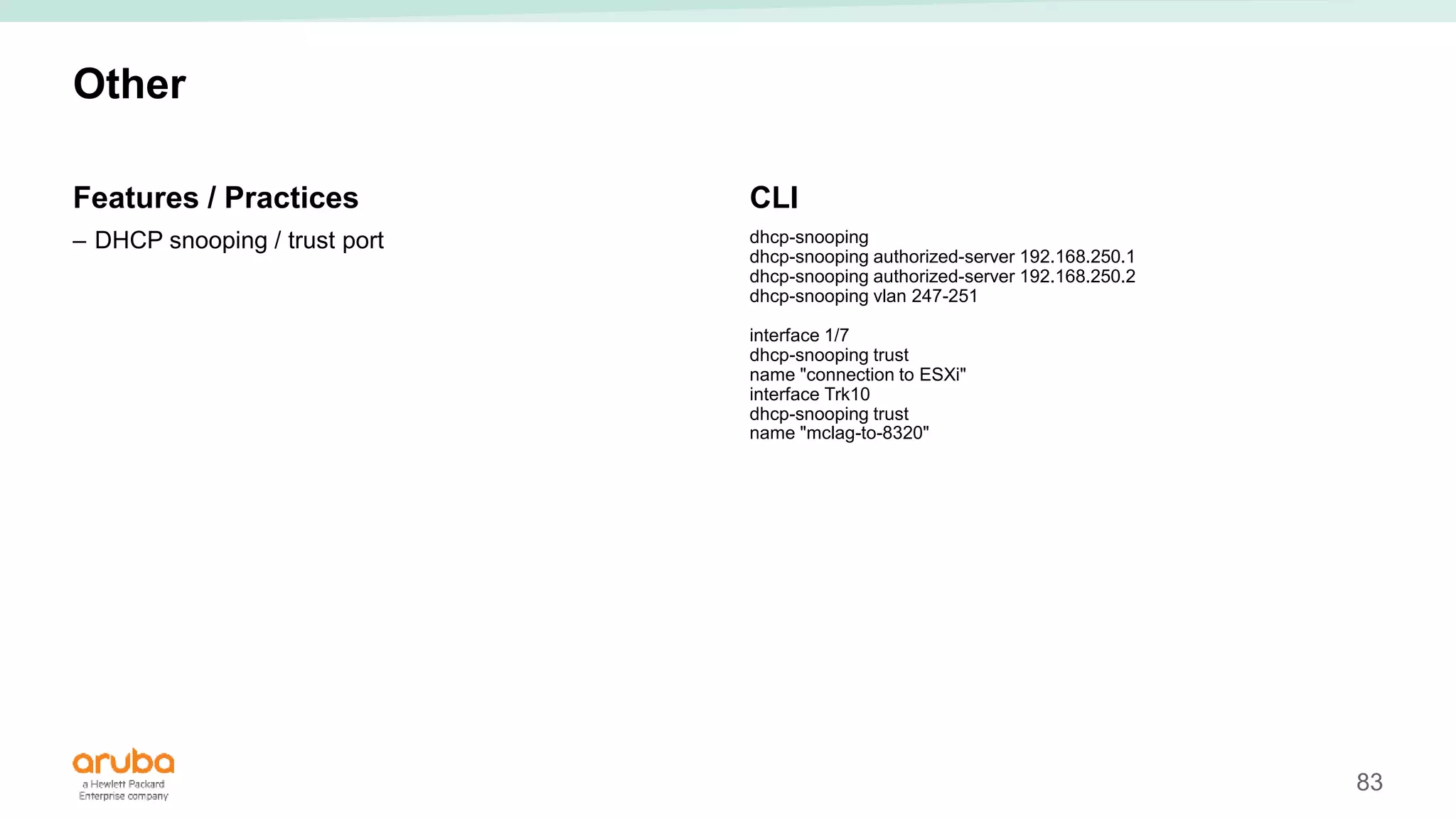
The document provides best practices for campus network design using ArubaOS-CX, emphasizing mobile-first architecture and the use of Virtual Switching Extension (VSX) technology. It discusses various configurations, including two-tier and three-tier campus networks, along with components involved such as core switches, access switches, and mobility controllers. Key focus areas include performance optimization, loop protection, and design implications for network management and scalability.